This post was originally published to The New Stack.
It is estimated that the cost of cybercrime could exceed $20 trillion by 2026, increasing the pressure on organizations to ensure that they have effective safety net mechanisms in place.
Thankfully, several security frameworks have been established to tackle these ever-rising cybersecurity threats. This article will explore two popular cybersecurity frameworks: NIST CSF and MITRE ATT&CK. It will provide a high-level overview of their features, investigate their differences and explain how to use the cloud with these frameworks.
NIST CSF
The National Institute of Standards and Technology (NIST) is a U.S. government agency whose sole purpose is to promote American innovation and industrial competitiveness. A big portion of its budget is dedicated to improving the cybersecurity posture of the United States.
The NIST Cybersecurity Framework (CSF) is a publicly-available security framework designed to help organizations minimize the risk of cyber threats. Although the framework guidelines are tailored to government organizations, NIST CSF can be adapted to any kind of enterprise because of its tried-and-true security practices.
NIST CSF Components
NIST CSF consists of three components: the core, implementation tiers and profiles.
The core component is responsible for establishing a common language and providing the basic set of desired cybersecurity activities and outcomes. This includes the main body of functions, which contain individual categories and sub-categories. Each row contains informative references such as existing standards, guidelines and best practices.
The tiers component provides organizations with a mechanism for assessing their cybersecurity risk management. In addition, it enables organizations to evaluate and adjust their level of rigor based on their organizational goals. In other words, it gives you a tiered outline of cybersecurity risk management options and allows organizations to adapt based on their needs and level of maturity.
Finally, the profiles component shows organizations how to find, identify and prioritize opportunities for improving their security posture. These profiles allow organizations to assess various factors, like the costs and risks involved, when optimizing the cybersecurity framework to best serve their needs.
NIST CSF Core Functions
NIST CSF’s core is divided into five main functions that are used for the development of security controls. These are basic cybersecurity activities that serve a particular security domain. The five functions are:
- Identify – Manage and protect identity and access control mechanisms of systems and services.
- Protect – Develop appropriate security controls to ensure the safe delivery of services to users without compromise.
- Detect – Capture traces and audit trails of suspicious activities for accountability and incident reporting.
- Respond – Establish effective activities to mitigate active attacks and persistent threats.
- Recovery – Develop and implement action plans for previously detected or exploited cybersecurity events.
The bulk of the core material consists of tables with unique identifiers that point to specific publications:
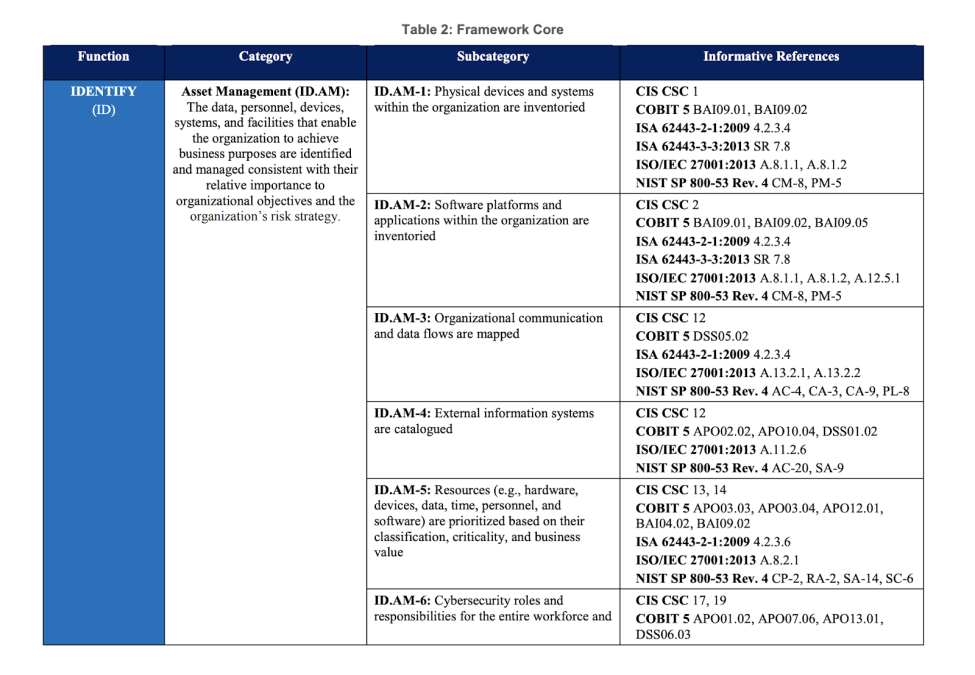
NIST CSF functions feference (source: https://www.nist.gov/)
Using NIST CSF Effectively
Realistically, using a NIST CSF framework consists of comparing checklists of your organization’s activities with those outlined in the framework’s core.
The framework itself guides the implementer through a series of published material that adheres to the specific security profiles. There is no one standard case, however, since implementers must conduct their own reviews and assess the applicability of those guidelines.
For example, in the core function reference for identity, you’ll see:
Identity-> Risk Assessment -> ID.RA-4: Potential business impacts and likelihoods are identified.
This row mentions the use of CIS Critical Security Control 12, which is a set of security mechanisms that prevent attackers from exploiting vulnerable network services and access points. This ensures that network communications are safe since a compromise will affect people’s lives.
Your organization’s end goals will help you determine which areas to improve based on your budget and risk mitigation goals.
What is MITRE ATT&CK?
Another popular cybersecurity tool is the MITRE ATT&CK framework. It is a public catalog of adversary tactics and techniques based on real-world observations, and is used as both a reference for past incidents and as a way to understand how the attack vectors work.
The ATT&CK Matrix
The ATT&CK Matrix consists of a reference table of tactics. Each column represents individual steps in a linear fashion, starting with reconnaissance tactics and ending with impact. Each column also contains entries with different kinds of scenarios and information about how they are used by adversaries to perform malicious attacks.
The framework offers three main ATT&CK Matrix variations:
- Enterprise: The Enterprise Matrix is the most extensive catalog of adversary techniques that target various systems like Windows, macOS, cloud infrastructure, SaaS, networks and containers.
- Mobile: The Mobile Matrix explains tactics and techniques for attacking mobile and portable devices.
- ICS: The Industrial Control System (ICS) Matrix covers security prevention techniques for systems that are typically mission-critical applications with a high-availability requirement.
It’s important to note that the Enterprise Matrix consists of several sub-matrices and also contains the Cloud Matrix, which is specific to cloud environments.
The overall aim of MITRE ATT&CK is to provide a foundational knowledge base of real-world attack scenarios and a way for the organization to understand the current cloud threat landscape.
Comparison of MITRE ATT&CK vs. NIST CSF
To use either of these frameworks, it is important to first understand their key strengths and weaknesses. One way to grasp the differences is to focus on a particular piece of a security framework that you care about and try to look for attack patterns or mitigations that apply to your organization.
Let’s look at the main differences between these two security frameworks next.
MITRE ATT&CK’s Focus
MITRE ATT&CK is more focused on specific tactics and techniques. It sources its data from real-world tactics and techniques from past incidents or mock events. For example, it lists malware, several backdoors and tools that attackers use to achieve broader goals and satisfy current objectives.
If you want to learn more about actual attack scenarios, like a certain tool that an adversary used to penetrate the network or a technique leveraged to establish persistence using a particular methodology, then MITRE ATT&CK is the more suitable application for your organization.
One of the particular characteristics of this approach is that it gives insightful pointers on how attackers can circumvent security mechanisms. Effective use of the MITRE ATT&CK framework requires improving existing systems to detect and thwart similar attack patterns.
NIST CSF’s Focus
NIST CSF is more focused on general best practices and guidelines. It is more like a body of knowledge pertaining to specific organizational needs. As an alternative to MITRE, it’s more foundational and considers how security best practices can be effectively integrated into a complex organizational system over time.
Therefore, NIST CSF could be as effective in practice as MITRE ATT&CK, as long as the people responsible for implementing it can directly map the practices into security controls and policies.
Cloud Integration with Orca Security
Both the MITRE and NIST CSF frameworks can be integrated into automated security services and mapped to direct audit trails. This alone is a compelling reason to evaluate their use in cloud technologies as part of a cybersecurity strategy.
Orca Security offers an extensive guide on using MITRE with the Orca Cloud Security Platform, which takes care of the legwork of mapping the attack patterns that affect real infrastructure misconfigurations.
The platform can report the percentage of alignment with NIST CSF, thus providing a clear metric that enables organizations to see the current level versus the ideal. With this knowledge, organizations can respond accordingly to correct the course of their day-to-day processes.





