PAN Prisma Cloud customers deserve better than a Maginot Line of cybersecurity
Abstract: In a recently published blog post, Palo Alto Networks claimed that Orca’s SideScanning™ technology delivers only “rudimentary security capabilities,” and the future of cloud security relies on installing their 0.5GB Defender on your workloads. In response, I’ll explain why they got it all wrong and why the future of cloud security is agentless.
I’ll start this blog post with a personal note – I am delighted that Palo Alto Networks has chosen to move away from its earlier approach of threatening competitors with legal action to a productive product vs. product comparison.
Orca’s Agentless Cloud Security Platform, powered by the patent-pending SideScanning technology has several major advantages over the traditional, agent-based PAN Prisma Cloud package.
Coverage
Coverage has always been the Achilles heel of security. It doesn’t matter how strong your security is if it’s only deployed in a portion of your environment. This is the Maginot Line of cybersecurity – it doesn’t matter how strong or long the walls are. If they don’t cover your entire fortress, they can’t protect it – and agent-based solutions never will.
On average, less than 50% of workloads are covered by agent-based tools. I’ve yet to see any large organization that has managed to reach > 80% coverage using agents – including PAN Prisma Cloud Defenders. The reasons are many and include:
- Organizational friction – unfamiliar (or unknown) environments that lack security governance (e.g. different BU’s, timezones, etc.)
- Unsupported versions (naturally – older OSes are at the highest risk, so how does it make even remote sense not to support them?)
- Minimal / hardened OSs – where heavy agents simply cannot be installed
- Communication issues – where the agents can’t communicate to the mothership – around 20% of the agents are not functional due to that
The outcome is always the same – security implementation with more holes than Swiss cheese.
Frequently, when customers switch from Prisma to Orca they find numerous neglected workloads with literally zero security. They’re rife with vulnerabilities, are already infected many times over, and provide absolutely no visibility.
If you somehow manage to deploy agent-based security on 70% of your environment (which can be considered an extremely successful implementation), your risk reduction remains far below 70%. Ungoverned environments are usually where your real risk resides.
Context
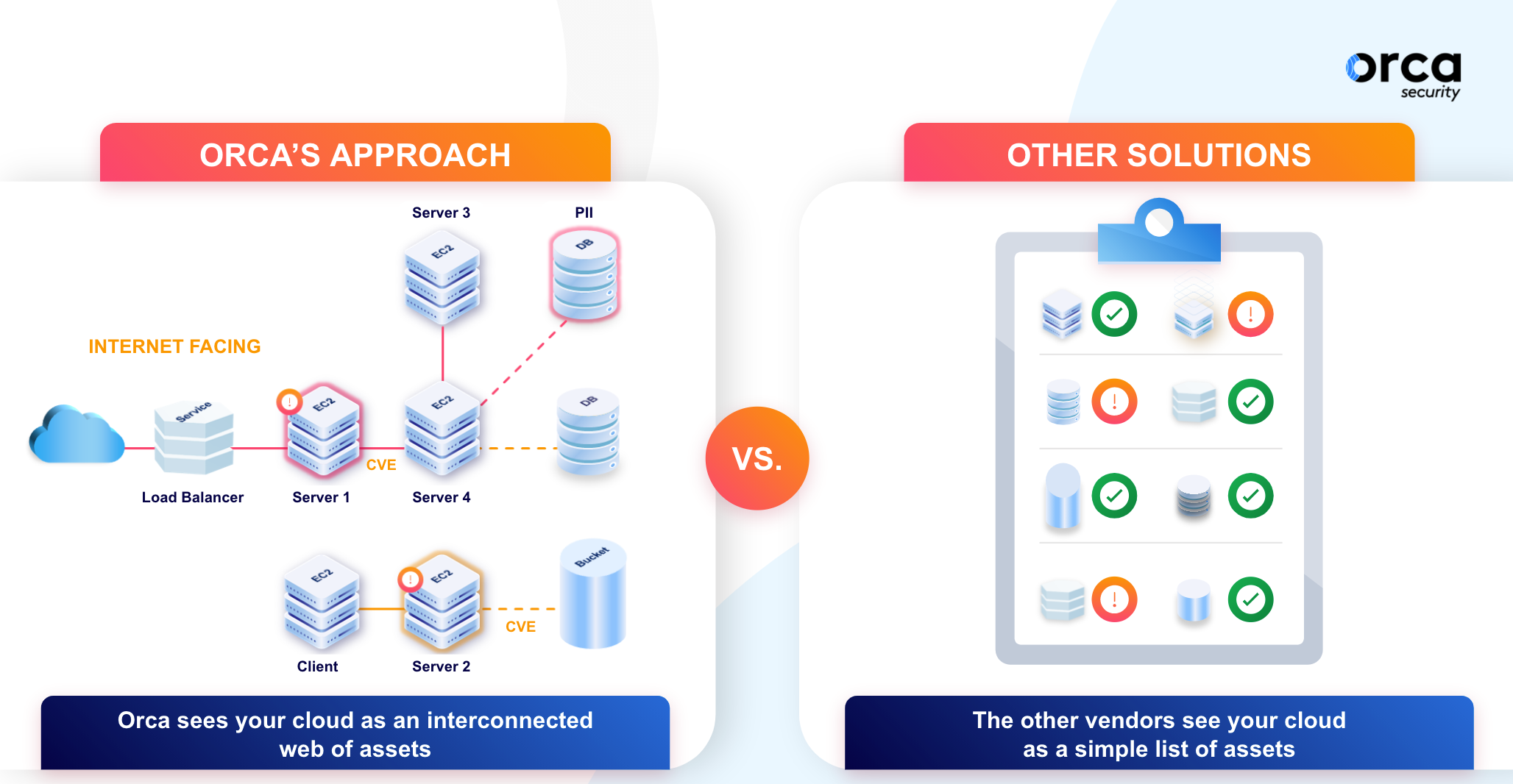
PAN Prisma Cloud is nothing more than a compilation of disparate tools based on a series of acquisitions – without any real integration. In sharp contrast, Orca’s Agentless Cloud Security Platform is purpose-built on a unified data model. We did this because we’re big believers in context. To prioritize risk, one must consider much more than the severity of the underlying security issue; you also need to consider its exposure and potential business impact.
Security practitioners who use Prisma need to do all the heavy lifting themselves to connect its findings across the suite and reach any meaningful conclusions. In a sample environment – one with an internet-exposed workload susceptible to a critical vulnerability running with overly permissive privileges – this shows up in Prisma as one of thousands of alerts, such as ‘critical’ vulnerabilities in blocked services, or overly permissive security groups not connected to anything. This is exactly what we highlighted in our videos that Palo Alto Networks’ lawyers demanded we remove from our website.
In contrast, Orca shows that same vulnerable, internet-facing workload as ‘imminent compromise,’ prioritizing it over the 99.9% of remaining alerts that aren’t exploitable.
Comprehensiveness
Delivered as SaaS and without consuming resources in customers’ production workloads, Orca runs a comprehensive set of checks. This includes a fully-featured malware scanner with heuristic scanning capabilities, lateral movement detection, authentication risks, and more. Prisma Defenders don’t possess such capabilities – likely due to its being resource-intensive, creating an unacceptable burden on production workloads its agents run on. Orca’s scanning from the side eliminates this concern while guaranteeing an always-up-to-date security platform.
In the interest of fairness, I directly address Palo Alto Networks’ claims in the following table:
| Palo Alto Networks Claim | Orca Security Rebuttal |
|---|---|
| “For example, in container environments, at least 50% of containers have a lifespan of less than 5 minutes. This frequent change is due to the high-release velocity of today’s DevOps teams – especially with containerized and Kubernetes environments. An agentless approach that only takes a snapshot of the infrastructure every 30 minutes will miss most runtime activity of these workloads (or about 50% of the operations).” | False. Don’t be confused between the short lifespan of containers and the timespan they reside in the scanned environment. The latter is measured in days, not minutes, and the two aren’t related at all.
Furthermore, Orca Security scans containers not only in runtime but also in CI/CD pipelines and image repositories. And it uses runtime scanning to guarantee 100% coverage, regardless of the method used to deploy or orchestrate the container into the environment. |
| Agentless solutions currently do not provide visibility or enforcement for DevOps teams during CI/CD phases. | False. The runtime scanning component (Orca = SideScanning; Prisma = agents) is completely agnostic to CI/CD scanning. |
| Agentless solutions don’t provide runtime protection capabilities | True, but this usually is the feature that provides the lowest amount of risk reduction.
Runtime protection sounds like a good silver bullet, but seasoned practitioners know it’s a ‘manner of last resort’ that can’t be relied upon. These are heuristic mechanisms prone to false positives and are almost never deployed in an active mode. Much more risk reduction can be achieved by having better hygiene, rather than by relying on heuristics to block attacks in real-time. |
So, Palo Alto Networks – while I naturally disagree with the statements in your blog post, I welcome the discussion. And I’d welcome the opportunity to accommodate an objective third-party, head-to-head product comparison of Orca Security vs your Prisma Cloud offering. Are you in?
For those that are interested in weighing in, I encourage you to join the conversation here: https://www.linkedin.com/posts/avishua_pan-prisma-cloud-customers-deserve-better-activity-6775106496301711361-cZLk





