On March 7, 2022, a new critical Linux privilege escalation vulnerability was published under the ID CVE-2022-0847, and named “Dirty Pipe”. This vulnerability affects every major Linux distribution from Linux kernel version 5.8 and above.
CVE-2022-0847 allows local unprivileged users to gain root privileges in a few small and easy steps, which make this vulnerability highly exploitable.
In fact, this vulnerability is so broad that it even affects Android devices. This vulnerability is similar to CVE-2016-5195, known as “Dirty Cow”, however, this vulnerability is considered more dangerous because it is easier to exploit.
What are Pipes?
Pipes, or pipelines, in Linux are an operating system (OS) functionality to deliver information between processes. Many Linux users use pipes to chain processes, so that the output of the first process, would be the input of the second process.
The “Dirty Pipe” Vulnerability Details
CVE-2022-0847 was found by security researcher Max Kellermann. He found that an unprivileged user can gain root privileges by injecting and overwriting code into read-only files including root processes.
This vulnerability exploits a flaw in the new pipe structure and in specific, in the way linux kernel handles pipe buffer flags. This can lead to an unprivileged user inserting data into a pipe and overwriting data in a root process, to further escalate their privileges on the system.
A public exploit has already been published, making it easy for a malicious force to use it.
From a containers perspective, this vulnerability makes it possible to modify files from container images on the host- and from there, effectively modify containers running on the same shared host or modify an image on a host so that every new container would relay and receive the modified files.
Remediation
All Linux systems, including Android devices, from Linux kernel version 5.8 are vulnerable. To remediate CVE-2022-0847 an update is needed, as Linux versions 5.16.11, 5.15.25 and 5.10.102 are patched for this vulnerability, and in the latest Android kernel.
Identifying the CVE with Orca Security
The Orca Security Platform can detect workloads impacted by CVE-2022-0874. In the main Risk Dashboard, users can navigate to the “From the News” widget and click on the “Dirty Pipe” announcement to learn more about the risk and see all the workloads that are vulnerable to the CVE.
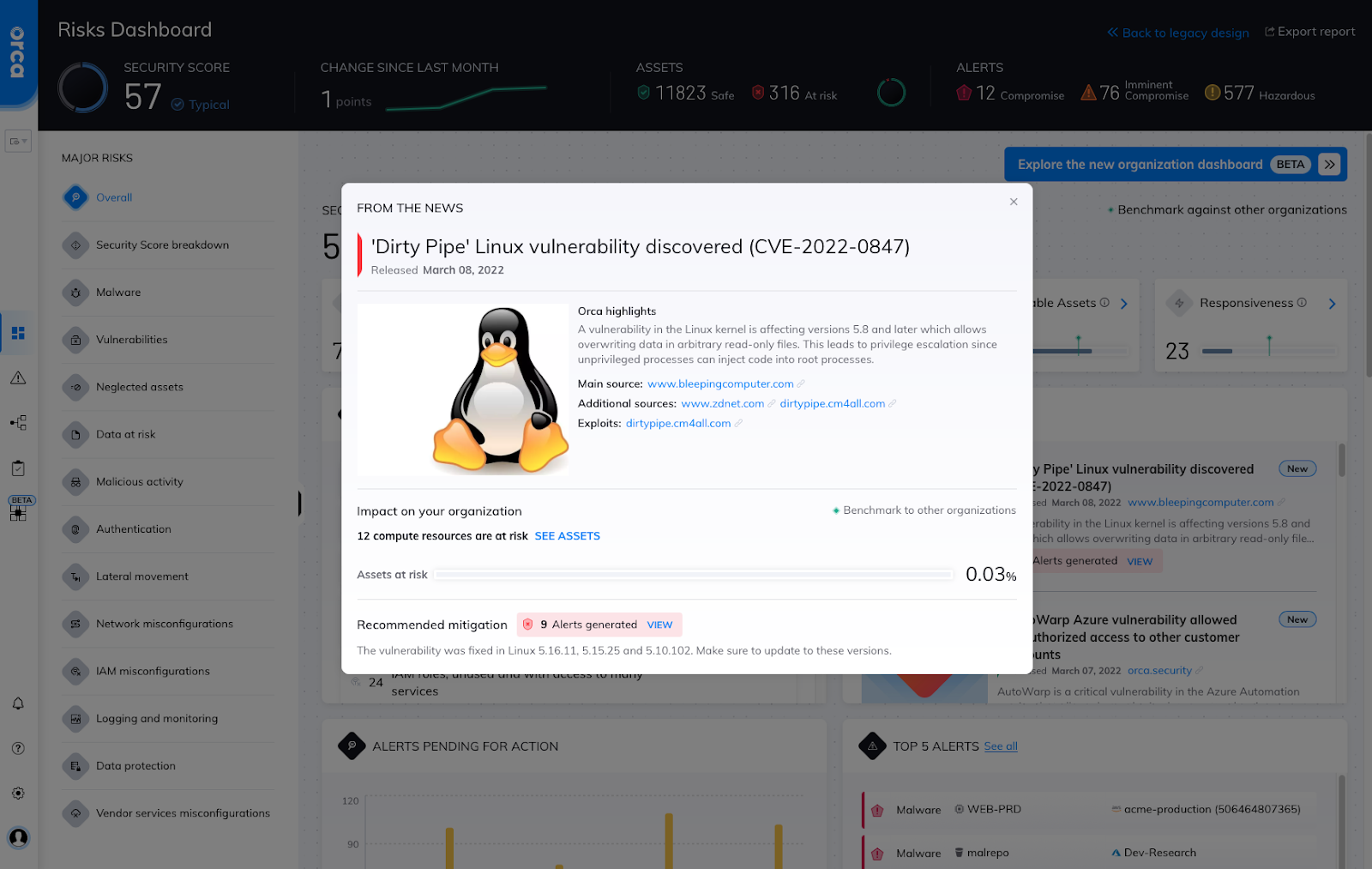
Dirty Pipe details within the Orca UI
Next, users can then click on View to expose specific finding details, prioritized by assets with the greatest risk.
Finally, users can explore the vulnerability details to learn more about CVE-2022-0847 and how to patch their workloads.
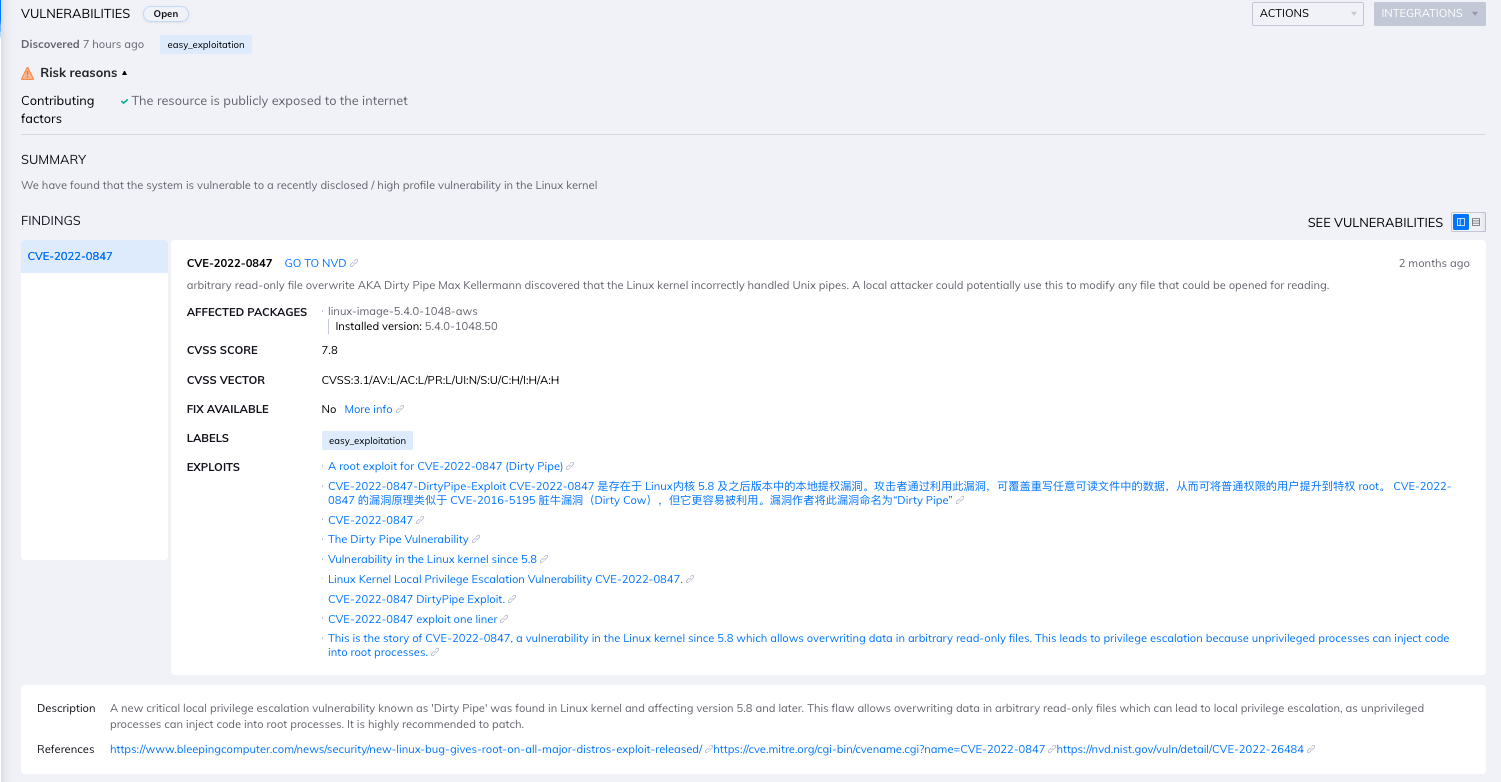
In-depth summary of the CVE with the Orca Security Platform
Sign Up for a Free Risk Assessment
To see if your environment is impacted by this CVE or other known vulnerabilities, sign up for a free risk assessment today.





