Table of contents
Google Cloud is among the top three most popular cloud providers, a market that Gartner predicts will exceed more than $1 trillion (USD) in 2027. Organizations of all sizes and industries depend on Google Cloud Platform (GCP) services to develop cloud-native applications, improve organizational efficiencies, and strengthen their competitive advantage. Yet through this dependence, companies also need Google Cloud security to contend with an ever-growing number of dynamic and distributed cloud risks.
Google Cloud security encompasses a broad collection of security tools, practices, organizations, and people. It aims to help organizations detect and remediate their most critical security risks, as well as meet their compliance requirements.
In this guide, we explore the concept of Google Cloud security, providing an in-depth look at what it entails, the value that it provides, and how your organization can leverage it effectively for optimal cloud security outcomes.
What is Google Cloud security?
Google Cloud security refers to a collection of solutions and practices designed to protect GCP. It includes the native security features of GCP, cloud security solutions offered by third-party vendors, as well as different practices and approaches for addressing risks and compliance issues.
Google Cloud security aims to safeguard the integrity, availability, and confidentiality of cloud infrastructure, applications, data, and the other components. While it helps limit the potential for security incidents, its effectiveness depends on the particular approach organizations take and the technologies they leverage.
Why is Google Cloud security important?
Multiple factors make Google Cloud security not only important, but imperative for organizations, including the following.
Shared Responsibility Model
Public cloud computing functions according to the Shared Responsibility Model, an arrangement between cloud providers and their customers. The model assigns specific responsibilities to each party for protecting public cloud environments from risk.
Three different types of arrangements exist under this model, each based on the business relationship between the two entities. They include:
- Software-as-a-Service (SaaS) or serverless
- Platform-as-a-Service (PaaS)
- Infrastructure-as-a-Service (IaaS)
Regardless of the partnership type, cloud providers must protect cloud infrastructure while organizations must secure their applications and data. In IaaS arrangements, however, organizations own the added responsibility of protecting their operating systems and databases.
Failure to adhere to the Shared Responsibility Model may result in significant consequences, including severe security incidents, financial losses, legal ramifications, regulatory penalties, and reputational damage.
Cloud security risks
Cloud environments are highly susceptible to security risks. Google Cloud security helps organizations prevent, detect, remediate, and respond to risks and avoid a potential security incident, data breach, and more.
Some of the most common risks include the following:
- Vulnerabilities: Security weaknesses in cloud infrastructure or resources that attackers can exploit.
- Misconfigurations: An error or gap in the configuration of cloud infrastructure or resources that results in a security risk.
- Identity and access management risks: A collection of risks that include overly permissive identities, excessive privileges, weak credentials, and more.
- Sensitive data exposure: Exposure of personally identifiable information (PII), personal health information (PHI), intellectual property, financial information, secrets, and more.
- Malware: Malicious code designed to infiltrate and exploit IT systems, leading to various adverse outcomes, including disruption, data breach, lateral movement, privilege escalation, and more.
- API risks: A collection of risks that include a lack of input validation, access control, monitoring and logging, and more.
Components of Google Cloud security
Google Cloud security encompasses several different areas, tools, and practices to minimize risk in Google Cloud environments. They include the following:
- Identity and Access Management (IAM): IAM governs which groups and users can access specific cloud resources. It allows admins to set permissions and audit identity and access activity across an organization.
- Data encryption: Offers Key Management Service (KMS) for cryptographic key management, enabling users to encrypt data with a symmetric or asymmetric key that they control.
- Cloud monitoring and logging: Ingests application data, log data, and data from GCP and non-GCP services to provide insight into the health of applications running on GCP.
- Vulnerability scanning: Scans web applications for vulnerabilities, including Kubernetes, App Engine, and Compute Engine.
- API security: Protects against distributed denial of service (DDoS) attacks, bots, and other API threats. It offers API monitoring, protection, a web application firewall (WAF), and more.
- Threat detection and prevention: Offers Intrusion Detection System (IDS) that detects intrusions, spyware, malware and command-and-control (C&C) attacks on your network. Google Cloud’s threat detection capabilities also monitor cloud logs for malicious and anomalous behavior. Also offers next-generation firewalls to help prevent intrusions.
- Network security and segmentation: Google Cloud offers Virtual Private Clouds (VPCs), or isolated private clouds within a public cloud environment, for network segmentation and network security.
Common Google Cloud security risks
Google Cloud security covers several different types of risks, including the following:
Misconfigurations
An error in the configuration of a cloud resource, misconfigurations can lead to a number of security risks, including exposing sensitive data or assets, providing broad access or permissions, and more. According to a recent study conducted by Gatepoint Research, misconfigurations rank as the top cloud security risk identified by executives.
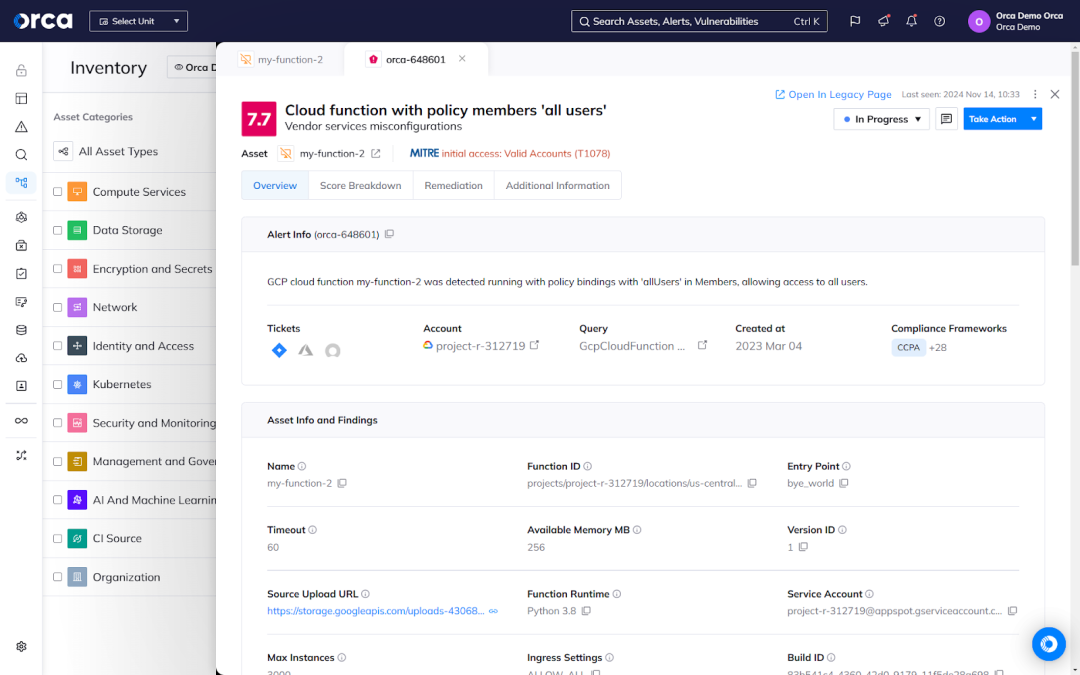
Vulnerabilities
Vulnerabilities represent a top cloud security risk and a security weakness introduced by third-party software or custom code used in cloud environments. On average, security teams can only address 10% of the vulnerabilities they detect each month, which illustrates their prevalence.
Sensitive data exposure
In cloud environments, storage buckets and databases are designed with security configuration settings to securely store sensitive data. However, misconfigurations and other factors often leave sensitive data exposed, including personally identifiable information (PII), personal health information (PHI), financial information, intellectual property, and other information.
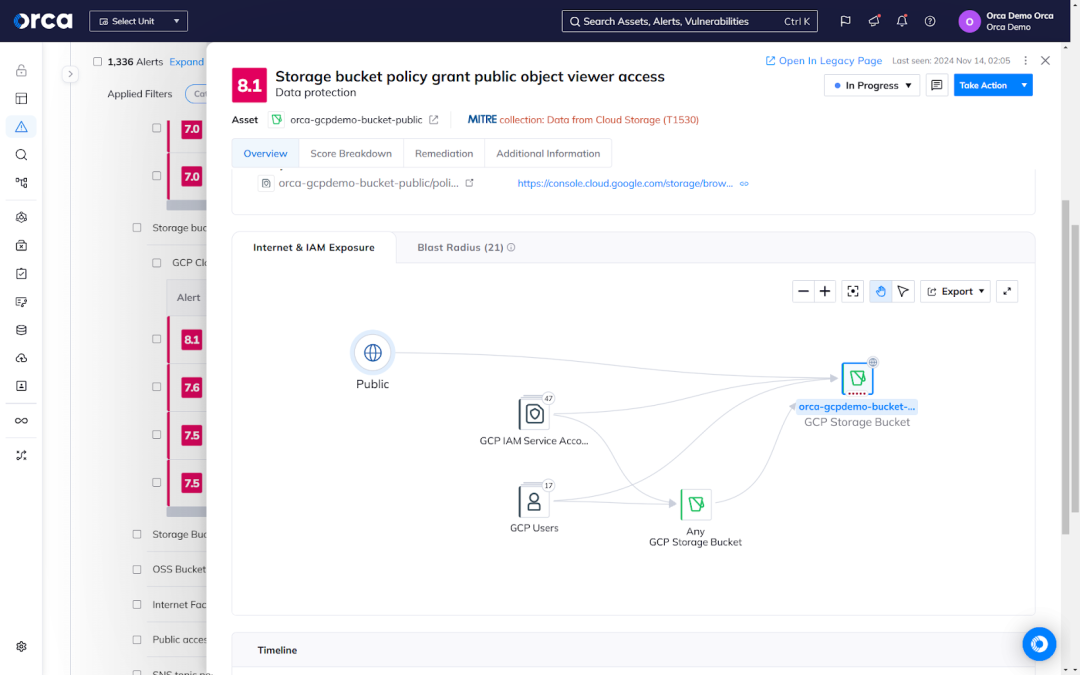
Sensitive data exposure can lead to significant financial, legal, regulatory, and reputational consequences. For example, the EU’s General Data Protection Regulation (GDPR) can fine companies up to €20 million or 4% of their global turnover for failing to protect personal data. Additionally, the average cost of a data breach globally now stands at the all-time high of $4.88 million (USD).
Identity and access risks
Identity and access risks involve the management of digital identities and their associated access and permissions. These risks cover a variety of types, including improper access controls, permissive identities, orphaned roles and accounts, and more. According to the Orca 2024 Cloud Security Report, 72% of organizations have unused IAM roles, which can provide attackers the opportunity to gain unauthorized access to your environment.
Challenges of Google Cloud security
Organizations encounter several challenges in relation to Google Cloud security, including the following.
Lack of multi-cloud compatibility
Many organizations rely on multi-cloud environments supported by more than one cloud provider. For those using the native Google Cloud security features, this can present significant challenges. It requires the use of multiple security tools to ensure adequate coverage, and multiplies the capacity, skill, knowledge, and time requirements of security teams and other departments. Additionally, it often results in limited security coverage, ineffective risk prioritization, compliance issues, and other adverse outcomes.
Limited visibility
Many teams struggle to gain full visibility into their cloud environments when using Google Cloud security solutions. Full visibility refers to both the breadth and depth of coverage of cloud resources and environments. As mentioned in the previous section, native security tools don’t support other cloud provider environments, leading to crucial gaps in visibility for multi-cloud estates.
Third-party security tools can also present similar limitations in terms of visibility. Point solutions solve a particular set of Google Cloud security use cases and require the use of multiple, disparate tools. Poorly integrated platforms present similar blindspots and gaps in visibility.
Lack of holistic risk analysis
In cloud environments, several different types of risks exist and interconnect with one another. For example, a vulnerability in a cloud resource can increase the risk of exposing sensitive data, just like one infected with malware can raise the severity of an IAM risk. Organizations often find it challenging to acquire solutions that can detect all types of risks and analyze their combined impact on their cloud environment.
Risk prioritization
According to the Cloud Security Alert Fatigue Report, nearly 60% of security teams report receiving 500 or more alerts per day, and more than half say they miss critical alerts on a daily or weekly basis. These alarming statistics point to a challenge facing most security teams: the ability to prioritize critical risks.
Effective risk prioritization requires full visibility into a cloud estate and the ability to detect different types of risks holistically. This remains a challenge for Google Cloud security teams.
Best practices for Google Cloud security
Several best practices can help you optimize your Google Cloud security, including the following.
Adopt a Cloud-Native Application Protection Platform (CNAPP)
According to Gartner, CNAPPs play a crucial role in helping organizations achieve their zero-trust goals. A cloud security technology, CNAPPs alleviate many of the challenges organizations encounter with Google Cloud security. Some advanced CNAPPs offer full visibility into organizations’ dynamic and distributed cloud environments, the ability to detect all different kinds of cloud security risks, as well as the ability to analyze risks holistically and prioritize them accordingly.
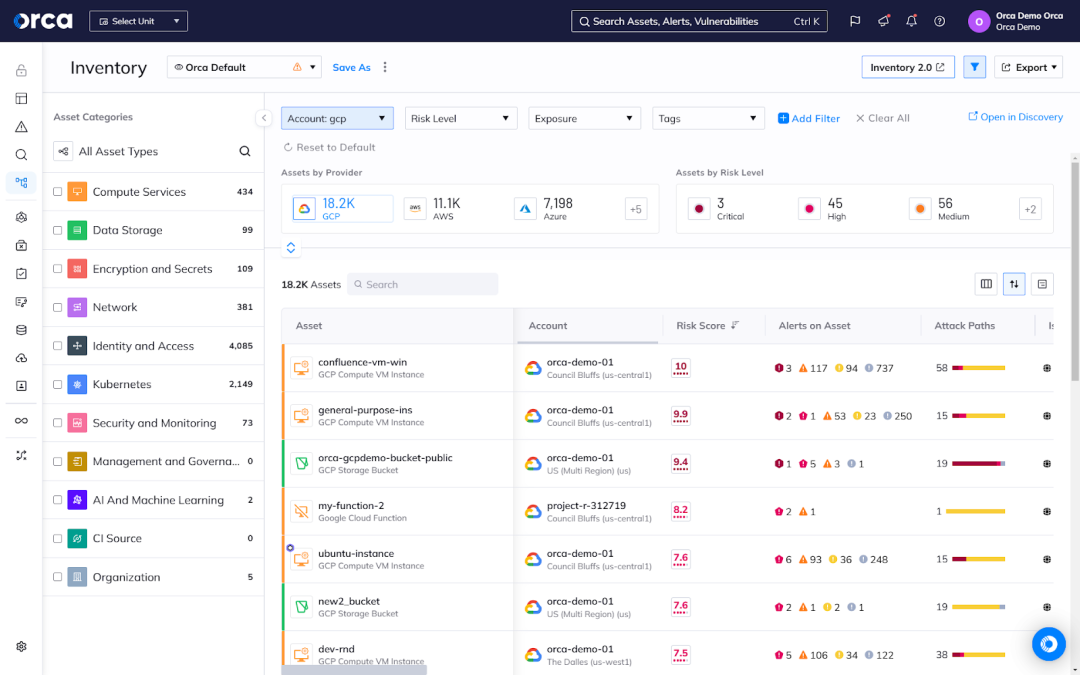
Additionally, these platforms often support cloud estates involving more than one cloud provider and environment. This enables organizations to effectively remediate their most critical and exploitable risks, reduce alert fatigue, and minimize constraints on time and capacity.
Some advanced CNAPPs also promote enhanced collaboration and reduce the friction between security and development teams, which must work together to fix cloud-native issues.
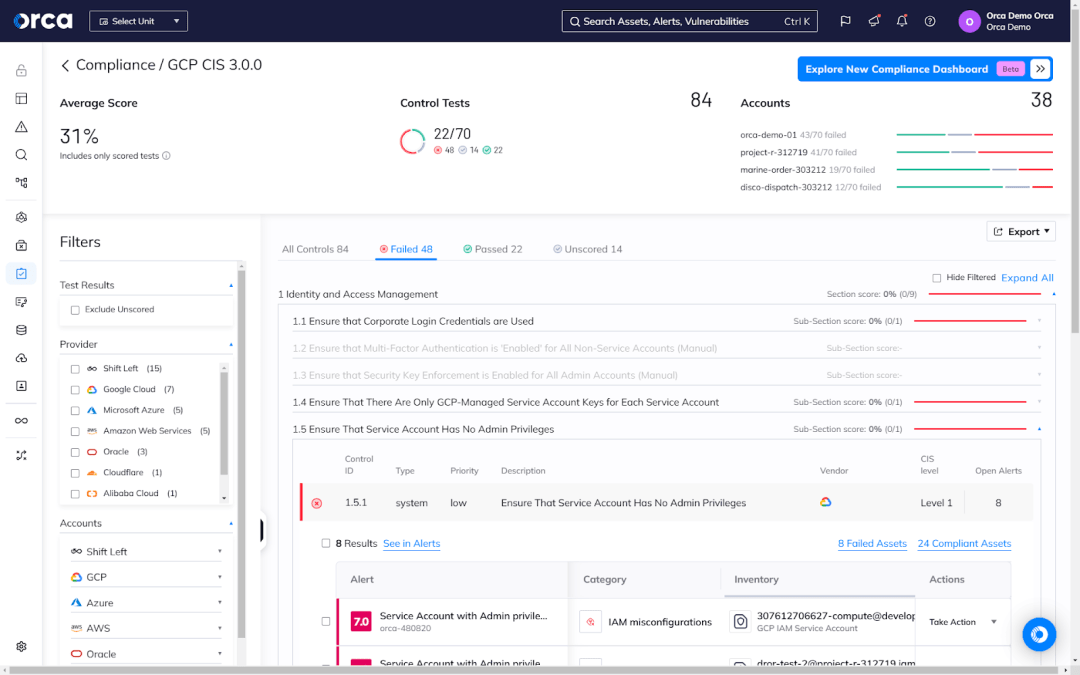
Enable compliance with CIS Benchmarks for Google Cloud
Covering best practices for securing Google Cloud environments, the CIS Google Cloud Computing Platform Foundations Benchmark is a helpful tool for organizations. Many CNAPP solutions offer digital versions of this framework to help you adhere to its controls as well as monitor and report on their status.
Best practice is to enable the framework and incorporate it into your regular workflows to ensure you continuously meet Google Cloud security best practices.
Shift to a DevSecOps framework
According to Gartner, organizations experience fewer security incidents when adopting a DevSecOps framework. This model incorporates security into every phase of the application and software development lifecycle (SDLC). It aims to prevent security risks from reaching a production environment, as well as making it faster and easier to remediate risks in runtime.
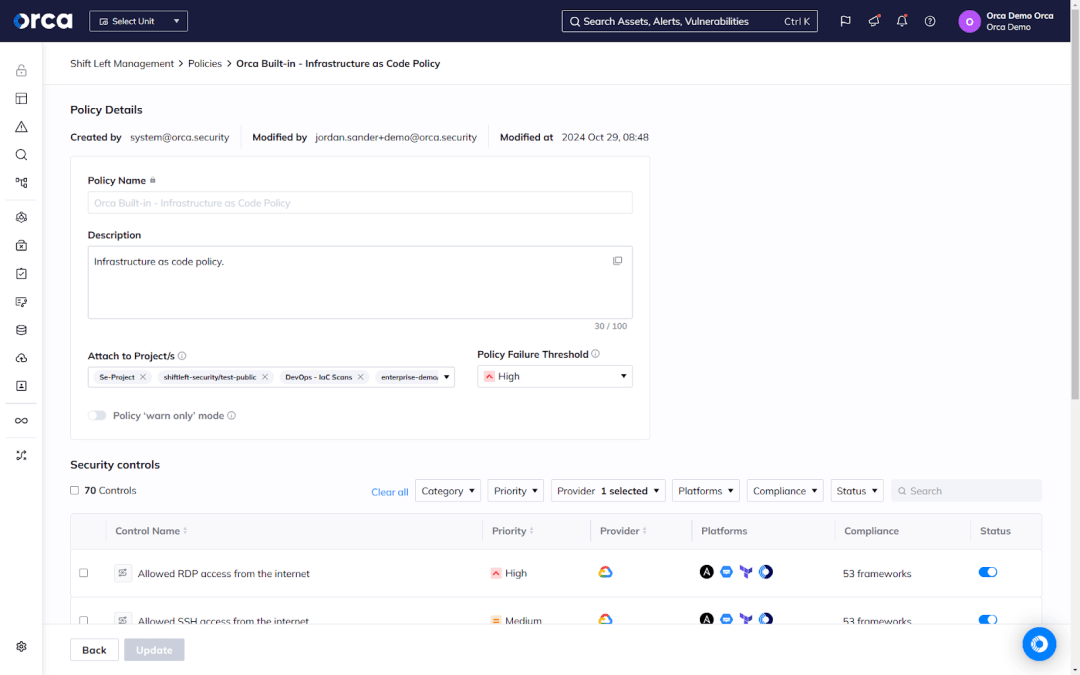
More advanced CNAPP solutions support DevSecOps through several features. This may include establishing developer-friendly security policies that incorporate security checks early in the SDLC, blocking risky builds and informing developers of issues. It also may include integrations that make it easier for security teams and developers to collaborate on risk remediation, while ensuring both can use their preferred tools and workflows.
Additionally, some CNAPPs clearly link cloud resources to their code origins to make it easier for developers to fix the source of runtime risks in development, accelerating the mean time to resolution (MTTR) as well as preventing the recurrence of future issues. For example, by addressing a flawed IaC artifact, development teams can prevent risks from propagating in production.
Utilize automations
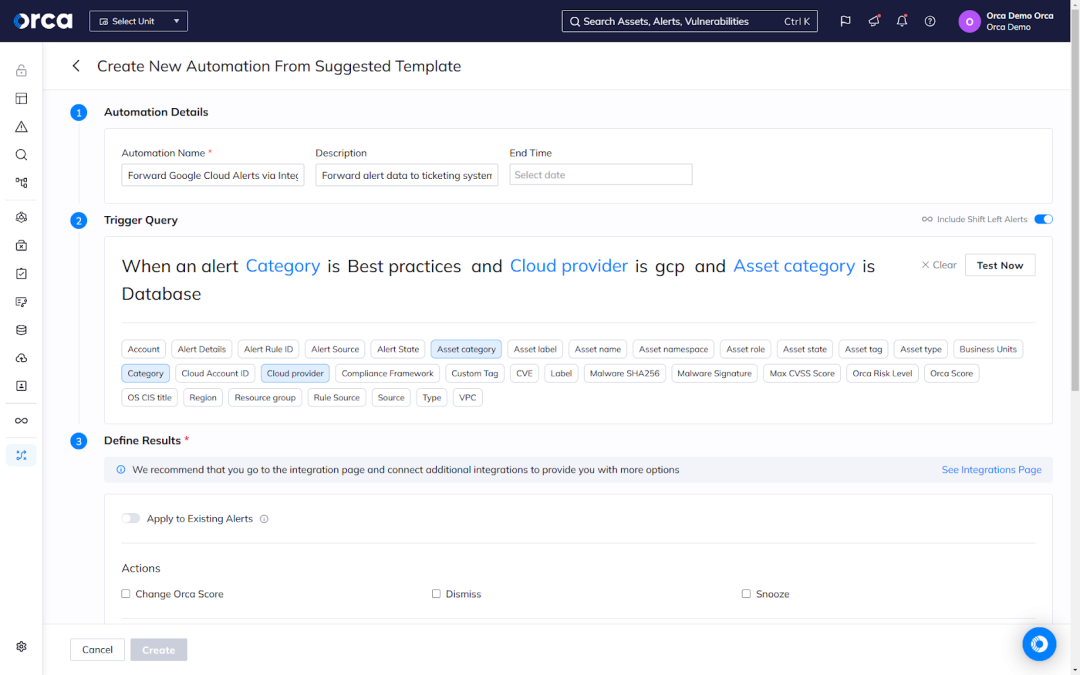
Many security tools offer the ability to configure automations, a feature that performs a task without human intervention according to predefined criteria. Automations can save security teams much-needed time and capacity to focus on other priorities. Best practice is to inventory the automations available in your cloud security solution and enable them as early as possible.
You should only use automations for routine and repetitive tasks that don’t require the oversight or involvement of your teams. For example, you can build an automation that automatically creates a ticket each time a particular alert surfaces. This saves security teams from needing to manually create and assign a ticket in the system used by development teams. It also means developers can receive the ticket sooner, accelerating their time to resolve an issue.
Other examples include automatically generating notifications, triggering automated workflows in SIEM and SOAR solutions, and more.
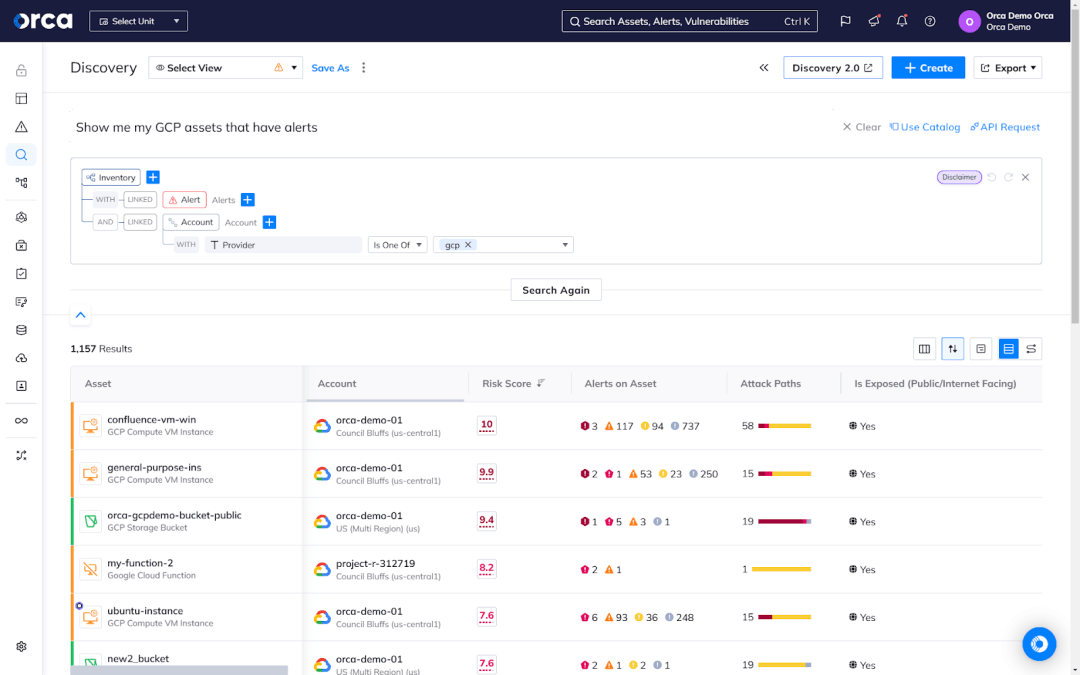
Leverage AI-driven security features
Many cloud security vendors have introduced features that leverage AI to help users streamline critical tasks. One example includes searching cloud environments by asking questions in plain language rather than the technical query language of each cloud provider. In addition to boosting productivity, these features can also compensate for knowledge deficits, such as unfamiliarity with query language of cloud providers.
Best practice is to learn about all AI-driven security features offered by your cloud security solution and to adopt them as early as possible. This enables you to maximize the productivity gains and time savings that these capabilities provide.
The future of Google Cloud security
Several trends continue to shape the future of Google Cloud security, including the following.
CNAPP adoption
According to Gartner, 60% of businesses that don’t invest in CNAPP will fail to reach zero trust goals by 2029. As organizations increasingly depend on cloud computing out of necessity, they need technology that provides full visibility, comprehensive detection, and unified cloud security across multi-cloud environments. This comes from a CNAPP product, which overcomes the disadvantages of point solutions and loosely integrated platforms.
AI innovation and risks
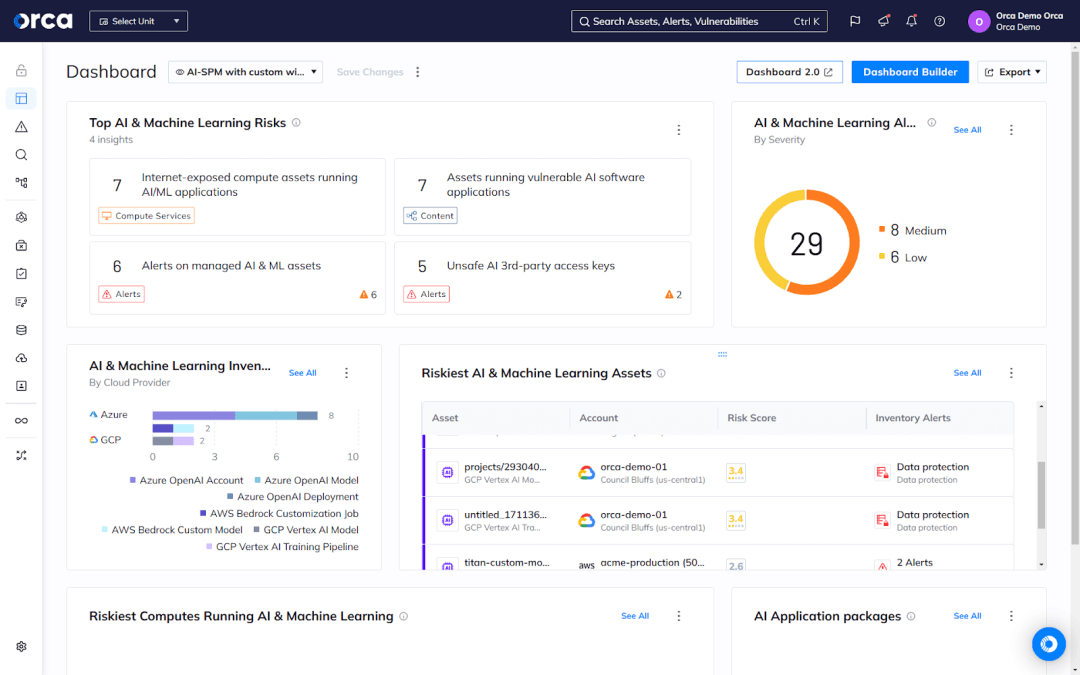
Most organizations are developing custom AI applications using cloud-native services and environments, a key finding from the Orca 2024 State of AI Security Report. This figure signals a significant and long-term investment in AI cloud computing. Yet it also points to a new and growing source of security risks in cloud environments. For example, the State of AI Security Report revealed that 62% of organizations have deployed an AI package with at least one CVE.
AI Security Posture Management (AI-SPM) technology has emerged to help organizations properly configure cloud provider AI services, as well as secure their AI models, packages, and data. Some advanced CNAPP solutions now offer AI-SPM solutions, which should become more prevalent and advanced as investment in AI innovation continues to grow.
AI-driven security
AI is not only introducing risk into the cloud security equation. It continues to help organizations compensate for shortages of time, resources, knowledge, skills, and capacity. Many cloud security vendors are leveraging AI in their products and services to help users accelerate and automate critical tasks. The future promises more investment and advancement in this area.
For example, the Orca Cloud Security Platform offers AI-Driven Search and AI-Driven Remediation. The first feature saves users from needing to learn the complex query languages of their cloud providers. Instead, they can ask a question in plain language to better understand any of their cloud assets or risks across their entire estate.
The second feature enables users to generate high-quality remediation code and instructions tailored to their remediation tool, giving them a head start and solid foundation for remediation work, even when lacking experience or expertise.
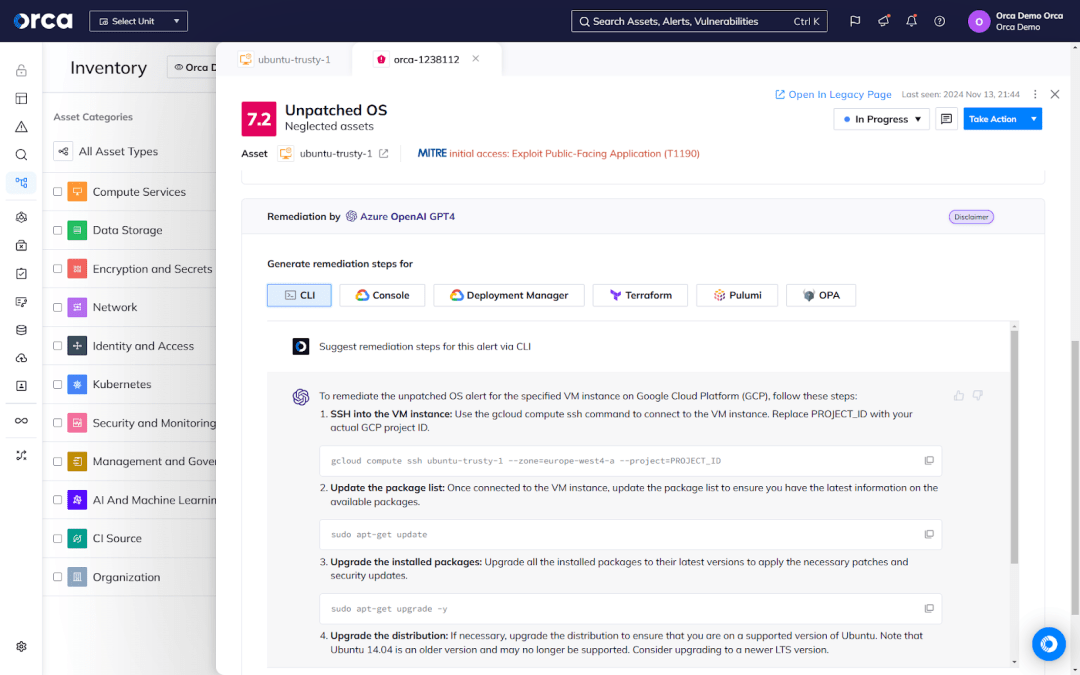
About the Orca Cloud Security Platform
The Orca Cloud Security Platform is an agentless-first CNAPP that enables organizations to optimize their security and compliance across the multi-cloud environments of Google Cloud, AWS, Azure, Oracle Cloud, Alibaba Cloud, and Kubernetes. A true CNAPP, the Orca Platform provides full visibility, comprehensive risk detection, effective risk prioritization, and quick time to value across the full application lifecycle.
Orca is a Google Advantage Partner that supports more than 100 Google Cloud services and products, including Chronicle SIEM/SOAR, Security Command Center, Pub/Sub, SSO, and Vertex AI. Orca is available for purchase in the Google Cloud Marketplace.
To see how the Orca Cloud Security Platform can help you fortify your Google Cloud security, schedule a personalized demo with one of our experts.
Conclusion
As dependence on cloud computing increases, so does the importance of Google Cloud security, which aims to protect one of the most popular cloud platforms available today. Encompassing the native tools and services offered by GCP and technology provided by third-party vendors, Google Cloud security helps organizations protect against prominent security risks. Depending on the approach, however, it may also come with significant challenges, including lack of multi-cloud compatibility, full visibility, and risk prioritization, to name a few.
To fortify Google Cloud security, you should look to implement best practices such as adopting CNAPP technology, embracing a DevOps framework, leveraging automated features, and leveraging AI security features.
You should also prepare for a future in which CNAPP solutions, AI tools, and AI risks play a more prominent role in Google Cloud security and beyond.
FAQs
What is GCP cloud security?
GCP cloud security is a collection of tools, practices, and strategies for securing your Google Cloud Platform. GCP cloud security encompasses both native security features offered by Google Cloud as well as those provided by third-party cloud security vendors. It also outlines the specific responsibilities for protecting Google Cloud between Google and their customers, a concept known as the Shared Responsibility Model.
What are the main security risks of Google Cloud?
Common security risks for Google Cloud include:
- Vulnerabilities
- Misconfigurations
- Sensitive data exposure
- IAM risks
- API risks
- AI risks
- Malware
What are the key benefits of Google Cloud security?
Google Cloud security offers a number of important benefits, including:
- Improved security posture
- Support for Shared Responsibility Model
- Prevention of security incidents
- Protection for business continuity
- Preservation of business reputation
- Insurance against financial losses from security incidents
- Avoidance of regulatory fines and penalties






