In the world of software development, automation is a huge time-saver, and GitHub Actions is one of the best tools for the job. GitHub Actions allow developers to automate, customize, and execute their software development workflows right in their GitHub repository. You can set up continuous integration and continuous delivery (CI/CD) pipelines, run tests, deploy applications, and much more. Essentially, it’s a powerful way to streamline your development process, making it faster and more efficient.
However, this power can be exploited by bad actors with a practice called typosquatting. Typosquatting involves creating malicious actions with similar names to popular ones. If developers make a typo in their GitHub action that matches a typosquatter’s action, applications could be made to run malicious code without the developer even realizing. Typosquatting is basically similar to a spider waiting in its web.
In this blog, we explain how we managed to leverage typosquatting in GitHub Actions and got several applications with inadvertent typos to run our ‘fake’ action. If we had bad intentions, these mistakenly triggered actions could have included malicious code, for instance installing malware, stealing secrets, or making covert changes to code.
With this blog we aim to increase awareness of this issue, and also explain how to protect against this risk to ensure you do not fall into a typosquatter’s trap.
Executive summary
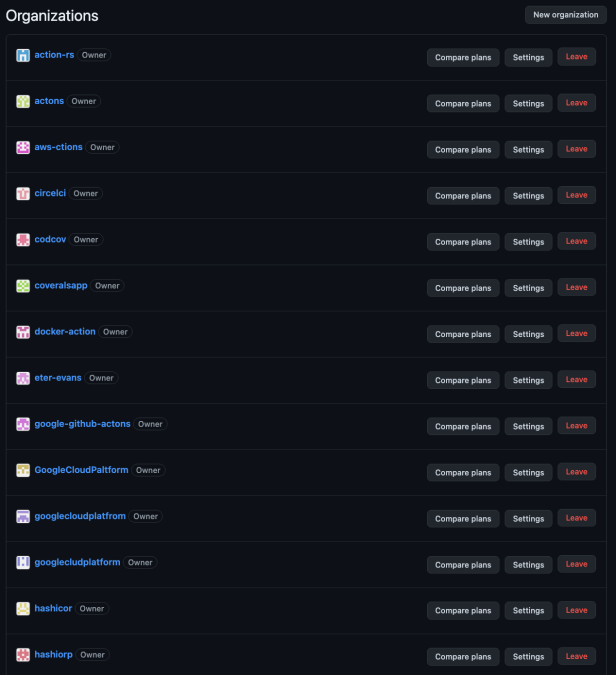
- The Orca Research Pod developed a PoC for setting typosquatting ‘traps’ in GitHub Actions. For the PoC, we created 14 organizations with names that could be typos of popular actions; such as circelci, actons, docker-action, google-github-actons.
- Then we forked the repositories so that when someone made these typos, they would still get the desired response instead of an error, and be unaware that anything was amiss. Bad actors could also easily make modifications and insert malicious code.
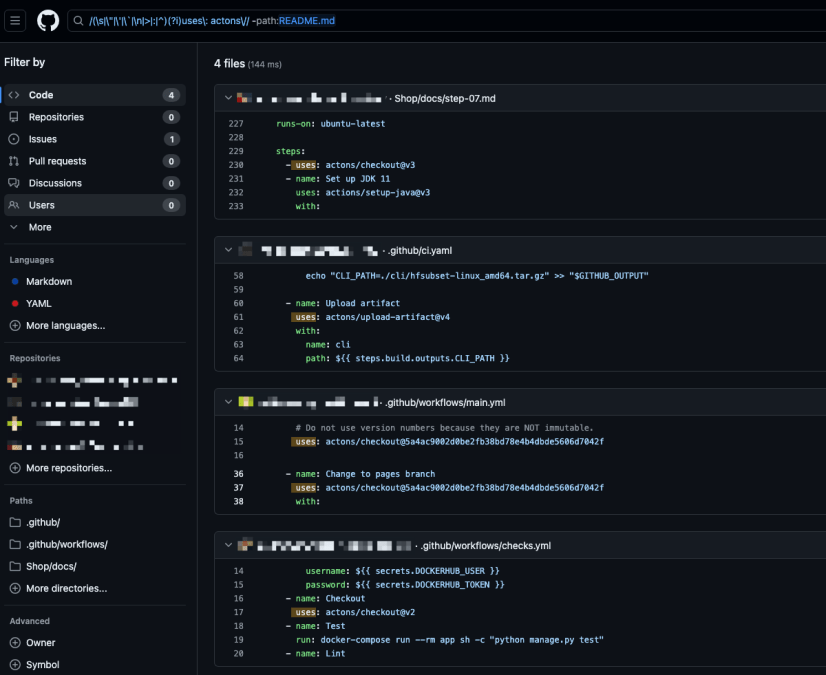
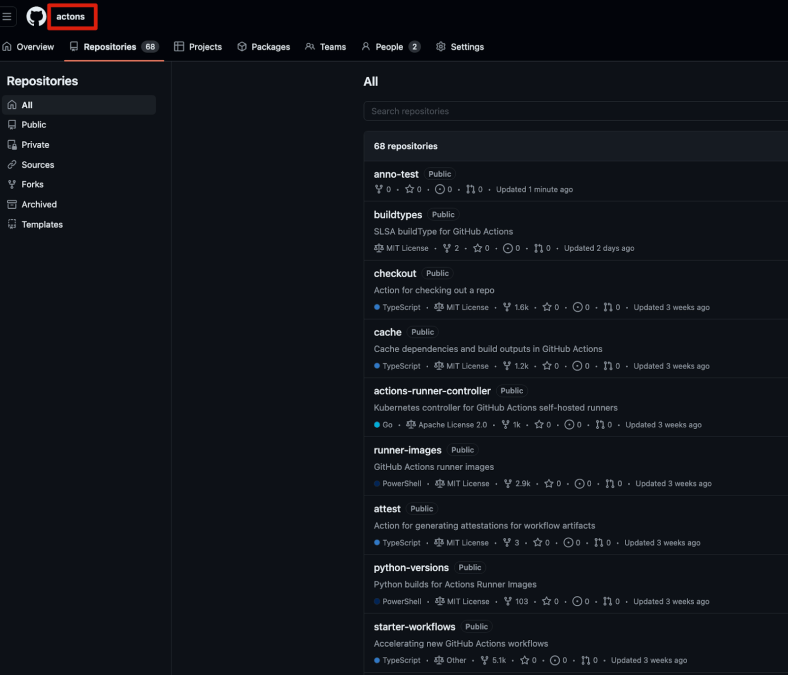
- We had the most results on our organization named ‘actons’, with four public repositories already referencing it. Within 2 months, the number increased to twelve, demonstrating how easily developers can fall victim to typosquatting.
- Although the number may not seem that high, these are only the public repositories we can search for and there could be multiple more private ones, with numbers increasing over time. It’s also important to point out that this means that an attacker would have had the ability to inject malicious code into these twelve applications, potentially causing further supply chain attacks. Also, the more fake organizations are created and the longer the wait time, the more organizations will become victims.
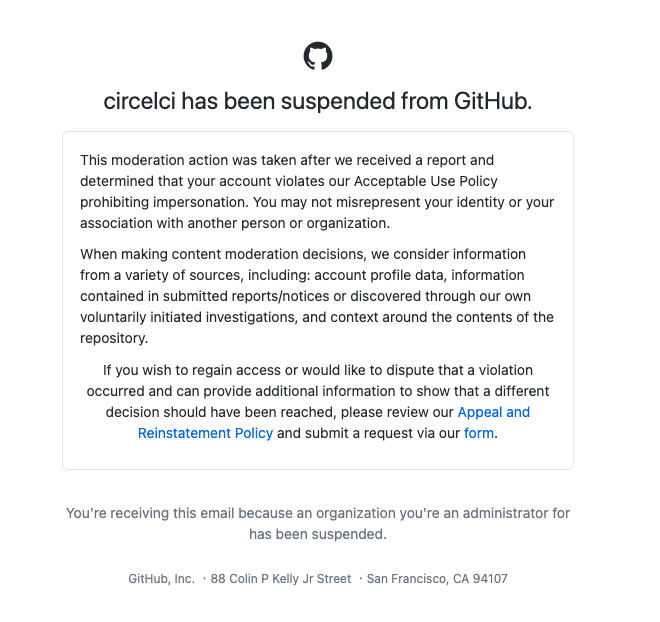
- After 3 months, GitHub flagged and suspended only one of the fake organizations (circelci), probably after someone submitted a report. The other 13 organizations are still running.
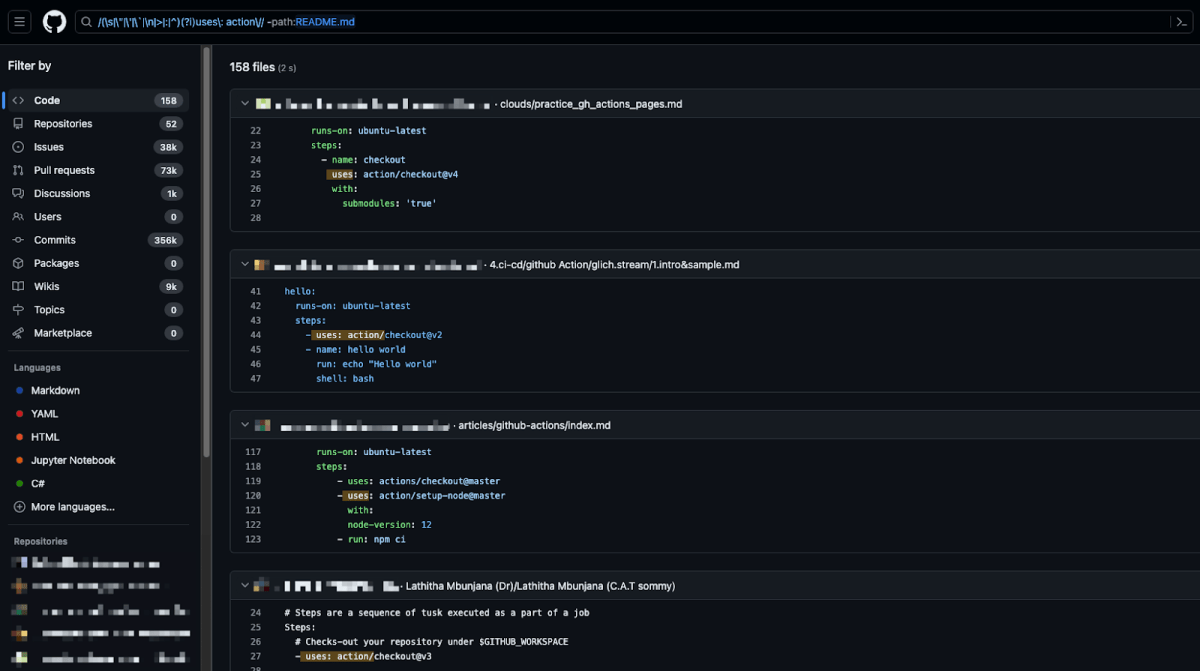
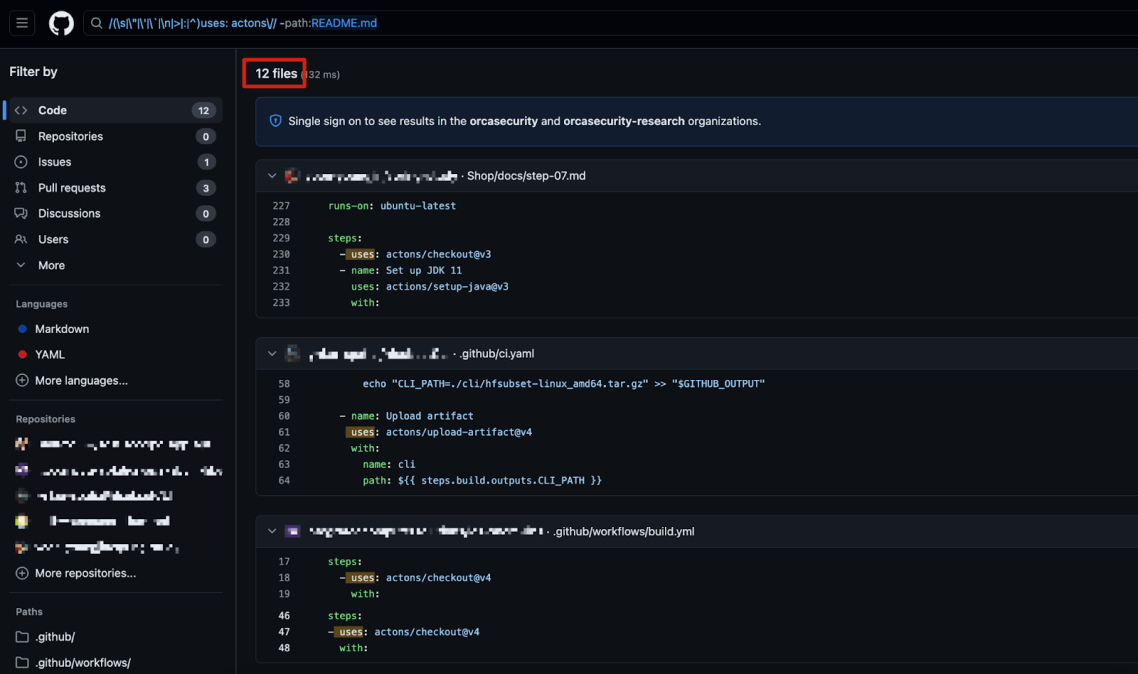
- Before we even started our PoC, a quick Github search revealed that there were 158 files calling the ‘action’ organization instead of ‘actions’, which is the intended one. After three months, this increased to 194.
- The experiment highlighted how easy it is for attackers to exploit typosquatting in GitHub Actions and the importance of vigilance and implementing best practices in preventing such attacks.
The power of GitHub Actions
GitHub Actions has rapidly become an indispensable tool for developers. How widely used is it? According to GitHub’s statistics, millions of workflows are run daily, automating tasks from CI/CD to code reviews and issue triaging.
You can grasp the power of GitHub Actions by looking at the sheer number of workflows and popular actions in use, and the thousands of actions available in the GitHub Marketplace.
For example, the actions/checkout action has been used millions of times, as are many others like upload-artifact, setup-python, and setup-node.
The dangers of GitHub Actions abuse
This naturally brings up an important question: Have you ever considered whether GitHub Actions are 100% safe to use? Chances are, you probably haven’t given it much thought. But even if you have, determining the legitimacy of an action can be challenging, especially when using a known one.
The reality is that anyone can publish a GitHub Action, simply creating a user account with a temporary email is enough to get started. This openness means that potentially malicious actions can find their way into the Marketplace.
Actions can do a lot more than just automate trivial tasks. They run within the context of your repository and generally have access to its code, files, and any secrets or configuration details explicitly provided to them. This level of access can be risky if an action is malicious – it could install malware, steal secrets, or make covert changes to your code. The implications of such access can be devastating. Imagine an action that exfiltrates sensitive information or modifies code to introduce subtle bugs or backdoors, potentially affecting all future builds and deployments.
In fact, a compromised action can even leverage your GitHub credentials to push malicious changes to other repositories within your organization, amplifying the damage across multiple projects.
What is typosquatting?
Typosquatting is a malicious practice where attackers can create websites, repositories, or packages with names that are very similar to popular ones, hoping that users will make a typographical error and inadvertently visit the malicious site or use the malicious package. This technique exploits common typos and the assumption that many users will not notice the slight difference in names.
What is typosquatting in GitHub Actions?
In the context of GitHub Actions, typosquatting involves attackers creating organizations and repositories with names that closely resemble popular or widely-used GitHub Actions. The goal is to trick developers into using the malicious action by exploiting common typographical errors.
In a normal scenario where there is a typo when calling an action, the workflow will fail and the developer will notice there is an issue and fix it. However if a malicious action exists with the misspelled name being called – the workflow will function without any issues.
Imagine you’re setting up a GitHub Action for your project and accidentally type “uses: action/checkout” instead of “uses: actions/checkout”, which is the actual GitHub actions organization. If an attacker has created an organization with that typo and the repository “checkout”, your workflow will run their action instead of the legitimate one. This simple mistake can have serious consequences.
In fact, we can already see with a quick Github search that there are 158 files calling the ‘action’ organization instead of the ‘actions’, meaning these repositories are at risk of being exploited. It’s also important to note that these are only the public repositories that we are able to search. There could be many other private repositories doing the same.
There are multiple other use cases we checked, for example the ‘actons’ organization, which was also one we used as part of our experiment.
The risks of typosquatting
When a typosquatting attack is successful, it can have severe consequences:
- Unauthorized access: Malicious actions can steal secrets or tokens from your repository, giving attackers access to critical infrastructure and data.
- Data theft: Attackers can exfiltrate sensitive data, including code, personal information, and confidential business data.
- System compromise: Malicious actions can execute harmful commands, potentially compromising your entire system, introducing vulnerabilities, or spreading malware.
- Reputation damage: A security breach can damage your project’s reputation, causing users and contributors to lose trust.
Real-world experiment: typosquatting in the wild
To understand the potential impact of typosquatting, we conducted an experiment. Here’s how we executed our typosquatting PoC exploit:
- Identify popular actions: Look for widely used GitHub Actions and the use of similarly named actions with a typo.
- Create lookalike organizations/repositories: Create organizations with names that are very similar to these popular actions and fork the relevant repositories (the actions themselves).
- Modify code: Modify the source code of the original action (in our exercise we did not make any modifications, but a bad actor could easily insert malicious code).
- Wait for mistakes: Wait for developers to make typos and reference our actions in their workflows by mistake.
First, we searched in Github for already existing miswritten actions in workflows which might be popular. These simple typos can redirect workflows to malicious actions without the developers realizing it.
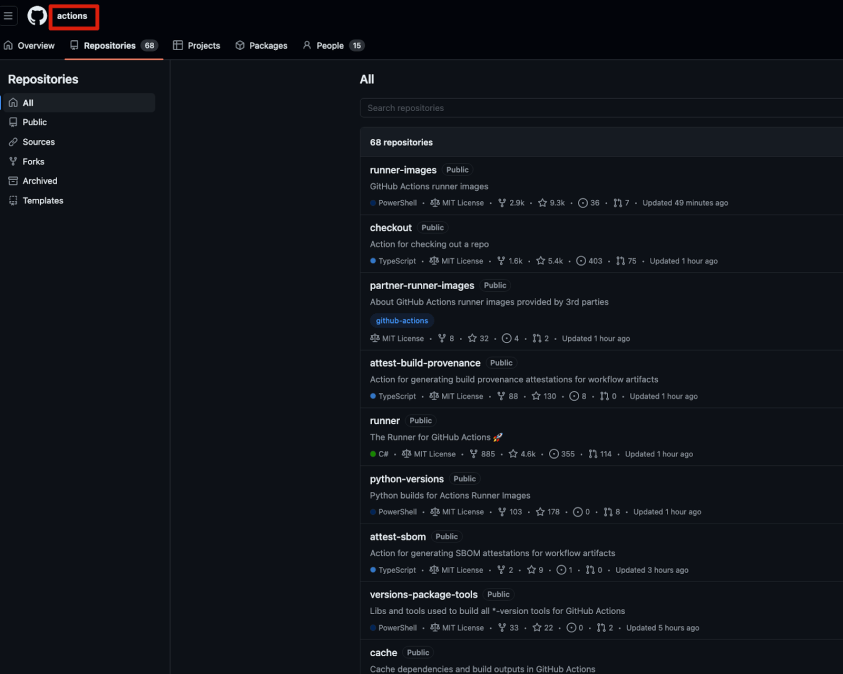
Next, we created multiple organizations with names closely resembling the well-known projects and forked all their repositories related to GitHub Actions.
For instance, we created organizations like “action-rs”, ‘conversalapp’ and such, and populated them with the repositories relevant for their actions, by forking them from the original organization. This setup ensured that any developer who made a typo when referencing these actions would not receive an error, making it less likely for them to notice the mistake.
vs.
In the hands of an attacker, they could potentially steal source code and other sensitive information and even change the code of the action and have it run as part of the victim’s workflow.
This experiment highlights how easy it is for attackers to exploit typosquatting in GitHub Actions and the importance of vigilance and best practices in preventing such attacks.
Conclusion
Although we were only running a Proof of Concept exploit and as such not running any actual code on the ‘tricked’ GitHub environments, the results of the experiment were still revealing. For example, initially, only four public repositories referenced our maliciously named organization ‘actons’. However, over a short amount of time, that number increased to twelve, demonstrating how easily developers unknowingly fall victim to typosquatting and never receive any error to alert them to this.
The actual problem is even more concerning because here we are only highlighting what happens in public repositories. The impact on private repositories, where the same typos could be leading to serious security breaches, remains unknown. This highlights the significant risks associated with typosquatting in GitHub Actions, where malicious code could be running undetected, potentially compromising entire CI/CD pipelines and leaking sensitive data.
Eventually, it took 3 months for GitHub to flag and suspend only 1 of our fake organizations (circelci), probably due to someone submitting a report. The other 13 are still up and running, continuing to catch typos in called actions from unsuspecting developers.
When digging deeper into the typosquatting issue in Github, we found another organization who had a similar idea as ours: ‘aws-action’. They even mention in their description that this is used for typosquatting research and don’t use it.
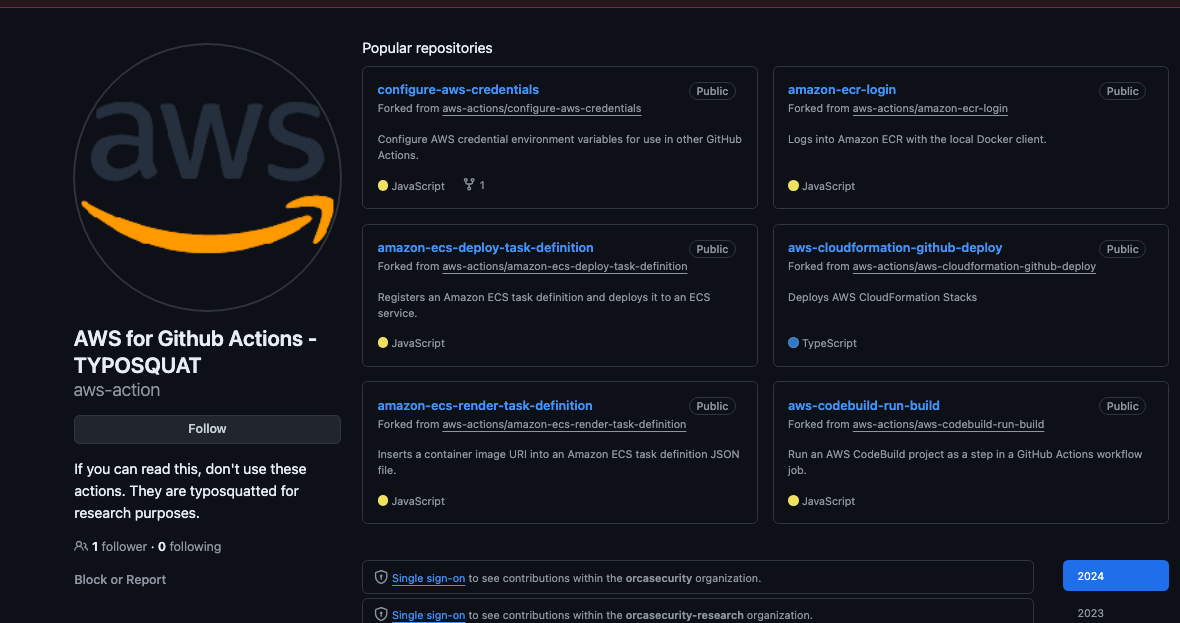
Even though they had this warning, we can see there are currently 40 public uses of this organization that are probably unaware of it.
Moreover, looking back at the uses for the ‘action’ organization we mentioned in the beginning, we can see the uses increased over time as well, with now 194 uses in total:
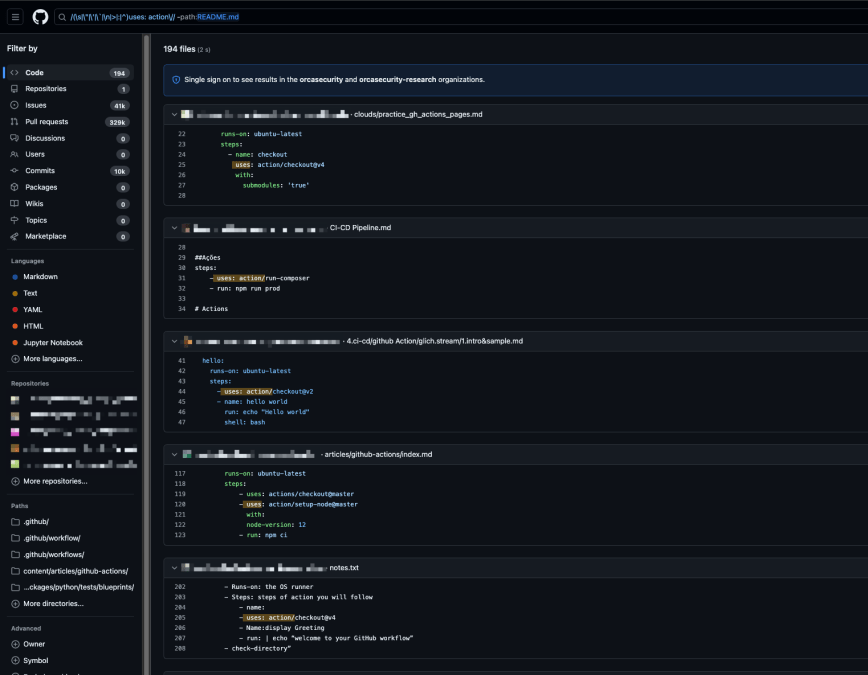
This really highlights that over time these numbers will just continue to grow and nothing stops an attacker from sitting and waiting, and eventually changing the code to something malicious.
How to protect against typosquatting in GitHub Actions
While GitHub has measures in place to review and monitor actions, the responsibility of ensuring the safety of workflows is ultimately that of the developer. Always verify the source and reviews of actions before integrating them into your workflows, and consider only using actions from verified creators and organizations.
Protecting your projects from typosquatting involves a mix of vigilance and best practices:
- Double-check names: Always double-check actions and their names before using them in your workflows to ensure you’re referencing the correct organization.
- Use trusted sources: Stick to actions from verified creators or those with a high number of stars and forks.
- Lock down dependencies: Use specific version tags or commit SHAs to ensure you’re using a known-good version of an action.
- Automate security checks: Integrate security tools that can scan your workflows for potential issues, including typosquatting risks.
- Educate your team: Make sure everyone on your team is aware of the risks of typosquatting and how to avoid them.
By taking these precautions, you can leverage the full power of GitHub Actions while keeping your projects safe from typosquatting attacks. Automation can greatly enhance your development process, and with a bit of caution, it can remain secure and reliable.
About the Orca Research Pod
The Orca Research Pod is a group of cloud security researchers that discovers and analyzes cloud risks and vulnerabilities to strengthen the Orca platform and promote cloud security best practices. To date, the Orca research team has discovered and helped resolve 25+ vulnerabilities in cloud provider platforms to help support a safe and secure cloud infrastructure.
The Orca Cloud Security Platform
Orca’s agentless-first Cloud Security Platform connects to your environment in minutes and provides 100% visibility of all your assets on AWS, Azure, Google Cloud, Kubernetes, and more. Orca detects, prioritizes, and helps remediate cloud risks across every layer of your cloud estate, including vulnerabilities, malware, misconfigurations, lateral movement risk, API risks, sensitive data at risk, weak and leaked passwords, and overly permissive identities.
Schedule a 1:1 demo to see how Orca can help you uplevel your cloud security.







