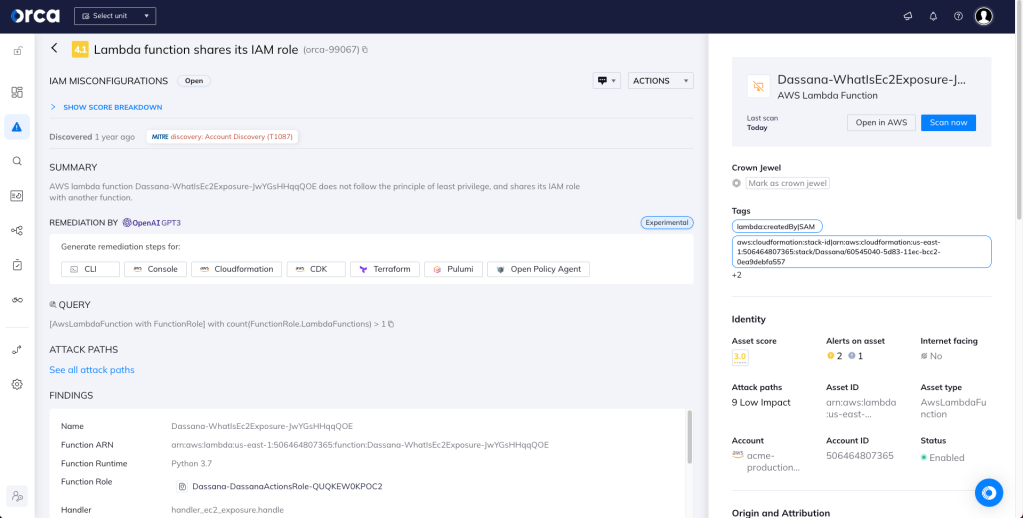
Lambda function shares its IAM role
Informational (4)
- Brazilian General Data Protection (LGPD) ,
- CCPA ,
- GDPR ,
- ISO/IEC 27001 ,
- Mitre ATT&CK v12 ,
- New Zealand Information Security Manual ,
- NIST 800-171 ,
- NIST 800-53 ,
- Orca Best Practices ,
- UK Cyber Essentials
About AWS Lambda
AWS Lambda is Amazon’s service for serverless computing. A serverless architecture is a way for organizations to build and run applications and services without having to manage the underlying infrastructure. Applications still run on servers, but the responsibility for server management rests with the cloud provider, utilizing a pay-for-when-you-use-it model. This reduces the cost of DevOps and enables developers to focus on their product without being limited by server capacity.
About IAM Roles
An IAM role in an AWS account is an identity with specific permissions that dictate what actions the identity can perform and which resources it can access. Unlike IAM users, IAM roles are not bound to a single person and can be assumed by anyone that is authorized to do so.
Roles provide a great way to delegate access to users or applications that don’t usually need access to your resources. With that said, extra care should be taken to adhere to the Principle of Least Privilege (PoLP), ensuring that minimum access is given to the fewest number of people.
Cloud Risk Description
When it comes to AWS Lambda, AWS recommends creating separate roles for each function, in order to promote the Principle of Least Privilege (POLP). “By using one dedicated IAM role per function, you can control permissions more intentionally. Every Lambda function should have a 1:1 relationship with an IAM role. Even if some functions have the same policy initially, always separate the IAM roles to ensure least privilege policies.”
This protects data from unauthorized access, and allows you to conform with various security and compliance standards.
How Orca Can Help
Orca detects and prioritizes cloud identity and access management misconfigurations such as weak and leaked passwords, exposed credentials, and overly permissive identities. Continuous IAM monitoring across your cloud estate prevents malicious and accidental exposure. In this specific case, Orca helps by looking for Lambda functions that share its IAM role with other functions, and will alert on this type of issue as shown in the screenshot above.
Recommended Mitigation Strategies
-
Always apply the principle of least privilege while creating IAM users.
-
Review your Lambda functions and make sure they do not share IAM roles.
-
Remove any unnecessary or unused IAM users from your AWS account.
-
Regularly audit for IAM users with admin privileges.
Useful Links
- 2022 State of Public Cloud Security Report: https://orca.security/lp/2022-state-public-cloud-security-report/
- Best practices for working with AWS Lambda functions: https://docs.aws.amazon.com/lambda/latest/dg/best-practices.html
- AWS Lambda FAQs: https://aws.amazon.com/lambda/faqs/
- Configuring AWS Lambda functions: https://docs.aws.amazon.com/lambda/latest/dg/lambda-functions.html
- AWS Security best practices in IAM: https://docs.aws.amazon.com/IAM/latest/UserGuide/best-practices.html
Orca Security, the cloud security innovation leader, provides cloud-wide, workload-deep security and compliance for AWS, Azure, and GCP - without the gaps in coverage, alert fatigue, and operational costs of agents.
