Lambda Function Exposes AWS Secret
Hazardous (3)
- Orca Best Practices
About AWS Lambda
AWS Lambda is an event-based, serverless computing platform that allows you to run code without provisioning or configuring infrastructure. There’s no need to spin up new servers or containers, perform OS maintenance, or manage memory and CPU cycles; the platform does it for you. All you have to do is execute your code via Lambda functions.
Lambda execution is triggered by demand. Your application runs and scales as required, from a few requests per hour to thousands per second.
Lambda provides a developer-friendly API for invoking functions. It can also execute function logic in response to certain events generated by other AWS services. For example, if Lambda receives a login event from a configured web service, it can execute the authentication function, which verifies the identity of the user.
Lambda also allows using environment variables for setting configuration values without modifying code. Environment variables are stored as key-value pairs and can be accessed by the application during execution. Ideally, environment variables shouldn’t contain sensitive information like secrets, tokens, passwords, and cryptographic keys; instead, they should be stored in purpose-built keystores, like AWS Secrets Manager.
However, if security-critical information is to be stored as environment variables, those variables should be encrypted. This protects data from unauthorized access, and allows you to conform with various security and compliance standards.
Cloud Risk Description
Lambda environment variables that store critical data like tokens, secrets, encryption keys, hash salts, and passwords, etc., should be encrypted. This keeps sensitive information safe from unauthorized access.
How Does Orca Help?
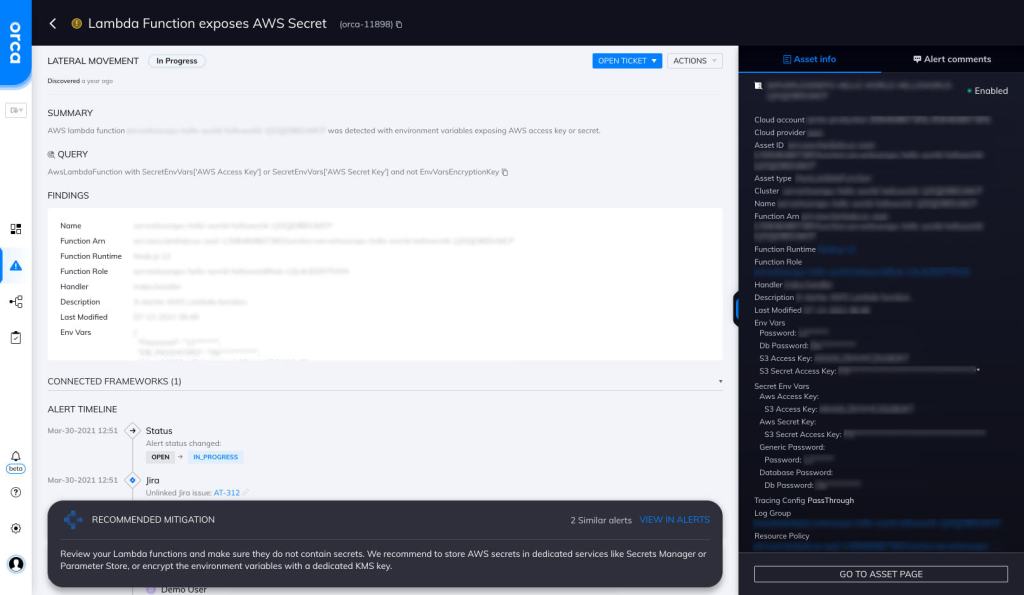
Orca detects sensitive data at-risk across both the workload and control plane, pinpointing the exact location and providing masked samples of the data for quick remediation. Orca is able to look for secrets in environment variables and alert on them. In this specific case, Orca helps by looking for “Lambda Functions that Expose AWS Secrets” and will alert on this type of issue as shown in the screenshot above.
Recommended Mitigation Strategies
-
Store information safely
Use safer alternatives to store sensitive information like AWS Secret Manager.
-
Encrypt
Ensure that all environment variables storing security-critical information are encrypted.
-
Apply the principle of least privilege
When setting IAM policies for Lambda functions, apply the principle of least privilege.
-
Keep it clean
Delete any Lambda functions that you are no longer using.
-
Use SSL/TLS
When communicating with other AWS services, use SSL/TLS.
-
Use Amazon Macie
Use Amazon Macie to detect and protect your sensitive information.
Useful Links
- AWS Lambda Secrets: https://orca.security/resources/blog/aws-lambda-secrets/
- Using environment variables in Lambda: https://docs.aws.amazon.com/lambda/latest/dg/configuration-envvars.html
- AWS Lambda features: https://aws.amazon.com/lambda/features/
- Configuring Lambda functions: https://docs.aws.amazon.com/lambda/latest/dg/lambda-functions.html
- Invoking Lambda functions: https://docs.aws.amazon.com/lambda/latest/dg/lambda-invocation.html
- AWS Lambda security: https://docs.aws.amazon.com/lambda/latest/dg/lambda-security.html
- Lambda troubleshooting: https://docs.aws.amazon.com/lambda/latest/dg/lambda-troubleshooting.html
- AWS Secret Manager: https://aws.amazon.com/secrets-manager/
- Amazon Macie: https://aws.amazon.com/macie/
Orca Security, the cloud security innovation leader, provides cloud-wide, workload-deep security and compliance for AWS, Azure, and GCP - without the gaps in coverage, alert fatigue, and operational costs of agents.
