Table of contents
Application Programming Interfaces (APIs) have revolutionized the way software apps interact with each other. APIs play an essential role in modern software development, allowing for seamless integration and interaction across various systems and services.
APIs serve as the connective tissue that power the applications we use everyday. From weather to social media apps, productivity tools to communication channels, APIs work behind the scenes to provide the information you see. Despite their value, they pose significant security threats if not properly protected, making API Security a top priority for enterprises. API Security is essential to protect sensitive data, maintain service integrity, and prevent malicious attacks.
In this post, we dive deep into the world of API Security, detailing what it is, why it matters, and how it works.
What are APIs?
An API, or application programming interface, is a set of rules or protocols that enables software applications to communicate with each other to exchange data, features, and functionality. APIs act as messengers that allow two separate software components to talk to each other and exchange data or functionality. Think of them as translators that enable different systems to understand each other’s language and work together harmoniously.
As digital innovation continues to accelerate, so does the need for interconnected systems and applications. APIs have become the backbone of this interconnectivity, enabling businesses to integrate various services, leverage third-party data, and create powerful ecosystems. The exponential growth of APIs is fueled by the increasing demand for cloud-based services, mobile apps, and the Internet of Things (IoT) devices. With more devices, platforms, and services emerging, APIs have become indispensable for facilitating seamless communication and data exchange.
Types of APIs
APIs come in different forms, each serving a specific purpose:
- Web APIs: These power web applications and facilitate data exchange over the Internet.
- Operating system APIs: These enable software programs to interact with the underlying operating system, accessing system resources and services.
- Library APIs: These provide pre-built code libraries that developers can leverage to add functionality to their applications without reinventing the wheel.
Managed vs. unmanaged APIs
While many APIs are carefully designed and managed by organizations, others can lurk in the shadows, unnoticed and potentially posing security risks. These “shadow” and “zombie” APIs are unmanaged and often forgotten, leaving them vulnerable to cyber threats.
As the API ecosystem continues to grow at an unprecedented rate, the need for robust API security measures becomes paramount. Businesses must prioritize securing these critical digital assets to protect their data, systems, and reputation.
What is API Security?
API Security refers to the measures and practices used to protect APIs from unauthorized access, data breaches, and other malicious activities. APIs serve as the backend structure for systems and services, making it crucial to protect their functionality, integrity, and the sensitive data they transmit against unauthorized access, misuse, or malicious attacks.
With the speedy adoption of APIs in recent years, threats of misuse and malicious attacks can cause application disruptions or service interruptions, resulting in potential lost revenue, customer frustration, and potential leakage of sensitive data. According to Gartner, “API security challenges have emerged as a top concern for most software engineering leaders, as unmanaged and unsecured APIs create vulnerabilities that could accelerate multimillion-dollar security incidents.”
Apart from the threats themselves, just knowing which APIs are in your cloud workloads is complicated. Given the pace of cloud-based application development, it’s almost impossible to keep track of new and changed APIs. Application complexity leads to misconfigurations, as well as unmanaged and unsecured APIs that create vulnerabilities. In fact, Gartner predicts that by 2025, less than 50% of enterprise APIs will be managed. API Security, therefore, is greatly increasing in importance.
Unique challenges of API Security
Securing APIs is not as straightforward as securing traditional web applications. Due to the inherent nature of APIs and their widespread use, API Security presents unique challenges.
First, unlike web applications, APIs often have no user interface. This absence makes it difficult to monitor activity and detect malicious attempts. Second, APIs often expose sensitive data and functionality and act as a direct path to backend systems. Since APIs are designed for machine-to-machine communication, they are a prime target for automated attacks.
Beyond these core challenges, maintaining a secure API ecosystem adds new complexities. The varied nature of API implementations, developed using different technologies and frameworks, can result in inconsistent security measures. Additionally, relying on third-party APIs exposes an organization to external security risks that it cannot directly control.
The rapid pace of development can also make it difficult to keep track of new and changed APIs, and misconfigurations or unmanaged APIs can create vulnerabilities in this dynamic environment. Furthermore, the threat landscape is constantly evolving, with new attack techniques and vulnerabilities emerging regularly. As a result, API Security measures must be adaptable and continuously updated to address these emerging threats.
Why is API Security important?
API Security can help your organization in the following ways:
- Prevent data breaches: Unsecured APIs can provide a gateway for cybercriminals to access sensitive data like customer records, intellectual property, and more. High-profile data breaches often stem from exploited API vulnerabilities. By protecting your APIs, you can maintain data privacy and avoid costly breaches.
- Mitigate DDoS attacks: APIs are a prime target for Distributed Denial of Service (DDoS) attacks that overwhelm systems with bogus traffic. Securing APIs can prevent attackers from taking down your websites, apps, and services, which can lead to downtime, lost revenue, and reputational damage.
- Stop injection attacks: Injection flaws like SQL injection and cross-site scripting enable attackers to insert malicious code into APIs. This can allow them to hijack accounts, steal data or even take full control of systems. API Security protects against these attacks by providing robust input validation.
Ensuring authentication & authorization: Weak authentication and excessive permissions in APIs create openings for unauthorized access and privilege escalation attacks. Implementing strong identity controls and least privilege principles locks down APIs.
Types of API Security threats
With APIs acting as gateways to your sensitive data and core systems, any vulnerability or breach could have devastating consequences. Here are some of the common API Security threats that may arise from poorly secured APIs.
Data breaches
One of the biggest threats is unauthorized access to sensitive data passing through APIs. A poorly secured API can provide threat actors with convenient access to valuable customer information, intellectual property, or other confidential data for exfiltration.
DDoS attacks
APIs are also top targets for Distributed Denial of Service (DDoS) attacks. This type of attack attempts to overwhelm APIs with bogus traffic and cripple mission-critical systems, which can lead to costly downtime.
Injection flaws
Attackers also look to exploit injection vulnerabilities. These occur when user input isn’t properly validated, allowing attackers to inject malicious code into APIs. SQL injection and other code injection attacks can give them full control over systems.
Authentication bypasses
Weak authentication and authorization controls create another major risk. If an API login system is flawed, threat actors may be able to bypass it entirely to gain unauthorized access. Other authentication risks include improper access controls and credential stuffing attacks.
Man-in-the-middle attacks
Attackers may intercept and manipulate data transmitted between the API and its consumers, potentially gaining access to sensitive information.
Best practices for API Security
1. Adopt authentication measures
Securing access is job one for API protection. You need robust authentication to verify identities and authorization controls to manage permissions. Implement strong password policies, multi-factor authentication (MFA), and JSON Web Tokens (JWTs) or OAuth for secure API key management.
2. Embrace encryption
Data security is paramount. All API traffic should flow over encrypted connections using TLS/SSL protocols. Data at rest in databases and object stores must also be encrypted. Leverage proven encryption algorithms, manage keys properly, and stay up-to-date on evolving standards.
3. Leverage API throttling
Malicious bots and bad actors will try to overwhelm your APIs with bogus traffic. Rate limiting can control how many requests are accepted over a certain period from individual IPs or clients. Set sensible thresholds tailored to your typical API consumption patterns.
4. Monitor, log, and analyze
You can only protect what you can see. Comprehensive monitoring and logging of all API activity is critical for rapid threat detection and incident response. Analyze logs proactively to identify anomalous behavior patterns before they become serious breaches.
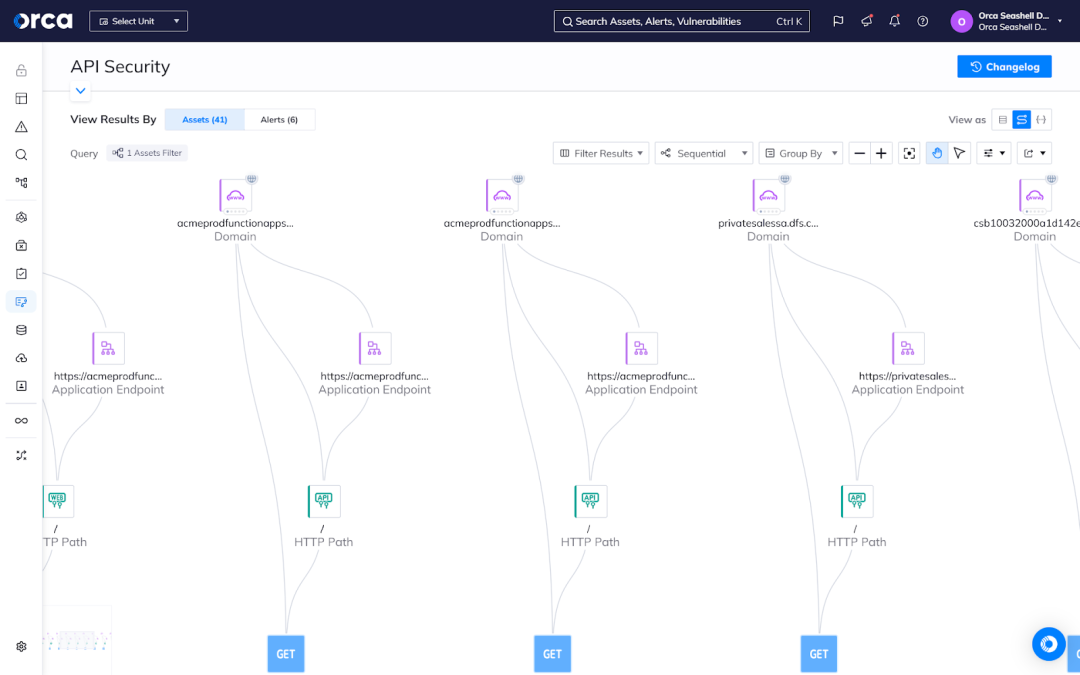
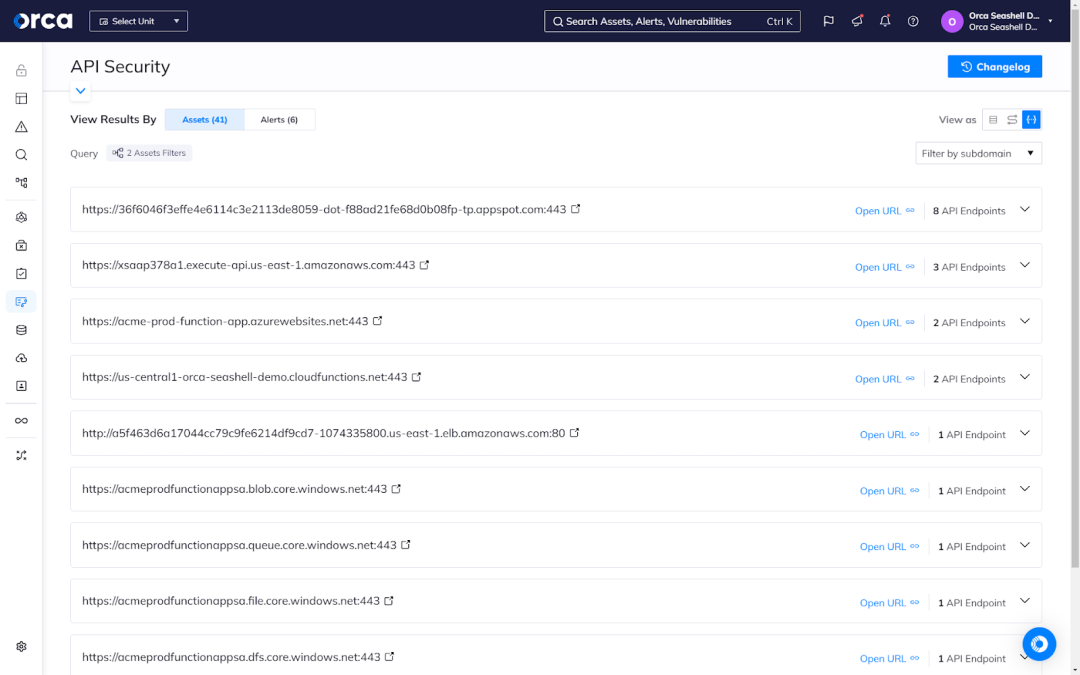
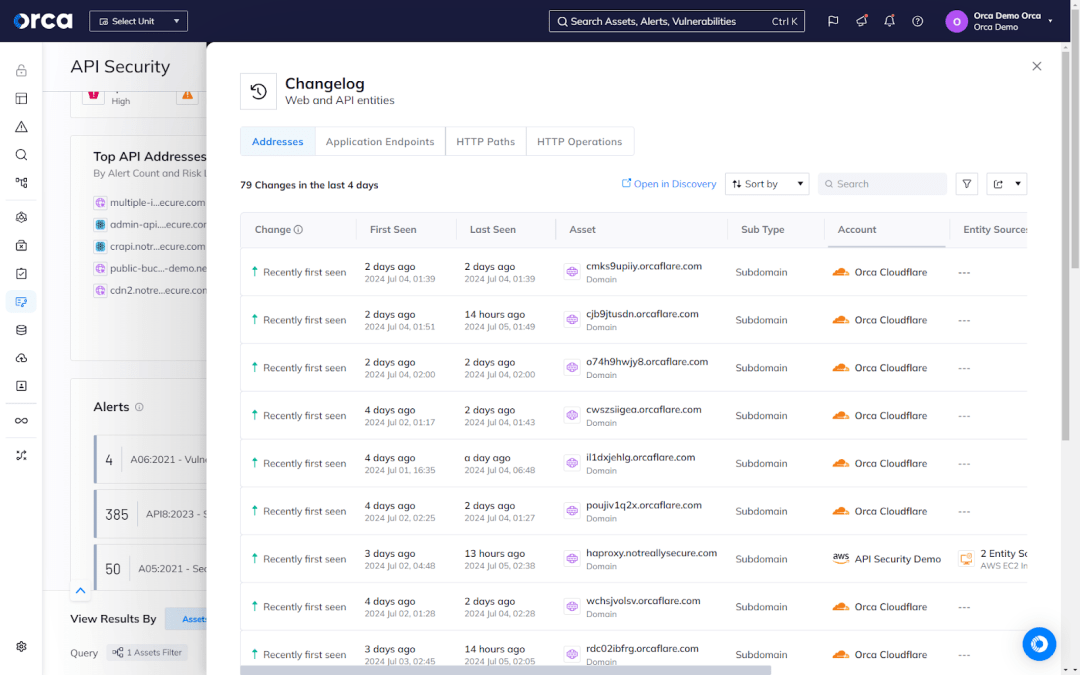
5. Stay up-to-date on vulnerabilities
New API vulnerabilities are constantly emerging. Keep a close eye on security advisories from cloud providers, vendors, and trusted researcher communities. Quickly patch any disclosed flaws in API specifications, code libraries, or runtimes you rely upon.
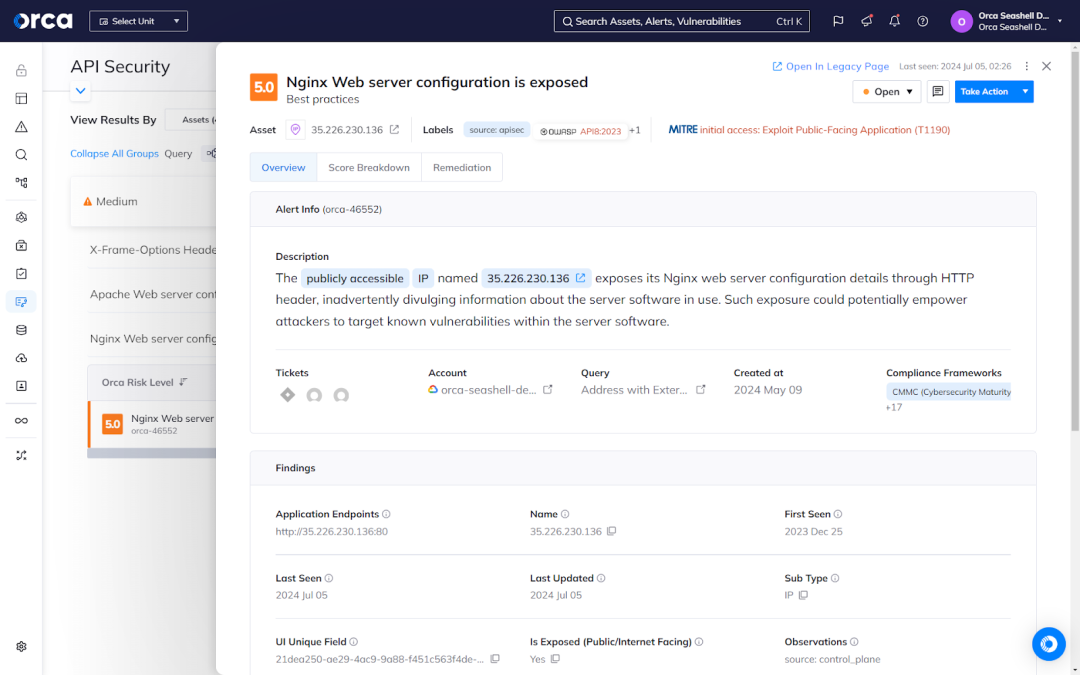
6. Leverage specialized tools
While APIs require some unique security measures, you don’t have to build everything from scratch. Look for API gateways, security testing tools, and true CNAPPs that offer advanced, integrated API Security.
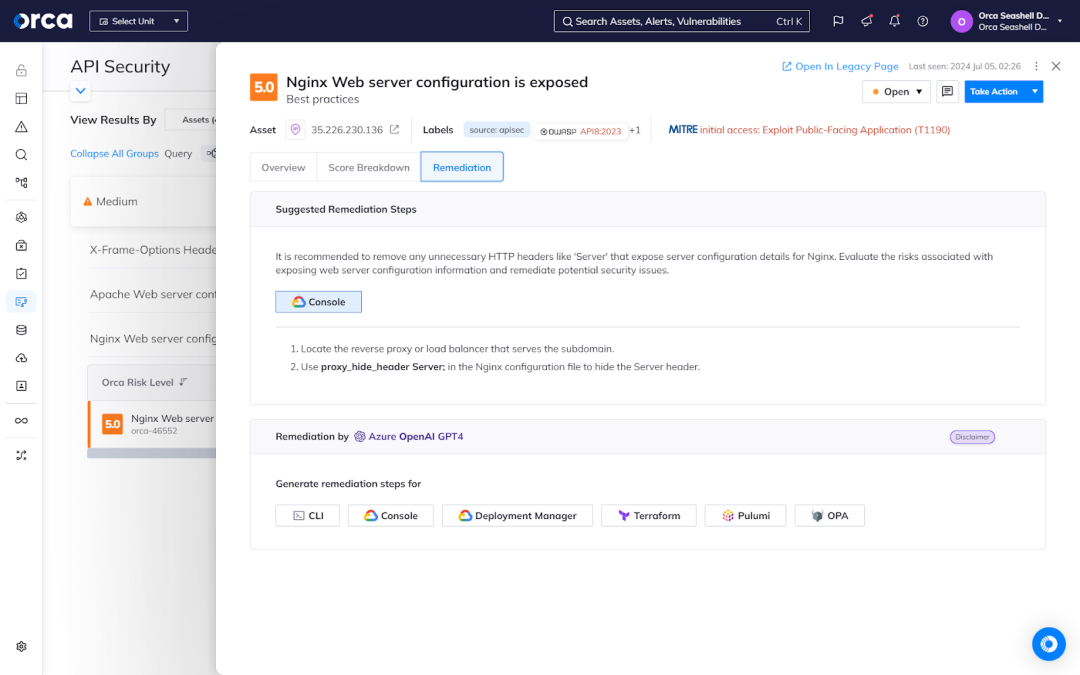
Tools and solutions for API Security
The right tools make all the difference for robust API Security. Combine gateway controls with encryption, testing, and true agentless-first CNAPP solutions for complete coverage of your critical API attack surface. Here’s how:
API Security gateways
An API gateway acts as a gatekeeper, managing traffic flow and applying security policies. Leading solutions provide API authentication, access control, rate limiting, data encryption, and activity monitoring.
Encryption and data protection
Encrypting data in transit and at rest is foundational to API Security. SSL/TLS encryption safeguards API communications, while field-level tokenization and format-preserving encryption lock down sensitive data payloads.
API Security testing tools
From static code analysis to dynamic testing with mock APIs, a range of tools uncover vulnerabilities before attackers do. Popular options include SoapUI, Postman, Netsparker, and Acunetix.
Agentless-first CNAPP solutions for API Security
True agentless-first Cloud-Native Application Protection Platforms (CNAPP) provide advanced API Security, including comprehensive full-lifecycle API discovery, inventory management, and risk assessment without requiring network or software updates. Fast and easy to deploy, these solutions minimize blindspots and provide a complete view of how API risks interact with other cloud assets and risks. These unified platforms also fully contextualize and prioritize risks across clouds, applications, and APIs.
Future trends in API Security
The future of API Security lies in leveraging advanced technologies and adopting a proactive, holistic approach to mitigate risks effectively. Here are some of the future trends to look out for when it comes to API Security.
1. Harnessing AI and Machine Learning
Artificial Intelligence (AI) and Machine Learning (ML) are poised to play a pivotal role in the future of API Security. These technologies can analyze vast amounts of API traffic data to detect anomalies, identify patterns, and predict potential threats with unparalleled accuracy. AI-powered security solutions can continuously learn and adapt, providing real-time threat detection and automated response capabilities. This proactive approach can help organizations stay ahead of ever-evolving API Security threats.
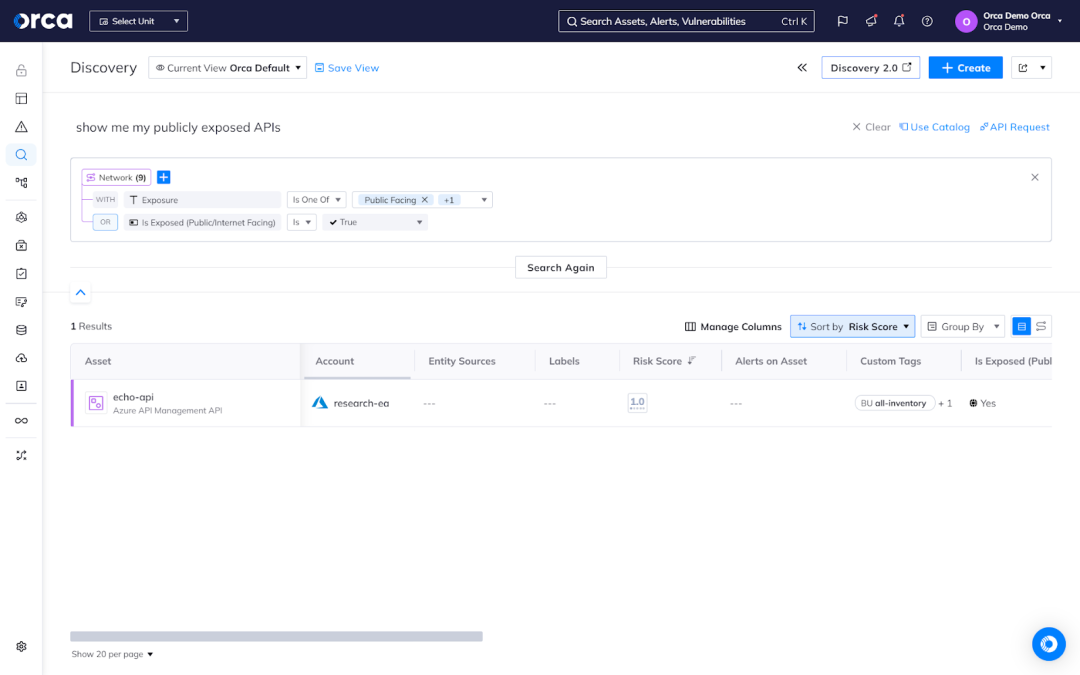
2. Embracing Zero Trust architectures
The traditional castle-and-moat security model is no longer sufficient in today’s distributed and API-driven environments. The future lies in adopting a Zero Trust architecture, which assumes that every user, device, and API request is untrusted until proven otherwise.
Zero Trust architectures enforce strict access controls, continuous verification, and granular policies for API interactions. This approach minimizes the attack surface and reduces the risk of unauthorized access or data breaches, even in the event of a perimeter breach.
3. Evolving API Security standards
As API usage continues to grow, industry-wide standards and best practices for API Security will evolve to keep pace. Existing guidelines, such as the OWASP API Security Project and the OpenAPI Specification, will be refined and expanded to address new challenges and emerging threats.
Collaboration between security experts, API developers, and industry organizations will be crucial in establishing comprehensive and widely adopted API Security standards. These standards will provide a robust framework for secure API design, development, and deployment across various industries and use cases.
4. Seamless integration with existing security ecosystems
In the future, API Security solutions will seamlessly integrate with an organization’s existing security ecosystem, providing a unified and centralized approach to managing API risks. This integration will enable organizations to correlate API Security data with other security signals, such as network traffic, user activities, and threat intelligence.
By consolidating API Security data with other security telemetry, organizations can gain a holistic view of their cyber risk posture, enabling better prioritization of remediation efforts and more effective incident response.
API Security, compliance, and regulations
As APIs become ubiquitous, ensuring compliance with data privacy and security regulations is crucial to prevent financial, operational, reputational, regulatory, and legal risks.
GDPR and its impact on APIs
The EU’s General Data Protection Regulation (GDPR) has far-reaching implications for how organizations handle personal data, including via APIs. Under GDPR, organizations must maintain robust security measures to protect personal data processed by APIs. This includes encryption, access controls, and breach notification procedures.
Maintaining audit trails of how personal data flows through APIs is also essential for demonstrating GDPR compliance. Organizations shouldn’t overlook the “right to be forgotten”— they need mechanisms to remove personal data from their systems upon request.
The CCPA and API data management
California’s Consumer Privacy Act (CCPA) grants consumers more control over their personal information collected by businesses. Like GDPR, it requires companies to implement technical safeguards to protect consumer data handled by their APIs.
Organizations need processes to respond to consumer requests to access, delete, or opt out of the sale of their data. Maintaining detailed data inventories that map personal info flowing through APIs is key for CCPA compliance.
Navigating HIPAA for healthcare APIs
For organizations that handle patient information, securing APIs that transmit protected health information (PHI) is critical for complying with HIPAA privacy and security rules. Encryption, access controls, and audit logging are must-haves.
But compliance goes beyond technical measures. Organizations need HIPAA-compliant policies and procedures governing the development, testing, and management of healthcare APIs. Staff training is also essential to avoid breaches.
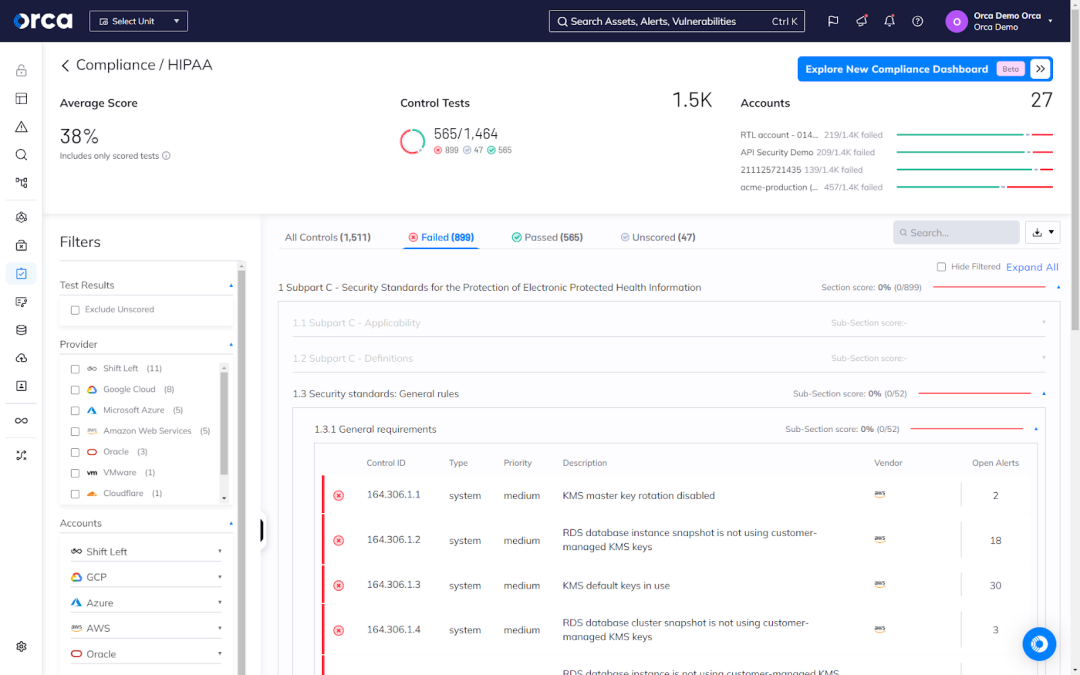
Sector-specific challenges
While GDPR, CCPA, and HIPAA are broad frameworks, organizations may face additional sector-specific compliance obligations for their APIs:
- Financial services: Regulations like PCI DSS mandate rigorous security for financial data flowing through payment APIs.
- Public sector: Government APIs must adhere to standards like FedRAMP and NIST 800-53 to protect citizen data.
- Telecommunications: Telecom providers must safeguard customer data transiting internal and external APIs per privacy laws.
Case studies on API Security breaches
Common API Security pitfalls
In cloud environments, storage buckets serve as containers that house critical data. A common and significant security risk happens when those buckets become publicly exposed to the Internet. This often occurs because of an API misconfiguration.
One common pitfall is failing to restrict bucket access controls properly. Storage buckets have complex permission models that can easily lead to over-permissive access if not locked down carefully.
Another issue is using overly broad cloud credentials with excessive privileges attached. Following the principle of least privilege is critical for API Security.
Real consequences
The impacts of API security breaches can be substantial. In 2022, the Australian telecom provider Optus experienced a significant cyber attack that leaked the sensitive data of more than 11.2 million customers. The incident came after attackers exfiltrated the data from an unauthenticated API. One year earlier, Twitter experienced an API security breach after an attacker exploited a Twitter API vulnerability to collect data and sell it to other cybercriminals.
Beyond reputational damage, these and other examples can lead to significant financial losses, disruptions to business continuity, lawsuits, and more.
Proactive prevention measures
To prevent the previous scenarios, your organization should implement robust access controls, follow the least privilege principle religiously, and monitor your cloud environment continually for misconfigurations or suspicious activity.
Using a comprehensive API Security solution with dynamic discovery, traffic analysis, and risk scoring can help automatically detect and remediate threats.
Ultimately, treating API Security as an ongoing discipline—not a one-time activity—is essential.
Conclusion
API Security is a necessary and vital area of cloud security. Without the proper API protections in place, organizations leave their most valuable digital assets exposed and vulnerable to exploitation. Yet by implementing API Security best practices and adopting solutions like a true CNAPP, you can better protect sensitive data, maintain service integrity, and prevent malicious attacks.
Learn more about the Orca Cloud Security Platform
The Orca Cloud Security Platform offers a true agentless-first CNAPP. Orca identifies, prioritizes, and remediates security and compliance risks for today’s most popular cloud service providers, including AWS, Azure, Google Cloud, Kubernetes, Alibaba Cloud, and Oracle Cloud.
A single unified solution, the Orca Platform provides API Security, CSPM, CWPP, CIEM, DSPM, AI Security Posture Management (AI-SPM), Multi-Cloud Compliance, Vulnerability Management, Shift Left Security, and more. Orca leverages its patented SideScanning™ technology to provide complete coverage and comprehensive risk detection across your entire cloud estate.
It also brings together insights and data into its Unified Data Model, enabling Orca to fully contextualize risks, accurately prioritize them, and also identify critical attack paths that combine multiple interconnected risks.
Leveraging the Orca Platform begins as soon as you complete a quick 30-minute onboarding session. Schedule a demo with one of our experts to see how the Orca Platform can enhance your cloud security.
API Security FAQs
Why is API usage growing exponentially?
API usage has been growing exponentially with digitalization and the emergence of cloud computing, mobile apps, and the IoT. The shift towards microservices, containerization, and serverless architectures has also supercharged API adoption. APIs enable different software components to communicate seamlessly, forming the building blocks of modern applications and the enablers of digital transformation.
What is the advantage of a CNAPP vs siloed API Security?
Traditional API Security tools operate in isolation, leading to blindspots and coverage gaps that pose significant risks. True CNAPP solutions provide complete coverage of your cloud estate and comprehensive risk detection, including vulnerabilities, misconfigurations, API risks, data risks, AI risks, IAM risks, and more. This unified view facilitates effective risk detection, prioritization, and remediation.
What are zombie APIs?
Zombie APIs are old, forgotten APIs that expand your attack surface. Often undocumented and unmanaged, they represent serious blindspots that attacks can potentially exploit to breach your systems. A robust API Security strategy includes discovering and decommissioning these zombie APIs.





