Table of contents
According to Gartner, the market for public cloud services is expected to reach $1.28 trillion (USD) by 2028, at a compound annual growth rate of 20%. All signs suggest that cloud computing has made the transition from revolutionary to essential technology. That’s welcome news for cloud service providers (CSP) like Oracle Cloud. Yet for organizations leveraging the platform, unlocking its enormous benefits calls for the right approach to Oracle Cloud security.
In this post, we dive deep into the topic of Oracle Cloud security to explore its importance, components, considerations, and more. We also look at best practices that can help you enhance your Oracle Cloud security.
What is Oracle Cloud security?
Oracle Cloud security encompasses a comprehensive set of technologies, services, and practices designed to protect data, applications, and infrastructure associated with Oracle’s cloud computing services. This multi-layered approach includes various security measures offered by Oracle Cloud and third-party vendors such as encryption, identity and access management (IAM), continuous monitoring, and much more—all aimed at safeguarding cloud resources and infrastructure and ensuring the integrity of cloud-based operations.
Today, the significance of Oracle Cloud security cannot be overstated. Businesses increasingly rely on cloud services for their critical operations, which means protecting these environments from cyber attacks is paramount. Robust security measures not only help prevent security incidents such as unauthorized access, but also maintain business continuity, ensure regulatory compliance, and preserve customer trust.
Oracle Cloud offers a variety of security services to its customers, including the following pillars:
- Customer isolation: Provides an environment fully isolated from other tenants and staff of Oracle Cloud.
- Data encryption: Secures data at rest and in-transit with encryption and key management services.
- Security controls: Limits access and permissions to promote the principle of least privilege (PoLP).
- Visibility: Provides visibility through comprehensive logging and monitoring, facilitating cloud detection and response (CDR) and auditing requirements.
- High availability: Offers resilient data centers that can scale on-demand.
- Secure infrastructure: Offers a secure underlying cloud infrastructure backed by adherence to strict security standards, the use of effective security controls, and more.
Why is Oracle Cloud security important?
Here are the three main reasons why Oracle security is important:
1. Shared Responsibility Model
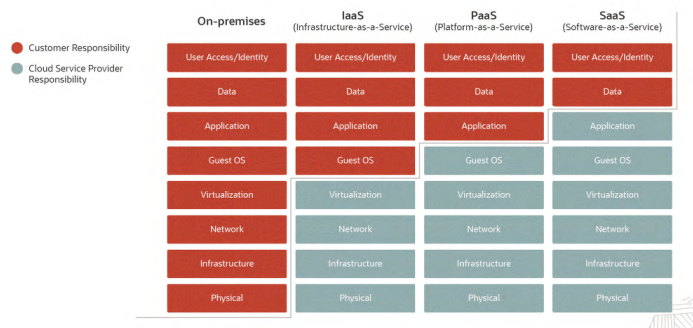
A fundamental aspect of Oracle Cloud security is the Shared Responsibility Model, which clearly delineates the security responsibilities of Oracle and its customers. Generally, this model assigns Oracle Cloud the task of securing the underlying cloud infrastructure, while making its customers responsible for securing their applications, data, identities, and access controls. This collaborative approach enables effective risk management.
The specific responsibilities of this model, however, depend on the type of cloud service delivery model, with three options available: Infrastructure-as-a-Service (IaaS), Platform-as-a-Service (PaaS), and serverless. IaaS gives customers the most ownership of their cloud environments and responsibility for security, followed by PaaS and serverless.
2. Risk mitigation and prevention
Many of the solutions and measures employed by Oracle Cloud security aim to address pre-breach risk—opportunities that could lead to a security incident but haven’t yet. These solutions help you stay proactive in mitigating attacks by detecting all your security risks, prioritizing those most critical based on business impact, and facilitating their timely remediation. This eliminates weaknesses in your attack surface before attackers can exploit them, minimizing the chances a risk results in a data breach or other severe security incident.
Additionally, some Oracle Cloud security solutions, particularly those offered by third-party vendors, focus on the prevention of risk by introducing security measures early in the software development lifecycle (SDLC). These measures include guardrail policies that detect issues in development and block risky projects from getting deployed to a runtime environment.
In these ways, Oracle Cloud security helps organizations avoid the serious security incidents and the financial, operational, legal, regulatory, and reputational consequences that may accompany them.
3. Business continuity
Oracle Cloud security aims to keep your business running—arguably its most important benefit to your organization. It helps protect systems from exploitation that can result in downtime and disruption to your daily operations. It also helps prevent high-profile incidents such as data breaches that can jeopardize the short- and long-term viability of your enterprise. For example, a breach can result in customer churn and lost business opportunities due to a lack of trust and confidence.
Oracle Cloud security also helps you meet compliance standards and avoid costly regulatory violations that can threaten your license to operate. In many ways, Oracle Cloud security serves as necessary insurance for your business continuity.
Common Oracle Cloud security risks
As organizations increasingly adopt Oracle Cloud, they encounter various security risks and challenges that must be addressed to maintain a robust security posture. Understanding these risks is essential for implementing effective security measures.
Misconfigurations
Misconfigurations rank as a top risk in cloud environments, a reality confirmed by most executives in a recent study. These security gaps or issues arise from the improper set up of security settings offered by cloud service providers (CSPs) such as Oracle Cloud. Here, “improper” can involve human error or lack of awareness. For example, users may use default settings when deploying cloud resources out of convenience rather than setting up a more secure configuration. Alternatively, users may not know about changes to CSP services which may result in misconfigurations.
Due to their prevalence and potential impact, organizations need continuous monitoring, detection, and remediation capabilities to mitigate misconfigurations in their environments.
Vulnerabilities
Like misconfigurations, vulnerabilities rank as a top security risk in the cloud. Vulnerabilities arise from outdated software, open-source components, software flaws, and more. These security weaknesses give attackers an attractive target for exploitation, enabling security incidents such as unauthorized access, lateral movement, and data exfiltration.
To address vulnerabilities effectively, organizations need to implement a vulnerability management program that can detect, prioritize, and remediate the most critical vulnerabilities. Prioritization is a key consideration for vulnerability management, especially considering that security teams can only address approximately 10% of the vulnerabilities they detect each month.
Overprivileged identities
In cloud environments, identities refer to both users and non-human identities (NHI), which are each assigned roles and associated permissions. When these permissions are excessive—more than what the user or NHI needs to do their job—they give attackers an opportunity to exploit them. For example, excessive permissions may allow attackers to gain unauthorized access, laterally move, elevate privileges, or compromise a high-value asset, such as sensitive data.
Minimizing the risk of overprivileged identities calls for adopting and enforcing policies that support the principle of least privilege (PoLP), as well as monitoring, detecting, and rightsizing excessive permissions of existing identities.
Sensitive data exposure
Sensitive data exposure represents a key cloud security risk and one that commonly occurs due to misconfigurations, poor coding practices, and more. The 2024 State of Cloud Security Report found that 20% of organizations have a public-facing database with sensitive data. This risk increases the chances for data exfiltration, ransomware, reputational damage, and regulatory penalties. The General Data Protection Regulation (GDPR), which protects consumer data in the European Union, can fine organizations for data privacy violations up to €20 million, or 4% of their global annual revenue, whichever is higher.
The risk for sensitive data exposure requires organizations to properly configure cloud assets such as storage buckets and databases. Additionally, they should use proper encryption for data at rest and in transit, continuously monitor for sensitive data exposure, and remediate risks in a timely manner.
Challenges of Oracle Cloud security
Organizations face several unique challenges when securing their Oracle Cloud environments. Addressing these challenges is crucial for enhancing overall security.
Full coverage, especially for multi-cloud environments
Cloud environments are highly dynamic and distributed, with resources constantly spinning up and turning down. This makes it difficult for security teams to understand what their cloud environments contain.
Many solutions only contribute to the problem. For example, point solutions, poorly integrated platforms, and legacy tools see only part of the picture, creating critical blindspots that inhibit effective cloud security.
In multi-cloud environments supported by multiple CSPs, the challenge increases. These environments lead to more visibility gaps and require more of security teams, such as unique technical expertise of each CSP. As a result, organizations need technology that can unify cloud security, creating a single and clear view of all risks and resources regardless of how many CSPs and environments are involved.
Comprehensive risk detection
Cloud environments present a multitude of different risks. These range from misconfigurations and vulnerabilities, to lateral movement risks and malware, to identity and entitlement risks, to much more. Organizations need the ability to not only detect each of these risks, but do so holistically and contextually.
Holistic analysis enables organizations to understand the relationship between different risks and cloud resources, analyze criticality according to business impact, and prioritize remediation accordingly. Point solutions and legacy tools don’t provide comprehensive detection due to incomplete coverage or specialization in limited areas of cloud security. This helps explain why most security teams report missing critical alerts on a daily or weekly basis, according to the Cloud Security Alert Fatigue Report.
This also calls for organizations to acquire technology that unifies cloud security for Oracle Cloud and other CSPs.
Cloud compliance
Compliance represents an enormous challenge for organizations, especially in the cloud. Cloud resources and risks constantly change, leading to compliance issues that surface regularly. Meanwhile, organizations must continually identify, track, monitor, address, audit, and report on their adherence to an extensive list of controls that may involve more than one framework. These demands can overwhelm organizations and distract them from revenue-generating activities or lead to compliance violations. This illustrates the need for compliance solutions that can automate many of the functions of compliance across its lifecycle.
Best practices for Oracle Cloud security
To enhance Oracle Cloud security, organizations should adopt a set of best practices that address the unique challenges of cloud environments. Here are key strategies to consider:
1. Learn the Shared Responsibility Model
To eliminate any potential security gaps, understand what aspects of security you own according to the Shared Responsibility Model. Note that this model depends on the type of cloud service delivery (IaaS, PaaS, or serverless) as well as CSP. Best practice is to learn about your specific responsibilities before entering into an agreement, which enables you to fully grasp your obligations and fulfill them successfully.
2. Inventory cloud resources
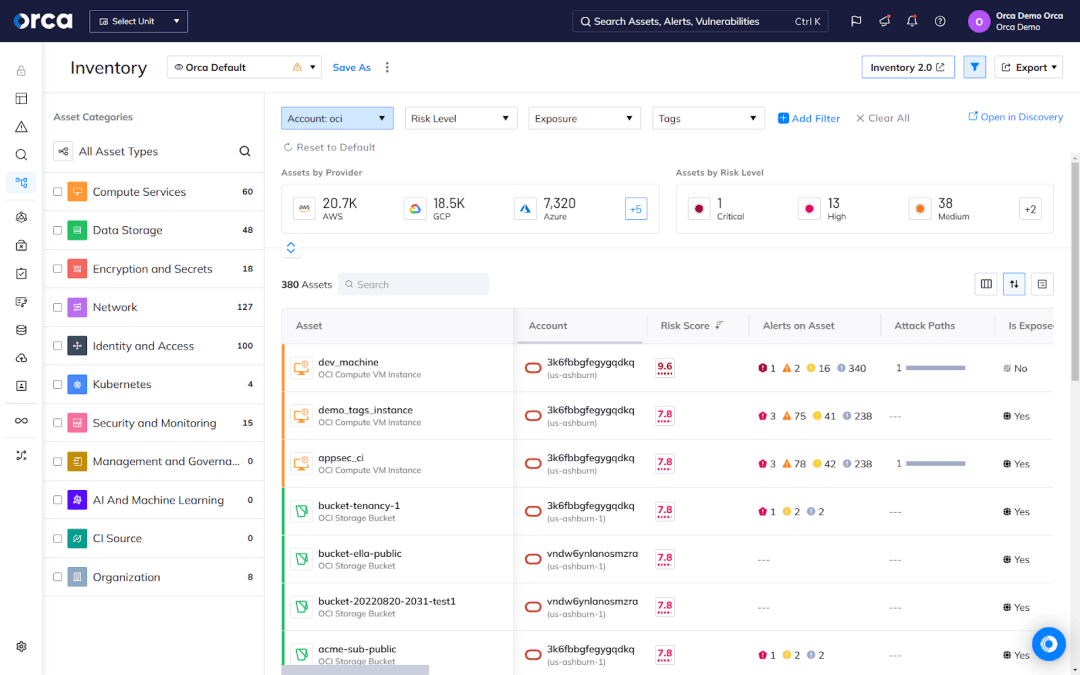
You can only protect what you can see. That explains why you should inventory all the cloud assets in your environment and establish the capability to detect new ones created in the future. This should encompass all types of cloud resources (e.g., compute services, data storage, users and groups, etc.) and span the entirety of your cloud estate. Best practice is to acquire a third-party solution that offers this capability, as this enables you to support multi-cloud environments offered by Oracle Cloud and other CSPs.
3. Prioritize risks by business impact
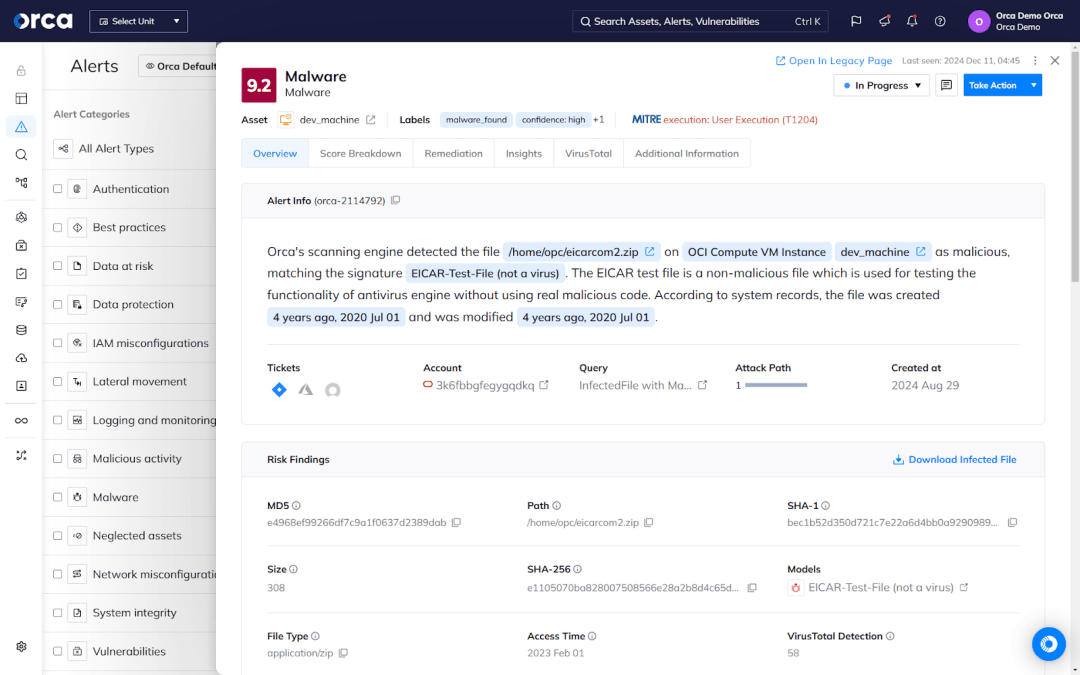
Once you gain full coverage, use your cloud security solution to detect and prioritize the risks in your environment. Here, priority should be based on business impact, not static risk factors or an incomplete risk analysis. Instead, each alert should base criticality on the toxicity of a risk relative to the broader cloud ecosystem. Once prioritized, your teams should remediate your most critical risks immediately, while addressing less severe risks at a later time.
4. Adopt a DevSecOps approach
Once you begin prioritizing your most critical risks, look to enhance security in the short- and long-term. This happens by adopting a DevSecOps framework, a software development process that embeds security into every phase of the application lifecycle.
DevSecOps works by establishing effective methods of collaboration between security, DevOps, and development teams for tasks such as remediating risks in runtime. DevSecOps depends on tight integrations that enable this coordination to happen seamlessly and within the preferred tools and environments of all teams.
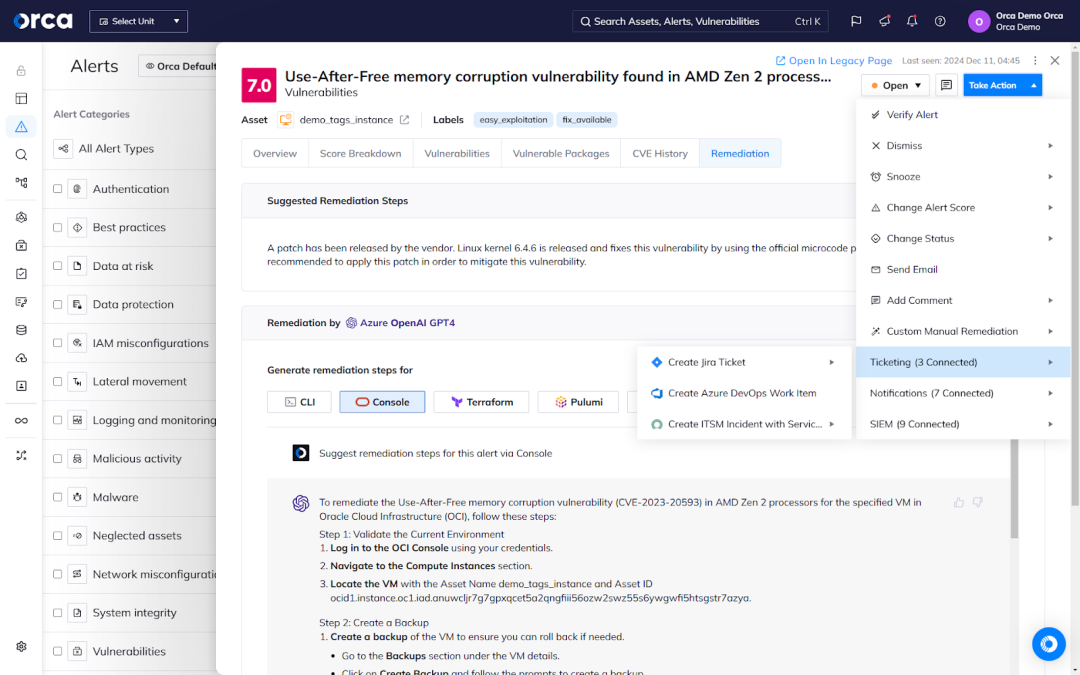
Additionally, DevSecOps also involves establishing security policies that catch issues in the early stages of the software development lifecycle (SDLC) and before they get released to production. These policies, known as “guardrails,” prevent developers from deploying risky builds in runtime.
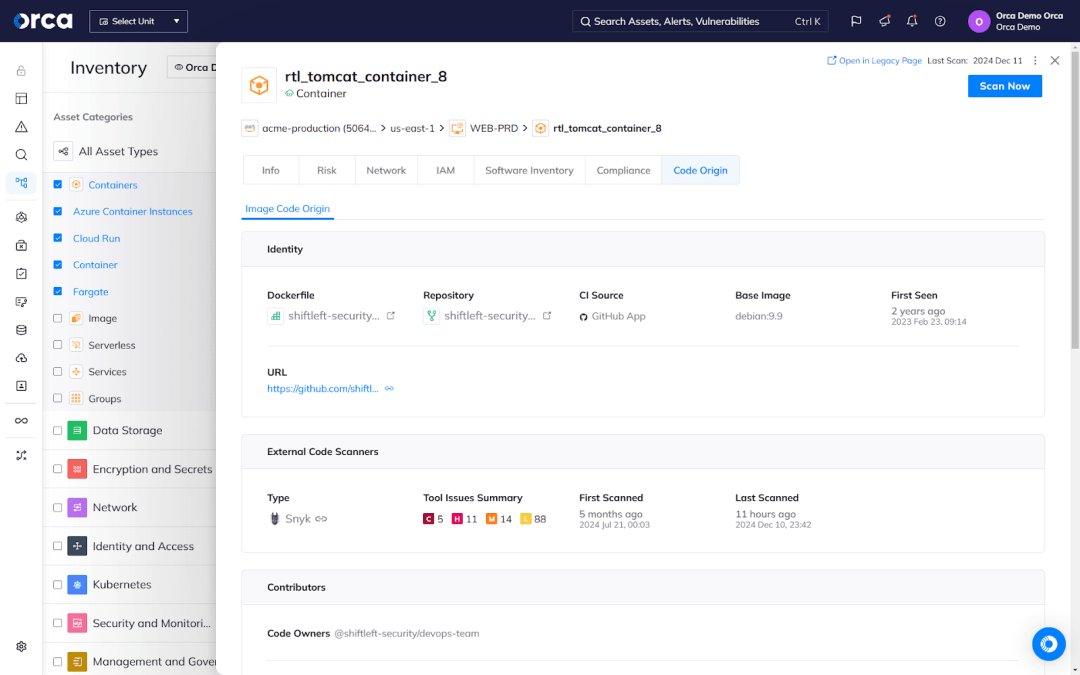
DevSecOps also involves linking correlating risks in production with their code origins for faster remediation and improved risk prevention. This means security teams can see the relevant metadata for cloud risks originating from a flawed development artifacts—such as an Infrastructure-as-Code (IaC) artifact or container image—including its code owner, source code repository, and more.
This saves security teams from tracking down developers who can fix issues, while eliminating a key source of runtime risks. A single flaw in an IaC artifact or container image can propagate hundreds or thousands of risks in production environments.
5. Automate compliance
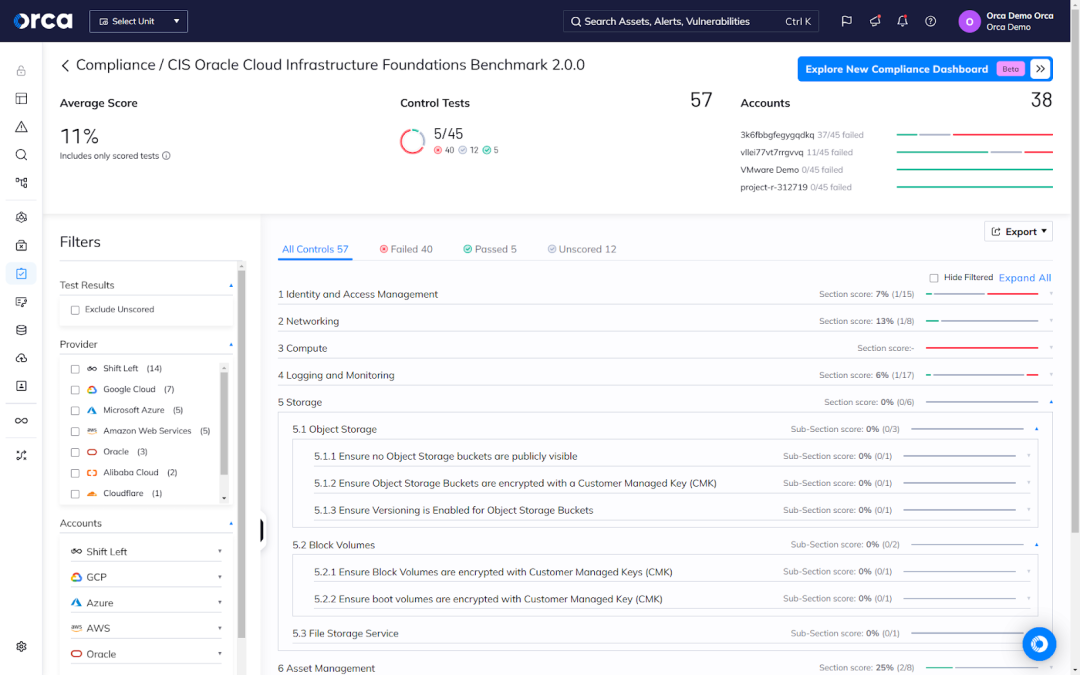
When it comes to cloud environments, compliance demands automation. That’s why you should look to automate as much of the compliance lifecycle as possible. This includes key aspects of compliance documentation, monitoring, auditing, reporting, and more. Below are examples of automated features available in some compliance and cloud security solutions:
- Documentation: Up-to-date and built-in templates covering major frameworks and industry standards.
- Compliance monitoring: Automated workflows that generate notifications to relevant teams when defined conditions are met.
- Compliance auditing: Automated compliance scoring that conveys overall adherence to a specific framework, along with filters for viewing and isolating areas of non-compliance or compliance within a framework.
6. Use a Cloud-Native Application Protection Platform
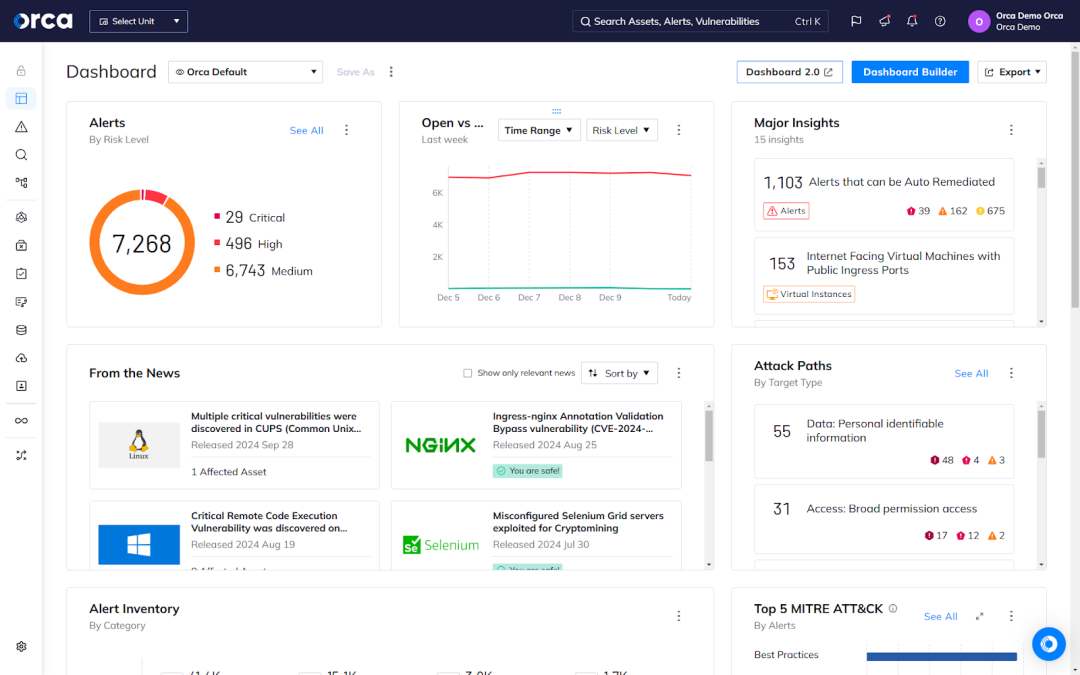
Cloud-Native Application Protection Platforms (CNAPPs) have emerged as the preferred solution for cloud security. CNAPPs consolidate multiple point solutions, offer full cloud coverage, and provide comprehensive risk detection. These qualities create the conditions for effective risk prioritization and remediation, enabling security teams to address their most critical security risks, accommodate scarce resources, and limit alert fatigue.
To enhance your Oracle Cloud security, look to adopt a CNAPP that supports multi-cloud environments with a comprehensive set of native capabilities. Examples include workload protection, security posture management, infrastructure entitlement management, vulnerability management, and more. Additionally, ensure this technology offers a complete feature set for multi-cloud compliance, including built-in frameworks that cover major regulations and industry standards.
The future of Oracle Cloud security
As technology evolves, so does the landscape of Oracle Cloud security. Let’s delve into the emerging trends shaping cloud protection’s future.
AI-driven security
Security teams notoriously face a shortage of time, capacity, and technical expertise. That may explain why many cloud security vendors continue to introduce new features for AI-driven security. These help security teams work faster and more effectively, without the expertise or experience normally required. For example, AI-driven features allow teams to remediate risks faster and easier, search cloud environments without using technical query languages, and more.
Advances in AI technologies and cloud computing are paving the way for increased investments in AI-driven security. We can expect to see continued enhancements for existing features, as well as new and expanded capabilities that serve more cloud security use cases.
AI innovation and risks
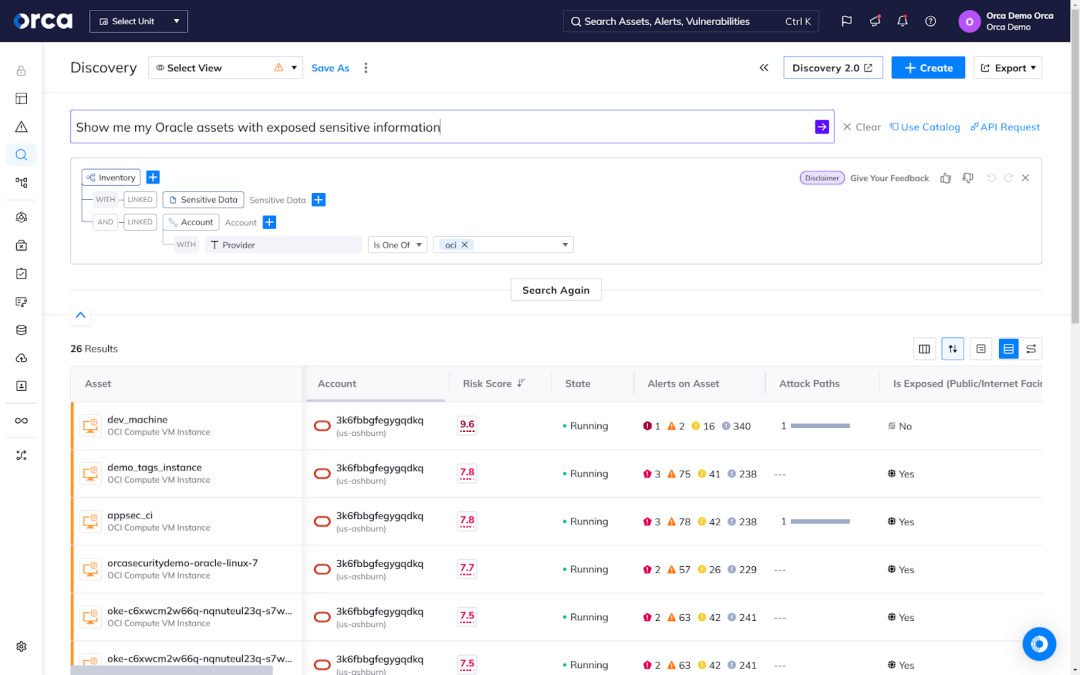
While AI can help enhance the work of security teams, it can also lead to important risks and challenges. AI Security Posture Management (AI-SPM) has emerged as a key field in cloud security, one designed to protect AI innovation in cloud services. Today, more than half of organizations are leveraging AI services in the cloud for custom AI development, according to the 2024 State of AI Security Report. That figure is estimated to rise, increasing the demand for AI-SPM capabilities and paving the way for more solutions and expanded capabilities in this area.
For example, the Orca Cloud Security Platform provides AI-SPM capabilities that help organizations secure more than 50 AI services, packages, and models in their cloud. Using Orca, teams can view all managed and unmanaged AI models deployed in their environment, ensure the proper configuration of AI resources, and detect sensitive data exposure, including training data.
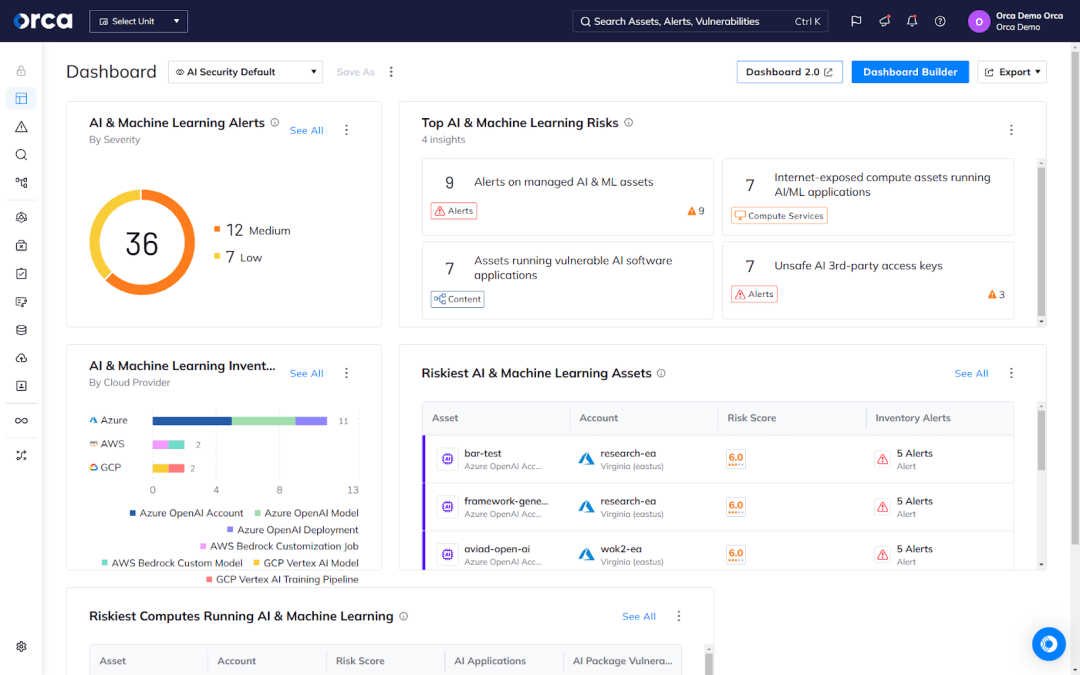
About the Orca Cloud Security Platform
The Orca Cloud Security Platform is an agentless-first CNAPP that fully supports Oracle Cloud and augments its native security features. The Orca Platform combines full multi-cloud coverage and comprehensive risk detection to effectively prioritize risks. This includes the often hidden toxic risk combinations that endanger your high-value assets.
Using Orca, teams can automate compliance as well as operationalize DevSecOps. For compliance, Orca offers more than 160 out-of-the-box compliance frameworks and a wide range of features for automation and customization. To support DevSecOps, the Orca Platform offers comprehensive capabilities for application security, including code security and source code management posture management (SCM-PM).
To see how the Orca Cloud Security Platform enhances Oracle Cloud security, book a personalized demo with one of our experts.
Conclusion
Oracle Cloud security plays an essential role in your ability to thrive and innovate in the cloud. Yet enhancing it remains a challenge, particularly for teams that lack the right technology and approach. You can improve your chances of success and reduce your cloud risks by following the best practices explored in this post. It starts with understanding the Shared Responsibility Model and continues with adopting a unified CNAPP. Fortunately, it allows you to better protect your data, applications, and cloud resources.
FAQs
What is security for Oracle Cloud?
Oracle Cloud security is a complete set of measures that protect data, applications, and infrastructure within the Oracle Cloud environment. It aims to mitigate the risks associated with modern cloud computing while also protecting against internal and external cybersecurity threats, maintaining the integrity, availability, and confidentiality of cloud resources.
What are Oracle Cloud security best practices?
Some of the Oracle Cloud security best practices that organizations should implement include:
- Understand your security responsibilities under the Shared Responsibility Model prior to entering an agreement with a CSP.
- Establish a complete and continuous view and inventory of cloud resources.
- Prioritize your remediation efforts to address your most critical risks, with criticality based on business impact.
- Adopt a DevSecOps framework that embeds security into every phase of the application lifecycle, enhances security efficacy, as well as promotes cross-functional collaboration and ownership of secure practices.
- Automate your compliance efforts wherever possible and across key functions, including compliance documentation, monitoring, auditing, and reporting.
- Acquire a Cloud-Native Application Protection Platform (CNAPP) to unify your cloud security and meet the current and future demands of cloud computing.
What are the key benefits of Oracle Cloud security?
Depending on the approach and solution(s), Oracle Cloud security can offer the following benefits:
- Risk mitigation and prevention: Security measures can help you address your pre-breach risks, prevent similar issues from recurring, and address in-progress attacks.
- Regulatory compliance: Compliance solutions can help organizations support their compliance requirements while minimizing the burden on teams.
- Business continuity insurance: Security measures can help organizations avoid severe security incidents that may jeopardize operations and result in major financial, regulatory, reputational, or legal consequences.





