Elastic IPs (EIPs) are public and static IPv4 addresses provided by AWS. EIPs can be viewed as a pool of IPv4 addresses, accessible from the internet, that can be used in numerous ways. Once an EIP is allocated to an AWS account, it can be associated with a single compute instance or an elastic network interface (ENI). An EIP can also be self-provided using the “BYOIP” (bring your own IP) feature, and stays allocated until the user decides to release it.
In October 2022, AWS released a new feature called “Elastic IP Transfer,” which allows the transfer of EIPs between different AWS accounts. This is attractive news to DevOps teams as it enables easier provisioning of services, as well as being attractive to suspicious attackers–since this feature enables you to transfer the EIP to any AWS account, even accounts that are not owned by you. For example, an unauthorized actor inside your cloud environment can, with the right permissions, transfer an IPv4 address to an account owned by it.
The consequences of taking over a legitimate IP address can range from DOS (Denial Of Service), to enhanced SE (Social-Engineering) and all the way into compromising the victim’s most critical Crown-Jewels. The research team at Orca Security recognized the risk behind this newly-discovered TTP as severe, because unlike the traditional Subdomain-Takeover attack, with an EIP the attacker can create malicious activity from an organizational Source IP and as a result bypass allow-lists of networking and security services. In their blog, Mitiga researchers explained extensive details on this potential attack vector.
Cloud Detection & Response (CDR) to Mitigate Cloud Threats
The Orca Cloud Security Platform helps customers quickly and easily identify, mitigate and, if needed, also recover from this kind of attack. This is possible by our Cloud Detection and Response capabilities to continuously collect and analyze intelligence from cloud feeds, workloads, and configurations in a single, unified platform.
With Cloud Detection and Response you can:
- Detect: Receive alerts when changes and anomalies occur that indicate possible malicious intent versus normal behavior, automatically prioritizing events that endanger the company’s most critical assets.
- Investigate: Research malicious activity to quickly gain insight into whether the events are malicious and if any of the organization’s critical assets are in danger.
- Respond: Intercept cloud attacks by leveraging remediation steps and automatically assigning issues using Orca’s 20+ third-party technical integrations (including SOAR, notifications, and ticketing systems).
Orca enables security teams to flip-the-script and become one step ahead of sophisticated attackers, through a comprehensive and prioritized alert system. Our easy-to-follow platform provides actionable step-by-step remediation processes, so incidents can be responded to quickly and efficiently.
We continuously research, develop and improve this state of the art system in order to tackle the latest threats. It’s within our top priority to help our customers increase their security posture by eliminating alert fatigue and equip their security teams with the most advanced defense systems. So they can mind less about security, and more about their business.
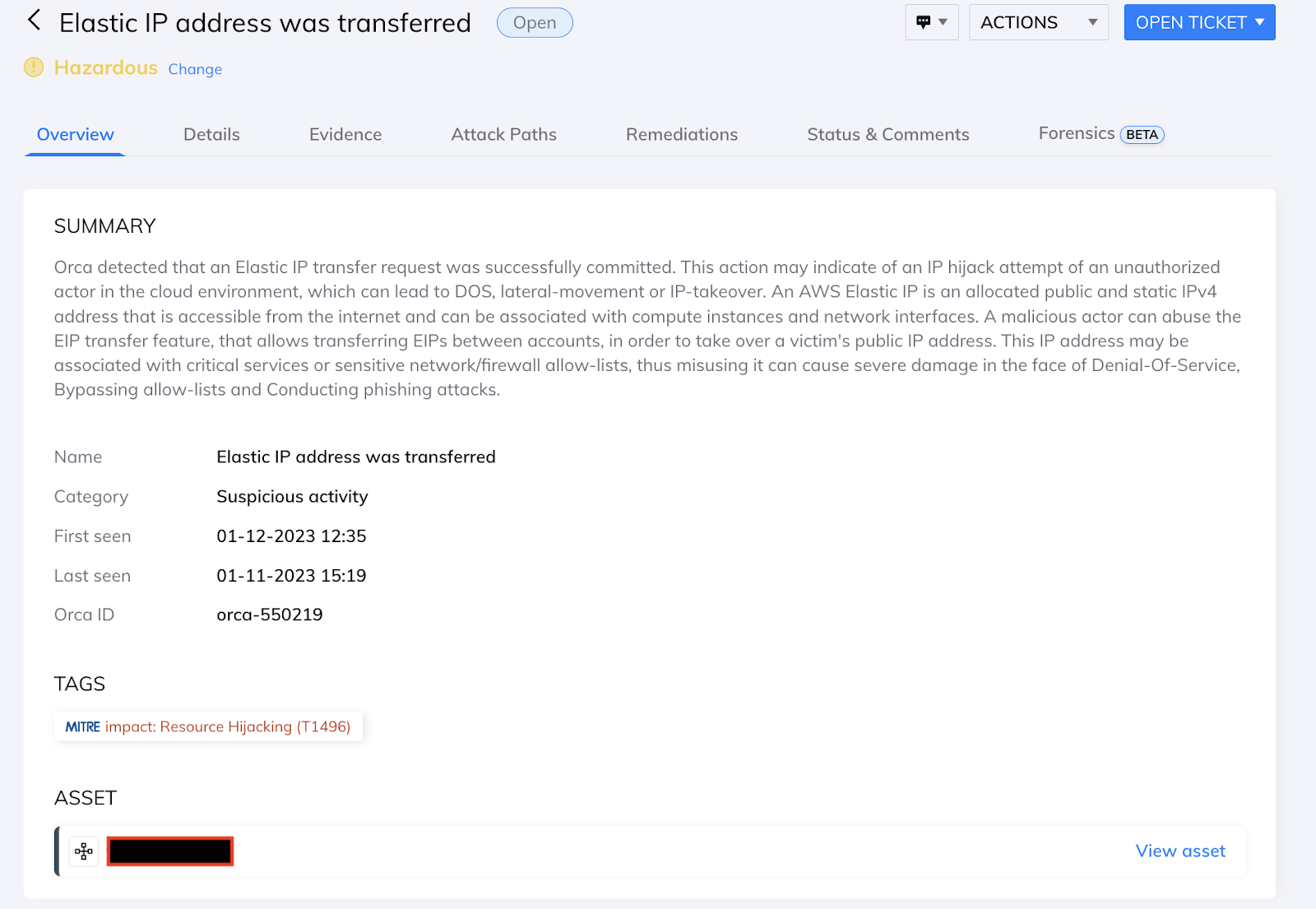
Identifying and Alerting on EIP Transfer Activity
Below, Orca triggered an alert due to the detection of the new EIP Transfer attack-vector with remediation actions and forensics for further investigation.
Conclusion
Orca Security is committed to identifying misconfigurations, vulnerabilities, and active threats across multi-cloud environments. With CDR, security teams can quickly identify suspicious and malicious activity to quickly take action. For more examples of real life attacks detected by the Orca Platform, visit our Cloud Detection and Response webpage.






