In this blog, we will demonstrate how Orca Security Cloud Detection and Response (CDR) analyzes cloud events and behaviors and combines this with cloud telemetry, existing workload and control plane risks in the cloud environment, and company crown jewel awareness, to assess whether anomalies indicate malicious intent and how dangerous they could potentially be.
What is Cloud Detection & Response (CDR)?
Cloud Detection and Response (CDR) helps organizations detect, investigate and respond to cloud attackers who have breached the perimeter controls of cloud resources and applications. By providing Security Operations Center (SOC) and Incident Response (IR) teams with contextualized data on potentially malicious events, security teams can accelerate investigation, triage, and response to cloud threats.
How is Orca’s CDR different?
Unlike other solutions that only look at events, behaviors, and risks on workloads, Orca also considers cloud-native configuration and identity risks to assess whether events indicate a possible malicious attack and could pose a serious risk to the organization.
Leveraging a single unified data model, Orca is able to combine and analyze the following information:
- Cloud provider logs & threat intelligence feeds
- Risks in cloud workloads such as malware and vulnerabilities
- Risks in configurations and identities, such as IAM risk, lateral movement risk and misconfigurations
- Awareness of the location of the company’s crown jewels (PII, financials, and other sensitive data)
This enables Orca to understand the full context of an occurrence and quickly identify which events and anomalies are potentially dangerous, versus those that are non-malicious.
Examples of how Orca CDR detects cloud attacks
Below, we discuss four examples of cloud attacks and how Orca CDR can detect anomalies in events and behaviors to determine whether these events indicate a cloud attack in progress.
#1: Unusual creation of EC2 instances
Through continuous modeling and studying User and Entity Behavior Analytics (UEBA) in the cloud environment, Orca detects an anomaly in a role’s behavior. Normally this role creates about 1 or 2 EC2 instances per week, but today Orca sees that the role has already created 12 EC2 instances. In addition, Orca’s workload scanning detects suspicious commands on one of the EC2 instances indicating that it has a crypto miner running on it.

Scenario #1 Attack Flow
Orca determines that it is highly likely that malicious activity is occurring and generates a high priority alert with the recommendation to investigate this more thoroughly. Specifically, Orca recommends to review the role’s activity issuing the API calls, the newly created EC2 instances and malware, and then determine whether the EC2 instances should be shut down and/or the role’s credentials should be rotated.
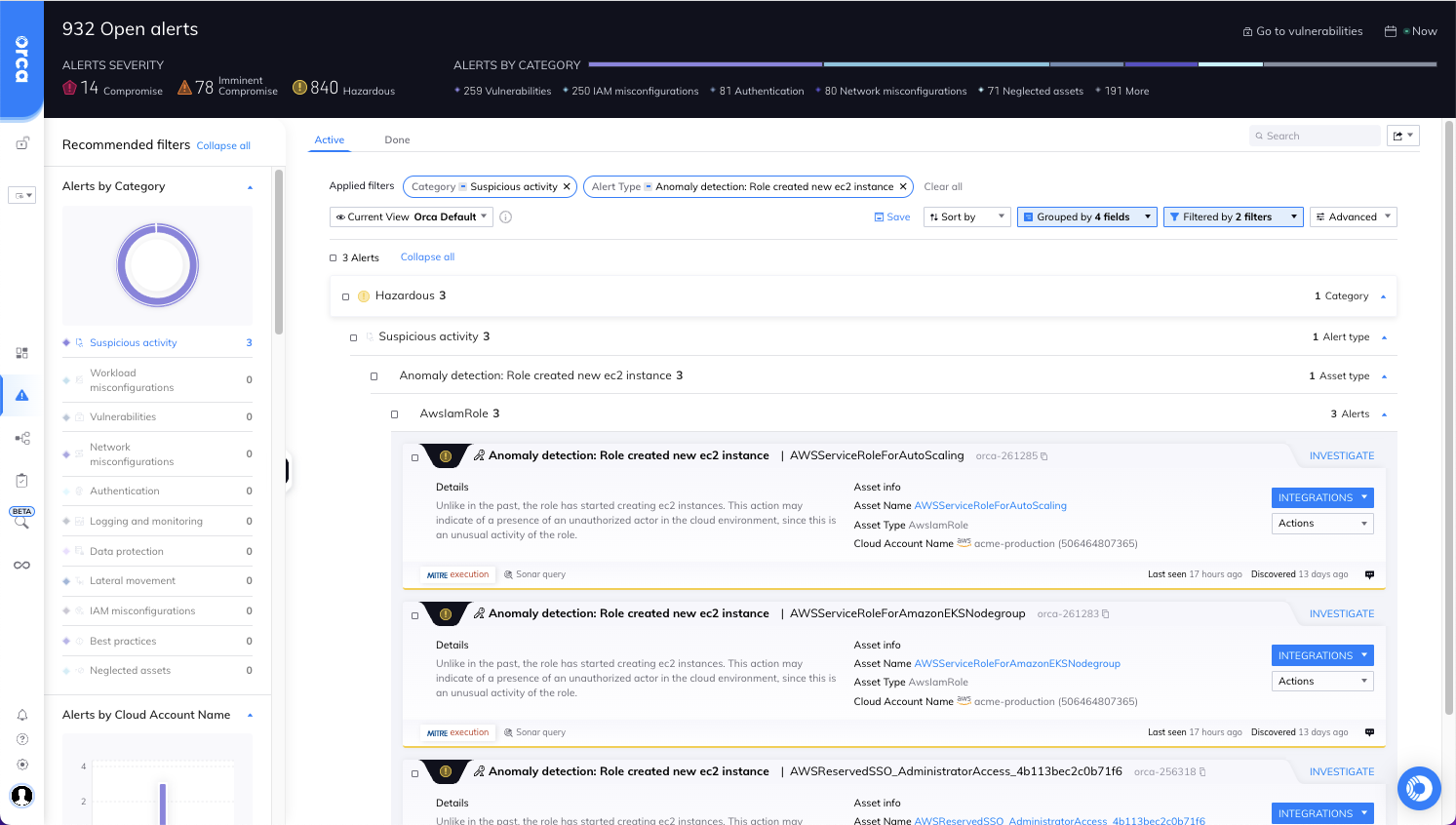
Orca CDR dashboard alerting to the unusual creation of EC2 instances
#2: API call activity indicates enumeration process
Orca detects API calls with unusual user agents. After further inspection, the nature of the API calls indicate that there may be an enumeration attack in progress. Enumeration attacks are executed by attackers to uncover information about the environment they are looking to compromise, for example listing EC2 nodes in the cloud account to gather information on their targets for lateral movement execution, or listing S3 buckets to try to exfiltrate sensitive data.
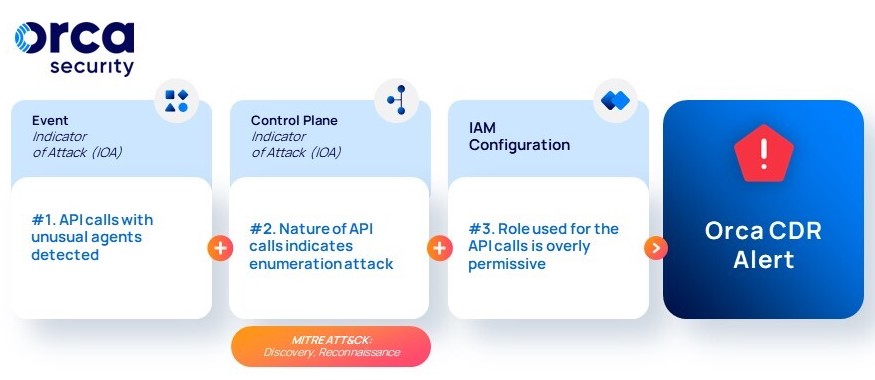
Scenario #2 Attack Flow
This suspicious behavior, combined with Orca’s findings from the control plane that the role used in the API calls is overly permissive, increases the risk and possible business impact. Therefore Orca considers this a possible attack of the highest severity. To intercept and respond to this attack, Orca advises to review the role’s activity issuing the API calls and any additional activity observed on the unusual user agent. Possible preventative actions would be to reduce the permissions of the role used in the API calls, and rotate potential hijacked role’s credentials with an unusual user agent.
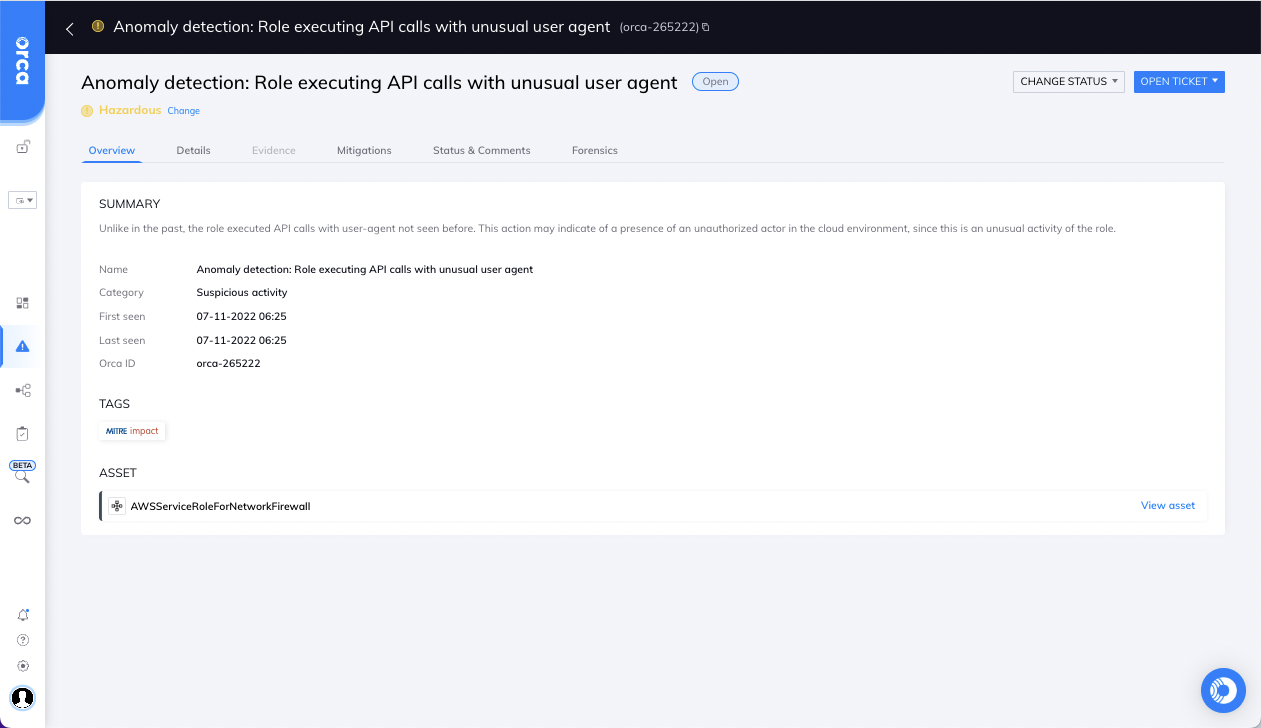
Orca alert including information on the detected API calls with unusual user agent
#3: Malicious IP trying to access Lambda function
Through continuous monitoring, Orca picks up on suspicious activity from a malicious IP address communicating with an AWS Lambda function, attempting to retrieve the source code of the Lambda function.
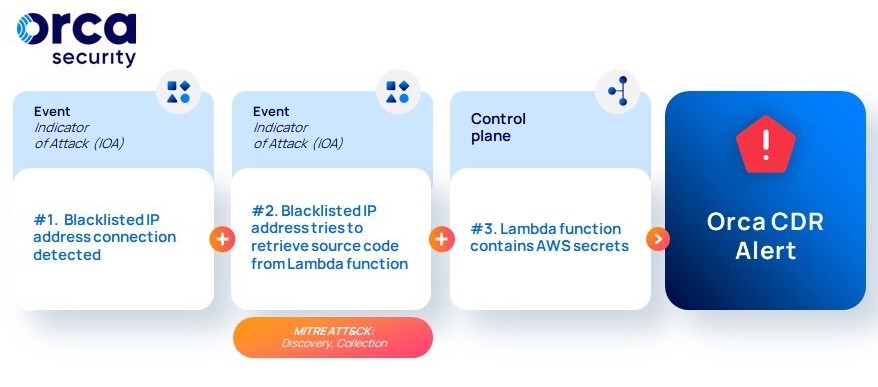
Scenario #3 Attack Flow
From previous scans, Orca knows that this Lambda function exposes AWS secrets and immediately generates a critical alert of possible malicious activity. Orca advises to review the role’s activity issuing the API calls, and protect the AWS secrets from exposure, for instance by changing the secret exposed.
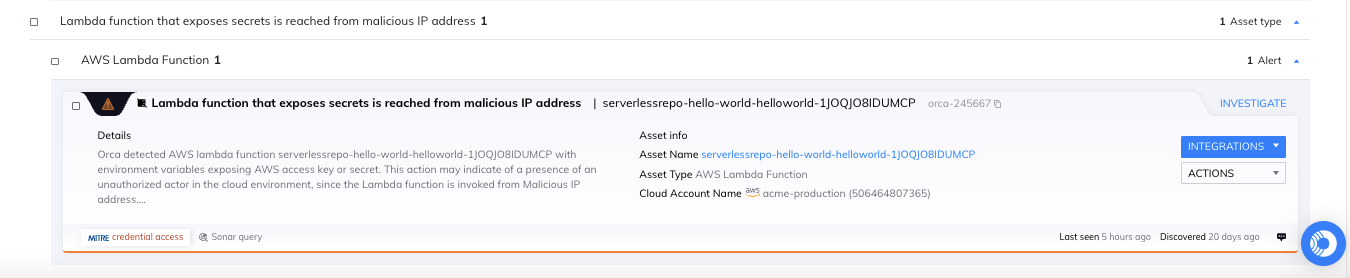
Orca alerts that a malicious IP address has accessed a Lambda function that exposes secrets
#4: Unusual role behavior on S3 bucket with PII
Leveraging User and Entity Behavior Analytics, Orca detects an anomaly in a role’s behavior. The role has made an API call to an existing S3 bucket, though it has never done this before. Two days later, the same bucket is enabled for public access with no authentication required. Through data plane scanning, Orca knows that this bucket contains PII. Since this behavior is a common technique for data exfiltration, Orca immediately escalates the issue so SOC teams can block public access to the S3 bucket that contains PII.
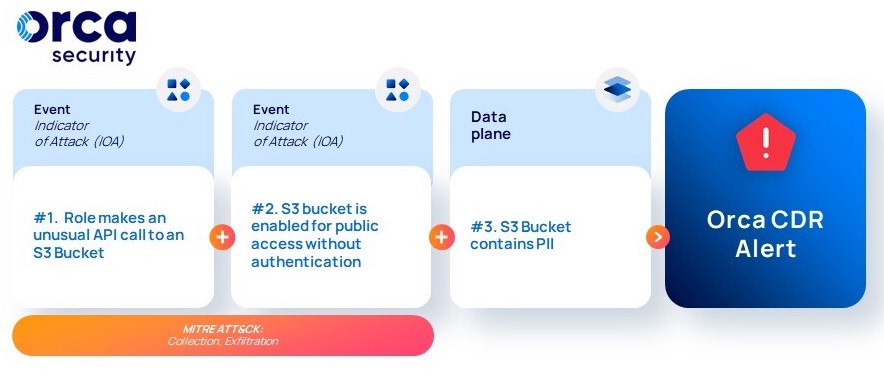
Scenario #4 Attack Flow
Learn more about Orca’s CDR
Would you like to learn more about Orca’s CDR capabilities? Watch our recorded demo or attend Cloud Security LIVE on July 28th, Orca’s half-day virtual networking event, to learn more about CDR and other top cloud security issues from your peers, thought leaders, and industry luminaries from around the world.
Want to get more hands-on? Sign up for a free 30-day risk assessment to see how quickly and easily the Orca Cloud Security Platform can help you identify and address risks in your cloud.