Gartner® recently published a new report titled, Innovation Insight: Cloud Infrastructure Entitlement Management. The report highlights the primary challenges, use cases, and benefits of CIEM, including an analysis of key CIEM capabilities and market trends.
In this blog post, we’ll discuss a few of the key observations from the report, one of which is a convergence of CIEM with wider cloud security capabilities. Along those lines, we’ll detail how the Orca Cloud Security Platform’s multi-cloud CIEM capabilities help organizations identify and prioritize cloud identity risks in an actionable way.
To read the full report, download the Gartner CIEM research.
What is CIEM?
CIEM (Cloud Infrastructure Entitlement Management, typically pronounced as “Kim”) capabilities, whether in a standalone tool or as part of a broader cloud security platform, are focused on helping organizations detect identity-related misconfigurations, ensure least-privilege compliance, and monitor identity hygiene in cloud environments.
CIEM solutions provide the mechanisms and operational tools for organizations to apply the Principle of Least Privilege (PoLP) to cloud infrastructure assets, entities, and configuration. They assist organizations in not only improving cyber hygiene, but also in defending against data breaches, malicious attacks, and other risks posed by excessive cloud permissions. Most significantly, the primary objective of CIEM technologies is to reduce the risk associated with the inadvertent and unregulated allocation of excessive, unused, and standing permissions to cloud resources.
CIEM benefits and use cases
The adoption of multiple cloud platforms by organizations and expansion of their cloud resources across a wider cloud estate has created challenges. The report’s analysts write:
“Multi-cloud entitlement management is challenging, given the rapid increase in the number and complexity of entitlements, and the inconsistencies among cloud provider approaches to their definition and configuration.”
Gartner, Innovation Insight: Cloud Infrastructure Entitlement Management, Henrique Teixeira, Abhyuday Data, and Michael Kelley, 11 May, 2023.
CIEM capabilities can help in alleviating these challenges. In the report, Gartner also lists some of the primary benefits of CIEM.
In general, these include:
- Multi-cloud visibility into least privilege violations – Presenting where there are policies that go against least privilege best practices, as well as aiding in reducing long-standing unused privileges in cloud infrastructure. This can also include showing access paths from a particular user/role to an asset, as well as access from the asset to all users/roles that have access.
- Automated risk management – Easing efforts to manage entitlements and identity misconfigurations across multiple clouds, in an automated and continuous way.
- Attack surface reduction – Minimizes potential risks related to access and excessive privileges, including account takeover and data breaches.
- Detection of identity anomalies and remediation – CIEMs calculate the baseline activity automatically and detect any anomalous occurrences that could indicate security incidents. They can also be configured to perform corrective steps automatically for entitlement policies.
- Supporting compliance efforts – By regularly assessing, monitoring, and securing entitlements in your cloud platforms, CIEMs can assist regulatory compliance, specifically requirements related to user access and policies.
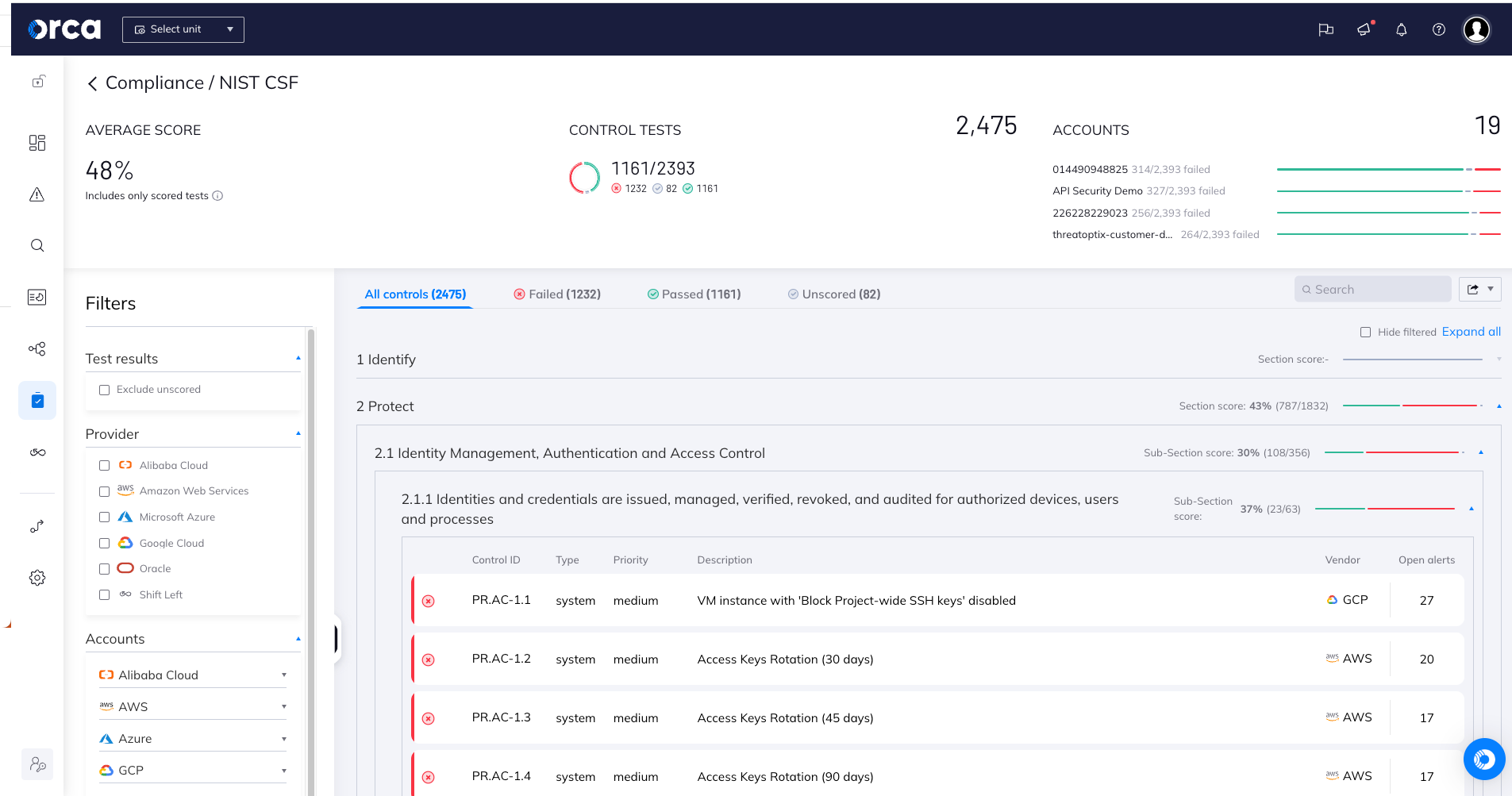
CIEM + the leading CNAPP platform = comprehensive cloud security
A key observation by the report’s analysts is that they are seeing a meeting point between standalone CIEM capabilities and more comprehensive cloud security platforms.
“Cloud infrastructure entitlement management (CIEM) capabilities are increasingly being embedded in cloud security posture management (CSPM) and converged cloud-native application protection platforms (CNAPP), given the similar graph- based approaches used for scanning for misconfigurations and anomalies. “
Gartner, Innovation Insight: Cloud Infrastructure Entitlement Management, Henrique Teixeira, Abhyuday Data, and Michael Kelley, 11 May, 2023.
We at Orca believe this to be a very positive development, for a number of reasons:
- Tool consolidation – Gartner observes that “[security and risk management] leaders are looking for more convergence and consolidation in their cybersecurity investments and are expected to achieve more with fewer resources.“ Including CIEM capabilities as a primary component of a CNAPP cloud security platform contributes to reducing the number of tools and vendors involved.
- Greater cloud context – Instead of siloed views into cloud identity and entitlements, CNAPPs provide full coverage and visibility into cloud estates and can detect security and compliance risks across the tech stack, including cloud configuration, workload, data, APIs, and identity.
- Better risk prioritization – By combining identity-related risks with vulnerabilities, context, and relationships, CNAPPs provide a holistic view of risks, recognizing how seemingly unrelated low severity risks can be combined to create dangerous attack vectors.
As the leading CNAPP platform in the cloud security market, Orca is committed to bringing to our customers comprehensive CIEM capabilities, including comprehensive visibility into cloud identities, policies, and entitlements, combined with the wider risk context of their cloud infrastructure, workloads, and data.
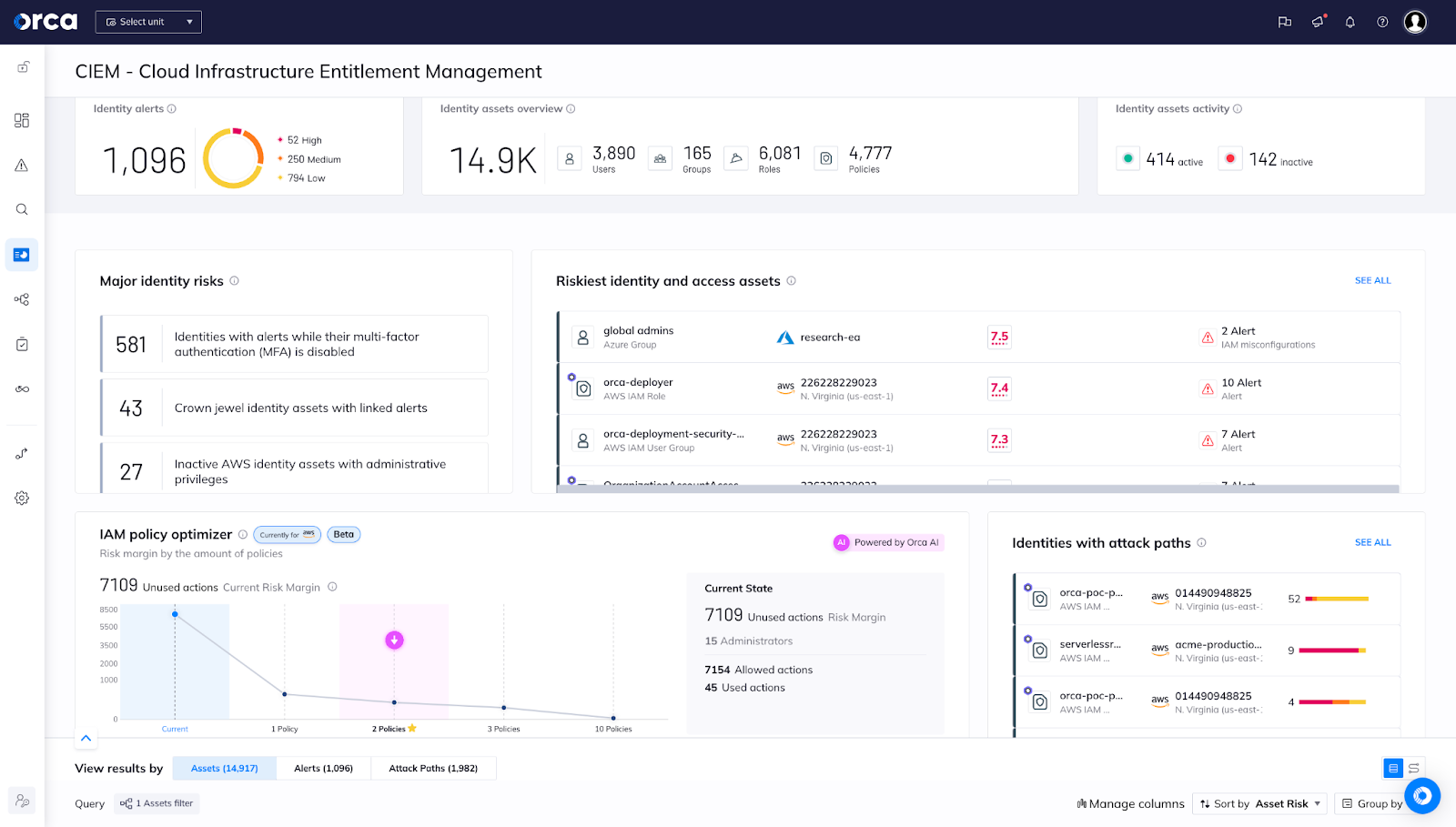
Orca’s CIEM Security View provides provides security teams with:
- Multi-cloud CIEM coverage in a single, unified platform, including information about users, groups, roles, and policies. Orca’s CIEM capabilities cover all Orca-supported cloud platforms, including accounts in Amazon Web Services (AWS), Microsoft Azure, Google Cloud, Alibaba Cloud, and Oracle Cloud Infrastructure.
- Identity and access posture management, with identity-related risks taking into account the wider cloud risk context. This includes showing how risks can be combined into attack paths (see more below).
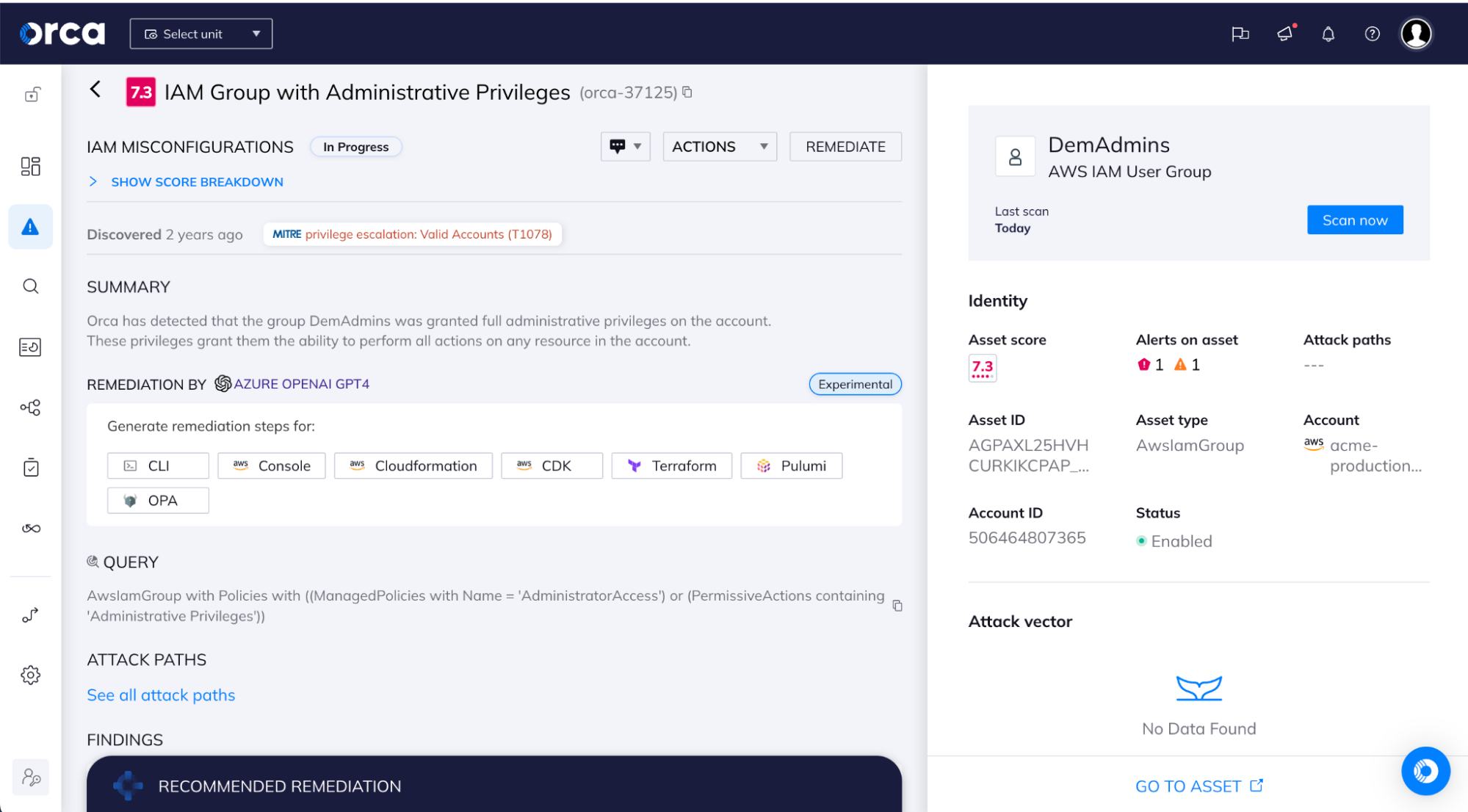
- Orca shows IAM assets associated with detected anomalies. Suspicious activities are displayed, allowing teams to quickly see which events are high severity and need immediate attention. This enables SOC and IR teams to accelerate triage and investigation into potential security events.
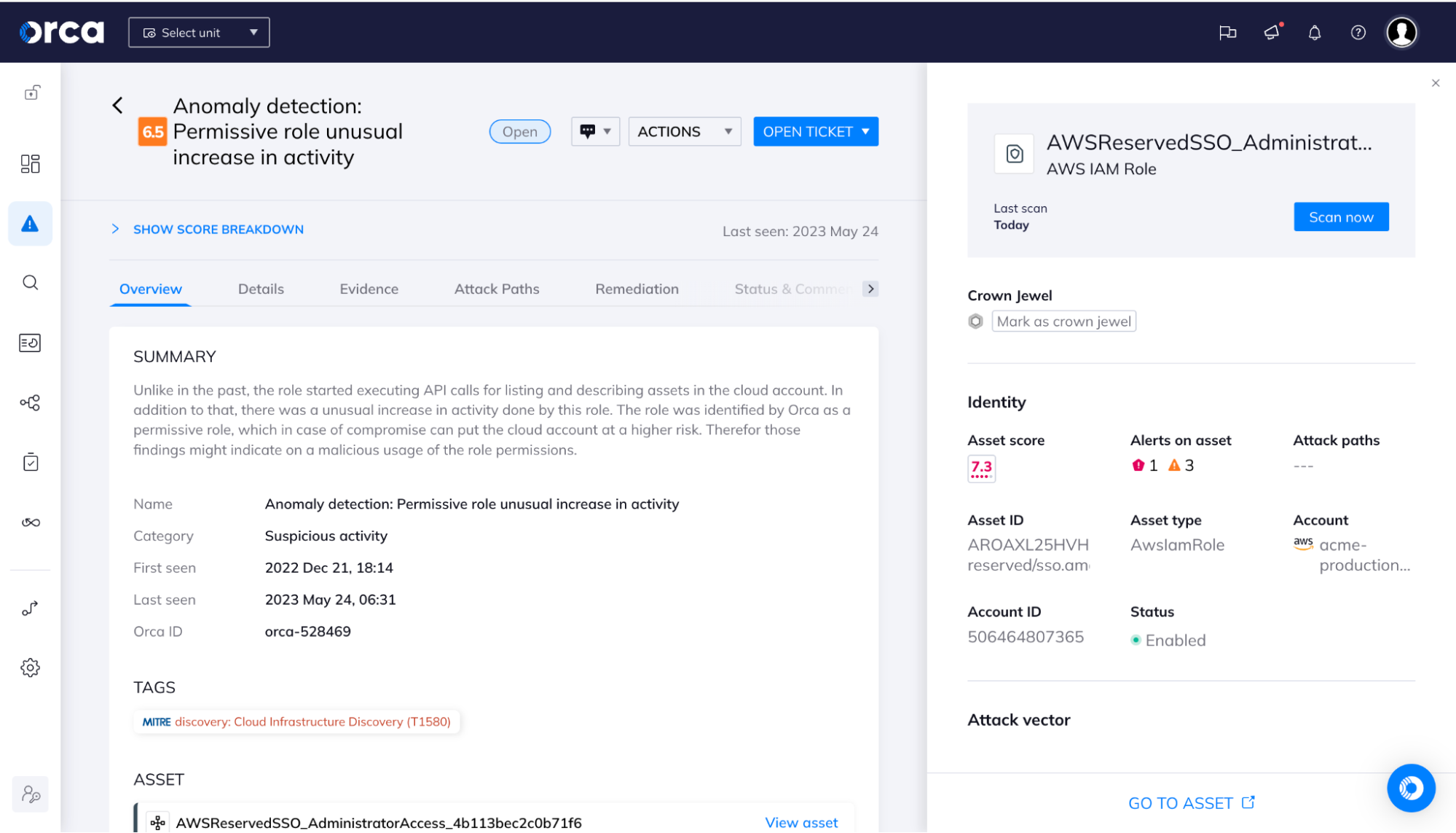
- Visibility into entitlements and access paths between users and roles and an asset using interactive graphs.
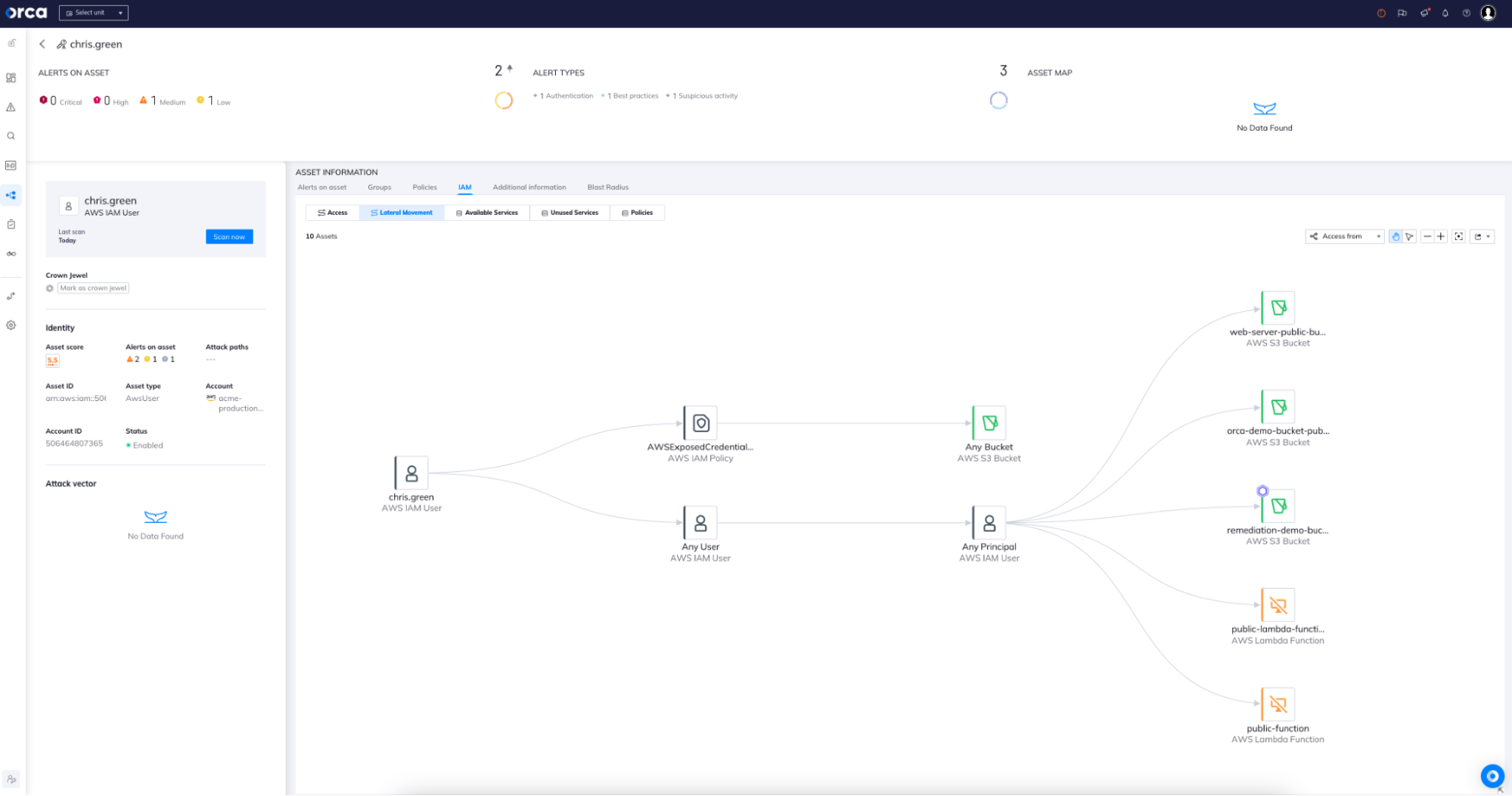
- A smooth user experience that delivers vital data to security teams in a clear and digestible manner, via a single page and unified flow.
Identifying risks not only for human identities, but also machines
The challenge of managing privileges and entitlements is not limited to the policies governing human users and roles. In its 2023 State of Cloud Permissions Risks Report, Microsoft estimates the percentage of dormant machine identities has doubled in the last two years from 40% to 80%. Gartner recommends:
“Reduce the risk of unmanaged machine identities by including workloads like containers, virtual machines (VMs), apps and services running as users within the scope of CIEM.”
Gartner, Innovation Insight: Cloud Infrastructure Entitlement Management, Henrique Teixeira, Abhyuday Data, and Michael Kelley, 11 May, 2023.
With Orca, customers have visibility into privileges of these workloads. To give just one example, Orca can detect Kubernetes misconfigurations in which the container image doesn’t have a user specified in it, resulting in the creation of containers that run as root. In Linux, “root” is the user that has access to everything on that host. So you definitely want to avoid that unless it’s necessary.
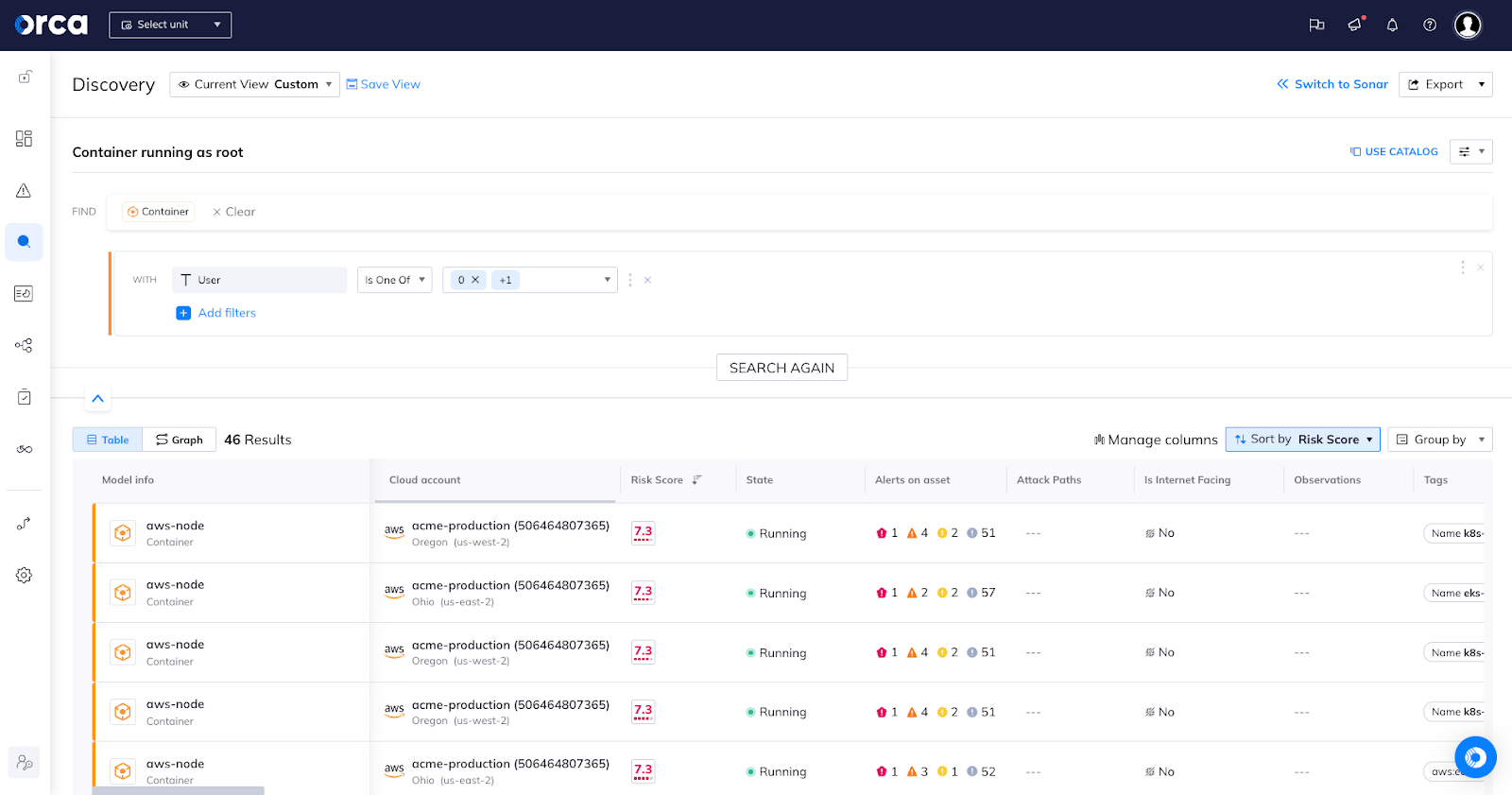
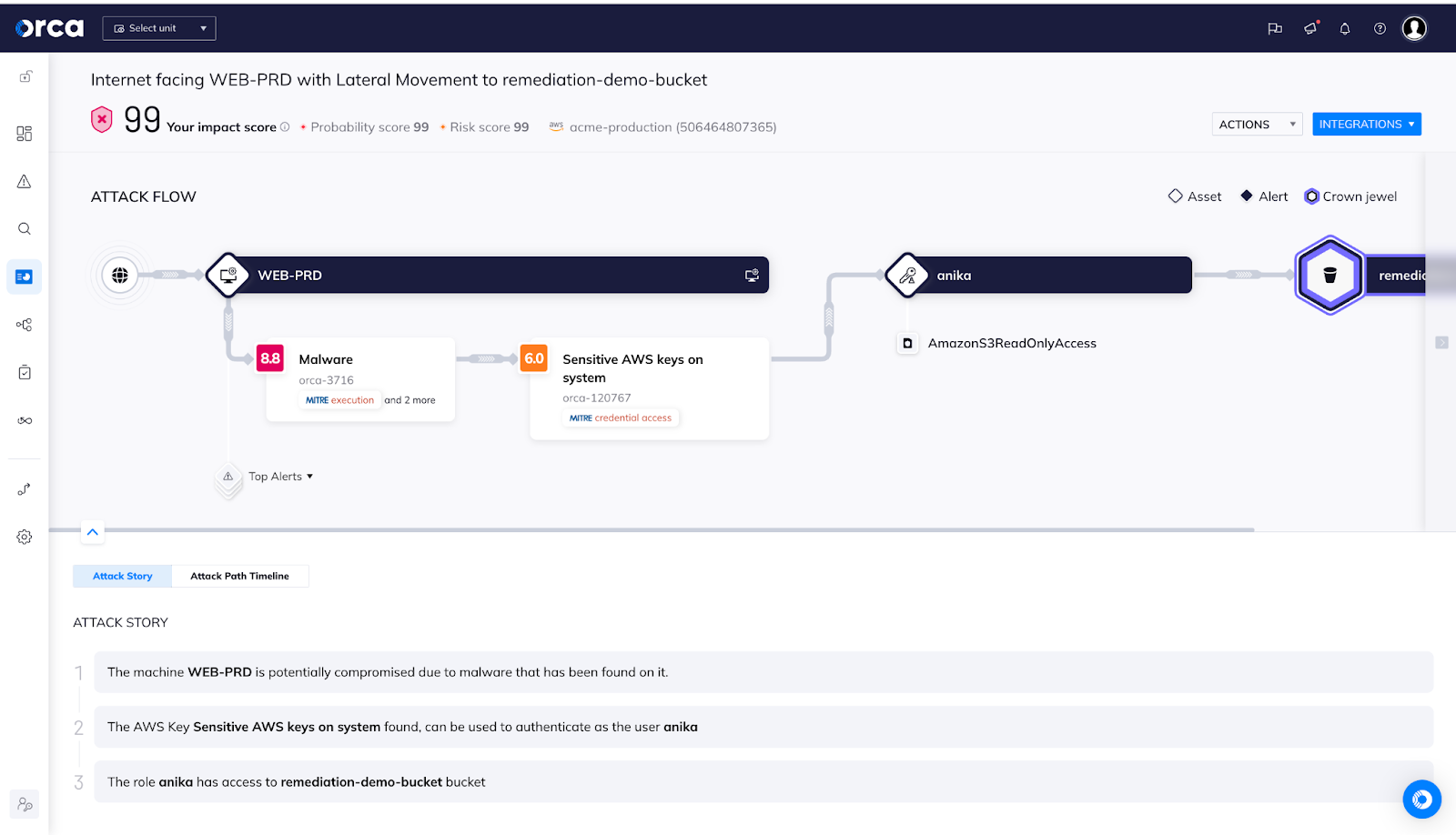
Showing how individual misconfigurations can be combined into dangerous attack paths
By unifying risk visibility across all cloud layers and across the entire development life cycle, a CNAPP like Orca can utilize attack path analysis and graph visualization to accurately pinpoint which risks endanger the organization’s most critical assets and are part of the most severe attack paths, so these can be remediated first.
In the example of the attack path below, the role “anika” has access to an AWS S3 bucket. When combined with other risks, in this case a malware-compromised VM, and sensitive AWS keys being found on that system, these separate, but interconnected risks form a dangerous attack path that can be exploited by an attacker.
Gartner, Innovation Insight: Cloud Infrastructure Entitlement Management, Henrique Teixeira, Abhyuday Data, and Michael Kelley, 11 May, 2023.
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.
Learn More
Although we hope you have enjoyed reading our take on the report, we do highly recommend that you read the entire Innovation Insight: Cloud Infrastructure Entitlement Management report. For more information on our CIEM capabilities, read our recent blog post. If you are interested in learning more, feel free to view our latest recorded demo of the Orca Platform.