Cloud environments, and the cloud native applications that run on top of cloud infrastructure, are highly dynamic. While detecting and responding to security incidents is critical in every environment, the nature of cloud computing complicates these tasks, requiring new methodologies and technologies.
In many cases, teams have attempted to use agent-based solutions to continually monitor and capture information covering cloud workloads. While this may be useful for a handful of business-critical applications, the management overhead in a large cloud native environment is a challenging burden.
Expanding Cloud Detection and Response with Forensic Snapshots
The Orca Cloud Security Platform delivers integrated Cloud Detection and Response (CDR) capabilities. These capabilities combine data from SideScanning snapshots with cloud provider audit logs, third-party agents, and the Orca Agent to detect suspicious activity, potential compromises, or advanced threats.
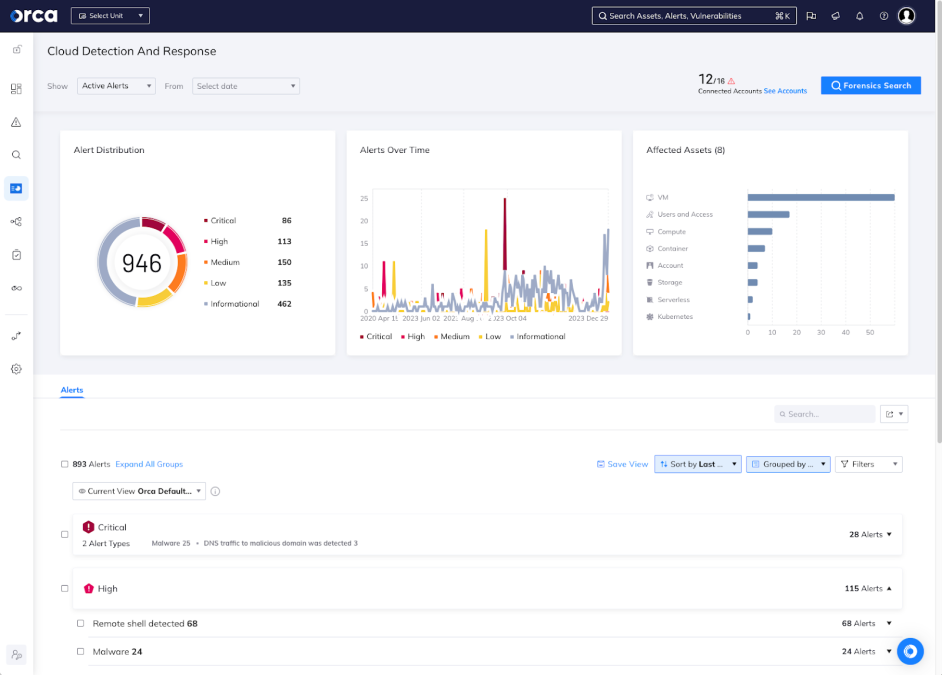
Cloud Detection and Response (CDR) dashboard in the Orca Cloud Security Platform
The Orca Platform can identify:
- Malware within an application filesystem
- Remote shell detection
- Suspicious activity in process memory
- Brute force attempts to cloud assets
- API access to malicious IP addresses
- And many more risks
Specifics on Forensic Snapshots
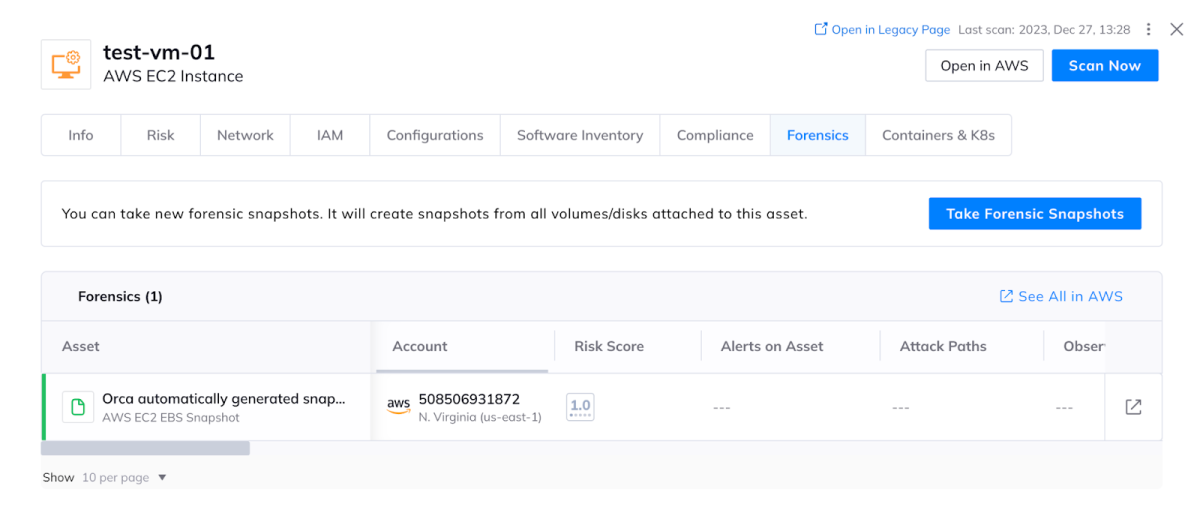
Analyzing an AWS EC2 instance with the option of taking forensic snapshots
From the beginning of this article we’ve highlighted the essential nature of Incident Detection and Incident Response. As the threat landscape continues to evolve, so too do our response methodologies. Digital Forensics and Incident Response (DFIR) is one of these. Incident Response can tend to focus on resolution and remediation of the incident as opposed to the subsequent investigation into root cause or post-incident improvement. However, without including some investigation of both the root cause and the potential spread of an incident, it can be impossible to ensure that the attacker is no longer resident or that they won’t easily return.
DFIR is an approach that allows the incident to be resolved whilst actively maintaining the required information to then revisit the circumstances so as to prevent similar incidents in the future. Orca Security’s forensic snapshots feature allows security and incident response teams to quickly generate usable forensic images of workloads without having to engage with other teams or external processes.
During an incident, teams can quickly and simply gather the necessary forensic snapshots while triaging the incident in Orca Security. This avoids the discovery and manual snapshotting that would be required for each of an asset’s storage areas. That involves identifying each volume and, using the cloud service provider’s tooling, snapshotting each one. Multiply this manual effort across the compute that would be part of the blast radius of an incident and you can immediately see the benefits of having this available in the same place you’re running your incident response from!
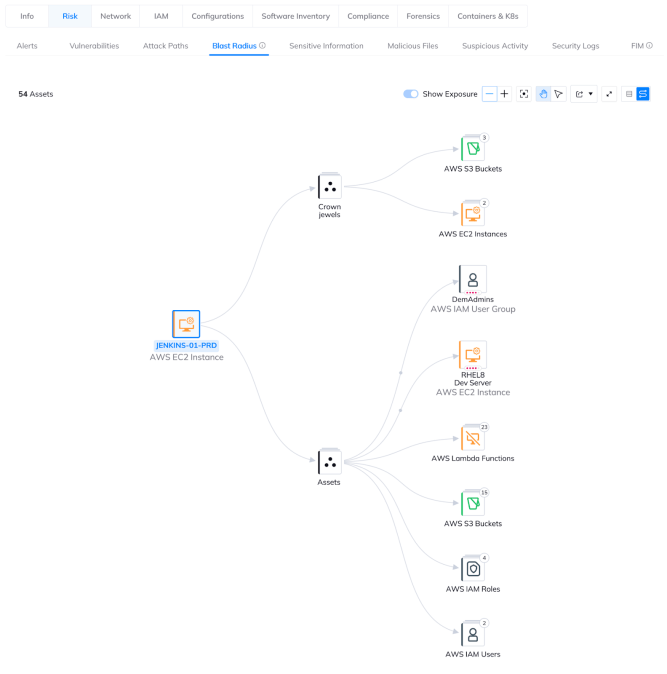
Analyzing the blast radius of a risk
Orca generated forensic snapshots are supported across:
- AWS EC2 Instances
- Azure Compute VM Instances
- GCP Compute VM Instances
- Auto Scaling Groups (ASG)
- Scale Sets
The Orca platform immediately treats these snapshots as any other asset. This means they, too, are part of the platform’s coverage and subject to the same compliance controls, risk analysis, and deep inspection for risks and issues. They are clearly labeled in the Orca platform as well as natively in the cloud service provider.
To learn more about our forensic capabilities or to see how Orca Security detects risks and threats across all your cloud assets and resources, please schedule a 1:1 demo with one of our team members.