Earlier this year, I had the pleasure of speaking with Caroline Wong from Cobalt and Jason Lane from Snyk on “Security is Job One” at Predict 2023. Caroline and Jason are both incredibly knowledgeable and, in the way of these sorts of panels, we ran out of time long before we ran out of things to say. There was one particular topic that we didn’t have a chance to discuss – the value of simplicity in solving security problems.
I had just read Adam Shostack’s “Fast, Cheap, Good: Lightweight Methods Are Undervalued” and, while Adam was talking about threat modeling specifically, his conclusions match my own experience in helping enterprises secure things. In this blog, we discuss the advantages of utilizing simplicity as a key strategy in addressing cloud security challenges for achieving comprehensive security coverage.
Example: Secure a Kubernetes Environment Step-by-Step
As an example, I’ve often talked to architects working on securing a new Kubernetes environment who were focused on complex solutions like service meshes before they’d solved for fundamentals like vulnerability and posture management. Modern service meshes are brilliant solutions for some risks but they also require a significant investment to realize their full potential. In my experience, too frequently, when security architects focus on the most complex solutions, they end up with incomplete coverage or, sometimes, delivering nothing at all (and delaying important projects).
If, instead, we focus on small, manageable projects that, combined, create defense in depth, we can pretty quickly make a measurable impact on the security of our cloud accounts, assets, and applications. For example, in our hypothetical Kubernetes environment, we probably want to focus on both the underlying infrastructure (the clusters we’ve deployed and the cloud services they use) and the applications we’re developing and deploying on top of that infrastructure.
For the infrastructure, the CIS compliance standard for the version of Kubernetes that I’m using is a perfect starting point to ensure that I’ve configured my cluster(s) with sane settings. If I haven’t, this will provide me with a roadmap, with the associated priority, for addressing the gaps in what is already deployed and running. If I’m using Infrastructure-as-Code to automate deploying these clusters, I can also scan the templates for them before they’re deployed to identify problematic configurations quickly.
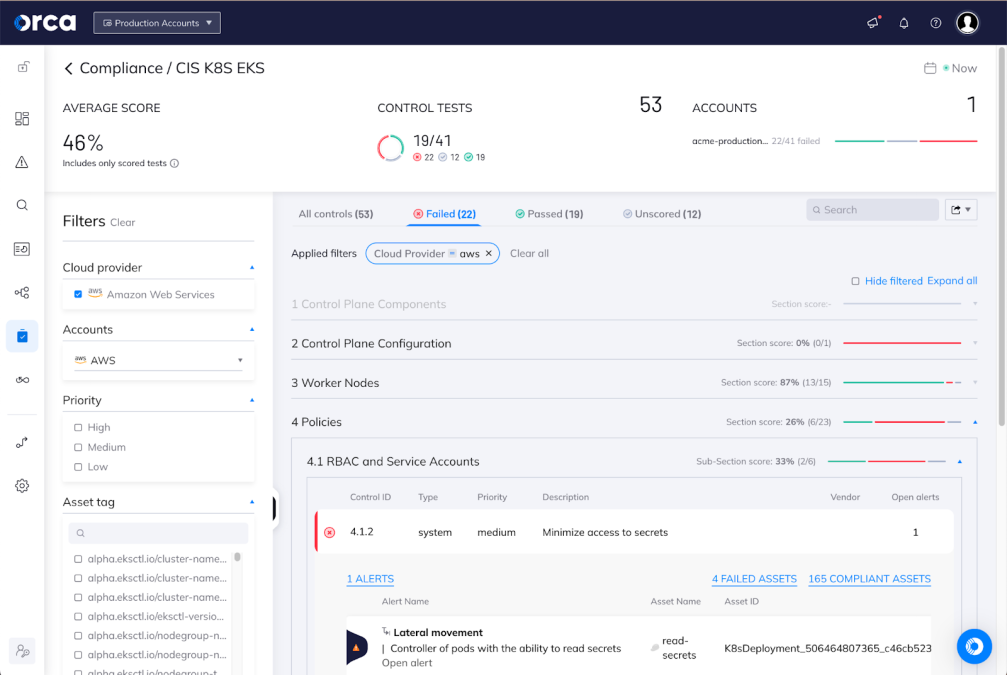
CIS Amazon EKS compliance results showing where we can address config issues
For my applications, I can, once again, start with simple steps to address common issues and build my security program from there. The first steps may include scanning for and managing vulnerabilities across the lifecycle of the application and finding and addressing where container images and deployments violate security best practices like running as root/running with privilege. We may also want to ensure that we’re looking for vulnerabilities and poor practice across the lifecycle of the container, starting at or before build time and continuing through to production.
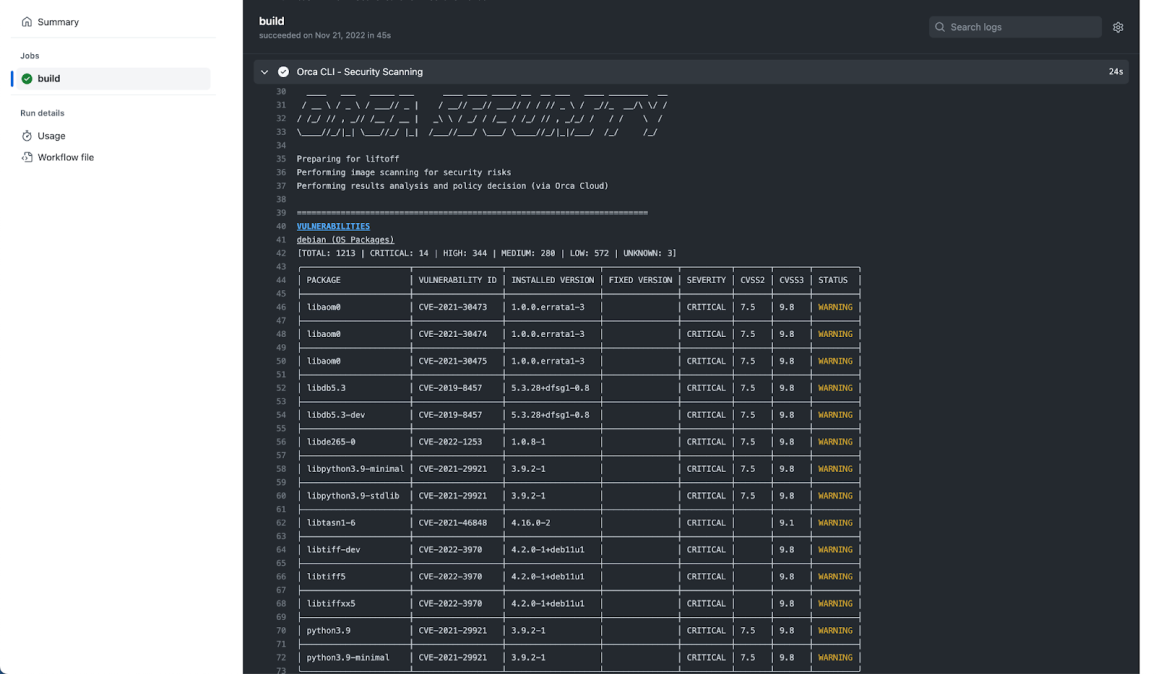
Scanning a container image in CI/CD
Simplify Cloud Security to Achieve Comprehensive Coverage
Of course, there is no one-size-fits-all approach but I’m glad to have had an opportunity to talk about simplicity as a potential virtue in solving security challenges. There’s a lot of other great discussion in the “Security Is Job One” panel and I would encourage you to spend some time with the recording to get a deeper understanding of the latest philosophies on critical cloud security requirements and how teams can tackle them.
Further Reading:






