Sensitive Data in File
Hazardous (3)
Non-platform specific
Orca Best Practices
About Sensitive Data
Sensitive data can be any confidential information that must be protected from unauthorized access. Sensitive data includes cryptographic keys that you use to encrypt your data, your customer’s payment card information, employee login credentials, API keys that enable you to integrate with a third party service, and more.
To truly secure all your sensitive data, you first need to identify all the places it exists in your cloud estate. Some of these locations will be obvious; e.g. your database servers, your source code repositories, and your web applications.
Storing sensitive data in unprotected files is a major security issue. This can range from storing encryption keys on a file server for easy access by an application, to putting your production database login credentials in a configuration file.
There can also be instances where sensitive data may mistakenly or unknowingly be written to files. For example, when your web application is run in debug mode, it can write the plaintext passwords of your users in the log file. Or when an engineer hardcodes their password in a Bash automation script that’s used once but remains on the server indefinitely.
Regardless of the means, sensitive data should always be carefully secured. Its exposure can lead to data and financial loss, and potentially, complete system takeover.
Cloud Risk Description
Unprotected sensitive data, like login credentials, payment card information, API keys, etc., may exist in poorly secured locations. If a malicious actor has easy access to sensitive data it can be exploited to gain unauthorized access to internal resources.
How Does Orca Help?
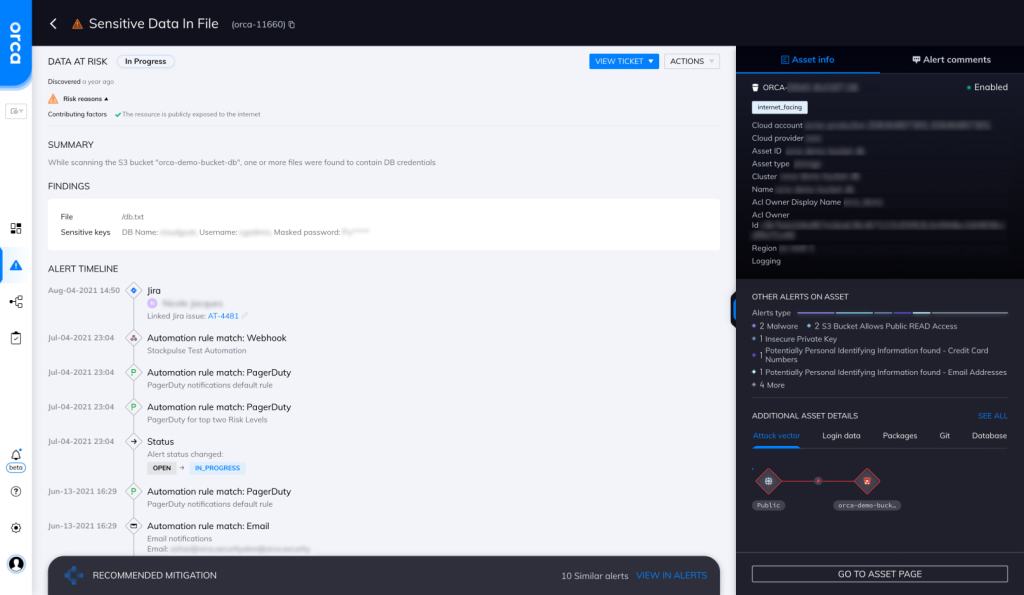
Orca scans the hidden corners of your cloud estate, searching for at-risk sensitive data, including personally identifiable information (PII), payment card data, and protected healthcare information. Orca indicates the exact location sensitive data is found and provides masked samples for efficient triaging and remediation.
Orca looks for sensitive data in files and will alert on this type of issue as shown in the screenshot above.
Recommended Mitigation Strategies
-
Scan and match
Scan your files periodically to identify any that match a predefined, sensitive data regular expression.
-
Educate
Educate developers and engineers on the risk of storing sensitive data.
-
Use secret stores
Use secret stores like Vault for safe storage of your encryption keys and secrets.
-
Audit
Audit applications, especially their logging mechanisms, to ensure that no sensitive information is logged.
-
Avoid environment variables
Try to avoid using environment variables to store sensitive configuration information.
Useful Links
- Inspecting text for sensitive data: https://cloud.google.com/dlp/docs/inspecting-text
- Tips to protect sensitive data: https://geekflare.com/tips-to-protect-sensitive-data/
- Vault: https://www.vaultproject.io/docs/what-is-vault
- Secure logging cheat sheet: https://cheatsheetseries.owasp.org/cheatsheets/Logging_Cheat_Sheet.html
- Encryption key management: https://www.thesslstore.com/blog/12-enterprise-encryption-key-management-best-practices/
Orca Security, the cloud security innovation leader, provides cloud-wide, workload-deep security and compliance for AWS, Azure, and GCP - without the gaps in coverage, alert fatigue, and operational costs of agents.
