As organizations increasingly rely on cloud-hosted web and API endpoints to power their applications and services, incomplete visibility and associated security risks have emerged as a top concern for security teams. Potential risks include misconfigurations that might inadvertently expose APIs, thereby expanding the external attack surface and providing attackers with opportunities to exploit vulnerabilities or manipulate the API’s business logic.
Recognizing these risks, external exposure and API security is a core component of the Orca Cloud Security Platform, providing organizations with multi-cloud visibility of their cloud web addresses and APIs, as well as enabling them to identify, prioritize, and mitigate related security risks.
We are excited to announce a new integration with Cloudflare, a widely-used web and cloud platform, to expand Orca’s web and API security coverage even further. Orca automatically discovers an organization’s web and API catalog through its agentless SideScanning technology. The integration with Cloudflare further enhances Orca’s capabilities by enabling it to ingest Cloudflare’s DNS records, granting security teams the ability to access their organization’s Cloudflare-registered domains and subdomains, thereby enriching the context of the discovered web and API assets. Having wide visibility into Cloudflare web addresses, alongside the addresses and web and API endpoints from AWS, Azure, and Google Cloud, in a single platform, empowers teams to strengthen their defenses against web and API-related misconfigurations and other security risks across their multi-cloud environment.
Orca shows Cloudflare domains alongside those from other cloud providers
Why Integrate with Cloudflare DNS?
Cloudflare is a popular cloud-based solution that provides content delivery network (CDN) services, DDoS mitigation, web application firewall (WAF), and distributed domain name server (DNS) services. Cloudflare powers internet requests for millions of websites and serves 46 million HTTP requests per second on average. Cloudflare has a very rich ecosystem, and has many similar characteristics to the largest cloud service providers (AWS, Azure, GCP).
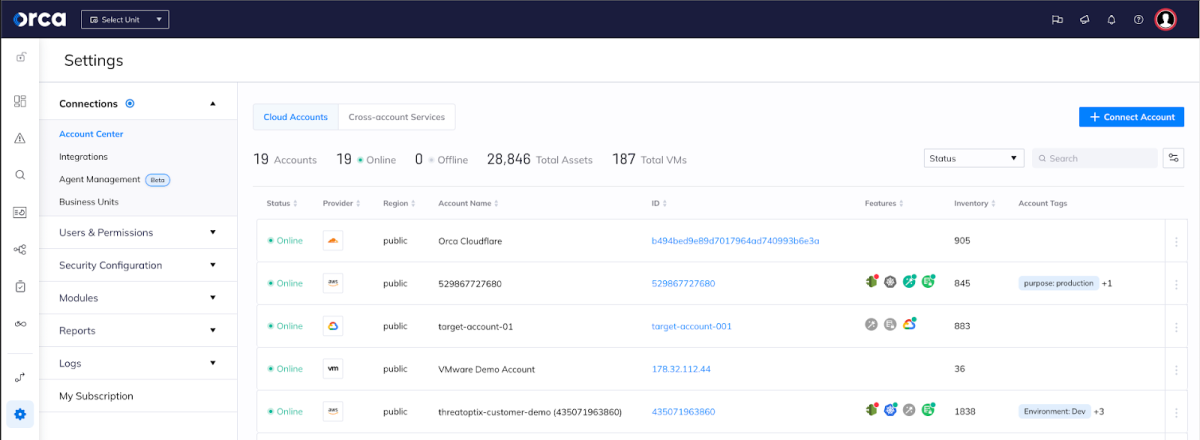
Orca Security allows for easy connection to Cloudflare accounts.
As a first step in our extensive plans for Cloudflare support, we have focused on Cloudflare’s DNS service. Leveraging Cloudflare’s REST APIs, Orca pulls the organizations’ DNS records configured in Cloudflare, making them accessible in the Orca platform, while also identifying security risks related to the Cloudflare domains and subdomains.
With the Cloudflare DNS integration, Orca’s customers can centralize their external exposure, web, and API security efforts. This streamlines security management by providing a unified platform for monitoring, identifying unintended exposure, and taking corrective actions across a broader spectrum of web and API endpoints.
Comprehensive Visibility of Cloudflare Domains and Subdomains
Once customers have connected their Cloudflare accounts in Orca, they benefit from a suite of web and API security capabilities designed to help organizations with continuous endpoint discovery and monitoring. As the Orca Platform is agentless, following a fast and one-time deployment, Orca scales with your cloud efforts, not against them. Each time a new Cloudflare domain or subdomain is added, it is automatically covered by the Orca Platform. This is especially critical for security teams as their organization’s cloud estate expands, helping with visibility, governance, and regulatory compliance.
Expanded Catalog of Web and API Endpoints
Orca provides organizations with an extensive view of their web and API attack surface. It continuously maintains an up-to-date inventory of all cloud assets, including API endpoints and web addresses, that security teams can use for monitoring, and provides valuable insights ensuring that no potential misconfigurations or other risks go unnoticed.
This visibility allows security teams to monitor and manage Cloudflare DNS configurations effectively. Cloudflare-registered domains and subdomains are now viewable within the Orca platform in several different ways.
Asset Inventory
Cloudflare domains and subdomains are viewable in Orca’s asset inventory, which shows all cloud infrastructure objects that are protected by Orca. Asset categories include virtual machines, containers, images, storage buckets, databases, IAM users and accounts, and other objects. This oversight is essential for effective cloud security. Remember Log4Shell, when organizations were scrambling to find out which of their cloud assets were vulnerable, and which ones had to be fixed first? This is why it’s so valuable for Orca’s agentless platform to provide a complete cloud asset inventory that continually covers 100% of the environment.
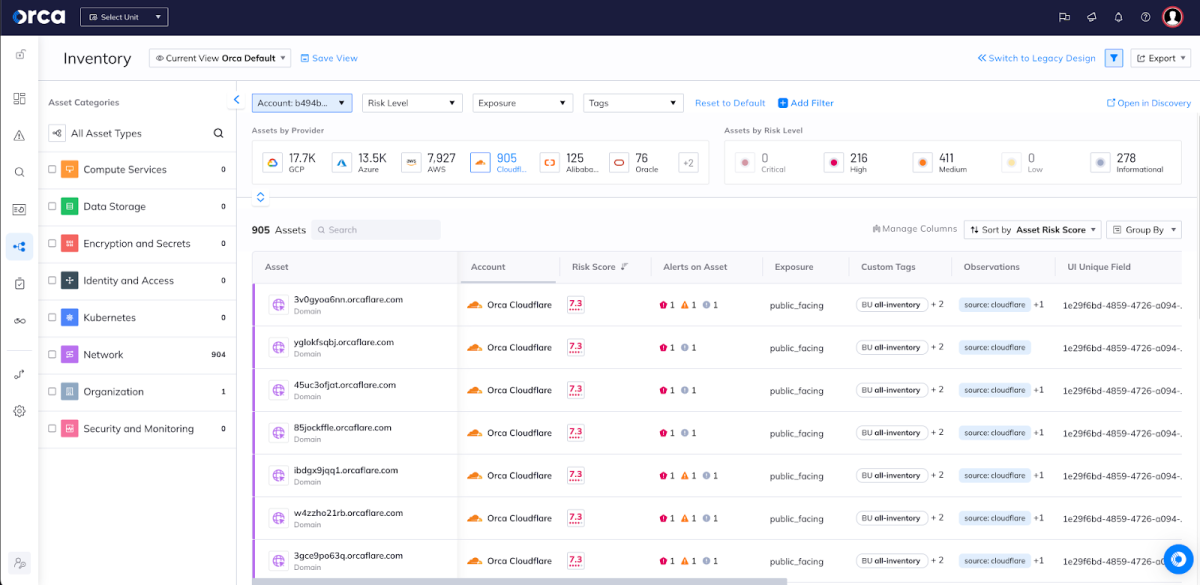
Cloudflare domains listed Orca’s Inventory dashboard.
Once an Orca user selects an asset, they’ll see more granular data. For example, as seen in the screenshot below, this subdomain asset page includes network information such as root domain, HTTP path, web endpoints, and more. You’ll also find a graph visualization showing the network connection from the domain to the web endpoint. The interactive graphs help users gain a complete picture of the relationships between cloud entities and risks that can often impact multiple entities.
All of this information gives security teams wide visibility into Cloudflare assets, their network connections, and their exposure level so they can easily monitor them, make necessary fixes, and strengthen their security posture.
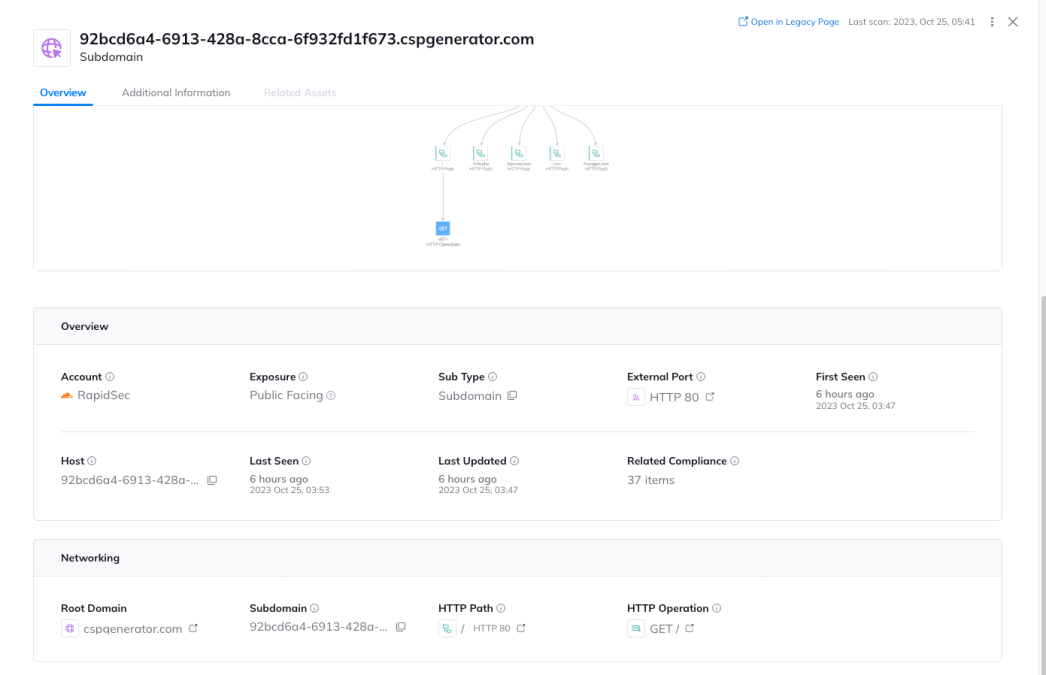
The asset view displays network information and a graph visualization showing the network connection from the root domain to web endpoint.
API Security View
API Security needs to start with full insight into which web addresses and APIs are running in the cloud environment. Orca’s ‘API Security View’ dashboard provides cloud and application security teams with an overview of all high-level API data and alerts.
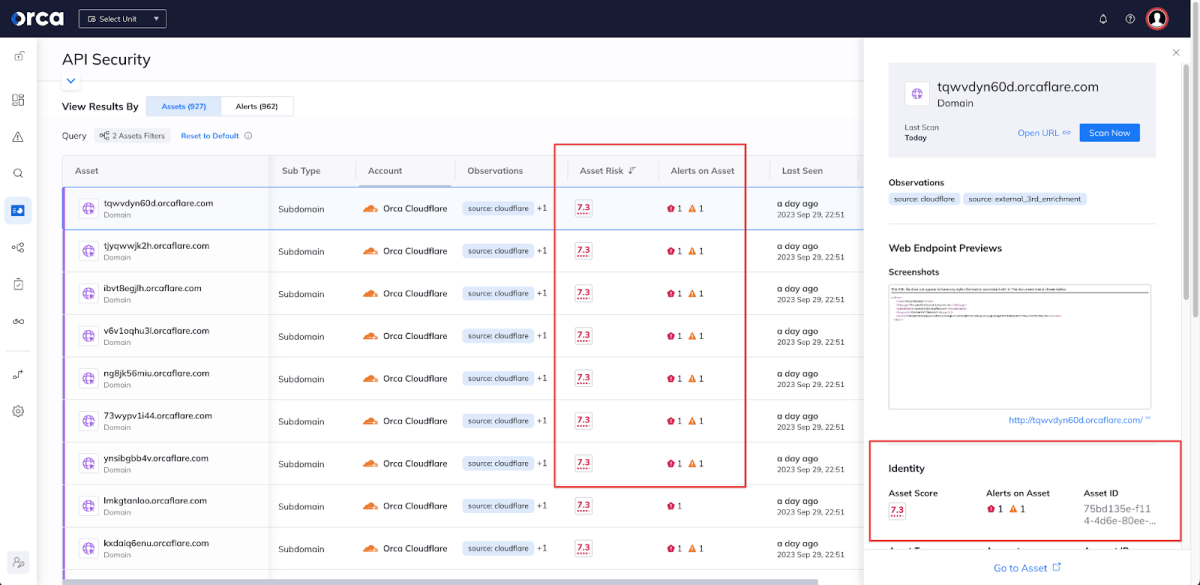
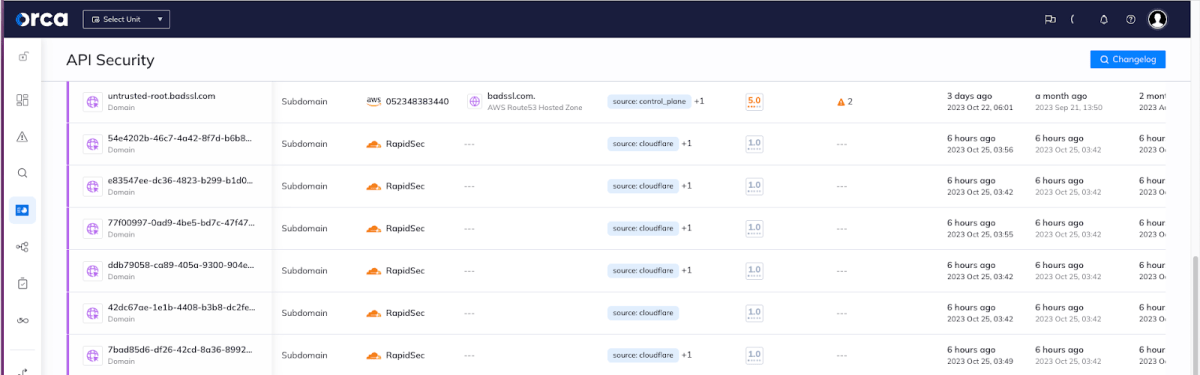
Orca shows Cloudflare subdomains in the API Security View.
Orca also lists web and API assets according to their ‘Asset Risk’ score, and shows the alerts corresponding to each asset. This gives security teams clarity of where to prioritize efforts to mitigate risks as strategically as possible.
Orca is able to surface a wide range of security risks related to web and API endpoints. For example, attackers may exploit a misconfigured domain and create a phishing site or host other malicious content on a subdomain, impacting anyone who visits the website. Below you can see an Orca alert to a subdomain takeover risk.

Orca alerting to a risk of a Cloudflare subdomain takeover.
Inside the API Security View you’ll also be able to access a changelog of all newly added and removed registered domains, subdomains, HTTP paths, and IP addresses— in the last specified number of days. The changelog also includes a search bar to easily search for a particular web or API entity. This functionality allows organizations to ensure that security remains robust even as the web and API landscape evolves.
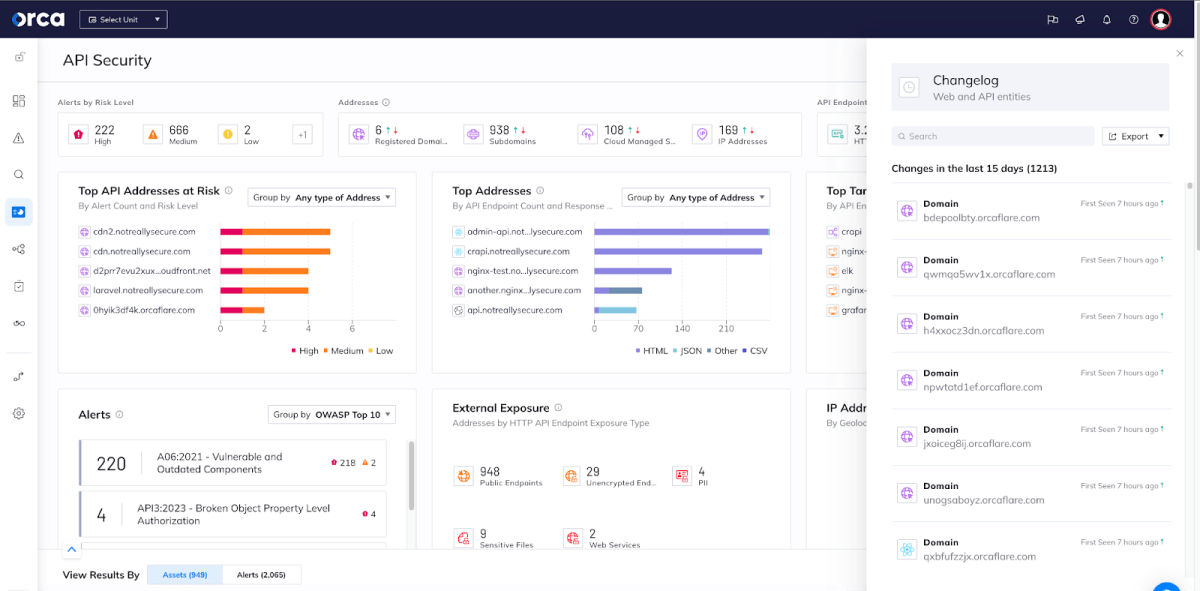
The Orca changelog shows newly added and removed web and API data.
Discovery Query Builder
Security teams can also find Cloudflare DNS data fully integrated in Orca’s Discovery query builder. This empowers security teams to quickly and efficiently query their cloud environments up to the deepest granular level, enabling them to make data-driven decisions based on this information.
Using Orca’s AI-powered query builder, you can create complex queries in a matter of seconds. Security teams can search for more high-level information such as a list of domains with connected HTTP paths (as seen in the screenshot below), or they can look for very granular information, such as searching for specific subdomains that were added within a particular date range. Using Discovery, in a couple of clicks, you can select assets, infrastructure, applications, and other objects and further filter them by means of an intelligent filtering component.
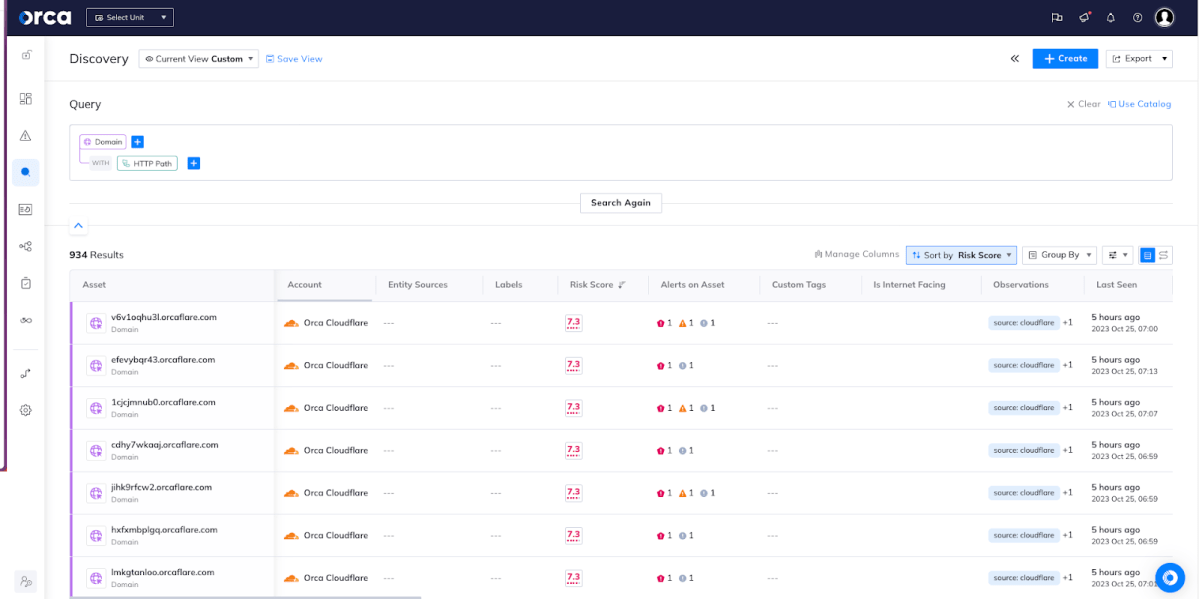
A list of domain addresses that include those discovered from Cloudflare accounts in the Discovery query builder.
Understanding the Relationship between Cloudflare Domains and Assets from Other Cloud Providers
Another valuable way security teams can use the Orca Discovery Query Builder to query the relationships between any cloud resources and see the corresponding results in graphs, as well as click on graph entries to further explore relationships. As a result, security teams can easily view and better understand the relationship between Cloudflare domains and assets within other cloud providers.
Whether you’re monitoring and securing virtual machines, databases, storage buckets, containers, their network connections, their exposure level, or other elements, knowing the relationship between any of these entities is of the greatest strategic importance.
As seen In the screenshots below, Orca is able to show in both graph and table views how an Amazon EC2 instance is linked to an IP address hosted in AWS, but that connects with many Cloudflare domains. Imagine if that EC2 instance has an identified vulnerability on it – being equipped with the knowledge to know how that vulnerability might impact other cloud resources (including Cloudflare domains in this case) is of tremendous importance. Orca empowers security teams with a multi-directional understanding of just how cloud risks in one asset or account can have a much wider impact.
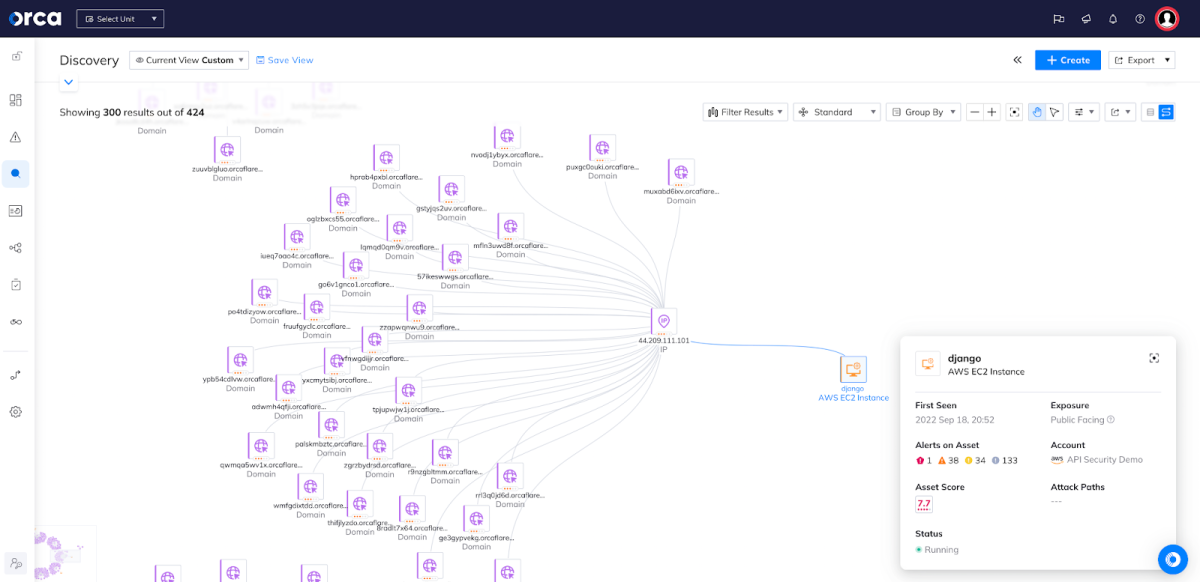
Orca’s graph shows the connection between the Amazon EC2 instance and Cloudflare domains.
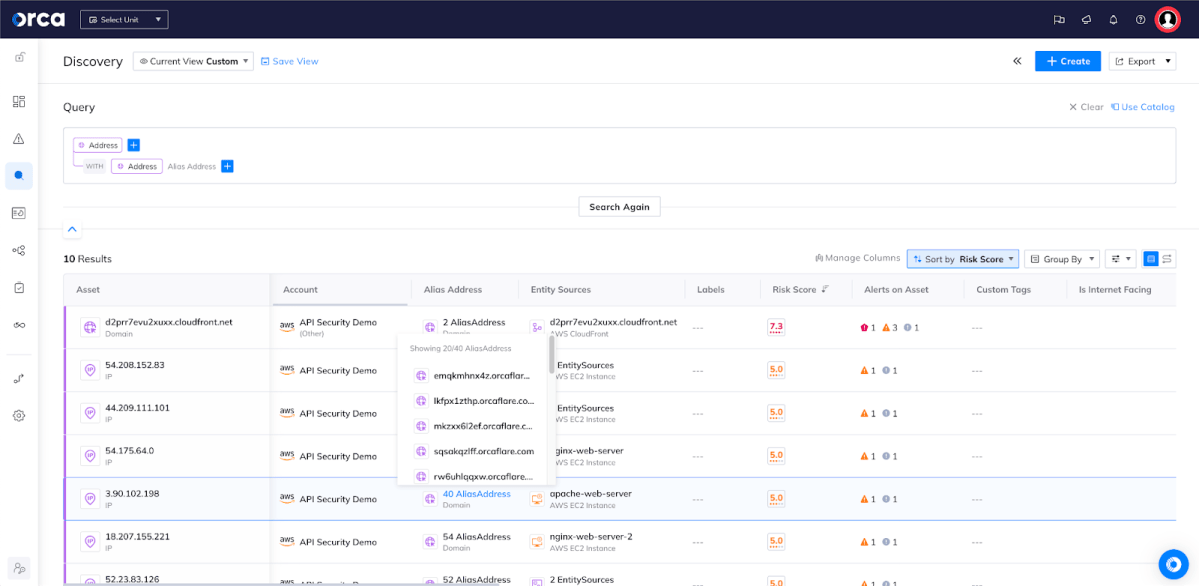
Orca’s table view shows the connection between the AWS hosted IP address and Cloudflare domains.
Learn More About API Security Capabilities Within the Orca Platform
Interested in learning more about Orca’s API Security capabilities? Watch this short explainer video, or view our on-demand webinar Securing APIs in Cloud Native Applications Best Practices.
Ready to try it out in your own cloud environment? Request a demo to see how quickly and easily the Orca Cloud Security Platform can help you identify and address web and API risks.






