We’re excited to present another head-to-head bout, this time featuring Orca Security and Qualys Cloud Platform. Our Cloud Security Punch-Out series comprises short-form comparison videos pitting Orca Security against some of the world’s largest IT security brands. Each match includes a quick scenario overview followed by a review and comparison of each solution. This punch-out was done on August 3, 2020.
Although Qualys has added some cloud security posture manager (CSPM) features the majority of the platform is experienced through a combination of workload agents (Qualys Cloud Agents) and scanners. Both attempt to assess vulnerabilities that exist within workloads. The Qualys Cloud Agent is installed inside each workload and runs alongside your applications, while scanners are network appliances that sit outside of network workloads and peer inside.
Our series lab represents a real-world cloud computing environment, but smaller. It’s a single AWS VPC with EC2 instances, a container, and a load balancer. We leverage security groups, route tables, and an internet gateway to route traffic to our public subnets and workloads. In addition, we have private subnets with workloads having no internet access. Outside of the VPC, there is a single S3 bucket.
Our customers tell us that modern cloud environments are born in unconventional ways, change rapidly, and are often managed differently across an organization. Leveraging a laborious, agent-based approach to workload security creates gaps in visibility and hence coverage. Given that, there is a stark contrast between Orca’s “one-and-done” deployment method and the agent-based, per-asset dependencies of Qualys Cloud Agents. So now having gone toe-to-toe with that product, the results speak for themselves.
Orca bobbed and weaved, providing complete coverage through contextually-generated security intelligence for virtual machines, containers, storage buckets, databases, and much more. At the cloud-plane level, Orca detected several insecure configurations and policies—such as a publicly readable (and writable!) AWS S3 bucket and IAM configurations, along with hazardous usage that Qualys Cloud Platform wasn’t able to detect.
Watch the blow-by-blow recap and the referee’s decision!
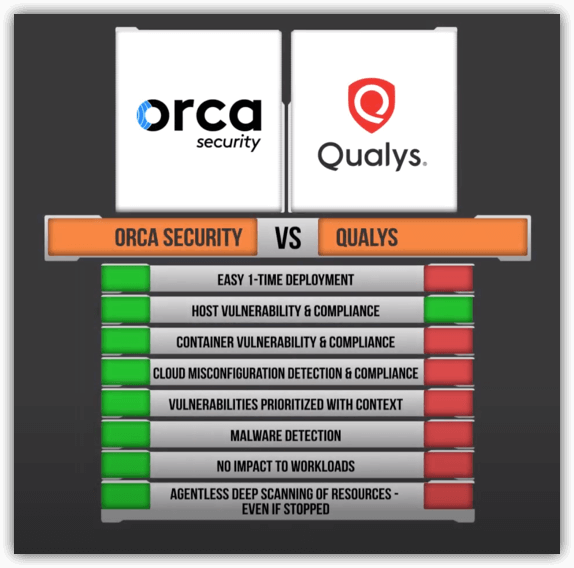
Spoiler Alert: Here’s the summary comparison table of Qualys Cloud Platform vs Orca Security