The Challenge
Standalone CIEM Solutions Lack Wider Cloud Context
Cloud identities present risks to organizations as they are a central component of every environment and cloud native application. Monitoring the effective management and auditing of cloud identities and permissions across multi-cloud environments requires comprehensive visibility and automation, which is lacking in point CIEM tools. Without the visibility into unmanaged identities, such as SSH keys, passwords, or account toles, security teams struggle to achieve comprehensive cloud security at scale.
Manually configuring and auditing cloud entitlements is inefficient and leads to misconfiguration errors.
Point solutions don’t have visibility into workload risks and unmanaged identities, such as SSH keys, passwords, and other critical issues, thereby limiting visibility into wider cloud context.
The result is poor risk prioritization, inaccurate or contextless remediation, and incomplete compliance.
Our Approach
Take Control of Your Identities
Instead of providing identity and access privilege management in a siloed solution, Orca combines identity risks with other risk data—vulnerabilities, misconfigurations, malware, the location of sensitive data, and lateral movement risk—to help you prioritize the risks in your environment in a holistic way.
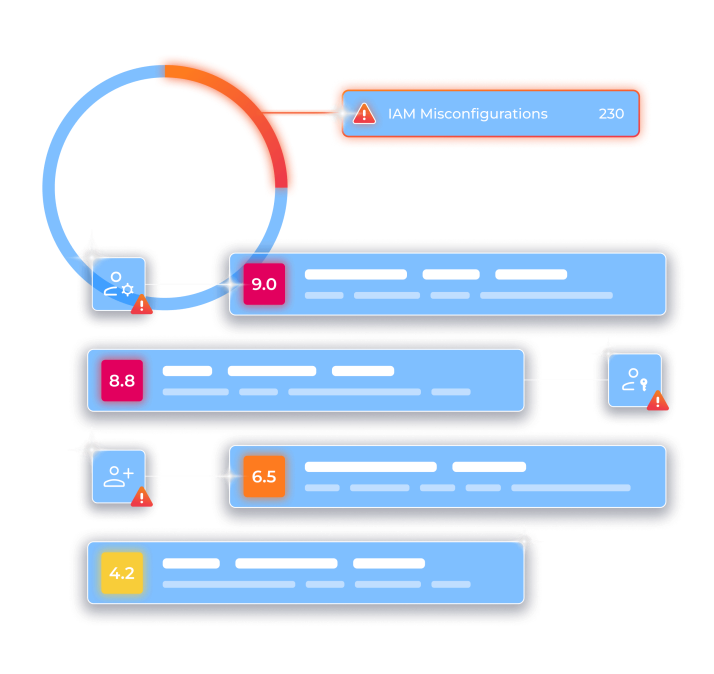
Monitor all identities, roles, groups, permissions, and policies deployed in your cloud environment.
Receive alerts when security best practices, such as the principle of least privilege, are not adhered to.
Get answers to questions such as: “Which human and machine identities have access to this Google Standard Storage resource?” or “Which AWS EC2 instances have access to an S3 bucket with PII?”
Orca’s CIEM dashboard helps organizations understand the relationship between access rights and cloud resources. Orca alerts when overly permissive identities are found and prioritizes them according to potential business impact.
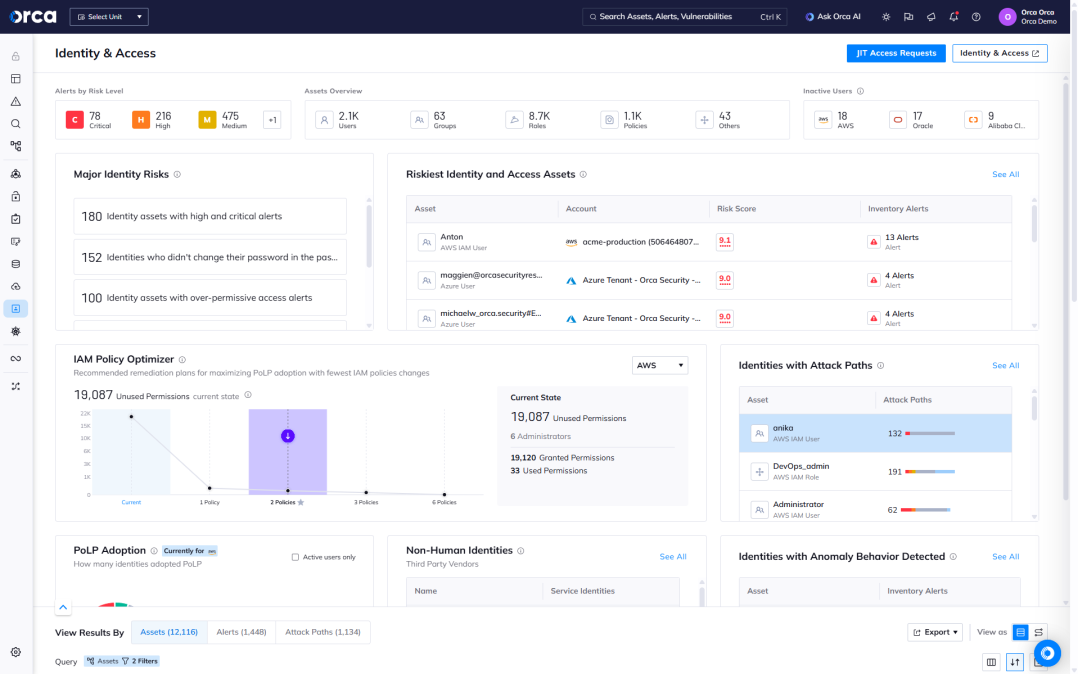
Centralized multi-cloud discovery and compliance
Orca’s agentless platform allows you to track cloud assets, roles and entitlements across multiple cloud platforms, and ensure compliance with regulatory standards and CIS benchmarks.
- Get granular, contextual visibility into all identities, configurations, access policies, entitlements, permissions, and activities in your cloud.
- View network access and publicly exposed resources in all of your cloud estate.
- Leverage thousands of controls across 20+ categories, including authentication, data protection, logging and monitoring, IAM misconfigurations, and system integrity.
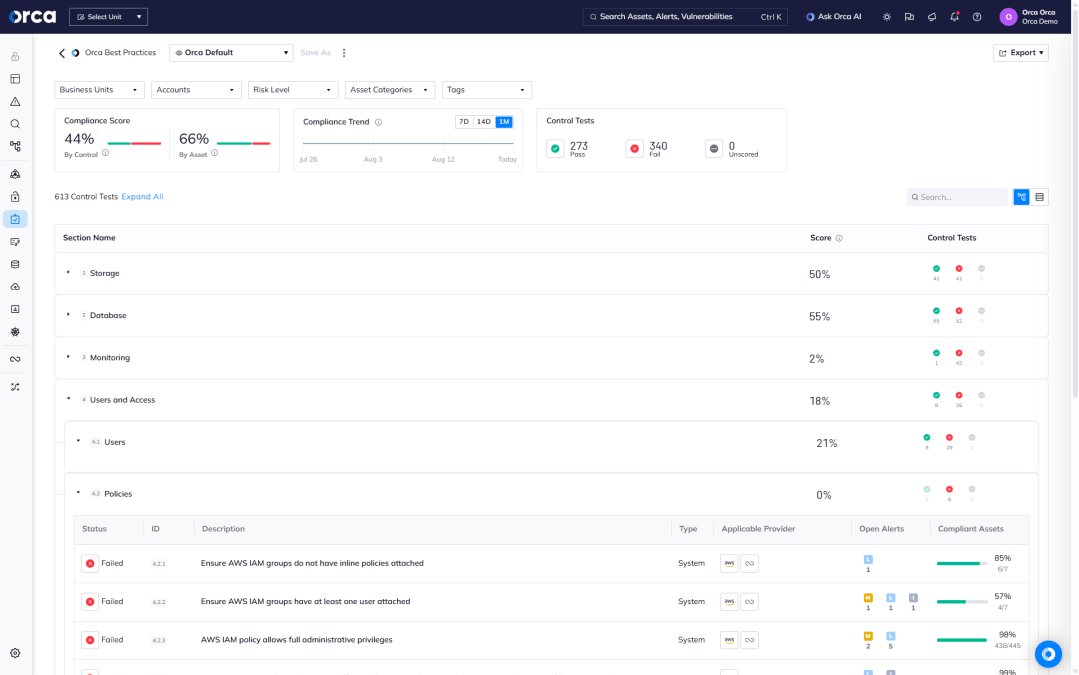
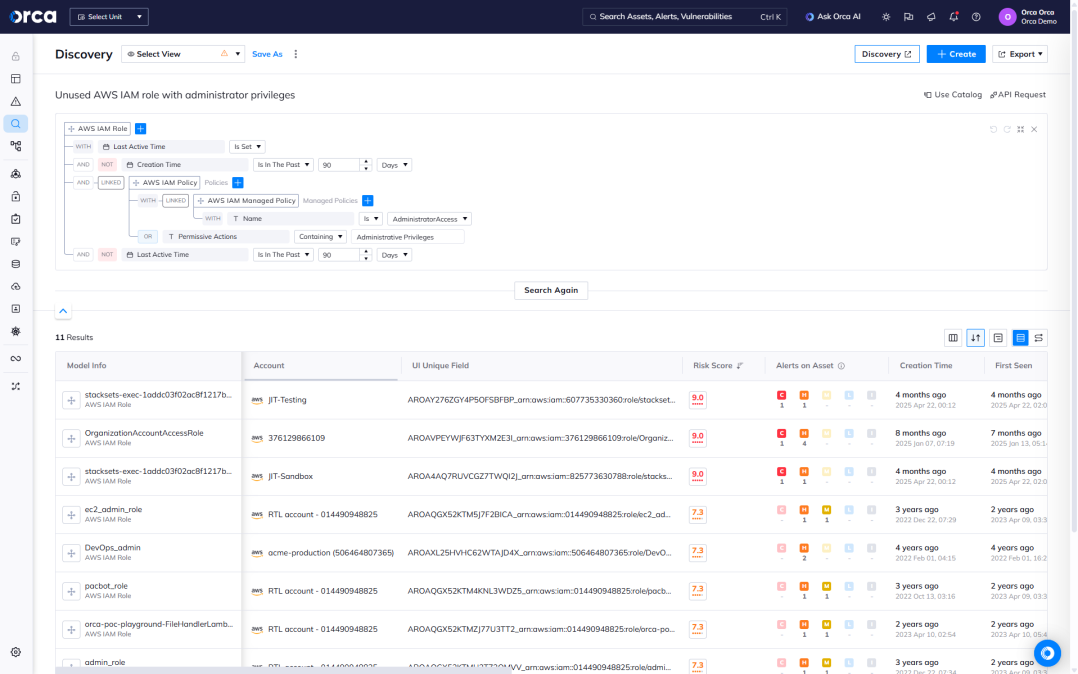
Advanced querying of identity and entitlement risks
Orca allows you to perform advanced queries on entitlement and identity data, using thousands of built-in alert templates, Orca’s intuitive query builder, an extensive query catalog, or our natural language AI integration.
- Set up customized alerts—with remediation actions—to be notified when cloud developers violate the least-privilege principle or other security policies.
- Support continuous compliance query templates that align with 185+ regulatory frameworks and CIS benchmarks.
- Integrate queries and alerts with your existing workflows and ticketing systems.
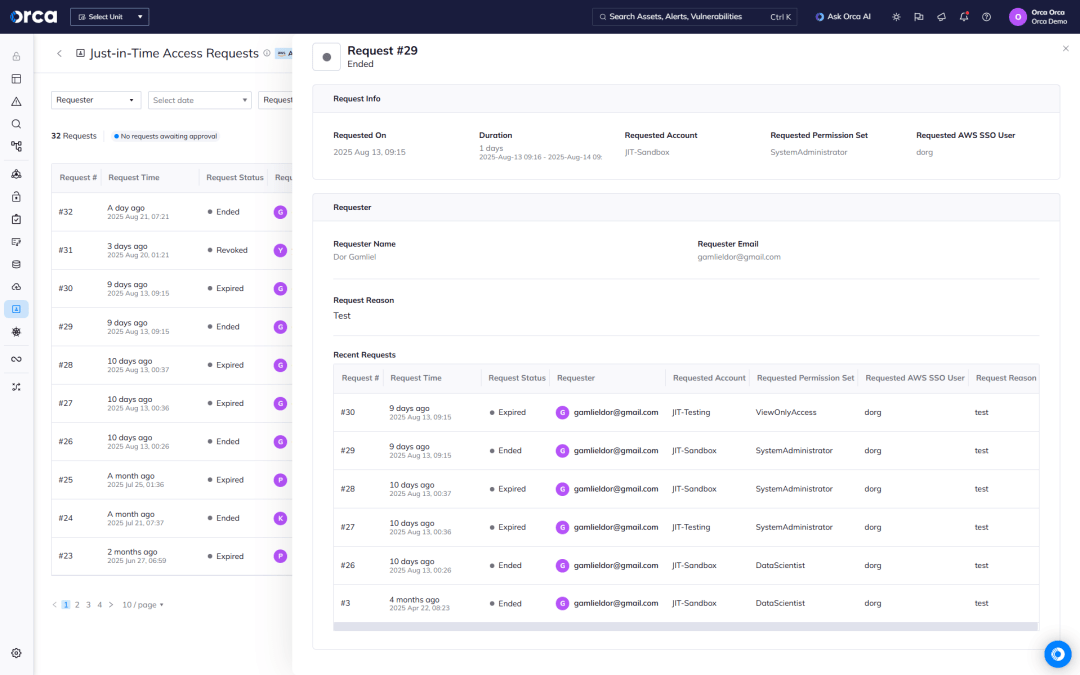
Use Just-in-Time (JIT) Access for least privilege control
Orca offers Just-in-Time (JIT) Access for AWS, enabling teams to reduce standing privileges and enforce least-privilege access across multi-cloud environments without slowing down operations.
- Grant time-bound, role-specific access only when it’s needed, minimizing risks associated with excessive or unused permissions.
- Centrally view and manage JIT requests, see full contextual and historical information for each request, and access detailed audit logs for continuous compliance and oversight.
- Make provisioning flexible and fast with our two-way Slack integration and ability to make and receive JIT requests regardless if you’re logged into the Orca Platform.
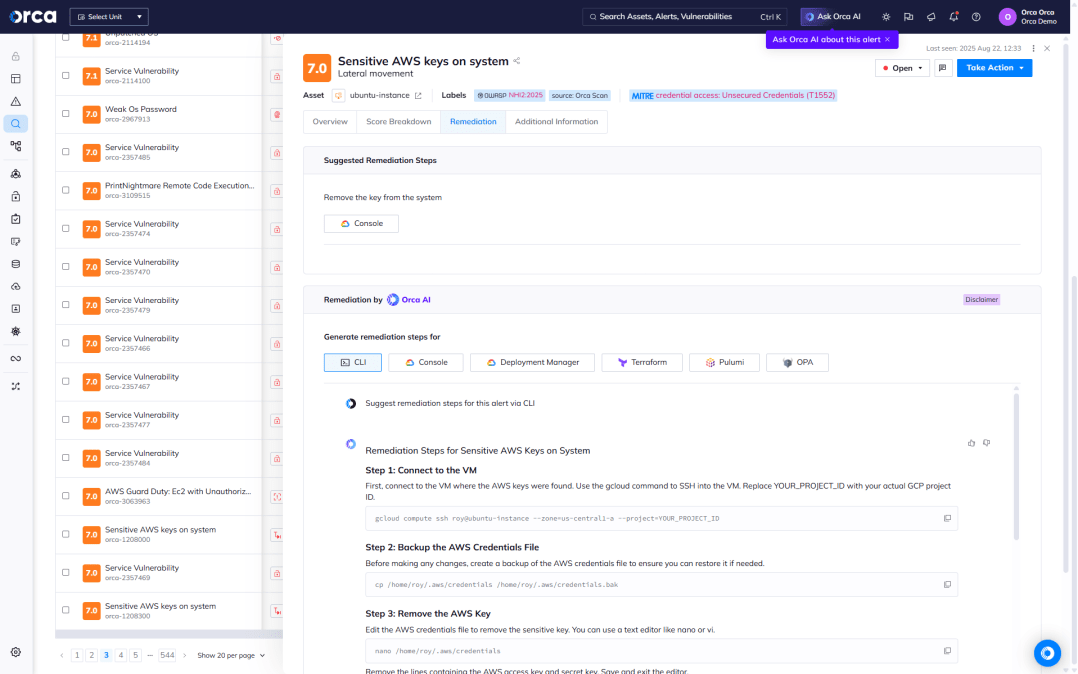
Find insecurely stored keys before attackers do
Unlike point solution CIEM products, Orca scans your unmanaged identities and other telemetry across the entire cloud estate for exposed keys, passwords in shell history, and other information that an attacker can leverage to move laterally in your environment.
- Orca scans each machine’s file system for private keys and creates hashes of all discovered keys. Then Orca scans all other assets for authorized public key configurations with matching hashes.
- Orca surfaces key-related information including paths to insecurely stored keys, workloads that can be accessed with exposed keys, and stored user accounts and permissions.
- Orca discovers any remote access keys, including cloud service provider keys, SSH keys, and more, that might allow attackers to access additional sensitive resources.
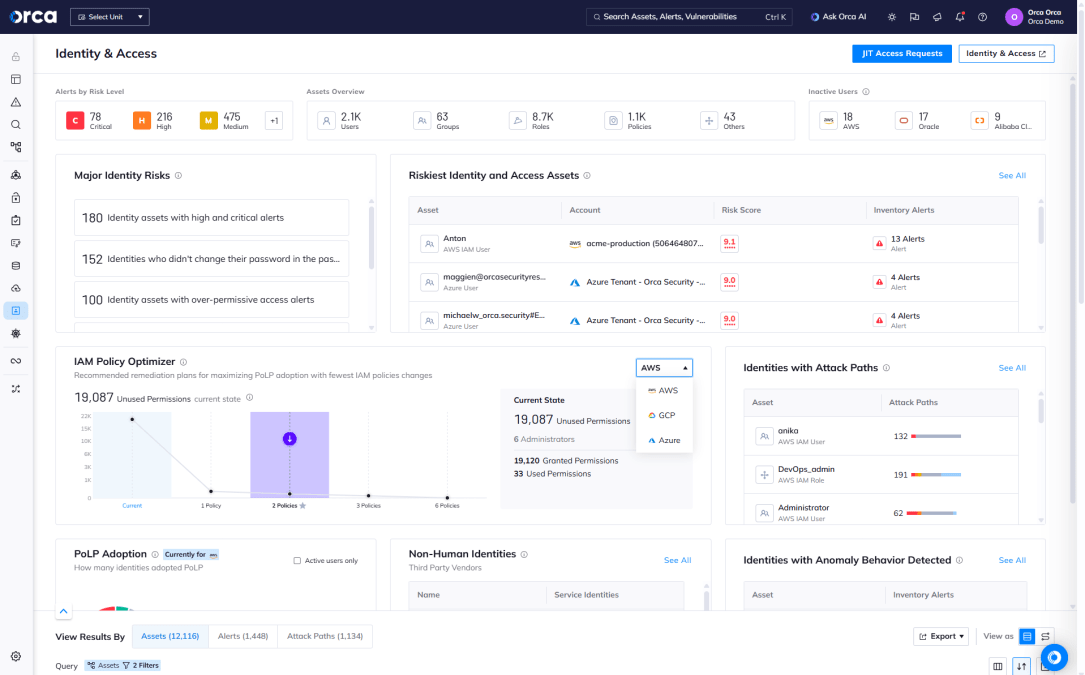
Apply optimal IAM policy configurations
Using prescriptive analytics and artificial intelligence, Orca calculates the largest security improvements that can be made with the least policy changes, and provides ready-to-use configuration files.
- Orca compares existing IAM policies to actual policy usage from the previous 90 days to recommend the largest security improvements with the least amount of effort.
- Orca suggests the optimal configurations that ensure a high level of IAM hygiene and compliance, without overburdening security teams.
- The recommended IAM policies can be downloaded and instantly deployed to your cloud account.
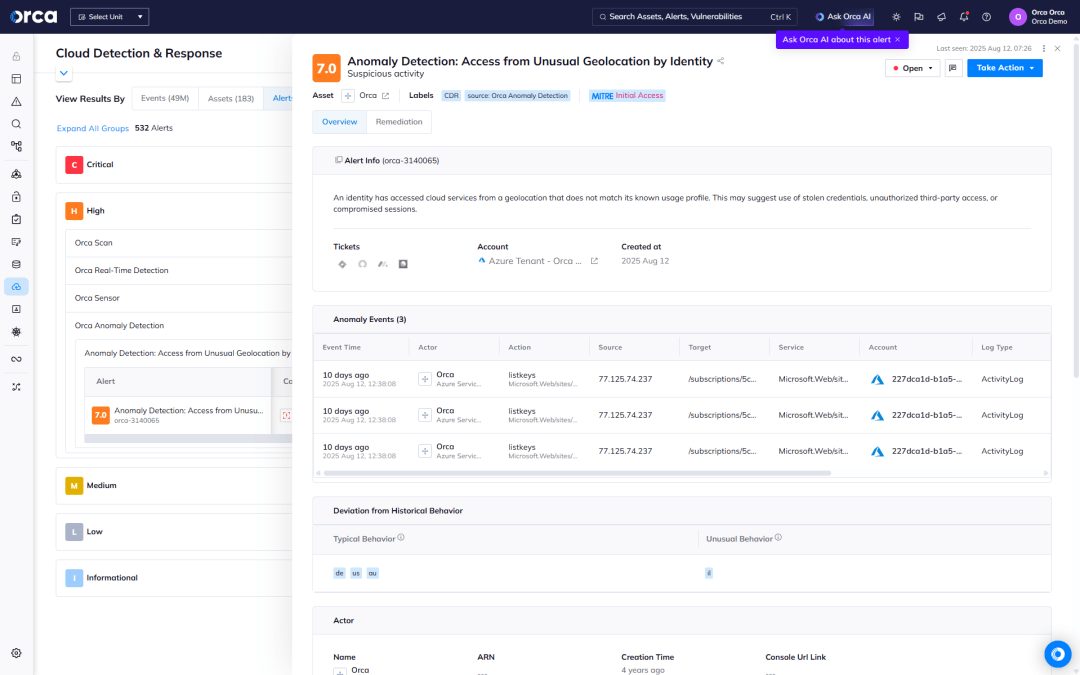
Detect and respond to cloud attacks
Orca allows teams to quickly identify and respond to cloud attacks by continuously collecting and analyzing intelligence from cloud feeds, workloads, configurations and identities in a single platform.
- Detect: Receive alerts when malicious user activities occur, such as compromised accounts and stolen access keys.
- Investigate: Research flagged activity to quickly gain insight into whether the events are malicious and if any of the organization’s critical assets are in danger.
- Respond: Intercept cloud attacks by leveraging remediation steps and automatically assigning issues using Orca’s 20+ third-party technical integrations (including SOAR, notifications, and ticketing systems).
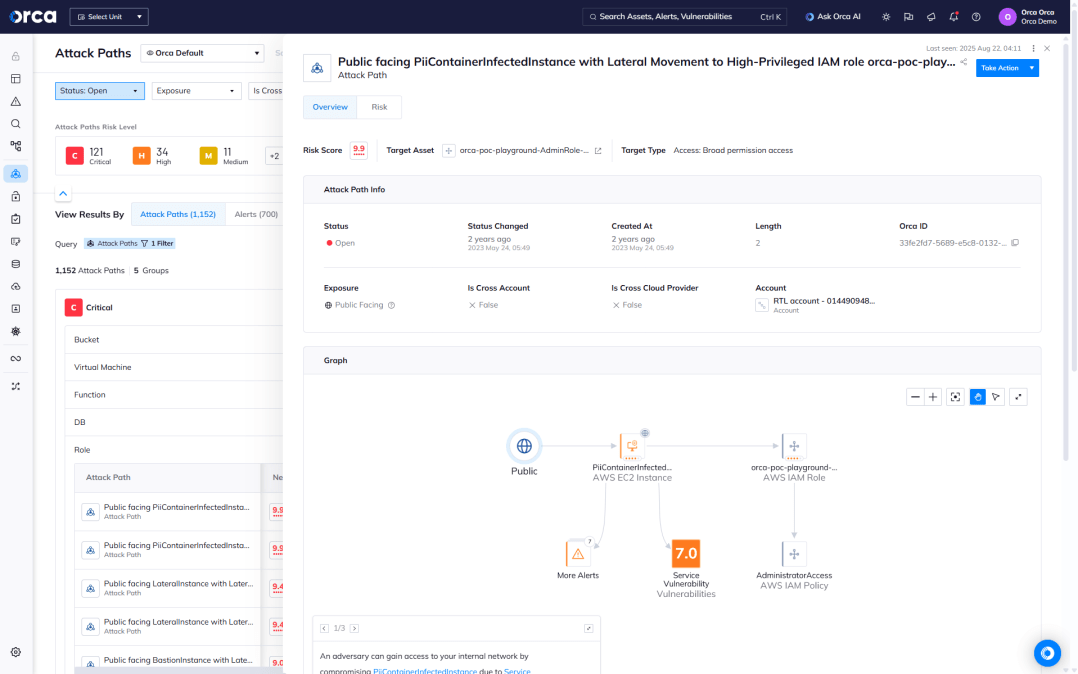
Attack path visualization and prioritization
By analyzing all the risks and vulnerabilities across all layers of your cloud environment, Orca discovers dangerous risk combinations that could result in a direct path to your critical assets, so security teams can focus on what matters most.
- Orca presents each attack path in a visual graph with contextual data on the relevant cloud entities (IAM, compute, storage, etc.) and the relations between them.
- By focusing on a much smaller number of prioritized attack paths, teams don’t need to sift through hundreds of siloed alerts.
- Orca shows teams exactly which issues need to be remediated to diffuse the attack path.
Orca Has You Covered
Frequently Asked Questions
Cloud Infrastructure Entitlements Management (CIEM) is a type of cloud security solution designed to manage access rights and permissions for cloud resource entities. CIEM (pronounced “KIM”) solutions are necessary for implementing the principle of least privilege (PoLP), a security strategy that ensures users only get access to the resources they strictly need to perform their jobs.
CIEM tools are gaining importance amid the continued increase in cloud deployments, infrastructures, and the sheer number of available entitlements.
CIEM enables organizations to successfully manage identity and resource access across rapidly changing cloud environments. Using a CIEM solution, organizations can strengthen their cloud security posture and benefit from compliance assurance, scalable entitlements visibility, cloud permission rightsizing, and automated detection and remediation of access risks.
Three important benefits of CIEMs include:
- Support and compliance for multi-cloud environments: CIEM solutions can provide centralized visibility and compliance for multi-cloud environments. This enables security teams to track cloud assets, compute pieces, services, roles, and entitlements across multiple cloud platforms while ensuring compliance.
- Automatic remediation: CIEM tools can automatically detect and remediate identity and access management (IAM) issues when it comes to entitlements management.
- Continuous validation for cloud infrastructure entitlements: CIEM solutions enable security teams to assess cloud infrastructure entitlements easily and effectively. These tools provide visibility into cloud identities, access policies, entitlements, configurations, permissions, and activities.
To ensure organizations manage cloud asset rights and permissions according to the least-privilege principle, CIEM solutions follow a continuous process that involves the following activities:
- Scan environment: CIEM solutions analyze the cloud environment to inventory all cloud assets, users, and entitlements.
- Inventory cloud estate: CIEM tools use this information to build a comprehensive view of the cloud estate and any risks associated with entitlements.
- Perform automated remediation: After scanning the cloud environment, CIEM tools automatically remediate identified issues, including revoking unnecessary privileges from overly permissioned roles, stopping unauthorized access, and more.
- Continuously monitor and alert: CIEM solutions also continuously monitor the cloud environment for new issues and alert security teams to potential threats or policy issues.
- Generate compliance reports: CIEM tools produce reports that help organizations audit and comply with regulatory frameworks and industry benchmarks.
Orca’s CIEM solution identifies the following risks:
- Privileged roles with cross-account trust
- Inactive IAM roles with admin privileges
- Unattached privileged policies
- Most active roles with cross-account trust
- Compromised assets with privileged IAM permissions
- Privileged inactive identities
In addition to detecting siloed identity risks, Orca uses attack path analysis to identify compound risk, i.e. when identity risks can be combined with other risks to create dangerous attack paths.
Orca provides Cloud Infrastructure Entitlements Management (CIEM) by:
- Promoting identity hygiene, including enforcement of Principle of Least Privilege (PoLP).
- Detecting deviations from identity best practices.
- Using identity data to help understand and prioritize the risks that are found in your system.
- Calculating optimal policy configurations based on role usage in the past 90 days, using Orca’s IAM Policy Optimizer.