IAM User with Administrative Privileges
Hazardous (3)
- Orca Best Practices
About AWS Identity and Access Management (IAM)
AWS Identity and Access Management (IAM) is a service that lets you manage and secure access to your AWS resources. IAM ensures that a user is authenticated (signed into AWS) and authorized (has required access permissions) before granting access.
An IAM user is an entity that a person or an application uses to interact with AWS resources. By default, a newly created IAM user has no privileges whatsoever. Neither will they have the authorization to perform any operation, nor the permissions to access any AWS resource.
AWS IAM makes it easy to assign permissions based on user roles. For example, a system architect may have permission to access all the resources in your environment, whereas an external consultant may only have access to a specific EC2 instance.
You can also give an IAM user admin privileges, which essentially allows them to do anything in the AWS environment. They can access, modify or delete resources, read and edit any data, and even provision or delete other users.
Cloud Risk Description
An IAM user may have administrator privileges, allowing them to freely perform any operation, or access any resource, in an AWS environment. The principle of least privilege dictates that no entity should have more than the bare-minimum level of permissions required to do their job. So, instead of granting admin privileges, an IAM user should only be granted the permissions they absolutely need to perform their duties.
How Does Orca Help?
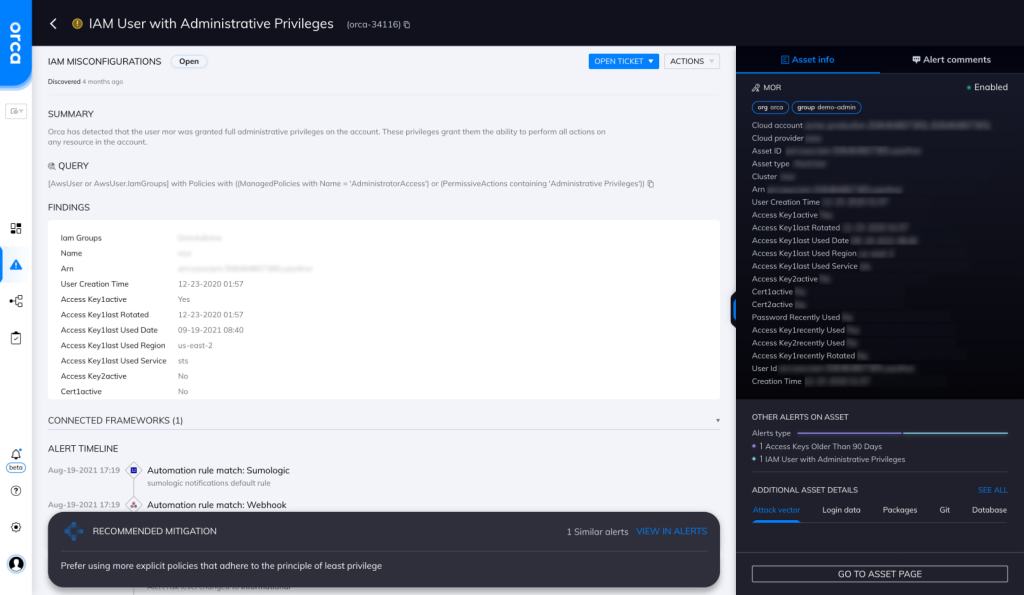
Orca detects and prioritizes identity and access management misconfigurations such as overly permissive identities. Continuous IAM monitoring across your cloud estate prevents malicious and accidental exposure. In this specific case, Orca helps by looking for “IAM Users with Admin Privileges” and will alert on this type of issue as shown in the screenshot above.
Recommended Mitigation Strategies
-
Apply principle of least privilege
Always apply the principle of least privilege while creating IAM users.
-
Enable MFA
Enable MFA for all AWS users.
-
Keep it clean
Remove any unnecessary or unused IAM users from your AWS account.
-
Audit users
Regularly audit for IAM users with admin privileges.
Useful Links
- Security best practices for IAM: https://docs.aws.amazon.com/IAM/latest/UserGuide/best-practices.html
- IAM features: https://docs.aws.amazon.com/IAM/latest/UserGuide/intro-structure.html
- IAM users: https://docs.aws.amazon.com/IAM/latest/UserGuide/id_users.html
- Managing IAM users: https://docs.aws.amazon.com/IAM/latest/UserGuide/id_users_manage.html
- Tagging IAM resources: https://docs.aws.amazon.com/IAM/latest/UserGuide/id_tags.html
- Troubleshooting IAM: https://docs.aws.amazon.com/IAM/latest/UserGuide/troubleshoot.html
- IAM introduction: https://orca.security/resources/blog/anatomy-identity-and-access-management-cyber-attack-aws/
Orca Security, the cloud security innovation leader, provides cloud-wide, workload-deep security and compliance for AWS, Azure, and GCP - without the gaps in coverage, alert fatigue, and operational costs of agents.
