Cloud-native applications, built on architectures like containers and Kubernetes, are composed of many interconnected microservices that run on cloud infrastructure. And these architectures continue to rise in adoption.
According to the Cloud Native Computing Foundation (CNCF), 96% of organizations are currently using or evaluating the use of Kubernetes. This adoption is driven by the many advantages that Kubernetes brings, including shorter release timeframes, lower IT costs, increased scalability, and flexibility in multi-cloud environments.
For these reasons development and DevOps teams are flocking to Kubernetes so they can effortlessly deploy their applications daily or weekly and deliver as much business value as possible to their end-user stakeholders.
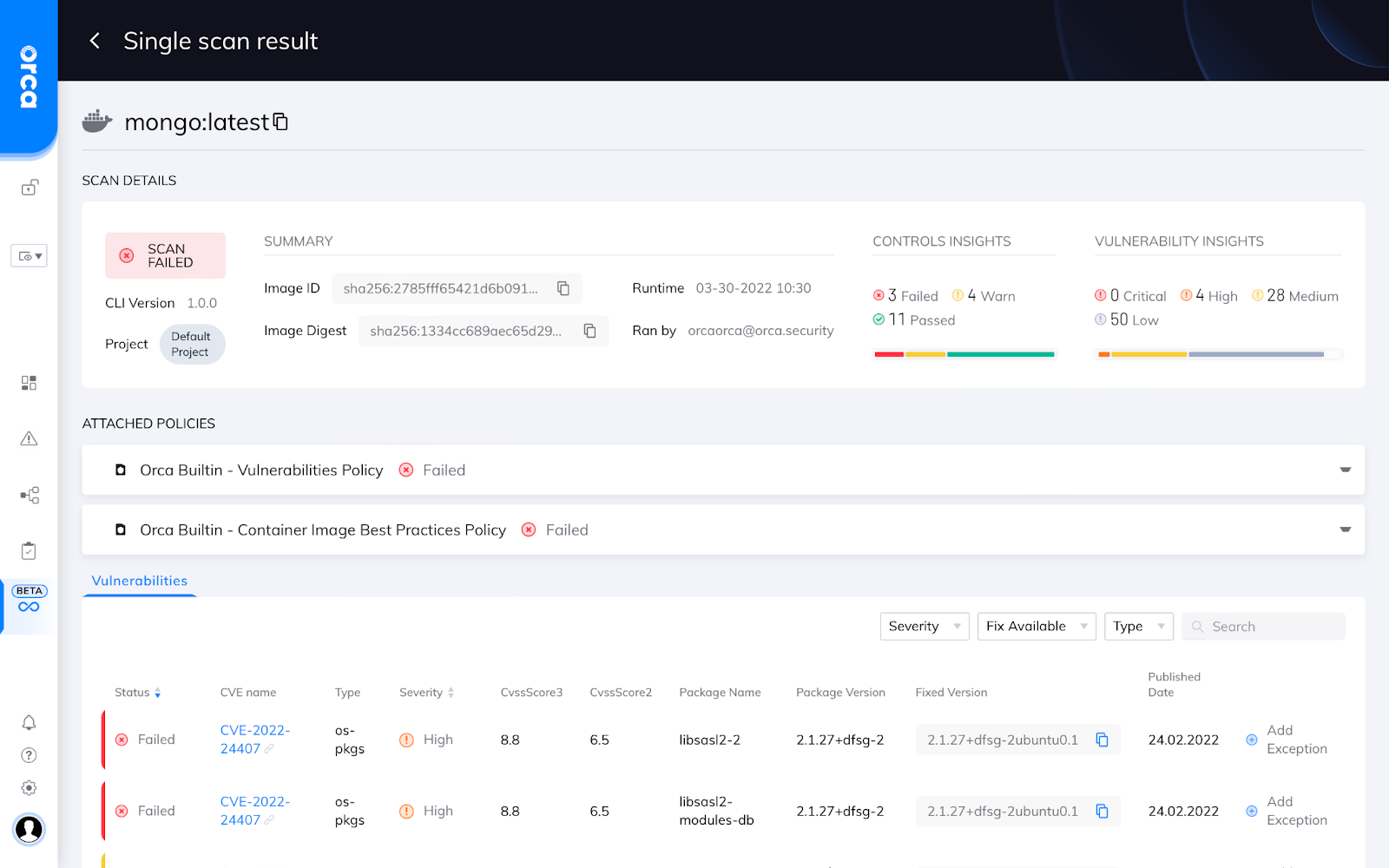
Example of Orca Security’s container image scan results
In addition to container and Kubernetes adoption, enterprises are leveraging Infrastructure-as-Code (IaC) as a technology and process to quickly and repeatedly provision cloud infrastructure.
Technologies like AWS CloudFormation templates, HashiCorp Terraform templates, and Kubernetes YAML files can be shared across development and DevOps teams. This allows teams to provision cloud infrastructure repeatedly without writing long, tedious files from scratch.
Addressing Cloud Risks Begins in Development
Many DevOps and security teams are familiar with runtime security requirements for cloud-native applications, including:
- Prioritizing vulnerabilities
- Identifying misconfigurations
- Detecting threats and preventing malicious activity
- Securing network configurations
- and many more…
However, many of these risks can be addressed in development to ensure that applications and infrastructure are secure by default.
For example, if development and DevOps teams scan their container images and IaC templates for vulnerabilities and misconfigurations, they can fix their top risks as part of the continuous integration and continuous delivery workflows.
Industry analysts continue to emphasize this requirement:
“Securing cloud-native applications offers enterprises the opportunity to redesign security approaches. Rather than treat development and runtime as separate problems — secured and scanned with a collection of separate tools — enterprises should treat security and compliance as a continuum across development and operations, and seek to consolidate tools where possible” – Gartner, Inc., Innovation Insight for Cloud-Native Application Protection Platforms, Neil MacDonald and Charlie Winckless, August 25, 2021
Integrating Cloud Security Across the Full Application Lifecycle
Security leaders are responsible for all aspects of the security governance program, including working with multiple teams to ensure applications are fully tested and securely deployed into production. Cloud-native companies can now count on Orca Security to integrate Shift Left Security capabilities securely across Build, Deploy, and Run both in native tooling and the Orca Cloud Security Platform. This provides DevOps and security teams with the context they need to support critical CI/CD phases in the development lifecycle:
- Build: Container images and IaC templates are scanned for vulnerabilities and misconfigurations on the developer desktop or as part of regular, continuous integration / continuous delivery (CI/CD) workflows.
- Deploy: Registries are continually monitored to ensure application artifacts are secure before deployment, with guardrail policies in place to prevent insecure deployments.
- Run: Production environments are monitored for risks with contextual alerts and risk prioritization, as well as integrations with modern ticketing and notification tools.

The Orca Platform brings differentiation to cloud native organizations with the ability to combine runtime context with vulnerability and compliance details across the application lifecycle. For example, organizations can now detect critical risks that often arise in development, including the following issues
- Sensitive data exposure: Context-aware controls, where an IaC template may configure an insecure storage bucket that stores PII.
- Secrets detection: Identifying secrets where a private key as part of a CI scan could allow lateral movement risks.
- Production risks connected to CI: Connecting the origin of artifacts and the exact CI that scanned them and auto-assigning new issues directly to the proper development or DevOps team.
Orca CLI
To deliver the capabilities discussed in this announcement, we are unveiling our command-line interface (CLI) called Orca CLI. The CLI will allow development and DevOps teams to scan their images and IaC templates, view results in their native tools, and communicate findings to the Orca Platform.
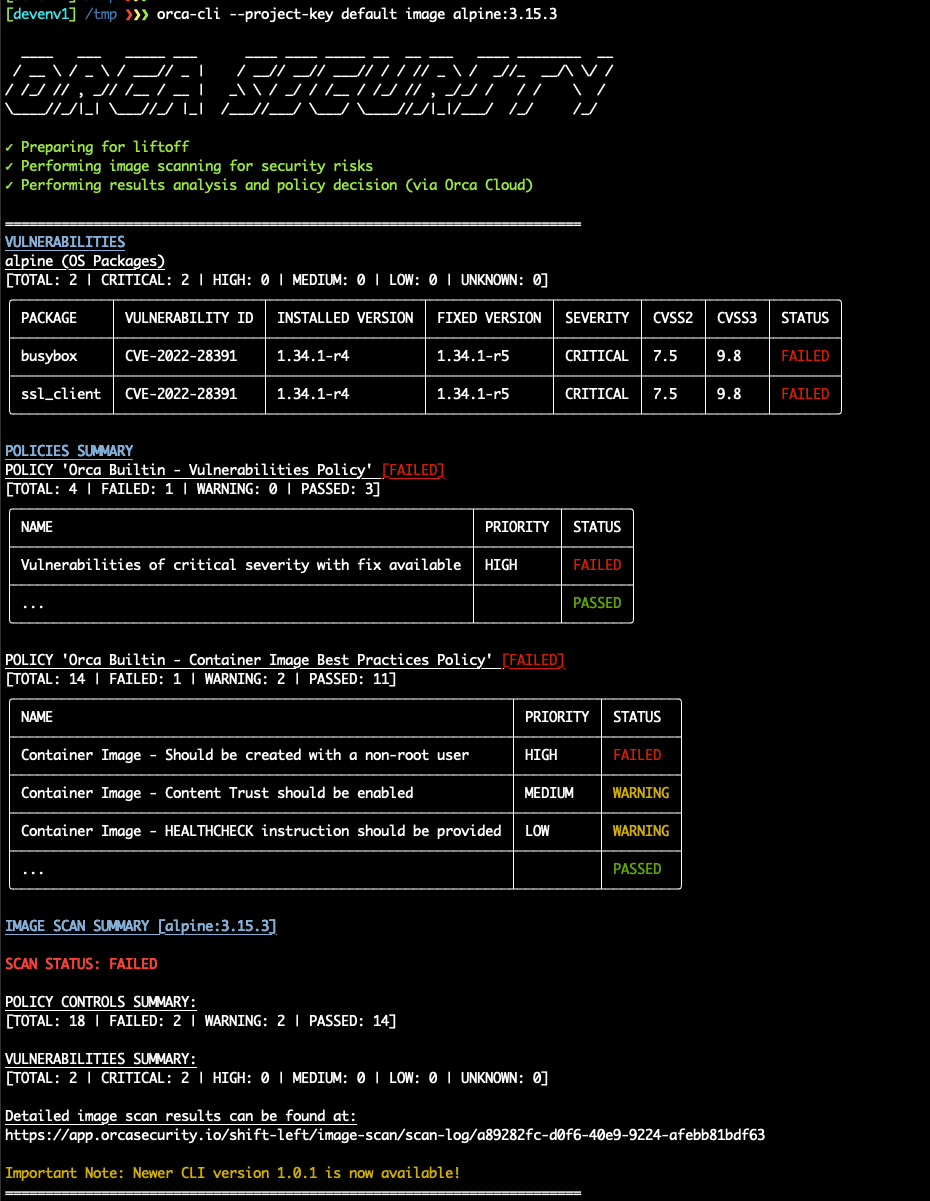
Orca CLI, our new command line interface
Orca CLI supports any standard CI tool, such as GitHub Actions, Jenkins, CircleCI, Bamboo, or Bitbucket.
Shift Left Dashboard in the UI
Within the Orca UI, users will see a new tab called Shift Left. The Shift Left dashboard shows the following three views: (1) Policies that teams set for the images and IaC templates, (2) Projects to group users at their organizations, and (3) Scans logs listing all scans and results in one place.
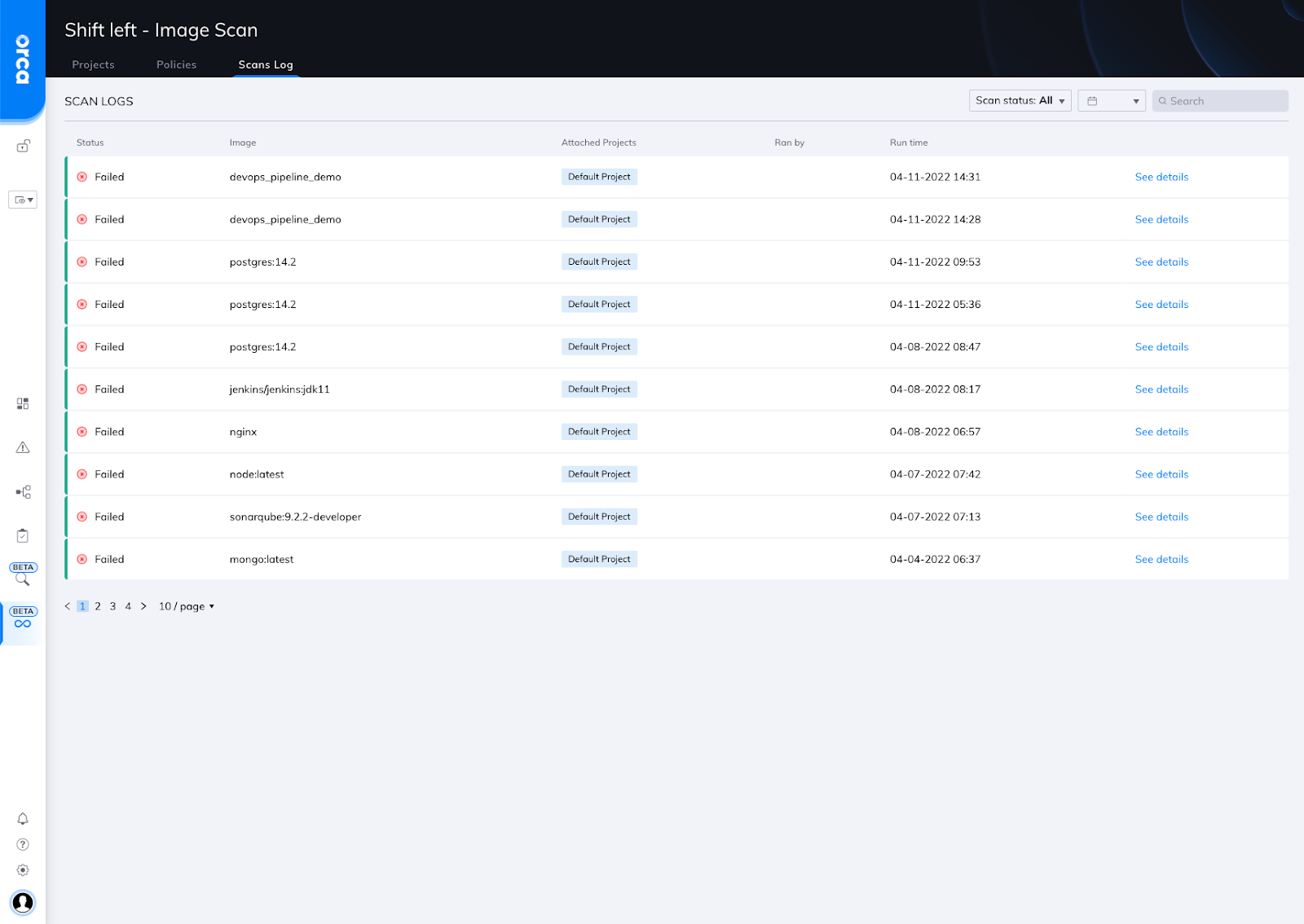
Orca Shift Left dashboard with Projects, Policies, and Scans Log tabs
Configuring Shift Left Security Policies
The Orca UI features a drag-and-drop Policy Catalog that includes pre-built vulnerability and compliance policies, as well as the ability to add custom policies.
Policies can be configured to alert on or block builds from moving forward in the development process with results shown in both native developer tooling and the Orca Platform.
Importantly, Policies can be assigned globally or to a specific Project, which likely represents a team or group at the organization. This flexible customization allows security teams to fine-tune Policies for specific teams across their company.
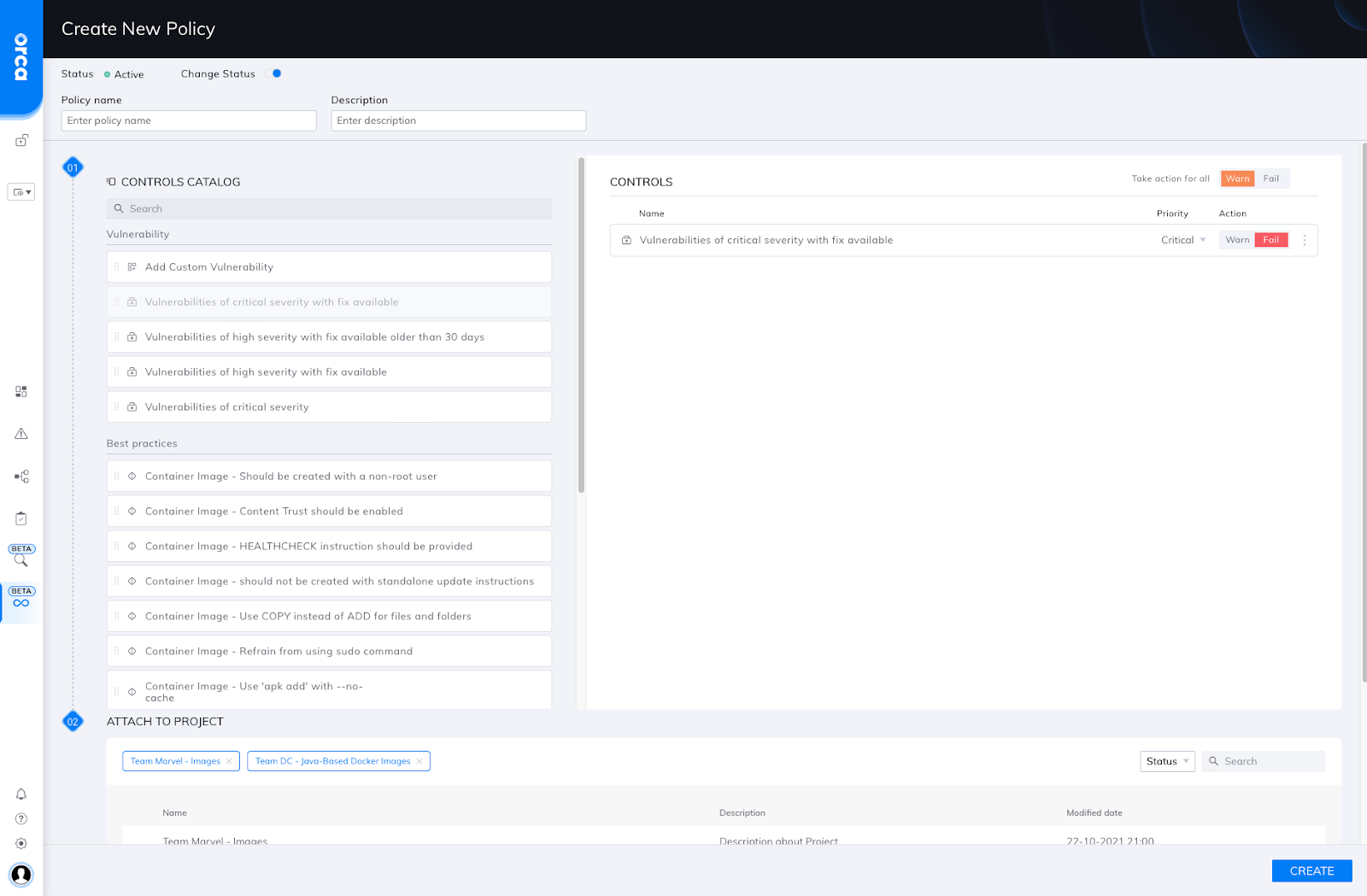
Orca Policy configuration UI
Viewing Shift Left scan results
All scan results are shown within the Scan Logs tab, where every scan can be viewed in detail. The results include CVE findings, as well as compliance findings, as shown in the screenshot below.
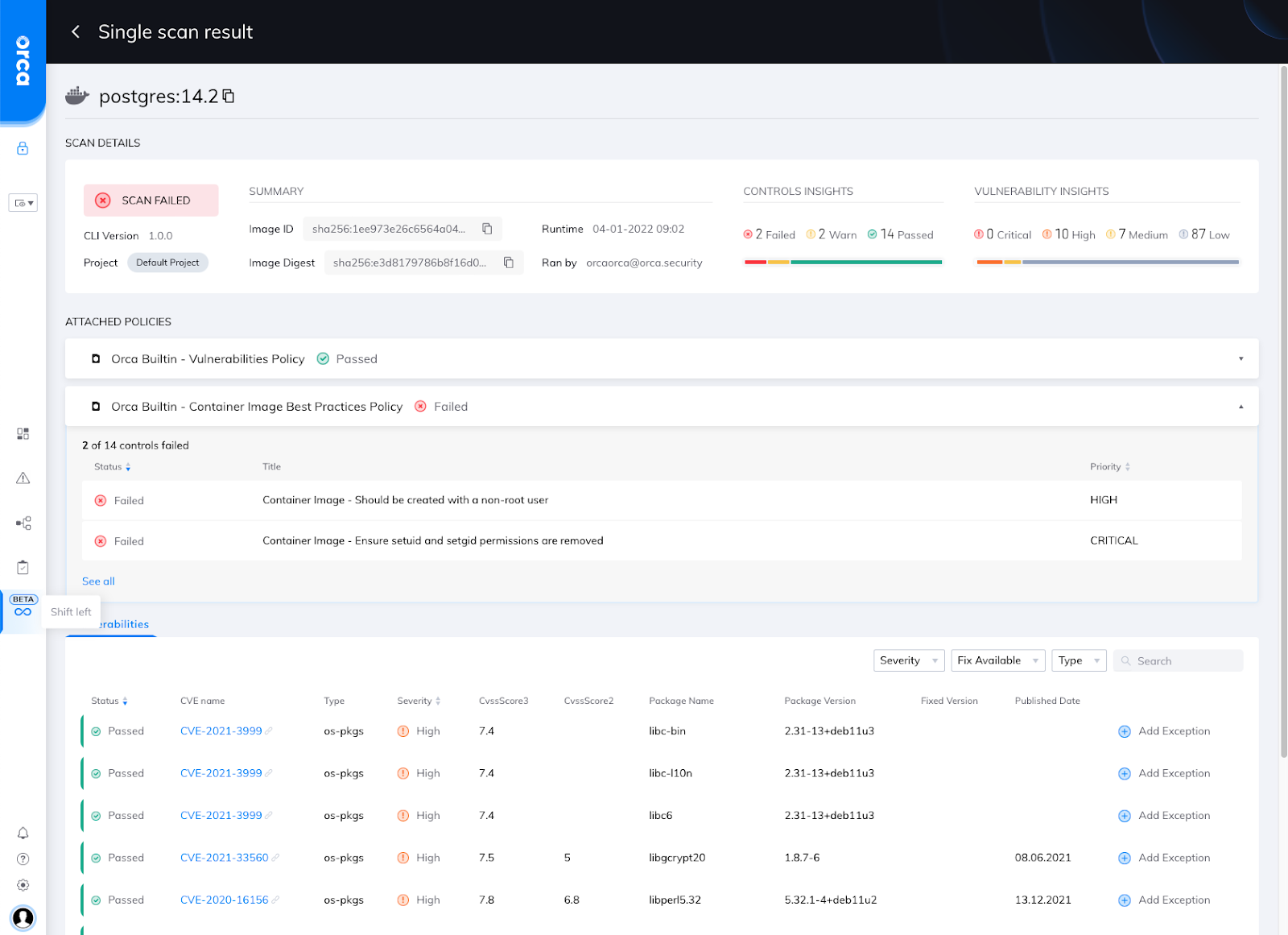
Shift Left UI with scan results
Future Shift Left Additions to the Orca Platform
As security teams partner with DevOps teams to secure their cloud-native applications, Orca is committed to providing even more powerful features for our users.
In the coming months, we plan to add policy-based registry scanning to provide added control over deployments as well as virtual machine (VM) image scanning as the next innovation in our Shift Left Security feature set. True to the Orca mission, we’ll continue to bolster our existing runtime capabilities to best support our customers.
Shifting Left with Orca
With these enhancements to Shift Left in the Orca Platform, security teams can now partner with development and DevOps teams across their organization to detect vulnerabilities and defects, fix these risks, and enable policies to prevent them from happening again.
Ultimately, this helps organizations achieve a higher level of code quality and security than ever before, and avoid damaging and costly security issues at production time.
Learn More
Ready to learn more? Download our Shift Left Security eBook or join us on June 21st for our Webinar ‘Find and Fix Cloud Security Risks Earlier in the Development Cycle’.
Are you going to KubeCon and CloudNativeCon on May 16-20 in Valencia, Spain (or attending virtually)? Come and visit Orca Security at Stand S77 – we’d love to talk to you and show you how Orca fits in seamlessly into your CI/CD process.
Want to get started right away? Sign up for a free 30-day trial to see how quickly and easily the Orca Cloud Security Platform can help you identify and manage risks early in your software development lifecycle.





