7 Areas of Focus for Federal Agencies, Sub-Agencies, and Contractors
On June 23rd 2022, the Cybersecurity and Infrastructure Security Agency (CISA) released the Cloud Security Technical Reference Architecture with co-authors from the United States Digital Service and Federal Risk and Authorization Management Program (FedRAMP). The publication addresses the on-going challenges federal agencies are facing with cloud security and supply chain contractors.
The report includes guidance for “new leadership, evolving threats, and changing requirements and technologies” for Federal agencies and departments and their contractors.
Key areas in the report cover how Federal agencies and their suppliers can avoid preventable cloud breaches that have downstream impacts on local communities and citizens. To effectively manage the risks of threat actors and nation-states that constantly scan the internet for vulnerabilities and easy targets, agencies need to plan ahead for cloud security before migrating assets to the cloud. When cloud security is built into the design architecture before any cloud migration occurs, Federal agencies, sub-agencies and contractors can proactively manage known cloud risks and avoid post-migration exposures.
The publication also addresses topics beyond cloud migration, including shared services, cloud security strategies, and Cloud Security Posture Management (CSPM).
Let’s dive into why this publication is needed now, seven key recommendations, and next steps Federal agencies can take now.
What is CISA’s Cloud Security Technical Reference Architecture?
A moderately quick read of 60+ pages, CISA’s Cloud Security Technical Reference Architecture report was released on June 23, 2022, providing the first high-level guidance from CISA to government agencies, their sub-agencies, and contractors on best practices when migrating to the cloud.
As the private sector has raced to the cloud, government entities have been more methodical. That has changed recently, as government buyers have more purchasing options for security technologies and are seeking to shore up security, especially in the cloud. Therefore, the government is setting standards for government agencies and contractors purchasing cloud services and security solutions.
The most important goal this publication can meet is guiding Federal Government agencies on how to best adopt cloud technology. This guide enables public sector leaders to budget and build cloud security into cloud migration projects proactively.
Why is CISA releasing the Cloud Security Technical Reference Architecture now?
As the move to the cloud has accelerated again in 2022, buoyed by return-to-work and post-pandemic market influences, government agencies and their supply chains need more federal guidance to secure sensitive data and intellectual property in their cloud ecosystems. Considering the elasticity, extensibility, and access to data that makes the cloud advantageous, that same data, if not secured correctly, is vulnerable to threat actors, including those colluding with and representing nation-states that are active in global cyber warfare campaigns.
Recent global security incidents, from Russia, Iran, and others, have highlighted the need for an international response from allied countries to address these global threats together. Echoing the need for governments to do more to improve security, security agencies from the U.S., UK, Australia, Israel, EU, and others, have proclaimed nation-state threats are posing unprecedented risks to international security in 2022.
In July 2022, the FBI and MI5 issued an unprecedented joint warning about the threat of IP theft by China. During an address to business leaders in London, FBI Director Christopher Wray said that China’s hacking program is “bigger than that of every other major country combined” and that the Chinese government is “set on stealing your technology.” Wray elaborated, “Just as in Russia, Western investments built over years could become hostage capital stranded, supply chains and relationships disrupted.”
As a subsequent response, this report provides real cybersecurity solutions for U.S. Federal agencies, sub-agencies, and contractors migrating to the cloud. With 90 percent of U.S. critical infrastructure reliant upon the private sector, it’s critical for the Federal government to take steps to make improvements. These recommendations offer strategies to improve partnerships with Federal sub-agencies, and their supply chains, to protect and defend data, users, and constituents from lost or exploited data. Federal agencies can use this report to build security operations into their cloud environments now, in anticipation that future guidance from CISA will expand upon the following seven key areas.
Shared Cloud Services Layer
One of the more robust sections in CISA’s Cloud Security Technical Reference Architecture publication revolves around the Shared Services Layer. This section includes descriptions on cloud service models, FedRAMP roles and responsibilities and special security considerations required by FedRAMP on continuous monitoring, incident response and the authorization boundary.
A key pillar in the Shared Services Layer is understanding the shared security responsibilities of the differing cloud services offerings. While similar to the shared responsibility model the major cloud service providers (CSPs) use for customers, CISA outlines those shared responsibilities by where digital assets reside and who’s responsible for those assets – whether they are stored on-premise or with CSPs, as illustrated in CISA’s Shared Security Model shown below.
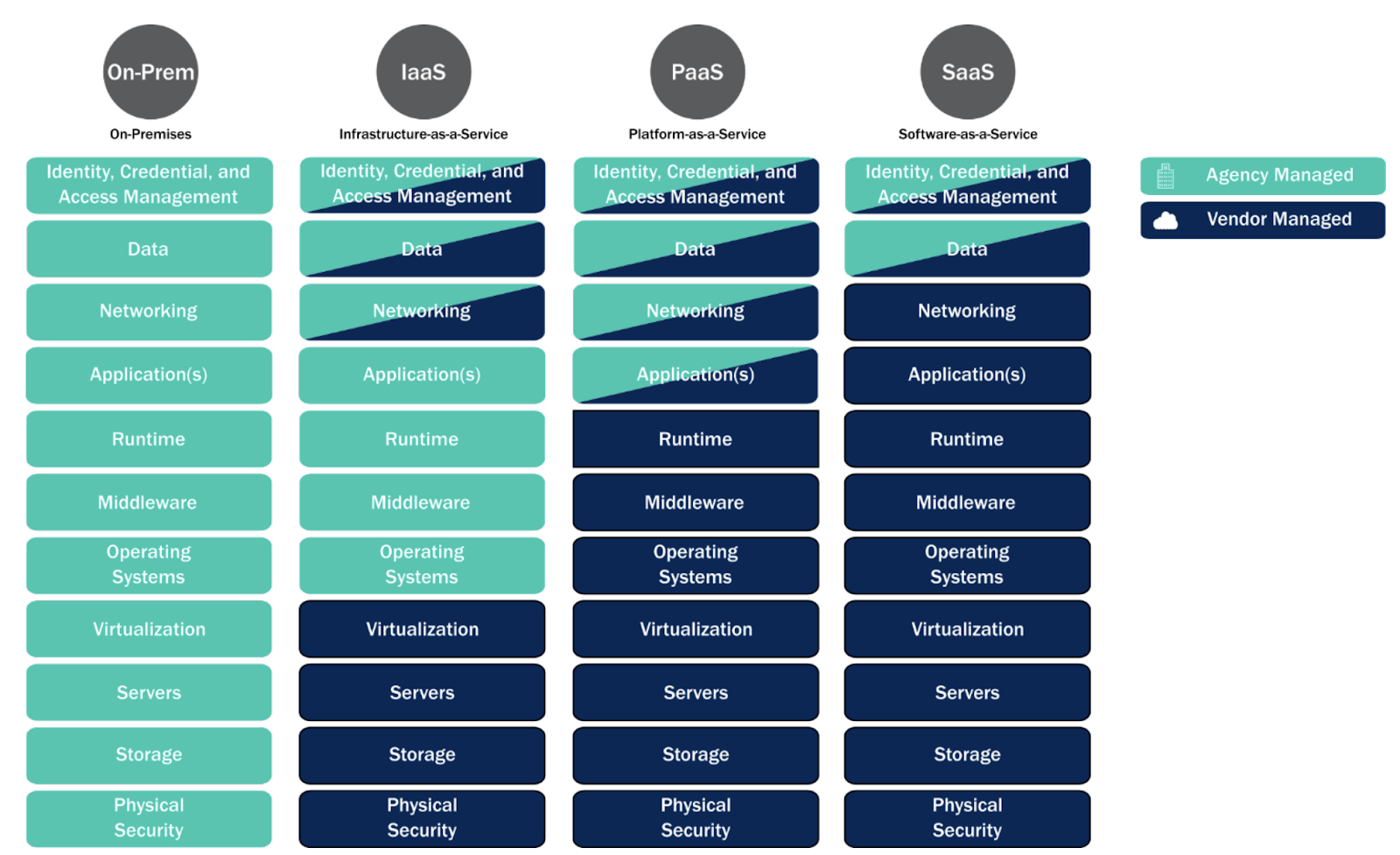
Figure 1: CISA’s Shared Security Model (source: CISA Cloud Security TRA report pg. 11)
It’s important to note that Software as a Service (SaaS) vendors carry much of the responsibility for the security of their environment and the services they’re providing. When consuming SaaS services, organizations and agencies should ensure they understand where their responsibilities end and the respective CSP’s responsibilities begin.
Sub-Agency Service Consumption of the SaaS Service
Another interesting topic in this section is sub-agency service consumption of the SaaS service. The guidance covers how that sub-agency can inherit the security controls included in the SaaS offering, however, the sub-agency is still responsible for ensuring alignment with areas like; incident response (IR), log management, identity and access controls (IAM), and configuration management. This last part is similar to if the sub-agency were procuring the CSP service itself.
When the sub-agency does not take into consideration their portion of shared responsibility for IR, log management, IAM controls, and configuration management. etc., they risk being non-compliant with Agency policy and potentially with regulatory requirements. Additionally, if they are not managing their portion of responsibilities under their Agency head, they could be at risk of a breach. This perspective should also include supply chain risks and be part of a holistic governance program.
Multi-Cloud Security and Log Management
Another core component to consider within this section centers on multi-cloud security. CISA recommends that an agency or organization consuming multi-cloud services should take steps to enable visibility of security across this type of ecosystem.
Building a program that enables a holistic view with complete visibility of the multi-cloud ecosystem allows an organization to achieve two goals:
- Maintenance of a coherent security posture, allowing for consistent response and remediation to vulnerabilities and events that may pose risk to their mission data and security posture;
- Enforce organizations and agencies to align with the OMB Memorandum (M)-21-31 for log management
The log management requirement in the OMB Memorandum is critical because it covers the organization’s responsibility within the Shared Services Layer. Log management offers organizations the ability to implement continuous network and cloud monitoring – both of which are critical components to gaining FedRAMP approval and maintaining authorization.
Secure Design for Cloud Migration
The Cloud Migration section of CISA’s Cloud Security TRA guidance also deserves attention – as it addresses several priority considerations agencies and organizations should take when migrating, moving, or expanding their cloud estates.
For example, when an organization or agency is designing software for their cloud, they should integrate shift left security throughout the build/test/run phases of their software development lifecycle (SDLC). This means they should empower their DevOps and DevSecOps teams with the tooling and support necessary to create environments and architectures that are scalable, replicable, and secure in accordance with policy or regulatory requirements (think zero trust).
Additional consideration is given to making sure that the agency or organization undergoing a cloud migration understands the required changes in the fundamental approach from managing on-premises infrastructure to managing a cloud ecosystem. This shift includes setting up policies and governance for the cloud to automate security testing, scan and patch for cloud vulnerabilities, deploying managed scripts with up-to-date security policies, enforcing least privilege, and centralizing common cloud services (i.e., security services).
Centralizing Cloud Services
Centralizing services should be given additional attention as it assists the agency or organization in reducing complexity and resource consumption. The reduction in complexity stems from having a consistent experience or view across the ecosystem allowing for streamlined management and security posture performance.
Resource consumption efficiencies relate to simplifying procurement (consistent with a homogeneous ecosystem), system maintenance, and compliance requirements. One other important part of this section is its focus on people and ensuring that proper support and training are provided to those tasked with managing and maintaining the cloud ecosystem.
Zero-Trust Security
The other special call out throughout the publication is on zero trust; Executive Order 14028 encourages agencies and organizations to adopt a zero trust architecture as a practical way to manage their risk posture and monitor their cloud risks and threats for rapid remediation and incident response to cloud attacks. One resource to help develop a strategy can be found in CISA’s Zero Trust Maturity Model. In particular, agencies that are on the zero trust path need to move from a traditional role-based authorization model to an attribute based model. Other key pillars in the zero-trust model that are more easily addressed when migrating to the cloud center on devices, applications, networks, and data.
Cloud Security Posture Management (CSPM)
The final section of this publication discusses Cloud Security Posture Management, or CSPM. The publication defines CSPM as ‘a continuous process of monitoring a cloud environment by identifying, alerting on, and mitigating cloud vulnerabilities; reducing risk; and improving cloud security.’ This is accomplished through a number of typical security approaches, such as adapting policies and standards to support the cloud ecosystem, improving identity, credential, and access management (ICAM), infrastructure and application protections, and incident response and recovery procedures.
One interesting call out is on data protection; the guidance states that the agency or organization should engage with the CSP to understand and determine how the data will be managed and protected. This is important when considering risks, like data leakage and data loss, and how the agency determines what data should be protected, how it will be protected, and who controls access and sharing of that data.
Moreover, CSPM solutions assist with the main security elements, including continuous monitoring and alerting on anomalies and events from cloud sources and monitoring logs. The right CSPM solution can help to prevent and identify vulnerable configurations that could result in a breach or loss of data. For security leaders who need to see their cloud environments holistically, CSPMs can deliver comprehensive visibility across the entire cloud ecosystem. This enables the agency or organization to properly manage its cloud estate in accordance with the CISA Technical Cloud Security Reference Architecture publication, FedRAMP requirements, and other associated regulatory and compliance needs.
Government Solutions for Cloud and Multi-Cloud Compliance
Orca is an agentless Cloud Native Application Protection Platform with Cloud Security Posture Management features, including capabilities to identify configuration and vulnerability issues in code repositories and assess against 40+ control frameworks. These capabilities offer federal agencies, sub-agencies, and third party suppliers proven cloud security government solutions. Customers with Orca Security can customize these compliance frameworks in the Orca platform to meet their unique regulatory and compliance requirements, including FedRAMP, NIST SP 800-53, SOC 2 Type 2, and HIPAA. Security and GRC Teams can save weeks at a time using Orca continuous compliance dashboards, real-time audit exports, and easy-to-track remediation artifacts for comprehensive audit readiness and preparedness.
Ready to see your multi-cloud environment in minutes? Sign up for a free, 30-day trial and cloud security risk assessment today – at no obligation to you.
Sources
- Russian hackers get the headlines. But China is the bigger threat to many US enterprises, Protocol, August 3, 2022: https://www.protocol.com/enterprise/china-hacking-ip-russia-cybersecurity
- To make US more cyber-resilient, government and business need far greater collaboration, U.S. White House press briefing, July 28, 2021: https://www.whitehouse.gov/briefing-room/press-briefings/2021/07/28/background-press-call-on-improving-cybersecurity-of-u-s-critical-infrastructure/
- Improving the Federal Government’s Investigative and Remediation Capabilities
- Related to Cybersecurity Incidents, White House Office of Management and Budget, 2021: https://www.whitehouse.gov/wp- content/uploads/2021/08/M-21-31-Improving-the-Federal-Governments-Investigative-and-Remediation- Capabilities-Related-to-Cybersecurity-Incidents.pdf






