To manage the risks in today’s cloud threat landscape, defenders are faced with a number of day-to-day responsibilities – investigating hundreds of security alerts, patching vulnerabilities, and threat hunting – to name a few.
Attackers use different practices to infiltrate and gain access within public cloud environments. It’s often said in cybersecurity that in order to effectively defend your cloud environments from attackers, you first need to think like an attacker.
One way security teams study attacker methods is by using threat modeling, a key method to proactively remediate vulnerabilities and detect active threats. In addition, threat modeling helps defenders understand their adversaries’ potential tactics, techniques and procedures (TTPs). The most popular threat modeling framework is the MITRE ATT&CK framework.
What is the MITRE ATT&CK?
The MITRE ATT&CK Framework, provided by the MITRE Corporation, is a globally-accessible knowledge base that is based on common threat actor TTPs, offering a methodology for security risk management of those TTPs in the security environment.
ATT&CK stands for Adversarial Tactics, Techniques & Common Knowledge and has been compiled based on real-world observations. It is used as a foundation for the development of specific threat models and methodologies, and is intended to be used by organizations as a tool to decrease their attack surface.
The framework lists the most commonly seen attacker TTPs into phases or groups, enabling security teams to assess risks at different points in the attack chain, evaluate their security posture strengths and weaknesses, and defend in the way an attacker would.
MITRE ATT&CK uses a shared language which describes the different phases of an attack. Each security event can be described using a dedicated matrix with columns (tactics) and rows (techniques). Tactics help us to understand: “What is the attacker trying to achieve?” While the techniques explain: “How was the attacker able to gain access?”
An attacker would likely use multiple combinations of varying tactics and techniques to successfully execute a compromised event. Toxic combinations of cloud security risks can enable an attack path that could cause a high impact on an organization. Orca Security conducted a study, State of Public Cloud Security Report, and found that the average attack path only needs three steps to reach a critical asset; meaning that an attacker only needs to find three connected and exploitable weaknesses in a cloud environment to exfiltrate data or hold an organization to ransom.
Understanding MITRE’s Cloud Matrix
The MITRE ATT&CK framework consists of different matrices which are relevant for various landscapes such as enterprise, mobile, and critical infrastructure. For this article, we will focus on the Cloud Matrix outlined below.
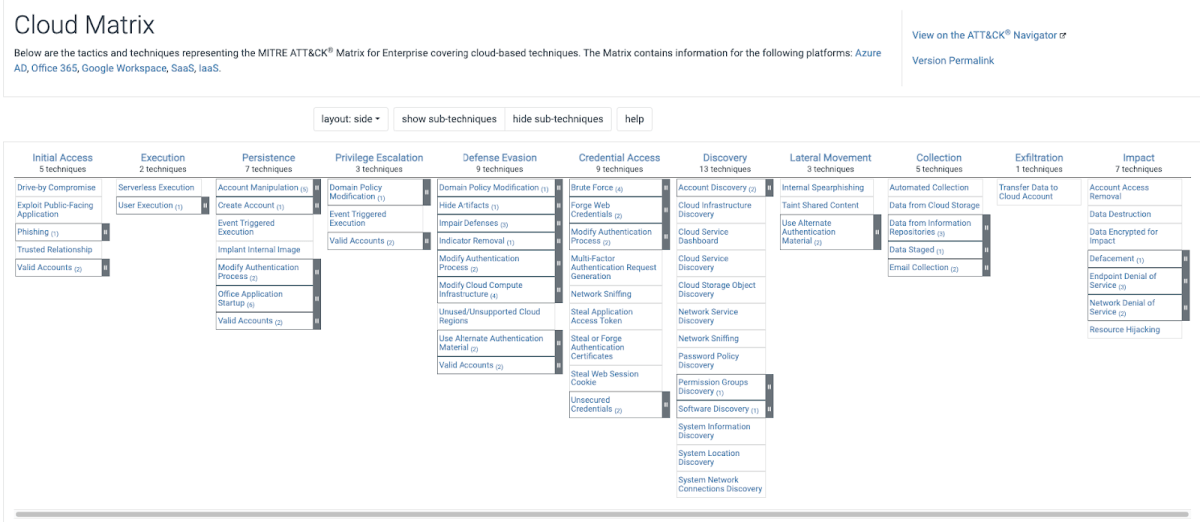
The Cloud Matrix v12 includes a total of 11 tactics and 64 related techniques (Version 12 was published in October 2022 – there have been on average 2 or 3 updates per year).
To give you a sense of how this works, here are a few examples of Cloud Matrix tactics and techniques:
- Initial Access (tactic), Phishing (technique) – Initial Access is the earliest stage that MITRE highlights, in which an attacker attempts to gain a foothold into the cloud environment. Most readers of this article will likely be familiar with phishing, which can be targeted toward a specific individual (i.e. spear phishing emails) or non-targeted. Attackers may send phishing messages that contain a malicious attachment or link, in order to gain initial access to victim systems. An alternative way of gaining initial access would be somehow obtaining valid cloud account credentials. Sophisticated attackers then use that access to pivot to other access to other cloud resources (i.e. lateral movement) or be able to, in certain cases, access sensitive data quickly.
- Credential Access (tactic), Brute Force (technique) – A well-known attacker technique to attempt to gain unauthorized account access is to utilize brute-force attacks. Attackers use common automated tools (that are also frequently used by penetration testers) that systematically and repeatedly guess IAM passwords until one is found that gives them access. Unsecured credentials is another technique MITRE lists, in which attackers can search file systems that contain insecurely stored credentials. As MITRE explains, “[t]hese can be files created by users to store their own credentials, shared credential stores for a group of individuals, configuration files containing passwords for a system or service.” Accessing cloud accounts without authorization and abusing cloud metadata APIs for privilege acquisition are threats cloud security teams need to be aware of.
- Collection (tactic), Data from Cloud Storage (technique) – In the collection stage, the attacker is trying to gather data of interest to their goal. A frequent objective is to access data from improperly secured cloud storage – from buckets, databases, and files on virtual machines. Encrypting sensitive data and restricting access to only necessary users are important security measures to consider, as well as implementing frequent audits to check for misconfigurations.
The MITRE ATT&CK framework helps security teams organize the path of an attack into a story format. This presents security risks with a more “human readable” language and explains the security gaps found, what was gained by the attacker during each stage of the attack, what information could have been compromised, and more.
How the Orca Cloud Security Platform Brings Added Value with MITRE ATT&CK
The Orca Cloud Security Platform leverages the Cloud Matrix, labeling all discovered security alerts with the relevant MITRE ATT&CK information. This context helps security teams to understand risks more quickly, associate them with any other related or combined risk types, and ultimately enable security teams to comprehend and remediate cloud security threats more effectively.
Let’s take a look into a couple of examples.
Linking the MITRE Categories to Specific Security Alerts
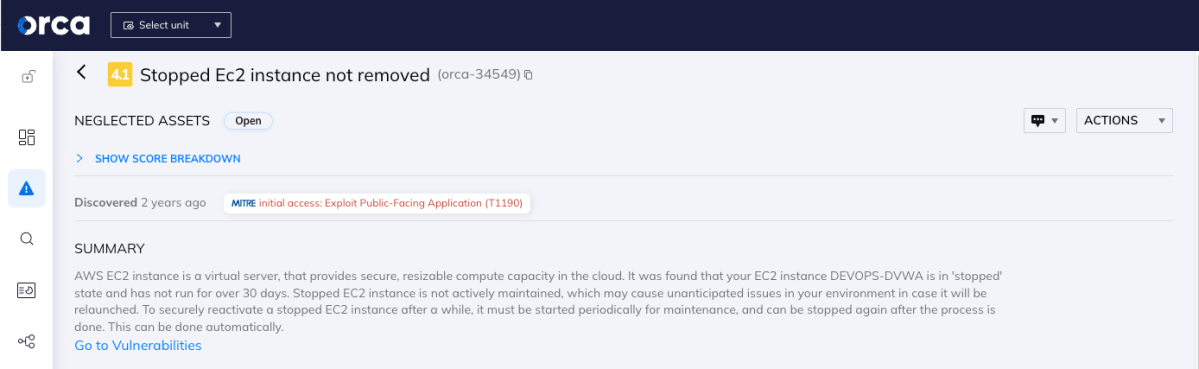
Orca Security alerts security and compliance teams to various cloud risks. In this example, it was found that there was an EC2 instance in a ‘stopped’ state, and the instance had not been active in over 30 days.
Stopped EC2 instances are not actively maintained, which may cause unanticipated issues in your environment, in the event it will ever be relaunched. To securely reactivate a stopped EC2 instance after a while, it must be started periodically for maintenance, and can be stopped again after the process is done. This process can be performed automatically.
The alert discovered by the Orca Cloud Security Platform and the MITRE ATT&CK framework indicates that a ‘stopped’ EC2 virtual machine can serve as the entrance point of a potential attack, since this machine could be not patched with the latest security updates. Therefore the Initial access tactic was assigned.
In addition, there are potentially unpatched applications housed in this machine, therefore the Exploit Public-Facing Application (T1190) technique was tagged.
By mapping and tagging alerts like this to MITRE TTPs, Orca aids security teams in understanding how an attacker could potentially exploit various security risks—misconfigurations, vulnerabilities, excessive privileges, and more—to carry out the different components of an attack. As a result, this will help strategically prioritize risks, patch vulnerabilities, and improve security hygiene.
Spotlighting Potential Attack Paths
One of the most useful ways that Orca uses the MITRE ATT&CK framework is with Attack Path Analysis, where you can view risks as an interrelated chain, rather than just siloed risks.
MITRE tactics are important to understanding which combinations are a direct path to your critical assets. Security teams can operate strategically by making sure that the risks that break attack paths are remediated first.
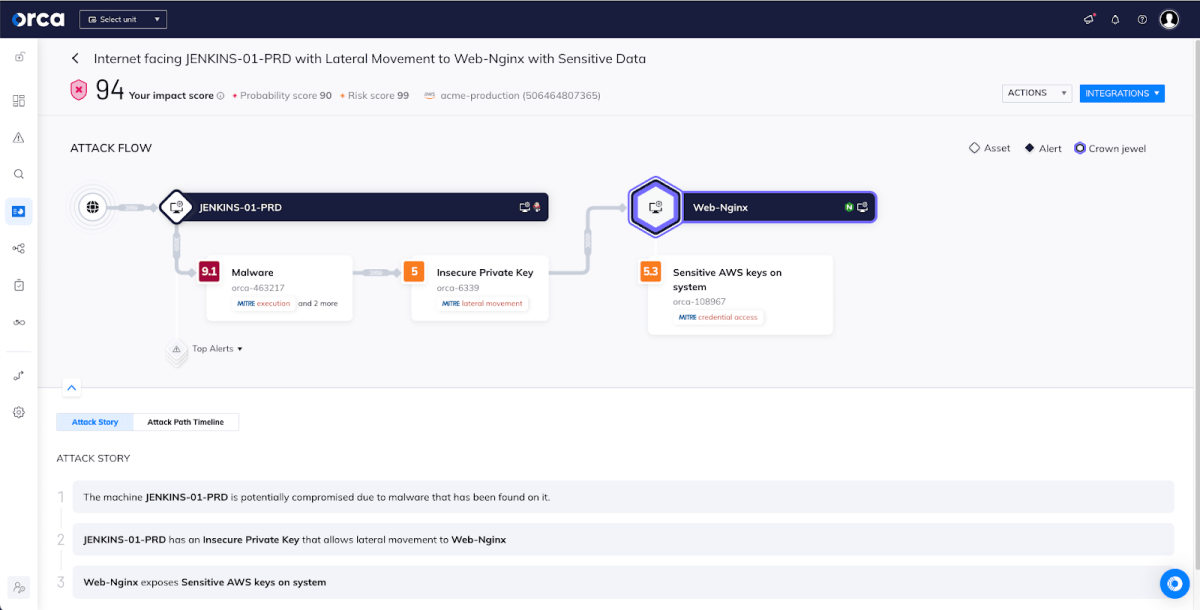
Orca provides a visual representation of each attack path, as shown in the diagram above, along with detailed information on each attack vector.
As you can see in the image above, every risk in the attack path is tied together using MITRE tactics from Initial Access going through different tactics like Lateral Movement all the way to an asset that has a tag like Credential Access, which is one of the tactics that designates a critical asset. The attack path visualization includes further information and context for each step in the attack path.
In short, Orca uses attack paths to help teams remediate more strategically, improving efficiency and ensuring that the truly dangerous issues are remediated faster, which in turn helps avoid damaging attacks and data breaches.
Strengthening MITRE ATT&CK Compliance
Once all cloud security alerts had been enriched, Orca created a dedicated compliance framework which is based on the ATT&CK V12, which is the latest version of the MITRE ATT&CK framework. The new continuous compliance report dedicated framework maps security alerts in MITRE ATT&CK language. The report is built into sections (MITRE Tactics) and the controls (Techniques), making it easier to rapidly determine which side of the attack fails or passes.
In the following radar chart, Orca presents all alerts mapped to specific Tactics (categories):
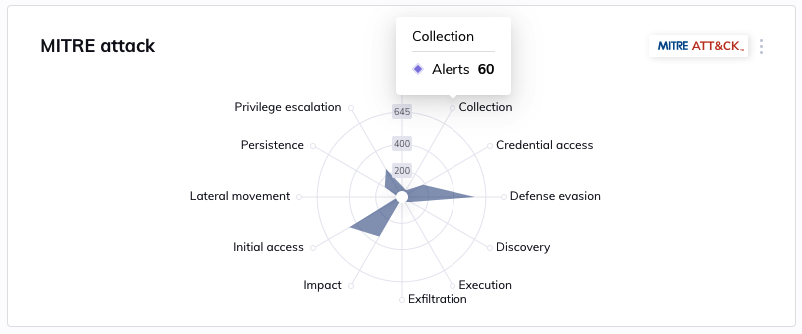
This gives security teams a high-level view of where their weak spots are, and which should be addressed. It also identifies whether they are found in the early phase of initial access, a later stage of defense evasion, or an advanced stage of data exfiltration.
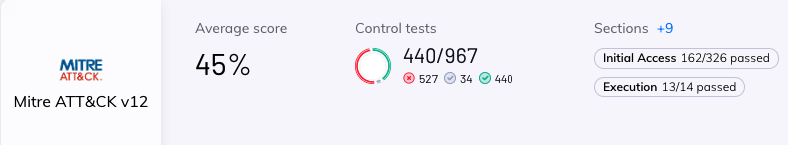
In the image above, Orca presents the general compliance score of all alerts within the given MITRE ATT&CK tactics and techniques. This allows the user to better understand their primary security gaps against the MITRE ATT&CK framework, as well as to assist them with internal and external compliance audits.
Orca also provides a granular breakdown of all tactics/techniques, while narrowing and guiding the user to the specific issues to be addressed and prioritized.

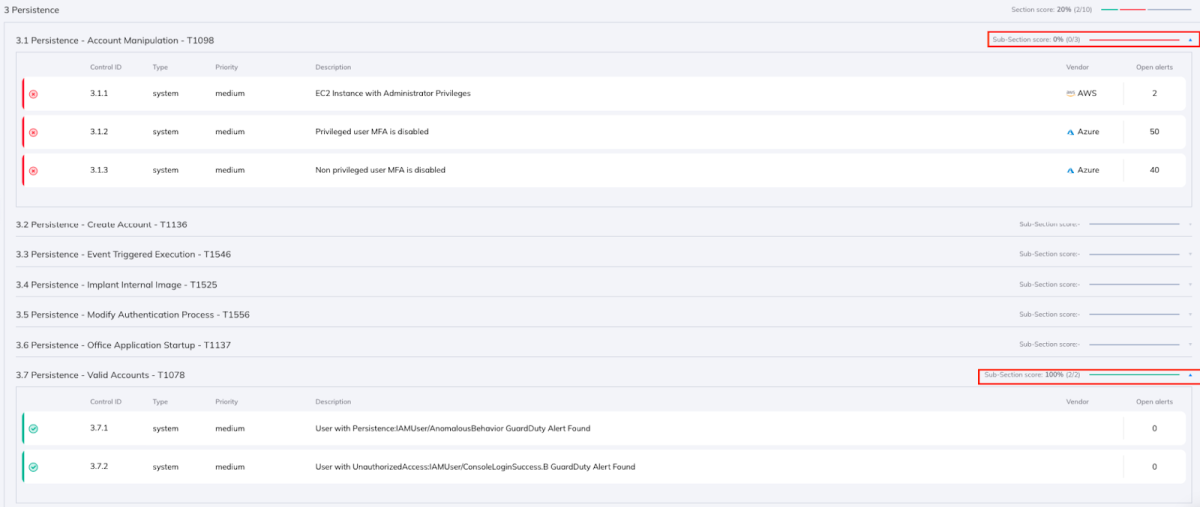
Let’s look at one last example of how Orca can help with MITRE compliance, in this case looking at a specific tactic – Persistence.
As seen as the image below, the organization’s findings reveal that there are two techniques related to this tactic, one of which requires attention:
- 3.1 Persistence – Account Manipulation – there are 3 relevant failed alerts in this category, connected to 92 different assets, which Orca has designated as not being fully addressed. If not addressed properly, this issue can potentially be exploited by an attacker to gain persistence following a successful access attempt.
- 3.7 Persistence – Valid Accounts – there are 2 alerts which passed. No further immediate action item is needed, but Orca users are able to know that these controls are covered securely.
In summary, by using the MITRE ATT&CK insights provided by Orca Security, a user can:
- Identify security weak spots that need attention.
- Improve the overall security posture while focusing on the various parts of the attack chain.
- Minimize the potential risk of the next cybersecurity event.
Leverage MITRE ATT&CK with Orca Security
If you are part of a SOC team responsible for cloud threat detection, you’ll want to read our eBook, The Essential Guide to Cloud Detection and Response (CDR)
Ready to try it out in your own cloud environment? Schedule a demo or sign up for a Free Risk Assessment to see how quickly and easily the Orca Cloud Security Platform can help you identify and address cloud risks. Since the Orca Platform is agentless, you will be up and running with minimal effort.





