To manage the risks in today’s threat landscape, defenders are faced with a number of day-to-day responsibilities – from investigating hundreds of security alerts, patching vulnerabilities, and threat hunting – to name a few.
Security teams use threat modeling, a key method to proactively remediating vulnerabilities and detecting active threats, to understand their adversaries’ potential techniques, tactics, and processes (TTPs).
The most popular threat modeling framework today is called the MITRE ATT&CK framework. This framework, provided by the MITRE Corporation, is structured based on common threat actor TTPs, offering a methodology for security risk management of those TTPs in the security environment.
With MITRE ATT&CK incorporated into the security strategy, defenders can use the framework for threat modeling and security attack analysis.
The History of the MITRE ATT&CK Framework
The MITRE ATT&CK Framework was first introduced in 2013 as a tool to help the US military understand and respond to advanced persistent threats (APTs). MITRE developed the Framework by analyzing hundreds of APT campaigns and mapping the tactics, techniques, and procedures (TTPs) used by the attackers. The goal was to create a comprehensive taxonomy of APT behavior that could be used to develop more effective defensive strategies.
Over time, the Framework gained traction in the cybersecurity community as a useful tool for organizations to better understand and defend against cyber attacks. In 2015, MITRE released the first version of the Framework to the public, making it available to organizations and cybersecurity professionals around the world.
Since then, the Framework has undergone several updates and revisions, with the latest version being ATT&CK v12. MITRE has continued to refine the Framework and expand its coverage to include new threats and attack techniques as they emerge. MITRE also provides regular updates to the Framework to reflect changes in the threat landscape and to incorporate feedback from the cybersecurity community.
Today, the MITRE ATT&CK Framework is widely used by organizations and cybersecurity professionals around the world as a standard for assessing and improving their defenses against cyber attacks. Its adoption has been facilitated by its open nature and the fact that it is freely available to the public. As cyber threats continue to evolve, the Framework is expected to continue to play an important role in helping organizations stay ahead of the curve and defend against advanced attacks.
What is the MITRE ATT&CK Framework?
The MITRE ATT&CK Framework is a globally-accessible knowledge base of tactics and techniques for understanding how cyber adversaries operate.
ATT&CK stands for (Adversarial Tactics, Techniques & Common Knowledge) and has been compiled based on real-world observations. It is used as a foundation for the development of specific threat models and methodologies, and is intended to be used by organizations as a tool to decrease their attack surface.
This framework helps organizations manage their cyber risk by understanding attacker behaviors and enhances their ability to investigate security incidents.
Gaining a better understanding of how adversaries mount attacks and using this information as additional context for prioritizing risks will better position you to improve your cyber defense posture.
What is the MITRE ATT&CK Matrix?
The MITRE ATT&CK matrix contains a set of tactics and techniques used by adversaries to accomplish specific objectives.
These objectives are categorized as tactics in the ATT&CK Matrix. The objectives are presented in a linear fashion starting with reconnaissance and moving to the right to the final goal of exfiltration or “impact”.
Currently the different MITRE matrices look at ATT&CK tactics for enterprise, which includes Windows, Linux, Cloud security, Containers and more.
The goal is to use the MITRE ATT&CK matrices that apply to what you are interested in (for Orca they are the cloud security, Windows, Linux, and container matrices) and review the tactics and techniques at different stages of an attack and identify and manage what controls you have in place to identify, prevent, or stop an attack.
Understanding Tactics in the MITRE ATT&CK Framework
In the context of the MITRE ATT&CK Framework, tactics represent the underlying motivation or purpose behind a particular technique or sub technique used by an attacker. They provide insight into what the adversary is trying to achieve or accomplish through their actions. For instance, an attacker might seek to obtain access to privileged credentials.
The Enterprise ATT&CK Matrix comprises 14 distinct tactics, which are as follows:
- Reconnaissance
- Resource Development
- Initial Access
- Execution
- Persistence
- Privilege Escalation
- Defense
- Credential Access
- Discovery
- Lateral Movement
- Collection
- Command and Control
- Exfiltration
- Impact
It is worth noting that tactics are an essential component of the ATT&CK Framework, as they allow security professionals to better understand the intentions of an adversary and help in the development of effective threat detection and response strategies.
Exploring Techniques in the MITRE ATT&CK Framework
Techniques are an integral part of the MITRE ATT&CK Framework, as they describe the methods and procedures used by an attacker to accomplish a specific goal or objective.The ATT&CK Matrix includes a comprehensive list of techniques that adversaries may use to achieve their objectives. These techniques are organized into different tactics, which represent the motivation or intent behind the attacker’s actions.
The Enterprise ATT&CK Matrix, which covers Windows, macOS, and Linux systems, comprises 14 distinct tactics, 193 techniques, 401 sub-techniques, 135 groups, 14 campaigns, and 718 pieces of software, as of the 2022 version. MITRE continually updates this list of techniques and provides details of new enterprise campaigns and any changes that may have occurred.
What is the Kill Chain?
The kill chain is a way of describing how a threat actor works their way from successfully attacking a vector to securing a foothold in a target network to reach their final objective.
With that foothold, a threat actor can laterally move across the network, looking for PII and internet-facing systems to prey upon credentials and access control – perhaps in search of command and control.
Does the threat actor want to use ransomware to encrypt the network and financially extort their targeted victim? Or do they want to quickly snatch the company’s crown jewels, and sell them on the dark web?
Understanding these TTPs and final objectives can aid defenders to manage risks proactively as well as stop attacks earlier on the kill chain.
When defenders can anticipate an attacker’s next moves on the kill chain, they can remediate security gaps – ideally before an attack occurs. If it’s an active security event, security teams can use threat modeling to identify potential compromises faster for investigation and rapid remediation.
Benefits of using the MITRE ATT&CK Framework
The MITRE ATT&CK Framework offers several benefits to organizations and cybersecurity professionals. Here are some of the key advantages of using the Framework:
- Improving threat detection and response capabilities: The Framework provides a comprehensive list of tactics, techniques, and procedures used by attackers, which can help organizations better understand and identify potential threats. By mapping their defenses against the Framework, organizations can identify gaps in their security posture and prioritize areas for improvement. This can help them proactively detect and respond to potential attacks, reducing the risk of data breaches and other security incidents.
- Enhancing communication and collaboration among cybersecurity professionals: The Framework provides a common language and framework for communicating about cybersecurity threats and incidents. This can help different teams and stakeholders within an organization work together more effectively and efficiently, improving overall incident response times.
- Supporting security testing and evaluation: By mapping their defenses against the Framework, organizations can identify areas where their defenses may be weaker or ineffective. This can help them prioritize investments in new security technologies or improve existing controls to better protect their systems and data.
Use Cases of the MITRE ATT&CK Matrix
Here are some common use cases of the MITRE ATT&CK Matrix:
Threat Intelligence: The framework provides a standardized language for describing tactics, techniques, and procedures (TTPs) used by threat actors. This allows for easier sharing of threat intelligence between organizations and helps defenders stay up-to-date on the latest threats.
Security Operations Center (SOC) Operations: Cybersecurity professionals can use the matrix to create a comprehensive defense strategy. It helps SOC teams to identify and prioritize threats, develop better detection and response capabilities, and measure the effectiveness of their security controls.
Cybersecurity Training: The matrix can be used in cybersecurity training to help educate employees on the latest threats and how to defend against them. By understanding the tactics and techniques used by attackers, employees can be better prepared to detect and respond to attacks.
Incident Response: The matrix can be used during incident response to quickly assess the scope and impact of an attack. By using the matrix to identify the tactics and techniques used by the attacker, responders can better prioritize their efforts and prevent further damage.
Compliance: Organizations can use the matrix to help meet regulatory compliance requirements by providing a comprehensive framework for assessing their security controls.
How is MITRE ATT&CK Cloud data used with Orca Security?
Not all threats are the same across security environments, and cybersecurity risk management requires a laser-focus on what matters most.
While vendors, particularly traditional EDR vendors, have long focused on ATT&CK as it relates to endpoints, Orca has deeply integrated this data specifically from MITRE’s cloud point-of-view.
Orca uses cloud risk research, threat intelligence, and threat modeling data from established organizations, such as MITRE, to advance our customers’ security postures.
Orca Security uses the MITRE ATT&CK framework in the following two ways to improve cloud security.
- The first is to assist with risk reduction and the tactics and techniques are used to provide contextual information that help show you if and how risks are related to each other. One use of this context is by creating attack path visualizations.Here are some of the specific ways MITRE ATT&CK is used:
- Identify risks that an attacker can use for an attack for each tactic (Orca tags alerts with tactic tags if applicable)
- Identify Cloud risks based on cloud configurations
- Improve prioritization of workload risks, what can be harvested or exploited or used against the customer
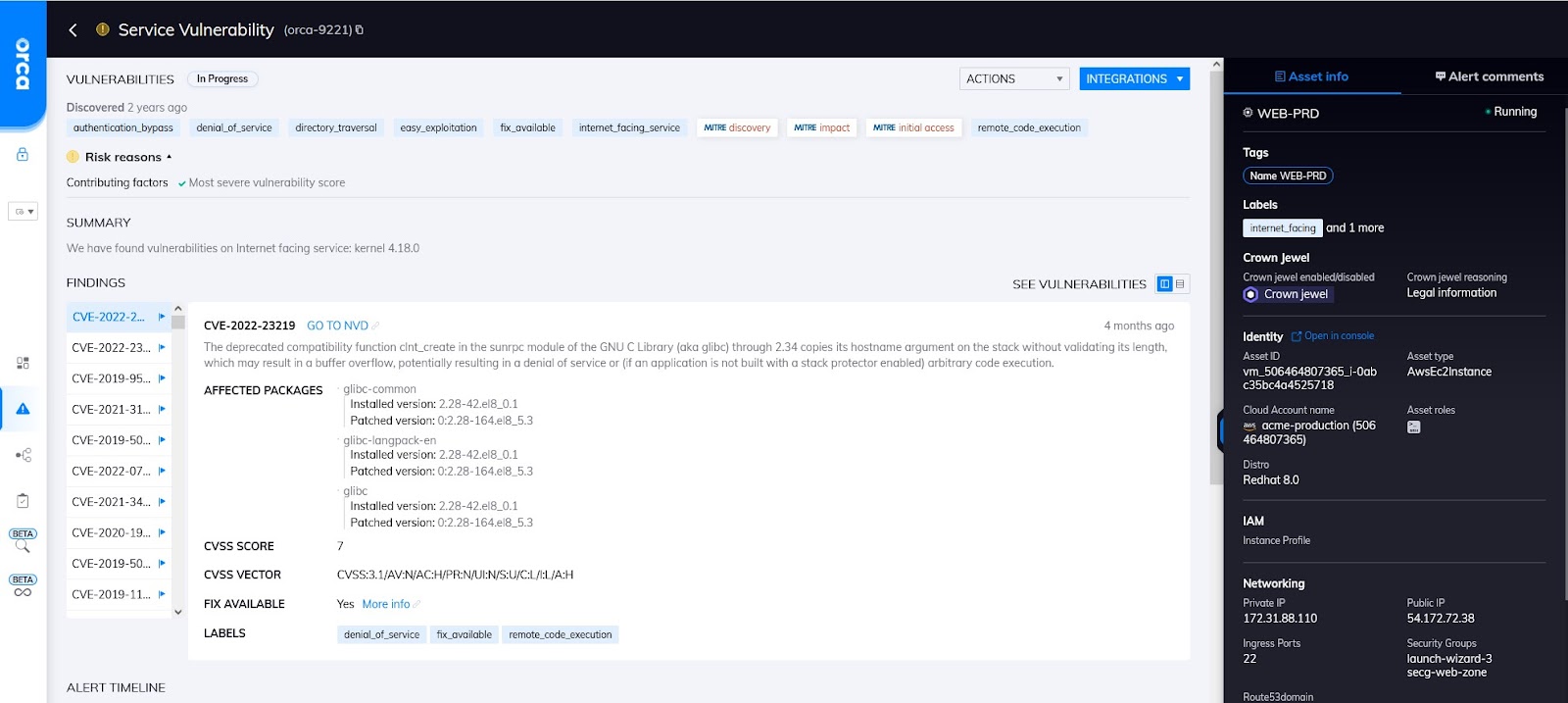
Vulnerability alert with MITRE labels
- Orca also helps with incident response (IR) and investigation. Here are some of the ways Orca uses MITRE ATT&CK data to help with IR:
-
- Identify events from cloud logs for anomalies or malicious events and in which tactic category they fall under
- Ability to see events against resources, which can assist in identifying attacks in progress to stop them before a breach occurs
- Orca uses this additional tactics and techniques information to help contextualize the events, for example only certain vulnerabilities can be used for “initial access” so this extra information improves risk prioritization
A good example of this is that Orca will tell you there is an initial access risk, which is a MITRE tactic, on an internet facing asset with a vulnerability that can be exploited through initial access.
And one of probably the most useful ways that MITRE ATT&CK is used is with attack path analysis, where you can view risks as an interrelated chain, rather than just siloed risks.
MITRE tactics are critical to understanding which combinations are a direct path to your critical assets. Security teams can operate strategically by making sure that the risks that break attack paths are remediated first.
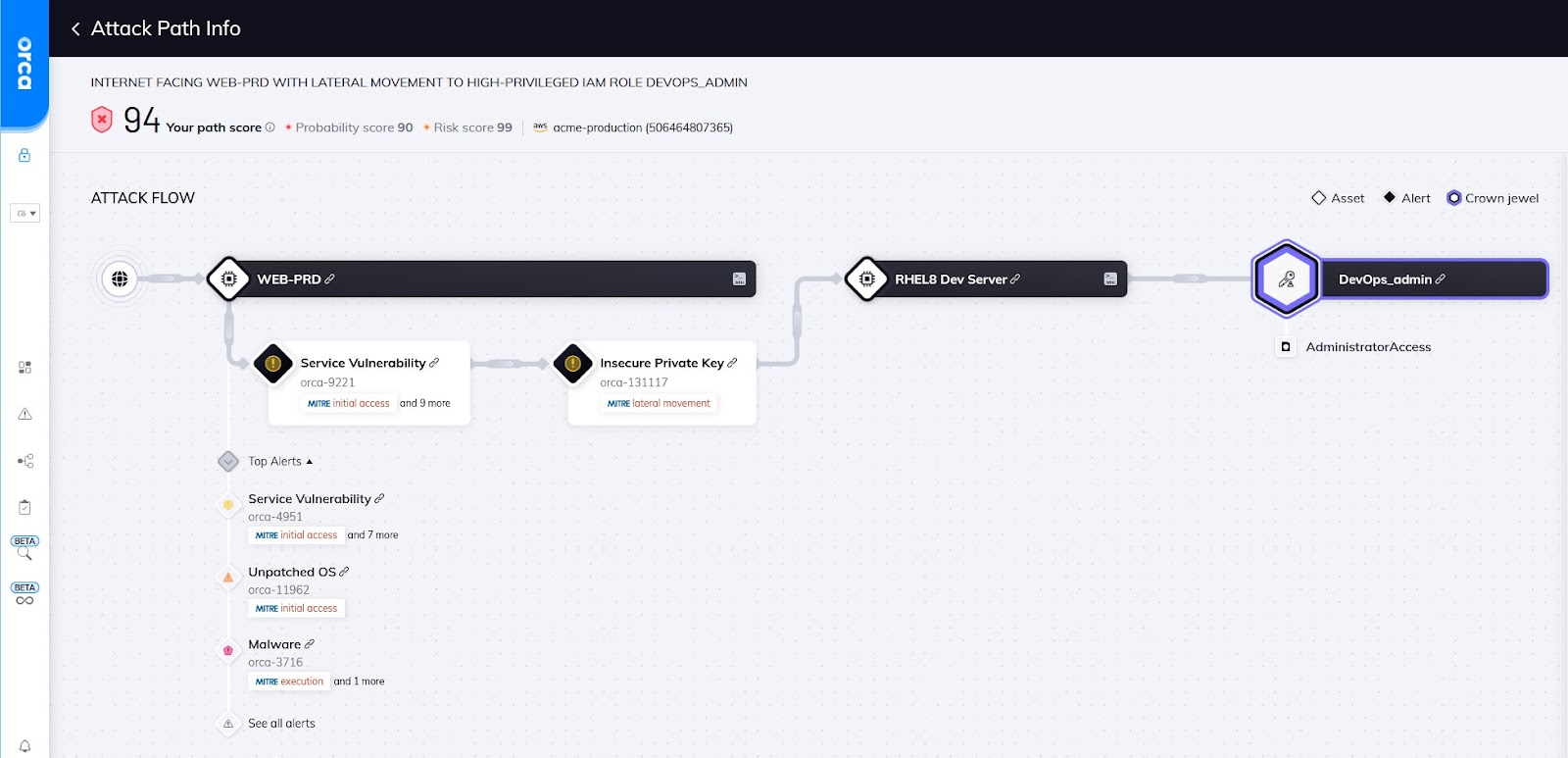
An attack path showing MITRE tags for each link in path
Orca provides a visual representation of each attack path, as shown in the diagram above, along with detailed information on each attack vector.
As you can see in the diagram, every risk in the attack path is tied together using MITRE tactics from “initial” access going through different tactics like “lateral movement” all the way to an asset that has a tag like “credential access”, which is one of the tactics that designates a critical asset.
The attack path visualization includes further information and context for each step in the attack path.
In short, Orca uses attack paths to help teams remediate more strategically, improving efficiency and ensuring that the truly dangerous issues are remediated faster, which in turn helps avoid damaging attacks and data breaches.
How is the MITRE ATT&CK used in the Orca Security Platform
Some of the specific ways that Orca uses the MITRE ATT&CK framework to help with risk prioritization and context:
- We map and tag alerts to MITRE Tactics if applicable
- You can currently search and filter by alert labels and MITRE tactics tags
- Orca has attack paths that use the MITRE tactics; an alert displays a visualization of the attack paths, all the way from initial access to final objective.
Leverage MITRE ATT&CK with Orca Security
Orca leverages MITRE ATT&CK in two ways, 1) to provide greater insight into threats and improve the ability to prioritize risks, and 2) to assist in the ability to respond to and investigate incidents.
Want to learn more about how Orca leverages the MITRE ATT&CK framework and Attack Path Analysis? Visit our Context-Aware Security page, watch the 2-minute video Orca Bytes: Attack Path Analysis, or read our blog on attack path analysis.
Looking to get more hands on? Sign up for a Free Risk Assessment to see how quickly and easily the Orca Security Platform can help you identify and address risks.