Infrastructure-as-Code (IaC) templates are a code or git-based template for automating the provisioning of cloud resources and configurations. These templates are used by development and DevOps teams to more quickly and easily configure cloud resources and deploy applications more efficiently.
Popular IaC template formats include AWS CloudFormation, HashiCorp Terraform, and Kubernetes YAML files. Organizations typically host these in a central location, or pull them from common sources publicly, to give large numbers of developers access to these templates. With their wide-ranging use, security issues can easily occur, such as a storage bucket exposed to the Internet or an IAM role or user entitlement that runs as privilege or admin.
All of these security issues and misconfigurations can easily spiral out of control if an insecure template is shared across tens or hundreds of developers at an organization. Thus, scanning these templates and enforcing security best practices is critical.
Why Shifting Security Left Is Important
Shifting security left refers to the practice of addressing cloud infrastructure and cloud native application risks earlier in the development process – rather than merely addressing these risks at runtime.
Shifting security left provides incredible advantages:
- Code flaws and risks are remediated before cloud infrastructure is provisioned and applications are deployed into production
- The overall security posture of the runtime environment is improved, avoiding costly data breaches or rapid remediation
- Compliance is more easily achieved by implementing crucial compliance policies earlier in the software development lifecycle
Recently, Orca Security released our Shift Left Security dashboard, command-line interface Orca CLI, and initial support for container images and IaC templates. Below, I want to present a deeper dive on the Orca Cloud Security Platform’s support for IaC templates.
Managing IaC Policies Within the Shift Left Dashboard
With the Shift Left Dashboard, users can navigate to the Policies tab to view all of their policies covering both container images and IaC templates. Next, users can either create a new policy or manage the built-in policy that is provided as the Orca Platform default.
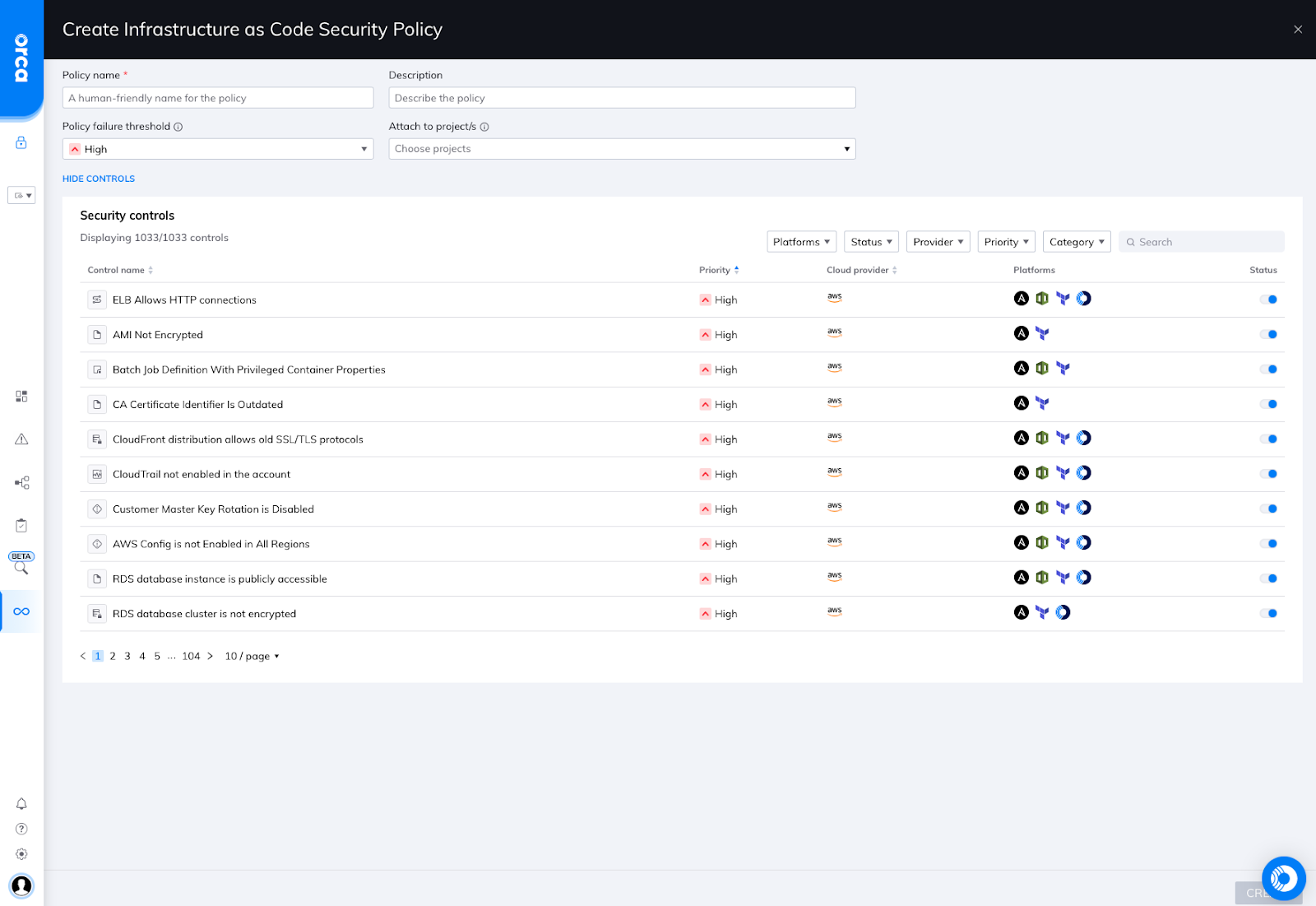
Orca Platform IaC policy UI
Expanding the IaC policy or creating a new policy allows users to easily view, enable, or customize over 1000 security controls governing their cloud infrastructure. These unified policies also map directly to the Orca Platform’s alert prioritization engine.
Scanning IaC Templates
Orca provides the ability to easily embed IaC scans in any SCM or CI workflow. Furthermore, by leveraging our command line interface, developers can also scan for issues locally to surface results before committing their code.
In the first example below, Orca provides the scan of a HashiCorp Terraform template within the terminal to show that master key rotation is disabled. Importantly, the description of the findings and results are clearly indicated.
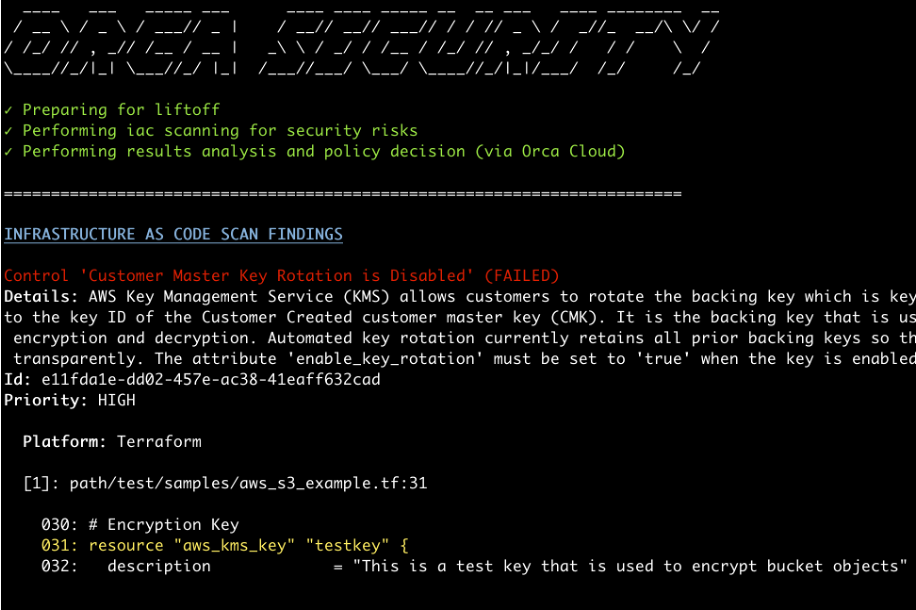
Orca CLI scan results for Terraform template
Additionally, Orca is able to provide the same results as part of CI tooling, as shown in the screenshot below. Here, we can see the scan results for the same Terraform template surfaced as part of a GitHub pull request.
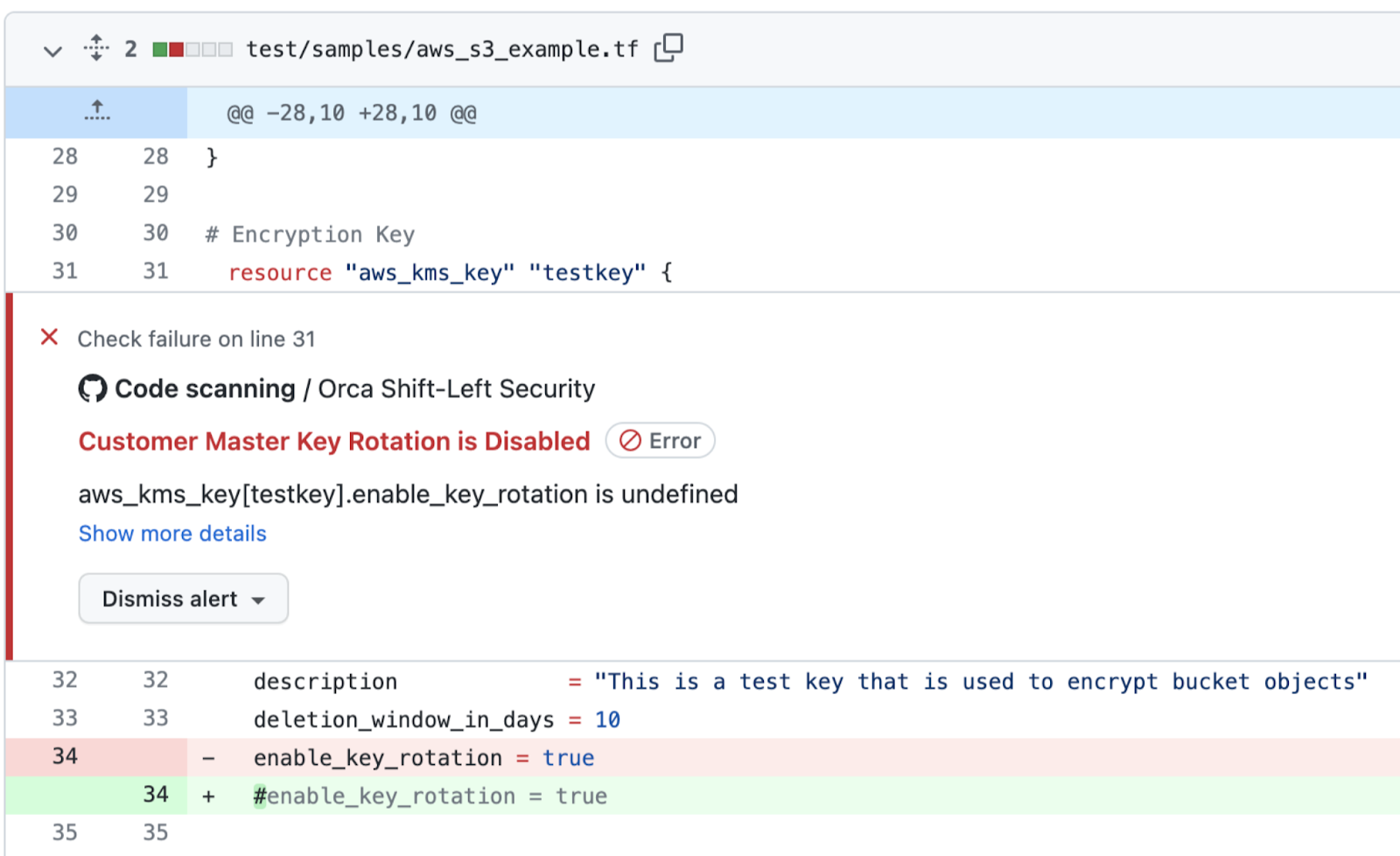
IaC scan results within a pull request
With these two examples, you can see how the Orca Platform integrates security controls for IaC templates, just like we do for container images.
Learn More About Orca’s Shift Left Security for IaC templates
To learn more about Shift Left Security as part of the Orca Platform, check out our official webpage or download our eBook 5 Requirements for Shifting Security Left Across the Application Lifecycle.
Orca’s cloud experts are ready to help you gain 100% cloud visibility in minutes with our complimentary cloud risk assessment and 30-day free trial. Sign up here today.






