Identity and Access Management (IAM) policies play a pivotal role in cloud security by governing access to resources and data within the cloud environment. It defines who can do what, when, and where, forming the foundation of security posture. Managing IAM policies to adhere to the Principle of Least Privilege (PoLP), however, poses a significant challenge, due to complexity, ever-changing cloud environments, the need to balance productivity vs. security, and other factors. This is especially true when managing large environments across multiple cloud service providers.
To alleviate this challenge, we’ve expanded coverage of Orca’s IAM Policy Optimizer, a groundbreaking tool that leverages AI to help security teams almost immediately improve their IAM policies to best comply with the PoLP.
In addition to optimizing AWS IAM policies, the IAM Policy Optimizer now also optimizes Azure Role-Based Access Control (RBAC) policies, and Google Cloud IAM policies. This enables organizations using any of the three major cloud providers to benefit from the significant cloud security posture and efficiency improvements that Orca’s IAM Policy Optimizer brings.
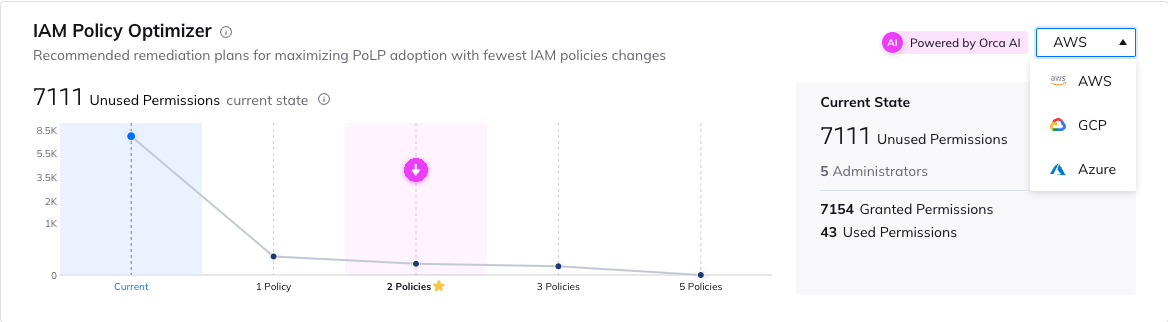
The IAM Policy Optimizer is part of Orca’s CIEM capabilities, and uses AI to automatically calculate the largest security improvements that can be made with the least changes to policies, users or roles. Similar to the “80/20” focus of the Pareto principle, Orca’s AI determines the optimal IAM policy configuration, pointing security teams to the actions that will leave the most significant impact, without requiring them to make massive changes, and provides the optimized configurations as a downloadable file that can be uploaded into the cloud platform. The IAM Policy Optimizer provides organizations with an invaluable time-saving tool to easily increase PoLP compliance while reducing the risk associated with unnecessary permissions and accounts.
The Challenge of Implementing the Principle of Least Privilege
In the cloud, IAM comprises users, roles, and policies, each with its unique nomenclature and challenges.
When it comes to cloud identities, IAM users refer to human actors, such as administrators, developers, and other personnel who require access to cloud resources. IAM roles are similar, in the sense that they are identities in your account that have specific permissions. While roles can also be assigned to human users, they often represent machine identities, which are essential for applications, services, and resources to interact seamlessly within the cloud environment. These roles can be assumed by various entities, including EC2 instances in AWS, service principals in Azure, and service accounts in Google Cloud.
The challenge here is twofold: ensuring that roles are correctly assigned and scoped to specific resources and functions, and that they possess the least privilege necessary for optimal security. Striking this balance is crucial to minimize the risk of accidental or intentional data breaches and system compromises.
IAM policies act as the blueprint for access control, defining what actions are allowed or denied for users and roles. Adding to the complexity, IAM policies are not identical in every cloud provider, and are written in a language specific to each, such as AWS IAM policies, Azure Role-Based Access Control (RBAC) policies, and Google Cloud IAM policies. Herein lies one of the most formidable challenges: crafting policies that are both comprehensive and restrictive enough to meet the PoLP, especially in a multi-cloud environment.
While PoLP compliance sounds straightforward in theory, the practical implementation can be intricate. Several factors contribute to the challenge:
- Granularity vs. Complexity: Striking the right balance between granularity and complexity is challenging. Extremely granular policies, which often provide the highest security, become unwieldy and challenging to manage, while overly complex policies can lead to errors and access violations.
- Changing Needs: Cloud environments are dynamic, with ever-evolving requirements. Keeping IAM policies aligned with changing roles and responsibilities can be a constant battle.
- Focus on Productivity: Organizations often grant more permissions than necessary due to fear of service disruptions. This approach, while seemingly acceptable, may lead to overly permissive policies.
- Lack of Visibility: Understanding the full scope of permissions and access can be challenging, especially in large and complex cloud environments.
Using AI to Calculate the Most Secure IAM Policies
When you add up all of these challenges, and due to the enormous scale of cloud IAM, it’s nearly impossible for humans to adequately audit identity and access privileges to the level needed for security. Having an automated platform to streamline policy creation, provide continuous monitoring, and support enforcement is vital.
This is where the IAM Policy Optimizer is so valuable. Powered by Orca’s AI, the tool—available for cloud accounts in AWS, Azure, and Google Cloud—analyzes permissions usage in the last 90 days, and clusters this usage into separate groups according to behavior. Orca then calculates the largest security improvements that can be made with the least policy changes, as well as suggests a new least-privileged policy to each of the new groups.
How Creating Only One New IAM Role Reduces Granted Permissions by 66%
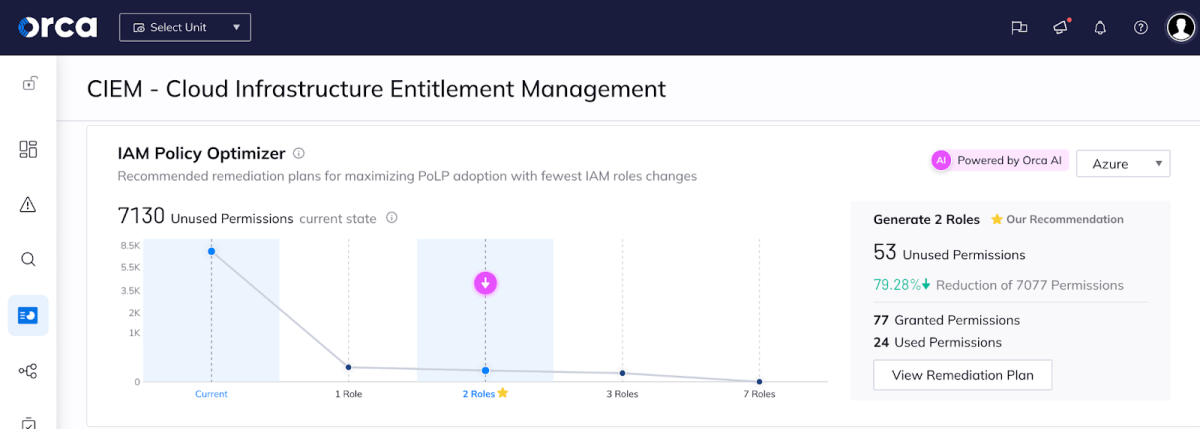
Let’s look at an example. As seen in the screenshot below, Orca has observed that there are 7,130 unused permissions currently in 7 Azure administrator roles. Despite having 7,154 granted permissions, the 7 roles are only currently using 24.
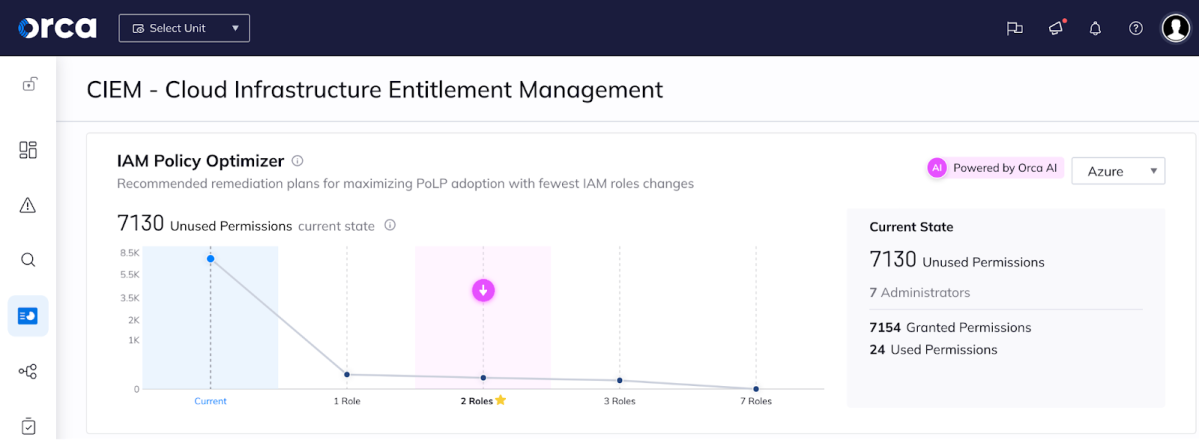
Orca then suggests a range of potential policy changes to better align with least privilege best practices. In our example, these include recommendations that range from requiring the fewest number of policy changes (generating 1 new IAM role that results in a 66% reduction in of granted permissions), to the most changes (generating 7 new roles, in ZERO unused permissions) – see both screenshots below.
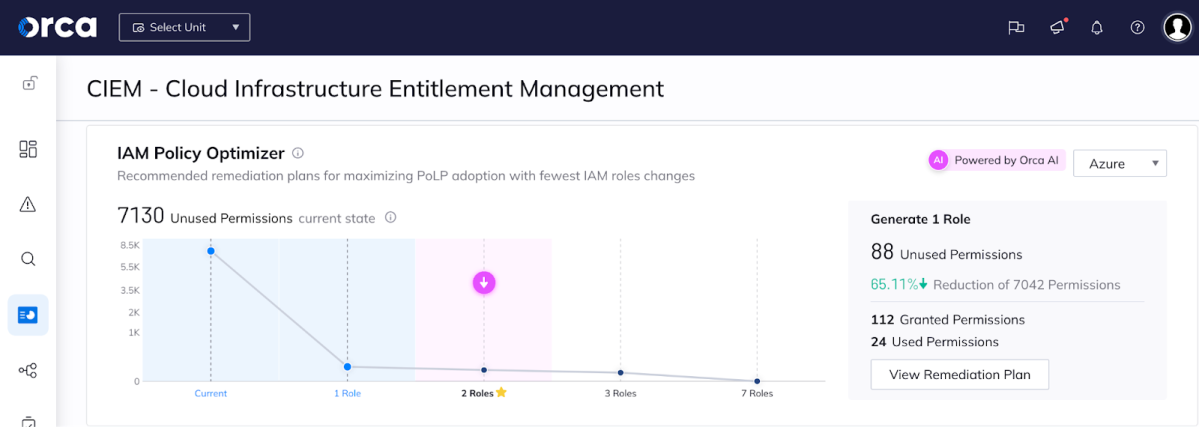
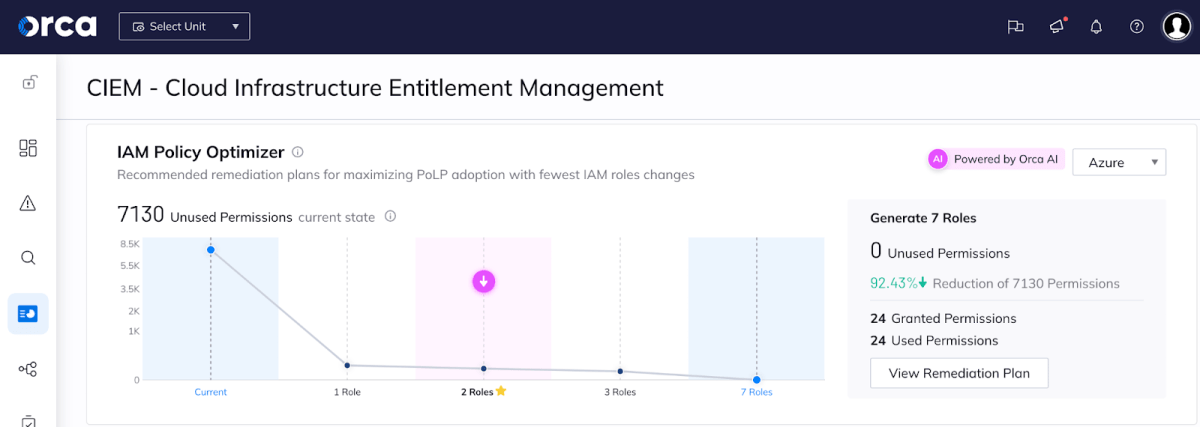
Why Creating Two New IAM Roles is the Optimal Configuration
Even though the optimal security might be reached with 7 new roles, as you can see in the screen above, there is very little security gain as opposed to creating 2 roles. Also, generating too many new roles might carry the risk of “breaking things”, in addition to the resources needed and complexity of carrying out the changes. This is why the IAM Policy Optimizer suggests the optimal configuration of 2 new roles.
The purpose of IAM Policy Optimizer is to find the ideal balance – to create a manageable number of policies with the greatest security gains. By grouping together entities that have similar usage patterns and giving them all the same policy, it makes CIEM work easier and more streamlined. This might give some IAM users more permissions than they already have (i.e. making a new singular role for a team of users may increase permissions of a particular user), but in the long run, it’s better to have 4 policies you understand for 4 groups of users, rather than 100 custom-tailored policies you can’t even begin to control.
In our example, Orca’s ideal recommendation is for the security teams to generate 2 new IAM roles, which would result in only 53 unused permissions, a 79% decrease from the current situation.
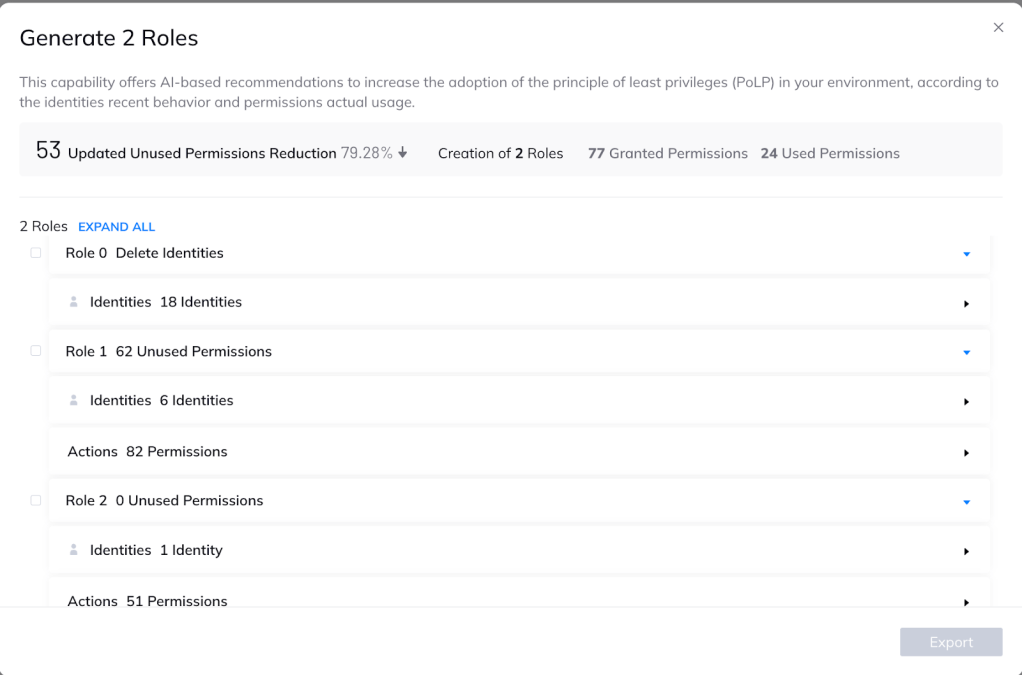
When you choose to view the remediation plan, the Orca platform provides a detailed list of actions to create this recommended policy change. While this can be done manually, Orca allows you to export the policies and automatically apply them in your environment with just a click of a button.
As you can see below, this includes:
- Deleting or deactivating 18 inactive identities (inactive identities increase the attack surface and should be deactivated or deleted)
- creating one role for 6 users with 82 permissions
- creating a second role for a single user with 51 active permissions.
So there you have it: the AI-driven IAM Policy Optimizer makes security teams’ lives easier by providing them with the most impactful IAM policies to adhere to the Principle of Least Privilege, with the quickest route to get there.
Other Ways Orca Uses AI for Cloud Security
Orca Security has been at the forefront of innovation when it comes to incorporating AI into cloud security. The Orca Platform extensively harnesses AI to bolster risk detection, streamline investigations, and accelerate remediation processes. This translates to substantial time and effort savings for cloud security, DevOps, and development teams, all while yielding markedly improved security outcomes.
For example, the Orca platform utilizes AI for advanced anomaly detection as part of our Cloud Detection and Response (CDR) capabilities, empowering SOC and incident response teams to identify suspicious activity, accelerate triage, and respond strategically.
Likewise, Orca offers AI-generated instructions to remediate risks, through an integration with GPT-4. When alerted by Orca to a security risk, security teams receive guided remediation steps for insertion into their preferred platform, such as CLI, Terraform, Pulumi, AWS CloudFormation, AWS Cloud Development Kit, Azure Resource Manager, Google Cloud Deployment Manager, and more.
In addition, Orca recently released our new AI-powered search, security practitioners as well as developers, DevOps, cloud architects, risk governance, and compliance teams can easily and intuitively understand exactly what’s in their cloud environments.
Wait until you see what we have planned in the near future. Stay tuned!
Learn More
To learn more about the Orca Cloud Security Platform, you can:
- Read more about our Cloud Infrastructure Entitlement Management (CIEM) capabilities
- View our latest recorded demo or schedule a personal demo for your team






