Recently, the continued rise of artificial intelligence has taken center stage in the media with the availability of new tools like ChatGPT. Here at Orca Security, as well as in the cybersecurity industry overall, we have been following closely–as well as exploring new use cases and opportunities to leverage AI within the Orca Cloud Security Platform.
What is ChatGPT?
ChatGPT is a new AI-powered chatbot developed by OpenAI, a company founded by industry leaders such as Sam Altman. The chatbot has gained popularity for its ability to understand human language and provide detailed answers to simple questions. It can complete tasks such as creating legal documents and writing code and blog pieces in response to user queries. ChatGPT stands out from other chatbots for its ability to remember previous user interactions and provide more personalized responses. The chatbot uses GPT3 Large Language Model developed by OpenAI and relies on a large text dataset from various sources. OpenAI has also developed other products such as Text-to-Image DALL-E-2 and it is backed by companies like Microsoft with $1 billion initial investment.
Why Should We Use GPT3?
At Orca Security we recently integrated GPT3 into our Cloud Security Platform to enhance the remediation steps provided to our customers for any cloud security risk. By fine-tuning these powerful language models with our own security data sets, we have been able to improve the detail and accuracy of our remediation steps – giving you a much better remediation plan and assisting you to optimally solve the issue as fast as possible.
You can use it to remediate findings in many ways, either via the command line, Infrastructure as Code (such as Terraform or Pulumi) or the console.
In addition, you can ask follow-up questions and fine-tune the remediation steps according to your specific needs.
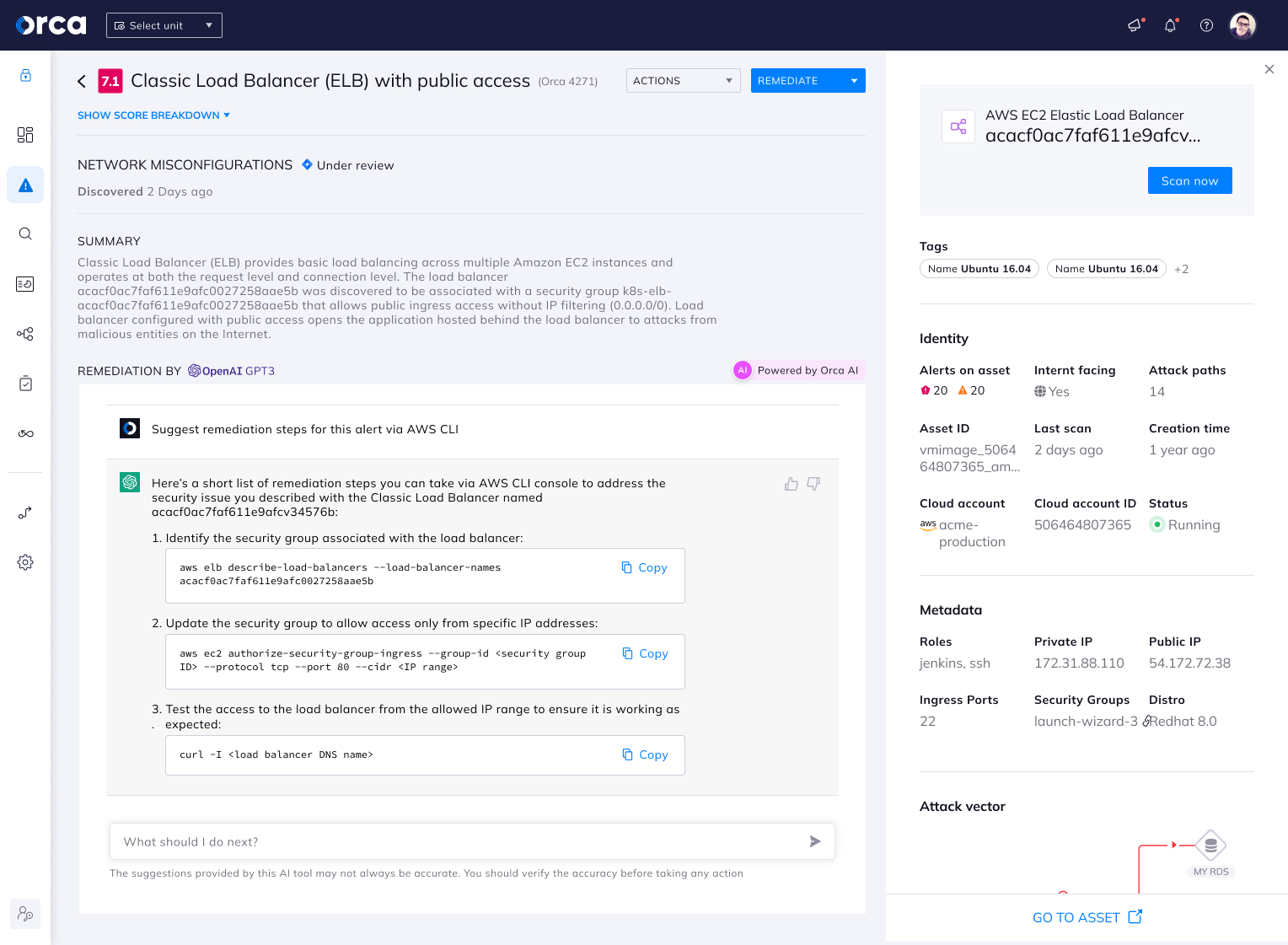
The integration of GPT3 into our cloud security platform is a prime example of our commitment to rapidly adopting cutting-edge technology that sets us apart from other solutions in the market.
How We Added GPT3 to the Orca Security Platform
We have leveraged the power of OpenAI’s GPT3 API, specifically the “Da-Vinci-03” series, to enhance our ability to generate contextual and accurate remediation plans for security alerts. We implemented a pipeline that takes in a security alert, which consists of basic information about the risk and its contextual environment such as affected assets, attack vectors, and potential impact. We then pre-process this data and feed it as input to GPT3, which generates a detailed explanation of the best and most practical ways to remediate the issue. Additionally, we can embed these remediation steps in tickets opened to DevOps or RND, such as Jira tickets, for easy tracking and implementation.
To ensure data privacy and security, we added several layers of filtering and sanitation to the input data, so that only the necessary information is passed to the GPT3 model.
While GPT3 is a highly advanced AI model, it is important to note that any interaction with an AI model carries an element of uncertainty. Despite this, we believe that the benefits of utilizing GPT3’s natural language generation capabilities outweigh any potential risks, and have seen significant improvements in the efficiency and effectiveness of our remediation efforts as a result of this integration.
Get Started With GPT3 in Orca Security
We adopted cutting-edge technology by integrating OpenAI’s GPT3 API to enhance our ability to generate contextual and accurate remediation plans for security alerts. We have built a pipeline that takes in security alerts and pre-processes the data, passing it to GPT3 which generates detailed explanations of the best and most practical ways to remediate the issues. This implementation allows us to offer a one-of-a-kind remediation experience for our customer’s cloud security risks, by generating high-quality remediation plans quickly.
Using GPT3 for alert remediation
To learn more about how the Orca Security Platform can benefit your team, you can sign up for a demo here.






