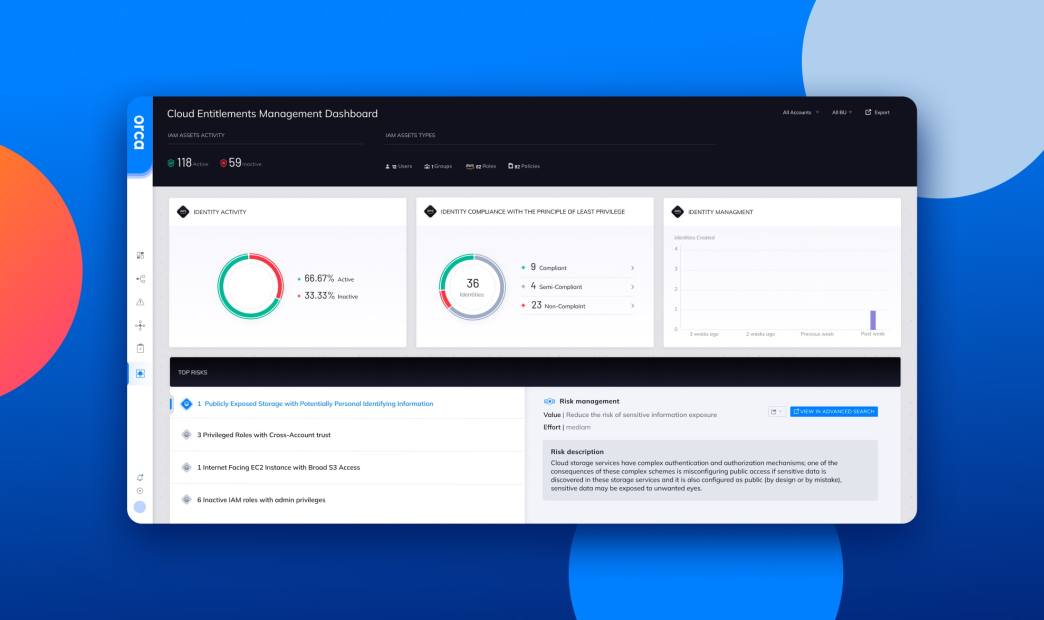
CIEM (Cloud Infrastructure Entitlements Management) is a fairly new category of cloud security solutions. CIEM as a term is both well defined and nebulous. At its core, CIEM is all about the management of cloud identities, but … how? Are you simply addressing basic identity hygiene, or are you getting the insight you need to actually reduce the most critical risks that could be used in an identity-based attack?
At Orca, we’ve studied the initial approaches taken by CIEM vendors and, more importantly, we’ve talked to many of our customers about what identity problems they are actually interested in solving.
So, what do real organizations want in terms of identity management? Well, basic hygiene is just a start. Yes, it’s very important, but today’s attacks are sophisticated, and security teams know that their defenses must be sophisticated, too. That means being able to prioritize the most critical identity issues and having the confidence that addressing those will in fact reduce the organization’s risk in a pragmatic way.
We took that as our mission when we architected our CIEM capabilities – to be pragmatic and provide real risk reduction value. We look at CIEM in three ways:1) identity hygiene, 2) detecting deviation from best identity practices, and 3) using identity data to help understand and prioritize the risks that are in your system in a holistic way.
First, we enable customers to improve their identity hygiene to reduce their attack surface. Identity hygiene best practices are primarily driven by the principle of least privilege (PoLP) – so here we do what almost every good CIEM product does. We identify inactive and over permissioned identities. We then provide visualization tools to allow you to quickly investigate and triage issues and reduce your attack surface through good identity hygiene.
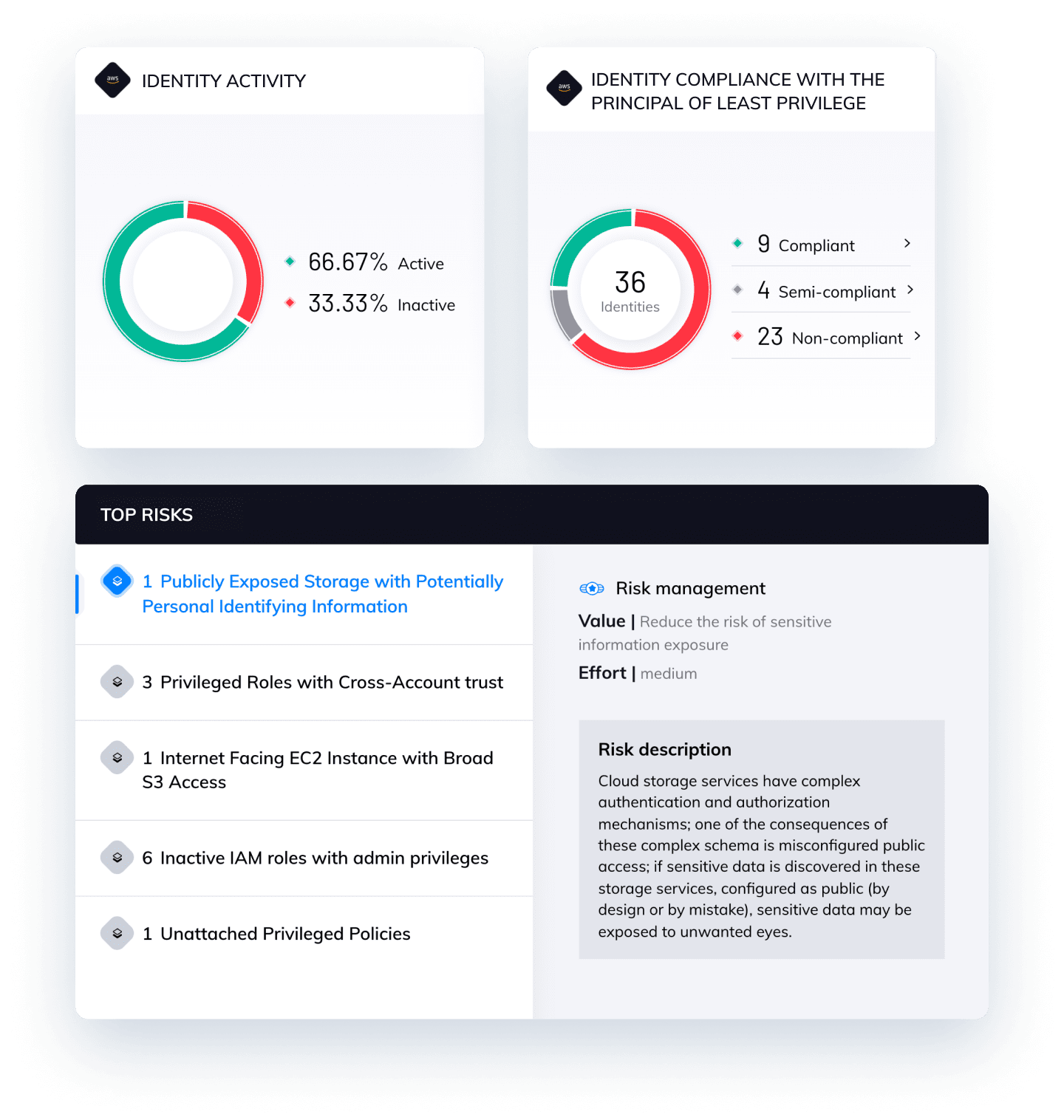
One of the identity capabilities that our customers requested the most is the ability to detect deviations from best practices using a library of well-defined rules. Following is an example of some of these best practice deviations in what we call Top Identity and Access Management risks.
Top IAM Risks
2 Privileged roles with cross-account trust
1 Inactive IAM roles with admin privileges
3 Unattached privileged policies
33 Most active roles with cross-account trust
1 Compromised assets with privileged IAM permissions
2 Privileged inactive identities
In every example above, two or more identity risks are combined to define a rule. These combined risks present a greater risk level than either risk on its own. All occurrences of these top IAM risks are listed in Orca, enabling security teams to easily examine and triage them as needed. These top IAM risks give you an actionable and easy to understand way of focusing your identity management efforts to reduce the most critical risks with the least amount of effort.
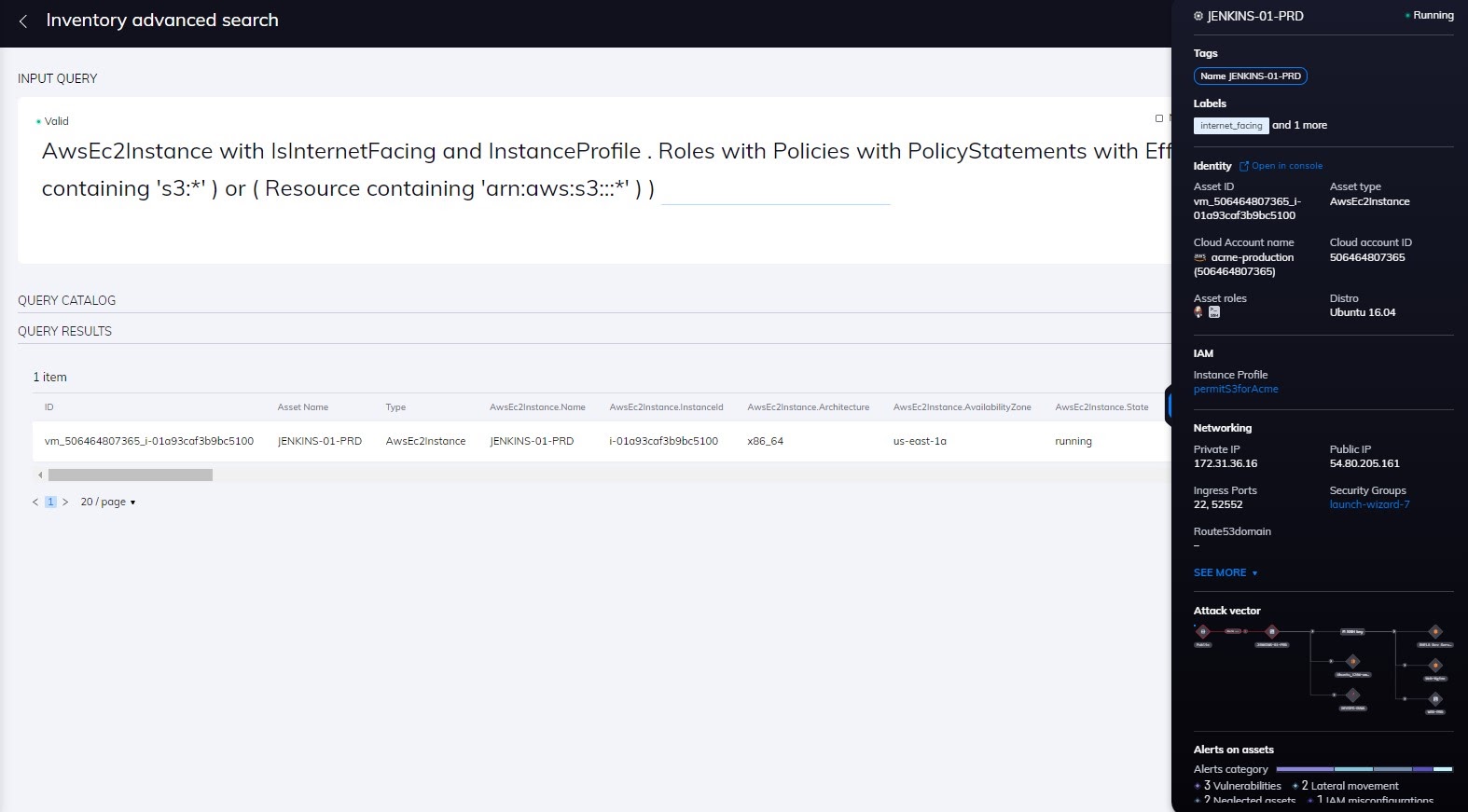
But Orca goes even a step further with this idea, and this is where it gets interesting. We leverage our universal data model to aggregate identity risk with other types of cyber risks. Where identity risk becomes more valuable is when it is examined in concert as part of a greater risk picture. When we look at an asset, we account for a variety of risks: identities, vulnerabilities, misconfigurations, malware, sensitive data, threat data, etc. By combining identity risks with other risk data, Orca can then provide prioritized and actionable risks for resolution.
By combining CIEM, CSPM, and CWPP capabilities into a single CNAPP platform and data model, Orca can flag attack chains containing risky combinations. For example, an infected workload that can assume a high privileged instance role allowing access to a database with PII would receive the highest prioritization. Orca does far more than just discover attack chains. It also prioritizes these attack chains with a score from 0-100. This prioritization of attack chains is extremely useful since for example, Orca might discover more than 150 attack chains in your environment, but only flag 10 of them as critical. So you can then work on mitigating the 10 attack chains that pose the most risk to your environment.
In summary, don’t rely solely on analytics and anomaly detection to improve your identity hygiene and don’t just look at identity risk by itself. Look at your cloud estate the way attackers do – holistically – and use context to identify your most critical risks. If you’d like to see for yourself how Orca can help you improve your identity hygiene as well as your overall cloud security posture, take the platform for a test drive. Sign up for a free 30 day cloud security risk assessment and get full visibility of your cloud estate, including critical risks that can only be found by looking at the full picture.