According to the Verizon Data Breach Investigation Report, vulnerability exploitation caused one in every five data breaches last year, a 34% year-over-year increase.
Protecting against breaches and severe security incidents calls for a multi-faceted approach. On the one hand, organizations need to proactively identify and remediate risks before threat actors can exploit them. And on the other, security teams need to protect their most sensitive workloads with runtime capabilities that can detect, monitor, and neutralize active threats in real-time.
This one-two combo ensures organizations can confidently meet the challenge of their maturing cloud estate and a prolific threat landscape that operates around the clock and globe.
It’s also why we’ve added a powerful set of new detections to Orca Sensor, a lightweight eBPF-based sensor that fully integrates with the Orca Cloud Security Platform. Our latest round of detections enhance real-time visibility and protection for a broader range of attack tactics, techniques, and misconfigurations across cloud and container environments.

Why is Orca adding new detections to Orca Sensor?
According to IBM’s 2024 Cost of a Data Breach Report, the mean time to identify a data breach is 258 days on average globally. As the number and cost of data breaches continue to increase, organizations need the ability to identify and respond to compromises earlier, faster, and more effectively.
That explains why we’ve added new detections that provide earlier signals of compromise, helping security teams uncover stealthy attack behaviors and strengthen runtime protections for containers and virtual machines, cloud infrastructure, the Kubernetes control plane, and more.
This release further enhances the Orca Cloud Security Platform, which combines real-time and agentless security with pre-deployment (Application Security) capabilities in one unified solution.
What do the new detections include?
While we continue to expand the detections offered by Sensor, the latest additions cover a variety of early indicators of compromise (IoC), including:
Container escape detection
Containers are a foundational element of cloud-native architectures—but if improperly secured, they can become launchpads for broader compromise. Our new container escape detections identify attempts to break out of container isolation using tools or misconfigured capabilities. By surfacing these actions in real time, security teams can act before attackers can escalate privileges and execute unauthorized actions on the host system.
Privilege escalation and cloud reconnaissance activity
Privilege escalation and reconnaissance are common mid-stage techniques used to deepen access and locate high-value targets. Our new detections identify attempts to escalate privileges via Polkit exploits or suspicious configuration changes. We also now detect enumeration and credential discovery operations using tools like Azure CLI and gcloud, helping teams stop attackers before they move laterally or exfiltrate data.
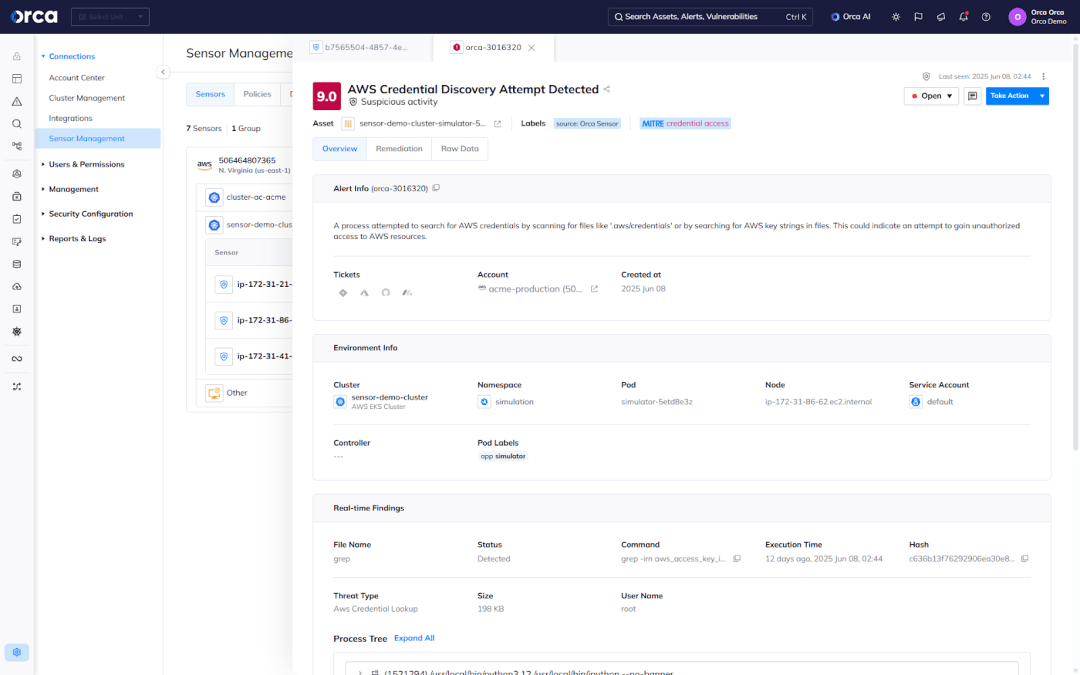
Abuse of legitimate tools (“living off the land”)
Sophisticated attackers often rely on legitimate tools to fly under the radar. Our latest updates catch “living off the land” techniques—such as using tools like GTFOBins or abusing cloud agents like AWS SSM—for lateral movement and execution.
Suspicious network activity
We also monitor for suspicious outbound traffic patterns, such as DNS lookups to known offensive security domains or the abuse of HTTP proxies, signaling possible exfiltration or command-and-control attempts.
Control plane and configuration monitoring
We also surface risks from actions such as attempts to copy artifacts from container file systems using the Kubernetes control plane, as well as changes to configuration capabilities. The former may indicate unauthorized data exfiltrations through compromised service accounts or stolen credentials, while the latter may indicate an attempt to alter system privileges.
About the Orca Cloud Security Platform
Orca offers a unified and comprehensive cloud security platform that identifies, prioritizes, and remediates security risks and compliance issues across AWS, Azure, Google Cloud, Oracle Cloud, Alibaba Cloud, and Kubernetes. The Orca Cloud Security Platform leverages Orca’s patented SideScanning™ technology to provide complete coverage and comprehensive risk detection.
Learn More
Interested in discovering the benefits of the Orca Platform and its real-time and agentless runtime security? Schedule a personalized 1:1 demo.






