“An apple a day keeps the doctor away”, the saying goes. Similarly, preventive cloud security measures are the most important way to maintain a healthy cloud security posture and avoid attacks from happening in the first place.
However, organizations should not stop there. It is also important to continuously monitor your cloud environments and be ready to respond if an attacker does manage to breach your defenses. Unfortunately it seems like attackers are still getting past defenses all too often. According to an IDC survey, in 2021 98% of companies experienced a cloud data breach in the last 18 months, up from 79% in 2020.
Why a new approach is needed for detecting cloud attacks
How can organizations detect and respond to attacks in progress? For on-premises infrastructure and endpoints there are many different types of solutions that can assist with this, including Threat Detection & Response (TDR), Endpoint Detection & Response (EDR), and Extended Detection & Response (XDR) tools. However, monitoring and responding to attacks in public cloud environments requires a whole new approach, which is why a new set of capabilities is emerging: Cloud Detection & Response (CDR).
In contrast to TDR, EDR, and XDR solutions that only examine workload risks, Cloud Detection & Response monitors workload risks as well as cloud-native configuration and identity risks. For example, if an attacker steals an over privileged role and performs actions outside its usual scope, such as creating new accounts or installing new software, this would be detected by a CDR solution. However, TDR, EDR, and XDR solutions would not pick up on this type of suspicious activity since they only focus on workload level threats such as malware and vulnerabilities.
In short, Cloud Detection & Response is a necessary tool for Security Operations Centers (SOC), Incident Response (IR) teams and security practitioners to closely monitor ongoing events, changes and behaviors in their public cloud environments. With CDR in place, teams will be alerted to any suspicious activity so they can quickly investigate and if necessary, intercept the attack.
Why current CDR solutions fall short
The problem with many existing CDR tools is that they are often TDR, EDR or XDR solutions that are being marketed as CDR solutions but don’t offer any actual cloud telemetry. In addition, existing CDR solutions are delivered as separate tools that focus only on the real-time aspect of events and attacks without any contextual insight into the existing cloud environment risks. Therefore these tools tend to have a high rate of false positives since they cannot accurately assess the danger of certain actions.
Orca’s new approach to Cloud Detection and Response
This is where Orca Security’s cloud-native Cloud Detection & Response capabilities are groundbreaking: Orca’s agentless platform consolidates intelligence from cloud feeds, workloads, configurations and identities in a unified data model to understand the full context of risks and which activities and events potentially endanger the organization’s most critical assets.
Why agentless CDR is a game-changer for the SOC
In addition to the clear benefits of an agentless solution, such as lower TCO, faster deployment times, less organizational friction and zero performance impact, there is another even more important advantage: 100% coverage. By deploying Orca, organizations are able to achieve complete coverage of all their cloud assets without blindspots. Since agent-based solutions require an agent to be installed on each asset that needs to be monitored, this often results in partial coverage; It is simply not feasible, and sometimes not technically possible, to install agents for every asset. According to Orca data, on average no more than 50% of assets get an agent installed, leaving you with serious security gaps. Needless to say, there really is no point in security if you don’t cover all assets.
Key capabilities of Orca CDR
Orca provides 24×7 monitoring of cloud provider logs and threat intelligence feeds, as well as risks found in cloud workloads and configurations, including malware, vulnerabilities, misconfigurations, identity and access management (IAM) risks, lateral movement risks, and sensitive data at risk. Orca performs continuous data analysis using a variety of techniques including Machine Learning and rules-based heuristics, to quickly and accurately alert on events and anomalies that indicate malicious activity.
With Orca’s CDR capabilities, organizations can detect, investigate, and respond to cloud attacks in progress:
- Detect: Receive alerts when changes and anomalies happen that indicate possible malicious intent versus normal behavior.
- Investigate: Research malicious activity with Orca’s detailed insights to quickly understand whether events indicate an attack and whether any of the organization’s critical assets are in danger.
- Respond: Ensure cloud attacks are intercepted before they can do any damage:
- Understand how to quickly break the attack in the fastest way.
- Follow remediation steps included with each alert.
- Automatically assign issues using Orca’s integrations with ticketing and notification systems such as Slack, PagerDuty, ServiceNow and Jira.
- Automate remediation through Orca’s integration and close partnership with SOAR solutions, such as Torq and Brinqa.
- Integrate with SIEM solutions (e.g. Splunk, Sumo Logic, IBM QRadar) for fast investigation and remediation.
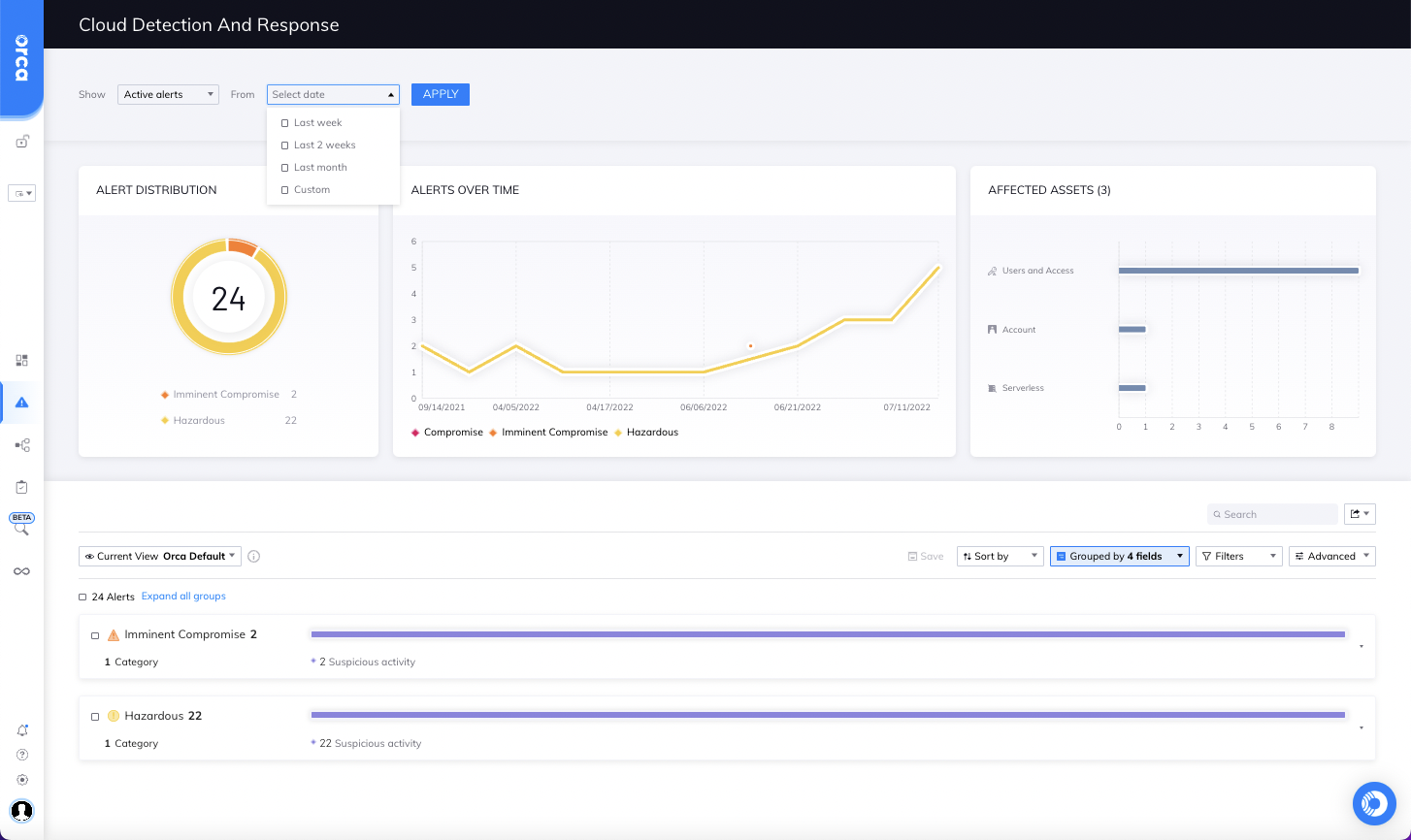
Orca Cloud Detection and Response Dashboard
Orca displays suspicious activities in the Cloud Detection and Response dashboard, and allows teams to filter alerts on risk level, alert ID, category and time discovered. Each CDR alert includes an ‘investigate’ option that displays the overview summary, details, evidence, mitigations, status and forensics for the alert.
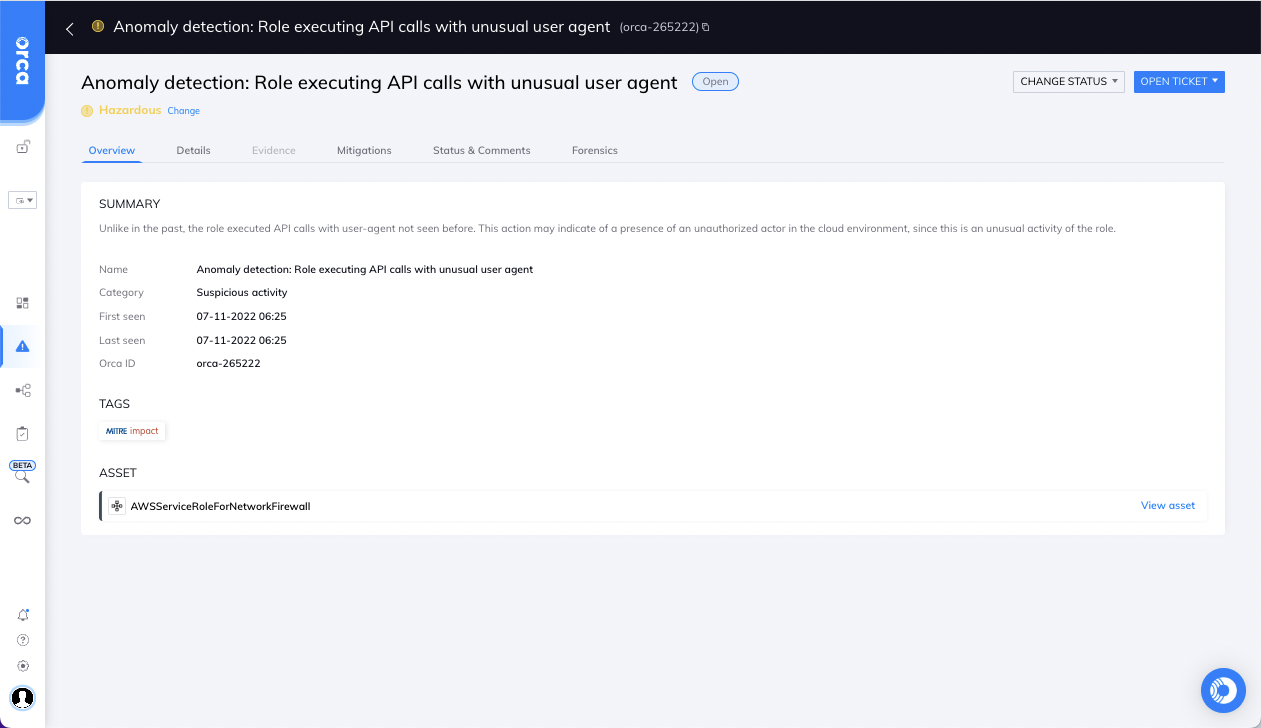
Users can fine tune CDR alerts by verifying or dismissing an alert, or changing the risk level of the alert.
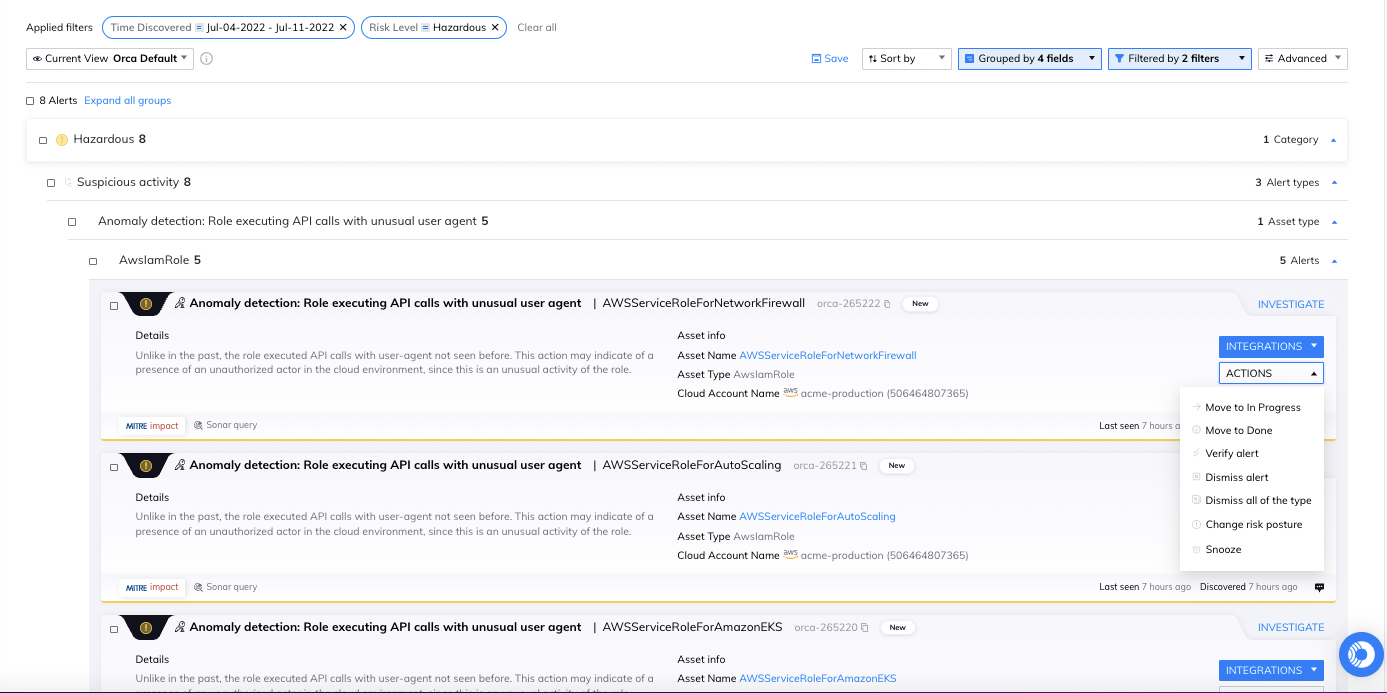
Examples of How Orca CDR Detects Cloud Attacks in Progress
In a separate blog, we describe four detailed examples of how Orca analyzes cloud events and behaviors and combines this with cloud telemetry, existing workload and control plane risks in the cloud environment, and company crown jewel awareness, to assess whether anomalies indicate malicious intent and how dangerous they could potentially be.
Learn more about Orca’s Cloud Detection & Response
Would you like to learn more about Orca’s CDR capabilities? Watch our recorded demo or attend Cloud Security LIVE on July 28th, Orca’s half-day virtual networking event, to learn more about CDR and other top cloud security issues from your peers, thought leaders, and industry luminaries from around the world.
Want to get more hands-on? Sign up for a Free Risk Assessment to see how quickly and easily the Orca Cloud Security Platform can help you identify and address risks.






