With 84% of vulnerable and exposed TeamCity servers likely already compromised, the recent issue in JetBrains’ TeamCity illustrates how a vulnerability in the infrastructure used to build and deliver applications to the cloud can quickly open up far reaching supply chain attacks that could potentially spread to many other organizations. Supply chain attacks are particularly attractive for bad actors since with only one breach, they are able to impact and penetrate many other environments and potentially reap far greater rewards than if they were to breach each organization individually.
The scale of the problem seems not to be sniffed at. We found that nearly half (46%) of the 885 publicly accessible TeamCity servers we identified using Shodan.io were vulnerable.
In this article, we will explore the specifics of CVE-2024-27198, show how an adversary might exploit such a problem in a few steps, and discuss how Orca Security can help organizations find and address similar risks.
What is TeamCity?
TeamCity is a popular Continuous Integration/Continuous Delivery (CI/CD) platform from the company JetBrains, and is used by DevOps teams to automate building, testing, and deploying application code. TeamCity was first released in 2006. Many popular games, websites, and banking systems are built with TeamCity.
JetBrains TeamCity vulnerability (CVE-2024-27198)
CVE-2024-27198 is an authentication bypass vulnerability in TeamCity that was published on March 4th, and allows an unauthenticated attacker to gain administrative access to a self-hosted TeamCity instance. The vulnerability has a CVSS score of 9.8, indicating that it is critical, and it is currently being widely exploited, with some estimates indicating that 84% of publicly accessible and vulnerable instances may have been compromised at one point.The vulnerability has an Exploit Prediction Scoring System (EPSS) score in the 97th percentile, indicating that it’s a highly critical CVE and only 3% of other CVEs have a higher EPSS score.
When exploited, this vulnerability allows an attacker to take any action available to an administrator, including creating new administrative users, accessing and modifying pipelines that build and deliver applications, and executing code remotely. Such an exploit raises the question of supply chain attacks, where an attacker is able to modify the applications being deployed, and ultimately impact the downstream customers and partners of the organization compromised.
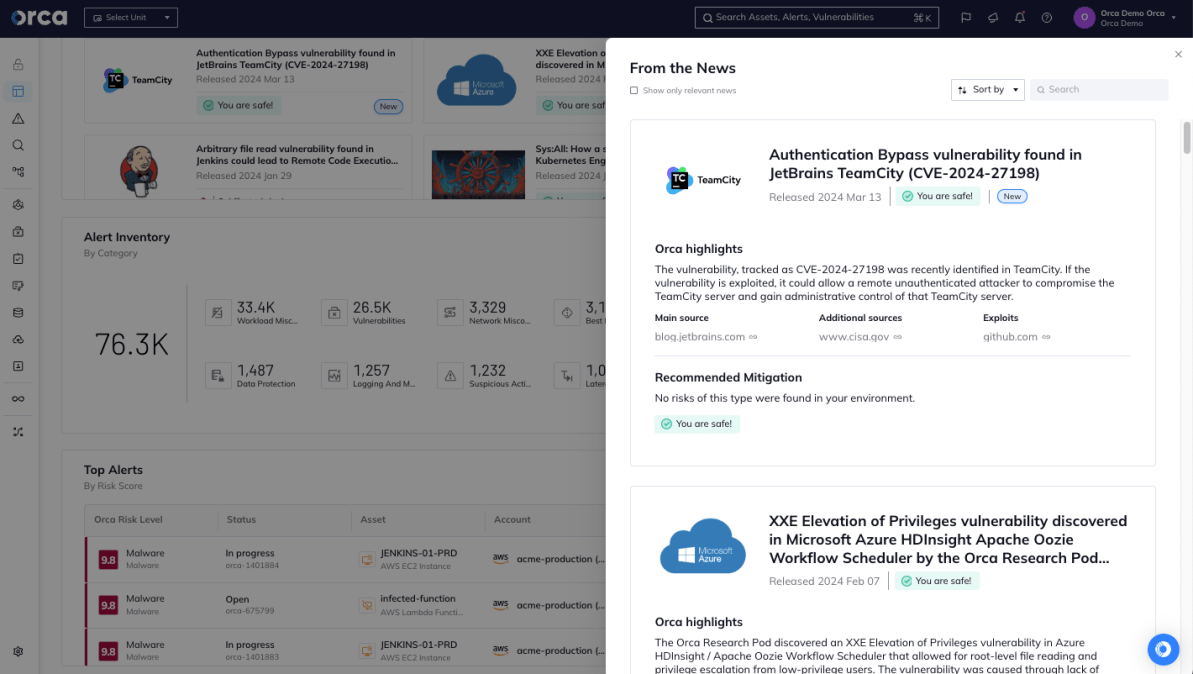
The Orca Cloud Security Platform notifies about breaking vulnerabilities and shows if you are vulnerable
TeamCity vulnerability exploitation
The TeamCity CI/CD server vulnerability in versions prior to 2023.11.4, allows attackers to bypass authentication by crafting a URL that leads the server to treat the session as authenticated. The attackers craft a URL targeting an unauthenticated resource that generates a 404 response, which can be achieved by requesting a non-existent resource on the server, and append a query parameter that the server interprets as a request for an authenticated resource. Specifically, the attacker uses a URL like teamcity-server:8111/hax?jsp=/app/rest/server;.jsp, where teamcity-server is a placeholder for any TeamCity resource. This requested endpoint will return the current server version information.
The core issue lies in how the BaseController class within the web-openapi.jar library processes requests. If a request isn’t redirected (no HTTP 302 redirect occurs), it calls updateViewIfRequestHasJspParameter. This function, upon encountering a request path not ending with .jsp (like one causing a 404 error), wrongfully processes the jsp parameter, allowing the request to access authenticated endpoints. Consequently, attackers manipulate this logic flaw to redirect requests to internal endpoints, thereby sidestepping authentication and gaining unauthorized administrative access. This exploitation reveals a critical lapse in the server’s request validation logic, enabling unauthorized access to sensitive administrative functionalities.
TeamCity vulnerability security implications
By successfully executing this exploit, attackers bypass the authentication mechanism of the TeamCity server, gaining unauthorized access. This breach allows them to explore and manipulate the server’s administrative functionalities. They can create new user accounts with elevated privileges alter build configurations, and access sensitive project data. The extent of the exploit’s impact can be vast, ranging from stealing proprietary code to injecting malicious code into the build pipeline, potentially leading to a widespread compromise of the software being developed and deployed through the TeamCity server. This unauthorized access and control over the CI/CD process not only jeopardizes the security and integrity of the application codebase but also exposes all associated systems and data to significant risk.
Risk management challenges for cloud-hosted CI/CD pipelines
As shown, an authentication bypass vulnerability like this one could easily place not just the CI/CD server itself but the entire supply chain that it supports at risk. Organizations that host pipelines like this in the public cloud may find additional complications in identifying and mitigating risk; for example, individual teams may self-provision and run these servers, making it harder to identify all assets at risk. Such servers may be exposed to the outside world, perhaps for interoperability with on-prem or cross-cloud processes. Finally, when a new vulnerability is found, it is difficult to identify at-risk installations and update them without both an inventory of the servers themselves and intelligence on what version(s) are deployed.
How the Orca Cloud Security Platform can help
Orca Security provides security teams with the tools necessary to identify all deployed CI/CD pipelines in the estate. This includes not just TeamCity but other self-hosted platforms such as Jenkins and ArgoCD. Organizations get complete coverage, showing them what is deployed and where, regardless of whether it is centrally managed or deployed by smaller teams.
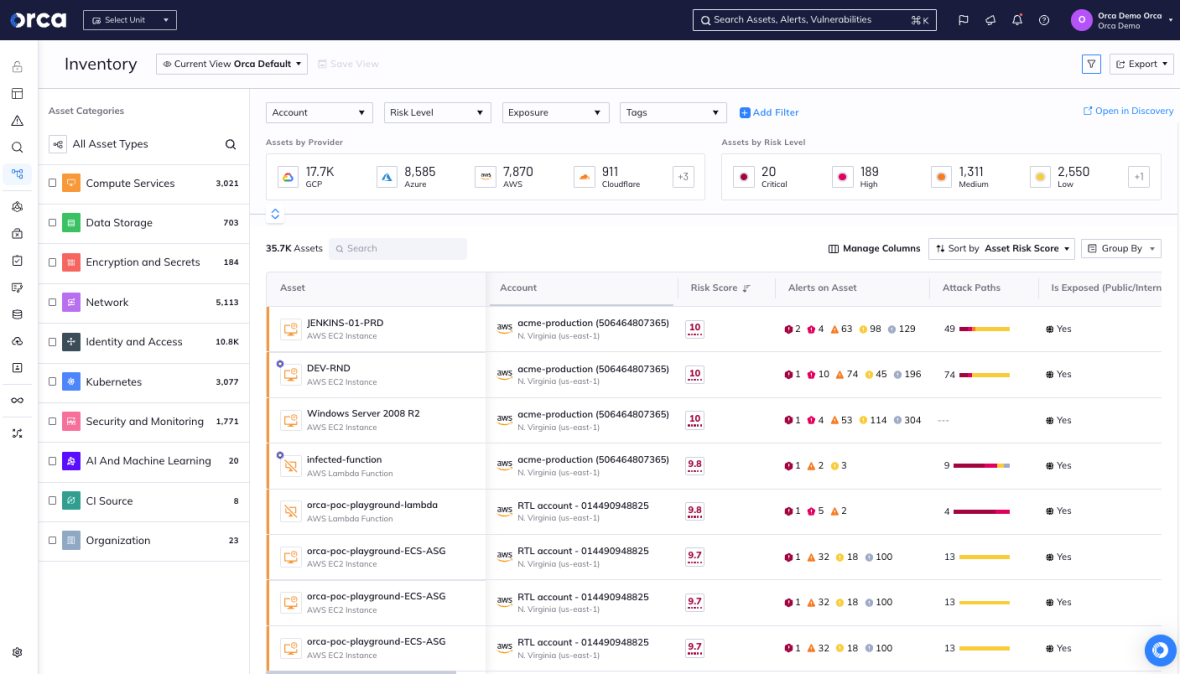
Orca provides a complete inventory of cloud assets, including CI/CD pipelines
Orca’s inventory provides great detail on the resources in your cloud, including the exact software version installed, network exposure, identified vulnerabilities, any suspicious activity, and other risks found on the asset.
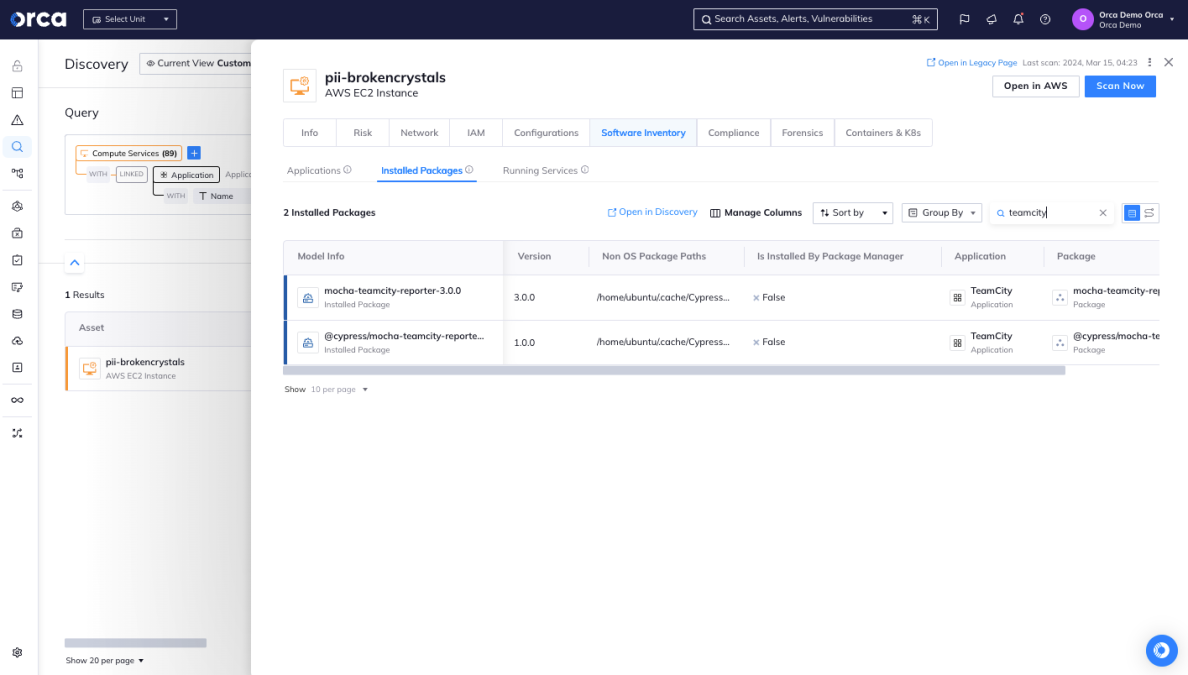
Orca shows where you have TeamCity installed along with the version
Orca will also calculate the exposure of these services so that vulnerable deployments can be identified. Not only will alerts be generated to show that the vulnerabilities are present, they will also be dynamically contextualized to show which assets are most at risk based on their exposure to the outside world, whether privileged identities are used by the workload, whether there is access to sensitive data, and other factors. This information helps teams fix their most critical risks first, which is essential when new vulnerabilities are discovered that are already being exploited by bad actors.
Learn More
Orca Security is trusted by hundreds of organizations and provides comprehensive, AI-driven cloud security that is easy to operate and brings value from day one. After a simple 30-minute deployment, Orca will start scanning and within hours show you all the risks in your cloud workloads, configurations, and identities and which ones are the most critical – all from a single platform. If you would like to learn more about the Orca Platform, schedule a 1:1 personalized demo with one of our experts.






