With organizations continuing digital transformation efforts and public cloud adoption breaking down traditional network barriers, misconfigurations surrounding cloud identities and access privileges represent one of the most dangerous risks in cloud security. These misconfigurations—which include inactive identities, overprivileged identities, and identities with cross-account access—increase the cloud attack surface and are a major concern for security teams. Gartner predicted that by 2023, 75% of security failures will be caused by insufficient management of identities, access, and privileges.
CIEM (Cloud Infrastructure Entitlement Management) is focused on helping organizations detect identity-related misconfigurations, ensure least-privilege compliance, and monitor identity hygiene in cloud environments. We are excited to announce that Orca has:
- Expanded its CIEM capabilities with broader cloud coverage and visibility for multi-cloud environments
- Added detections for a wide range of identity-related risks
- Released the CIEM Security View dashboard to improve user experience for more easily managing information about cloud identities
Overall, these capabilities empower organizations to better understand the relationship between their identities, access rights, and cloud resources, and reduce their cloud attack surface.
New CIEM Dashboard Brings Wider Cross-Cloud Visibility
Orca’s newly-released CIEM Security View provides security teams with a fresh design, brings wider cloud coverage, and offers a smooth user experience for security and compliance teams.
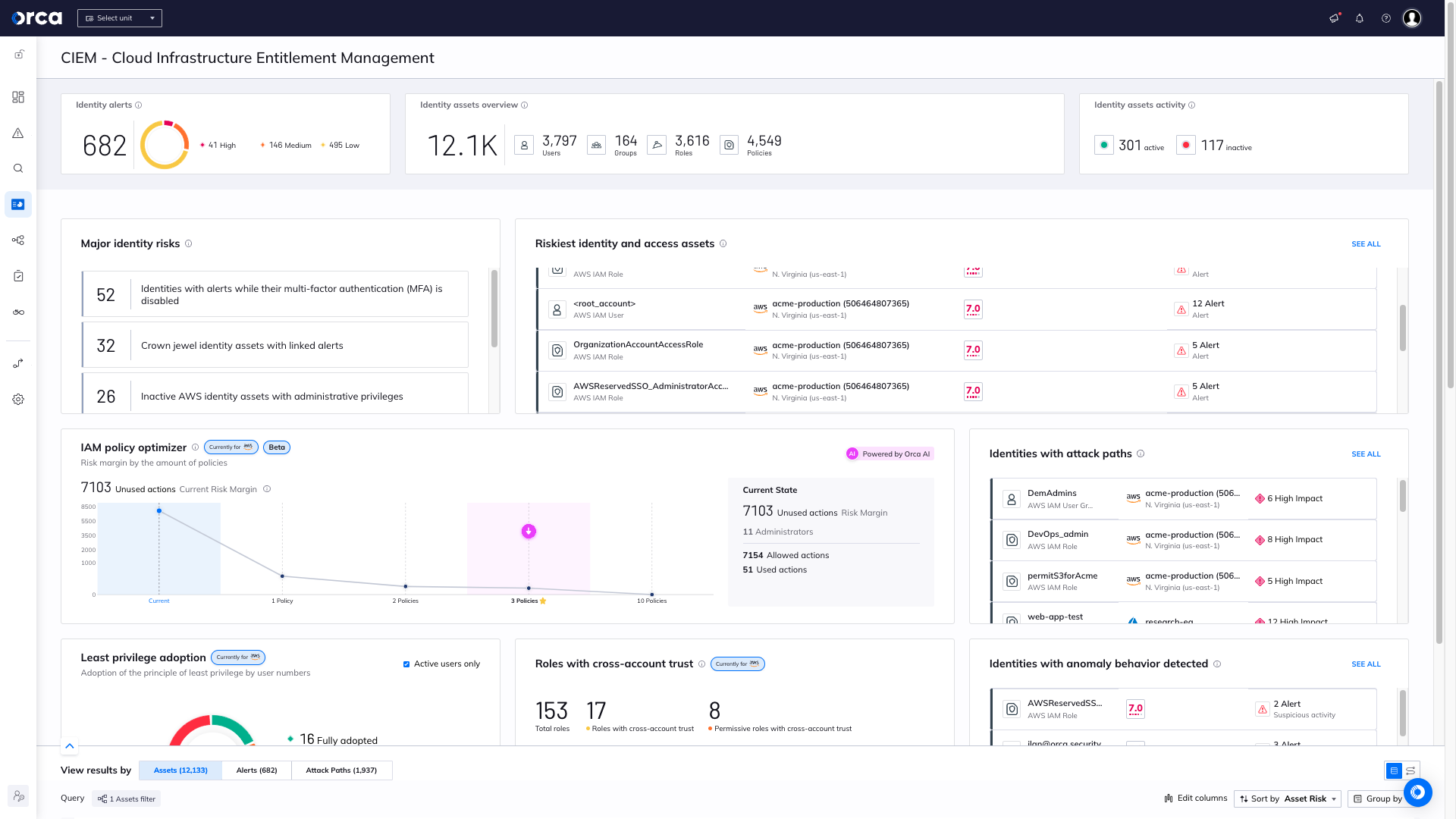
The CIEM Security View provides security teams with:
- Multi-cloud CIEM coverage in a single, unified platform, including information about users, groups, roles, and policies
- Identity and access posture management, with identity-related risks taking into account the wider cloud risk context
- A smooth user experience that delivers vital data to security teams in a clear and digestible manner, via a single page and unified flow
We discuss each benefit in detail in the sections below.
Multi-cloud CIEM Support
Orca has expanded its CIEM capabilities to cover all Orca-supported cloud platforms, including accounts in AWS, Microsoft Azure, Google Cloud, Alibaba Cloud, and Oracle Cloud Infrastructure.
The Identity assets overview section provides a wide view into users, groups, roles, and policies, with each asset clickable to allow for deep insights into each individual asset, including associated identity risks.
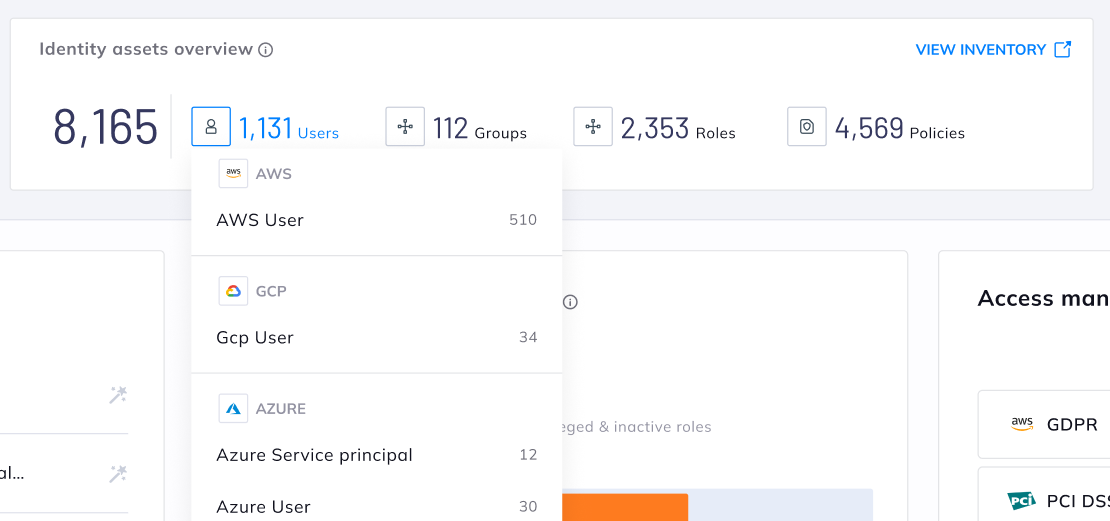
A single, multi-cloud cloud security solution is more beneficial for organizations than cloud platform native security tools, which are specific to each platform. When it comes to CIEM, the ability of security and compliance teams to not only have as wide a lens as possible across their cloud estate, but also to see the potential interconnected identity-related risks across each platform, greatly improves identity asset and risk management, without the need to maintain and align policies across disparate solutions.
Detection and Prioritization of Identity and Access Risks
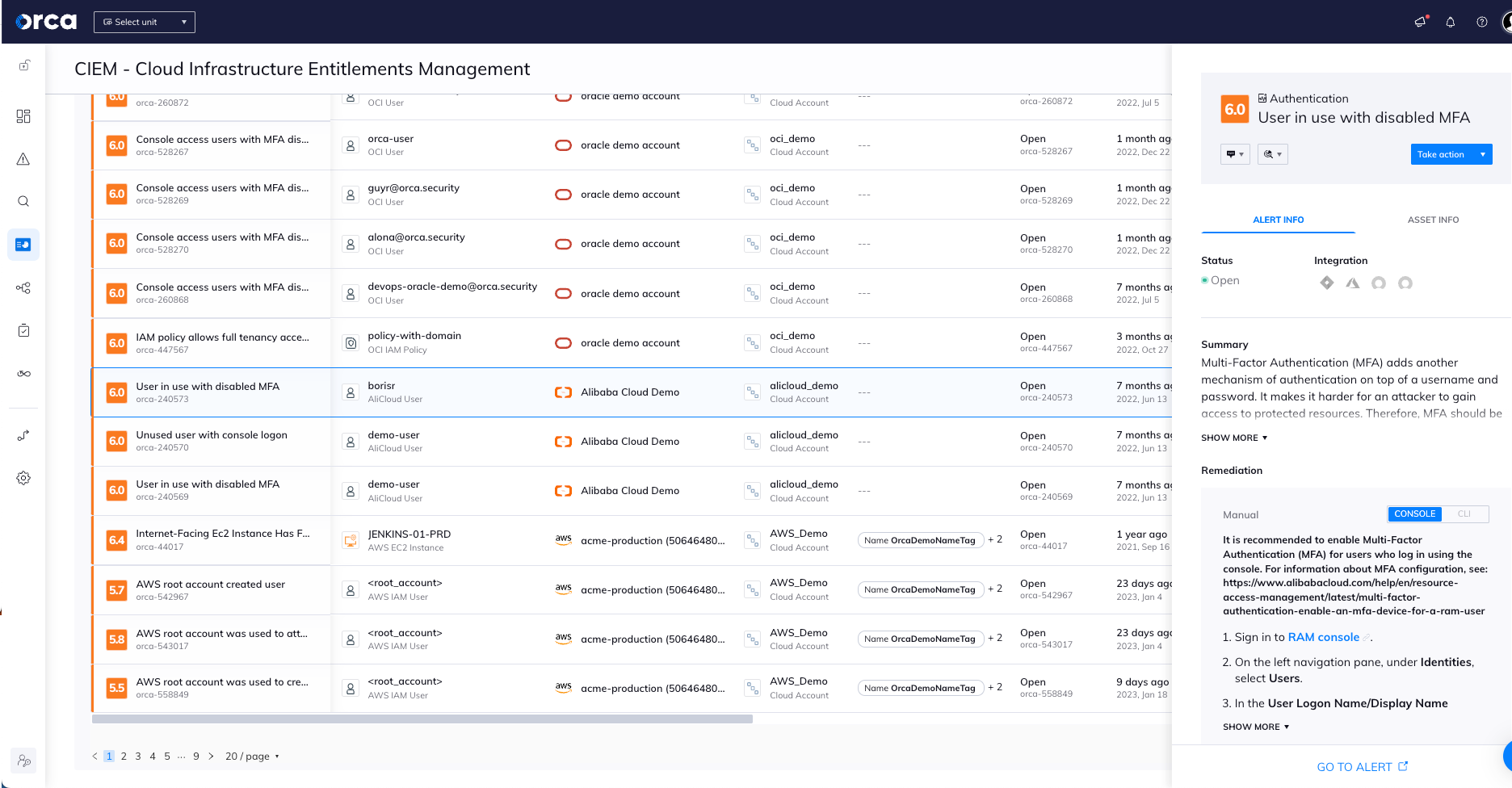
Beyond an inventory of identity assets, Orca’s CIEM capabilities enable customers to improve their identity hygiene to reduce their attack surface. Identity hygiene best practices are primarily driven through adopting the Principle of Least Privilege (PoLP). Orca identifies identity misconfigurations and other related risks and provides several tools to allow you to quickly investigate and triage issues. For example, Orca identifies over-privileged Identities with a high percentage of unused access and powerful infrastructure permissions.
Orca customers can see a breakdown of active and inactive users (based on its activity within the last 90 days). It’s best practice to reduce privileges of inactive users, or to delete them entirely, if deemed appropriate.
Orca alerts when unused or overly permissive identities are found and prioritizes them—including an assigned Orca Risk Score— according to potential business impact.
The Major identity risks widget provides a valuable list of the most prevalent and alarming identities with high-impact risks in your cloud estate. Examples include:
- MFA-disabled Identities with high-severity alerts
- Inactive AWS identity assets with administrative privileges
- Identities with alerts who didn’t change their password in the past 90 days
Clicking on each category will bring you further down the same page with an easy-to-consume list of the specifics of each risk and impacted identity asset.
It’s also important to note that instead of providing identity and access privilege management in a siloed solution, Orca combines identity risks with other risk data—vulnerabilities, misconfigurations, malware, the location of sensitive data, and lateral movement risk—to help you prioritize the risks in your environment in a holistic way. In contrast, CIEM point solutions don’t have visibility into workload risks and unmanaged identities, such as SSH keys, passwords in shell history, whether a cloud asset is internet-facing, and other critical issues, thereby limiting visibility into wider cloud context.
Further, by applying Attack Path Analysis Orca warns when attackers could combine individual identity-related risks in the cloud environment to form potentially dangerous paths toward sensitive assets. Each attack path is automatically scored based on a number of criteria, including exploitability, severity, and business impact. This allows security teams to focus on remediating the risks that pose the greatest danger to the organization’s sensitive data, reducing alert fatigue and preventing potentially damaging data breaches.
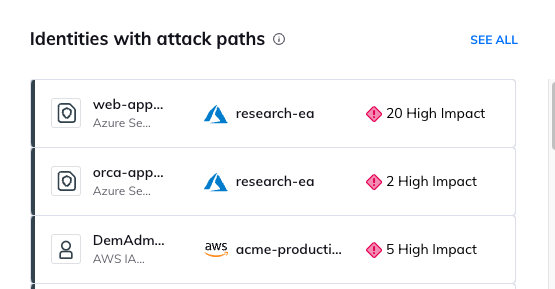
Other valuable widgets on the CIEM security view include:
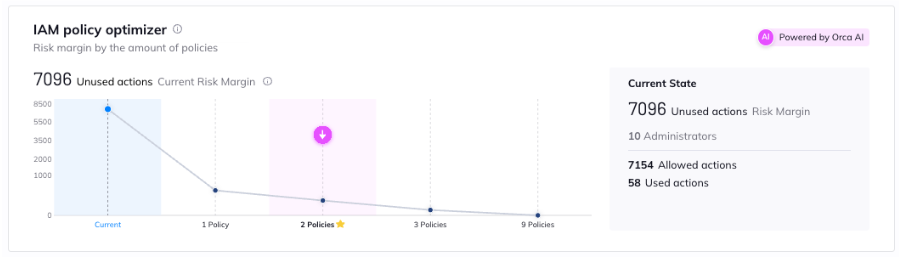
- IAM Policy optimizer: Powered by Orca’s AI, this analyzes IAM administrators’ recent usage, and clusters this usage into separate groups according to behavior. Orca calculates the largest security improvements that can be made with the least policy changes, and provides teams with guided remediation steps to reduce IAM risk, as well as suggests a new least-privileged policy to each of the new groups. Users can implement custom remediation based on their own playbooks for an alert, or initiate on-demand remediation directly from Orca telemetry. NOTE: Stay tuned for more news about the policy optimizer in the coming weeks.
- Roles with cross-account trust: This summarizes how many roles you currently have in your AWS environment, how many of them have cross-account trust (meaning they can be granted access between multiple AWS accounts in the same organization), and then how many of those are “permissive” with broad access permissions. This enables you to easily prioritize which roles you need to pay attention to, and to lower the usage as much as possible with these roles.
- Identities with anomaly behavior detected: This widget shows the top 10 Identity and Access assets associated with anomaly detection alerts, sorted by the asset risk score. This enables SOC and IR teams to accelerate triage and investigation into potential security events.
Easy User Experience
The CIEM security view gives security teams an ‘HQ’ for all CIEM, without the need to leave the dashboard for other pages. This includes CIEM alert information, remediation actions, and even the ability to perform auto-remediation steps from the same page.
In addition, the fresh new user interface features color-differentiation and spacing to present CIEM data in a digestible, accessible manner.
Ready to Try Orca Security’s CIEM Capabilities?
Sign up for a free 30 day cloud security risk assessment or request a demo of the Orca Cloud Security Platform and get full visibility of your cloud estate, including critical identity risks.






