Sensitive Info in Git Repository
Hazardous (3)
Non-platform specific
About Git Repositories
Git is open source content-tracking software used by programmers to develop, modify, and maintain software applications, typically in a multi-contributor environment.
Git stores and tracks every bit of information inside a repository. Think of the repository as a database that contains the history of all the changes, ever made, to all the files in your project. This gives users the ability to switch/revert to a previous version of a software application, at any time.
Git tracks changes via commits. Think of a commit as a snapshot of your project. Any time a user wants to add new changes to a repository, they create a new commit, using the git commit command. This allows them to bundle up one or more changes as the next snapshot of the project, and then add it to the repository.
However, sometimes, users accidentally push sensitive information into a Git repository, which can be exploited by malicious actors.
Sensitive information can include passwords, tokens, secrets, access keys, SSH keys, certificates, and hostnames, etc. Such information should never be hardcoded in source code or pushed as part of a configuration file. However, mistakes do happen.
Cloud Risk Description
Sensitive information like database passwords, API keys, encryption keys, hash salts, and secrets, etc. can mistakenly get pushed into a Git repository. If they are part of the source code of your application, cybercriminals can easily extract them and compromise your systems.
Any pushed sensitive data must be detected and removed immediately, both from the repository and the history.
How Does Orca Help?
Orca detects sensitive data at-risk across both the workload and control plane, pinpointing the exact location and providing masked samples of the data for quick remediation. It also leverages context such as the location and accessibility of the assets containing the data. This approach separates the noise from the risks that are truly critical to the business.
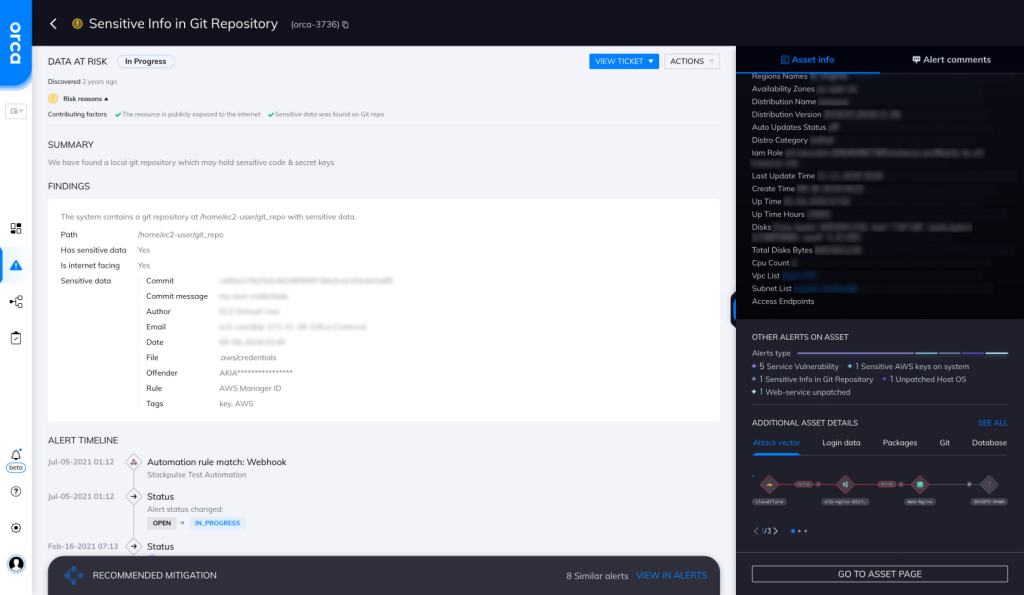
Orca looks for sensitive information in Git repositories and will alert on this type of issue as shown in the screenshot above.
Recommended Mitigation Strategies
-
Educate
Educate developers about the importance of storing sensitive information securely.
-
Store smartly
Use environment variables to store keys and secrets on your development and staging systems. In production environments, secret stores like Vault are recommended.
-
Don't push sensitive data to a Git repository
Use tools like git-secrets, that prevent you from pushing sensitive data to a Git repository.
-
Use MFA
Use multi-factor authentication (MFA) for your Git accounts.
-
Add a SECURITY.md file
Add a SECURITY.md file to your project, highlighting all the key security aspects for your project.
-
Be mindful of sensitive information
Scan for any slipped sensitive information, using tools like Gitrob.
Useful Links
- Git-secrets: https://github.com/awslabs/git-secrets
- Gitrob: https://github.com/michenriksen/gitrob
- Adding a security policy to Git: https://docs.github.com/en/code-security/getting-started/adding-a-security-policy-to-your-repository
- Removing sensitive data from Git: https://docs.github.com/en/authentication/keeping-your-account-and-data-secure/removing-sensitive-data-from-a-repository
- Reviewing your SSH keys: https://docs.github.com/en/authentication/keeping-your-account-and-data-secure/reviewing-your-ssh-keys
- Best practices for Git user security: https://docs.github.com/en/[email protected]/admin/user-management/managing-users-in-your-enterprise/best-practices-for-user-security
- GitHub secret scanning: https://docs.github.com/en/code-security/secret-scanning/about-secret-scanning
Orca Security, the cloud security innovation leader, provides cloud-wide, workload-deep security and compliance for AWS, Azure, and GCP - without the gaps in coverage, alert fatigue, and operational costs of agents.
