Table of contents
As the market for cloud computing grows, so does the need for enhanced cloud security measures. That may explain why Gartner forecasts that investments in cloud security will surpass all other segments in the global security and risk management market. It also illustrates the importance of Azure security, the area of cloud security specific to Microsoft Azure, the world’s second most popular cloud service provider (CSP).
Azure security encompasses a comprehensive set of tools and practices designed to protect cloud environments, applications, data, and other resources from threats. As changes to cloud services continue at an accelerated rate, and attacks become more sophisticated, organizations need enhanced capabilities and measures for Azure security.
In this article, we discuss Azure security’s core components, best practices, and how you can leverage its features to protect your cloud estate.
What is Azure security?
Azure security is a comprehensive solution designed to protect cloud resources within the Microsoft Azure platform. It combines various services, tools, and best practices to maximize the integrity, confidentiality, and availability of your cloud. Azure security includes both native security features offered by Microsoft Azure, as well as third-party solutions compatible with the cloud platform.
Native features of Azure security include:
- Identity and Access Management (IAM): Ensures that only authorized users can access your data and resources.
- Network Security: Protects your network from threats, misuse, or unauthorized access.
- Data Encryption: Helps maintain the privacy and security of data in the event of a system compromise.
- Threat Protection: Actively monitors and defends against in-progress attacks.
Microsoft Azure continuously updates its native security features to address emerging threats. But Azure security doesn’t just involve the CSP. It operates according to the Shared Responsibility Model, where your organization and Microsoft play crucial roles in protecting Azure’s public cloud environment. This collaborative approach covers all security considerations—from infrastructure to applications and data.
By leveraging Azure security best practices, you can meet your requirements under the Shared Responsibility Model, build a robust defense against cyber threats, and ensure your organization can operate in the cloud securely and confidently.
Why is Azure security important?
Several factors make Azure security a key priority for your organization. They include the following.
Shared Responsibility Model
When using Microsoft Azure, it’s crucial to understand the Shared Responsibility Model. This model assigns key security responsibilities to CSPs and their customers, including your organization. While CSPs are generally responsible for securing cloud infrastructure, your organization owns the task of protecting your data, identities, and applications.
Risk mitigation and prevention
Azure security helps you prevent successful cyber attacks and compromises. By following best practices, you can identify and remediate risks before attackers can exploit them. And by introducing security measures early in the software development lifecycle (SDLC), you can also prevent security risks from entering your production environment.
Azure security features offer a comprehensive toolkit to identify vulnerabilities, detect unusual activities, and respond swiftly to potential breaches. This proactive approach can save you from costly data leaks and reputation damage.
Business continuity
Security incidents such as data breaches can significantly disrupt the continuity of your business—due to system downtime, customer churn, reputational damage, and more. Azure security provides insurance from the consequences that accompany a data breach or other severe security incident. In this way, it helps you optimize the ROI of your cloud investment by balancing risk and reward.
Components of Azure security
When it comes to safeguarding your cloud environment, Microsoft Azure offers a powerful suite of security features designed to keep your infrastructure secure and resilient against threats. These capabilities work cohesively across operations, applications, storage, networking, compute, and identity management. Let’s dive into the key components that make up Azure’s robust security framework.
Operations
Azure security offers a variety of features to support security operations. These include solutions for risk detection, monitoring, and remediation; policy management; resource management; application performance management (APM); cloud detection and response (CDR); and more.
Applications
Azure security places a strong emphasis on application security, providing essential tools that enable the secure development and hosting of web applications. This includes a Web Application Firewall (WAF) that protects against common application threats like SQL injection and cross-site scripting. It also includes controls for application authentication and authorization.
Storage
Azure security offers a number of features that support secure storage. This includes role-based access controls (RBAC), which enable you to support and enforce the principle of least privilege (PoLP) across your Azure resources and environment(s). It also includes features for data encryption at rest and in transit, which together help you secure data across its lifecycle, prevent security incidents, and meet your compliance requirements.
Networking
In addition to the previous features, Azure security offers important capabilities for network security. This includes controls for network access and segmentation, firewalls for protecting your cloud workloads, features for managing and monitoring your virtual network (VNet), and more.
Compute
In terms of your compute, Azure security offers a number of features and capabilities. This includes antimalware and antivirus services, features for the secure management and encryption of access keys, solutions for backup and recovery, encryption for virtual machine (VM) disks, capabilities for patch management, and more.
Identity management
Identity management is a fundamental aspect of Azure security, which offers a number of features to support it. This includes capabilities that help secure your identities, including multi-factor authentication (MFA), authenticators, password policy enforcement, RBAC controls, and more. Additionally, Azure security offers features that help you manage users and groups while securing access to data and applications. This comprehensive approach to identity security not only helps prevent unauthorized access but also simplifies identity management.
Common Azure security risks
Here are some of the most common security risks associated with Microsoft Azure:
Misconfigurations
According to the 2024 Cloud Security Strategies Report, most executives (57%) rank misconfigurations as their top cloud security risk. Misconfigurations come from the improper setup of security settings offered by your CSP. Common examples include overly permissive roles or identities, unencrypted data, exposed secrets, default credentials, and more. A misconfigured security group could inadvertently allow unauthorized access to sensitive resources, while an open storage bucket might expose critical data to external threats. Addressing these oversights is essential to maintaining a secure environment.
Vulnerabilities
Azure, like any system, is susceptible to vulnerabilities, which can arise from unpatched software, outdated systems, open-source components, and more. Failing to address these vulnerabilities can pose significant risks to your cloud resources. For example, if an Azure virtual machine is running outdated operating system software that has known security flaws, it could become an easy target for attackers looking to exploit those weaknesses. Regularly updating and patching your systems is crucial for safeguarding your Azure environment.
Sensitive data exposure
Data security and privacy are essential requirements of cloud computing. Failing to protect sensitive data can lead to severe consequences, including costly security incidents, as well as financial, reputational, legal, and regulatory consequences. Improper data handling, insufficient encryption, permissive access controls, and other issues can put sensitive data at risk. This illustrates the need for advanced data security measures.
Permissive identities
Permissive identities represent a prevalent and key security risk, granting excessive permissions to users, roles, services, or resources. This gives identities more access and rights than necessary, opening the door for unauthorized access and other security incidents. Implementing and enforcing the PoLP helps mitigate this risk by ensuring users have only the access needed to perform their roles.
Internet-exposed resources
Internet-exposed resources can significantly increase your attack surface. While some Azure resources must be publicly accessible, unnecessarily exposing others can lead to vulnerabilities. Carefully evaluating which resources need public access and securing those that do not is crucial for maintaining a strong security posture.
Challenges of Azure security
Here are some challenges you are likely to encounter in Azure security:
- Limitations of native security features such as multi-cloud compatibility: Azure offers a number of native security features and services that can help fortify your cloud security. Yet these capabilities work exclusively for Azure and not other popular environments such as AWS, Google Cloud, Oracle Cloud, or Alibaba Cloud. As a result, organizations using multi-cloud environments from more than one CSP must rely on additional security tools. This can lead to gaps in coverage, compatibility issues, and higher costs.
- Lack of visibility: Without comprehensive monitoring tools, organizations may struggle to detect potential threats, operating in the dark and missing critical alerts or anomalies. This lack of visibility leaves systems vulnerable to critical risks and attacks.
- Siloed risk analysis: Many tools used for Azure security provide limited risk analysis that doesn’t account for the relationship between risks and the broader cloud environment. To determine the severity of a vulnerability, for example, they analyze only the risk itself, not whether it would enable attackers to laterally move, elevate privileges, or endanger a high-value asset. This limitation often comes from a lack of coverage across the cloud environment, as well as the inability to detect different types of cloud risks, such as vulnerabilities, misconfigurations, sensitive data exposure, malware, API risks, and more.
- Alert fatigue: Along with the previous challenge, many Azure security tools also contribute to alert fatigue by failing to effectively prioritize alerts. This often occurs as a result of the insufficient or limited risk analysis we examined previously. It can also result from the lack of a unified platform that can provide a single pane of glass for cloud security intelligence and capabilities.
- Compliance: Compliance remains a necessary aspect of business continuity. Yet it also presents significant challenges in the cloud—due to its dynamic, distributed, and self-service nature. This illustrates the need for full and continuous cloud coverage, comprehensive risk detection, and effective prioritization—all of which make cloud compliance possible.
Best practices for Azure security
To fortify your Azure security posture, consider the following best practices that can help you safeguard your cloud environment.
Understand the Shared Responsibility Model
Establishing a clear understanding of the Shared Responsibility Model in Azure is the foundation for a robust security strategy. As a CSP, Microsoft Azure must secure the underlying cloud infrastructure, such as the physical data centers, network, and virtualization layers. However, as a CSP customer, you need to protect your data, identities, and applications, as well as properly configure the cloud services you use.
Your specific responsibilities under this model depend on the chosen form of cloud service delivery (i.e., Infrastructure-as-a-Service, Platform-as-a-Service, or serverless). Best practice is to fully understand your obligations so you can effectively support and fulfill them. When this happens, you create the conditions for achieving your security, compliance, and business objectives.
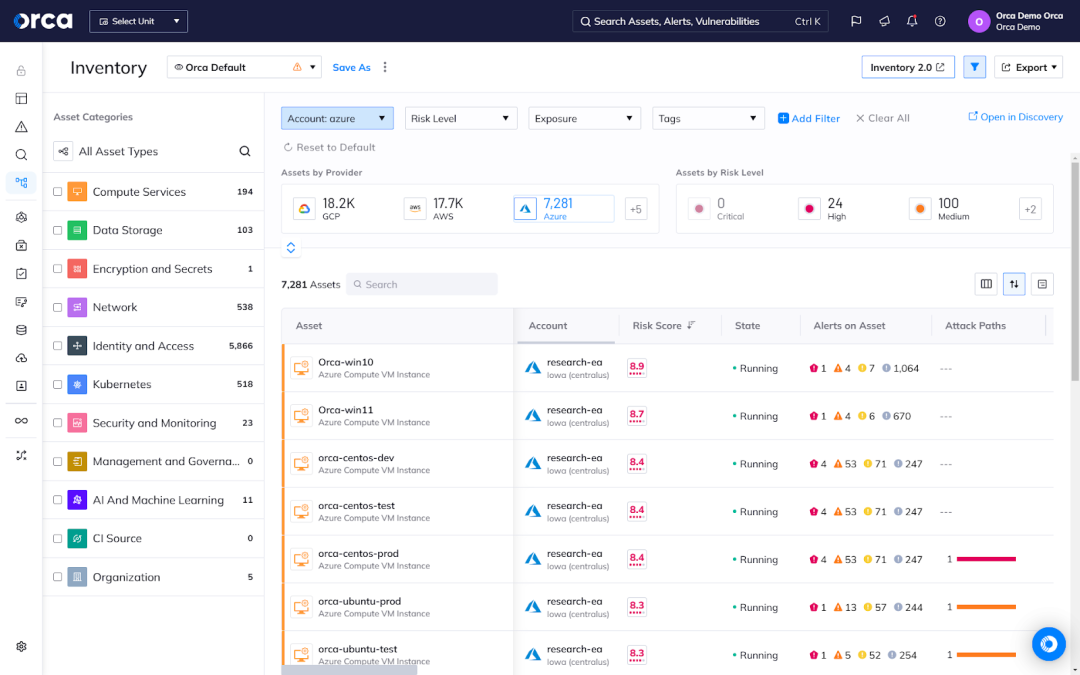
Get a complete inventory of cloud resources and risks
Effective cloud security starts with getting a full inventory of your cloud resources and risks. Acquiring and sustaining this inventory calls for a solution that combines full coverage with comprehensive risk detection. The former means you can identify cloud resources and risks across your cloud estate, including multi-cloud environments involving more than one CSP. The latter means you can detect all types of cloud risks, not just a limited set, and analyze them in relation to one another.
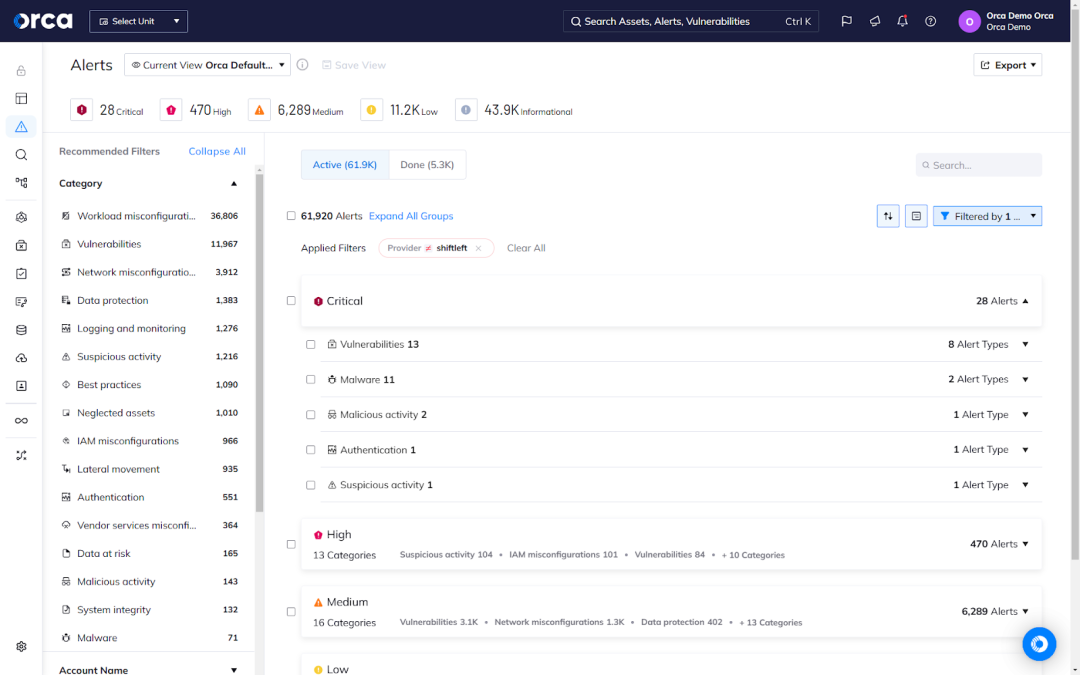
Prioritize risks according to business impact
Research shows that security teams can only address a fraction of the vulnerabilities they detect each month. This illustrates the importance of risk prioritization—intentionally focusing your resources to address the most critical risks in your environment. Security teams often make the mistake of attempting to remediate every risk or vulnerability present in their cloud, which may allow the most time-sensitive risks to go unattended.
Best practice is to acquire a solution that effectively prioritizes risks in your environment across all types. You should also fully configure this technology to take advantage of features that automate and accelerate workflows. By aligning your security efforts with the reality of your organization’s attack surface, you can make more informed decisions and achieve a higher return on your security investments.
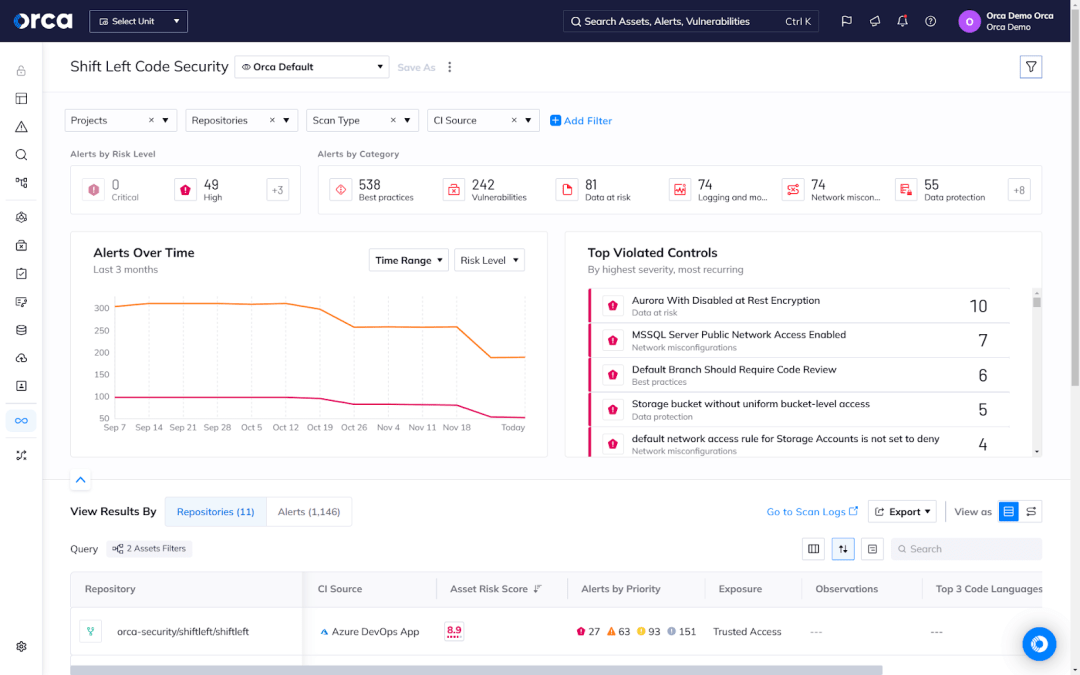
Embrace a DevSecOps framework
Adopting a DevSecOps framework is a proactive way to embed security into every phase of the application lifecycle–spanning the earliest phases of the software development lifecycle (SDLC) to runtime. This approach helps you catch vulnerabilities and misconfigurations when they are easiest and least costly to fix, prevent certain risks from resurfacing in a production environment, and more. By automating security checks and integrating them throughout the SDLC, you can ensure consistency and efficiency, ultimately strengthening the application security from code to cloud.
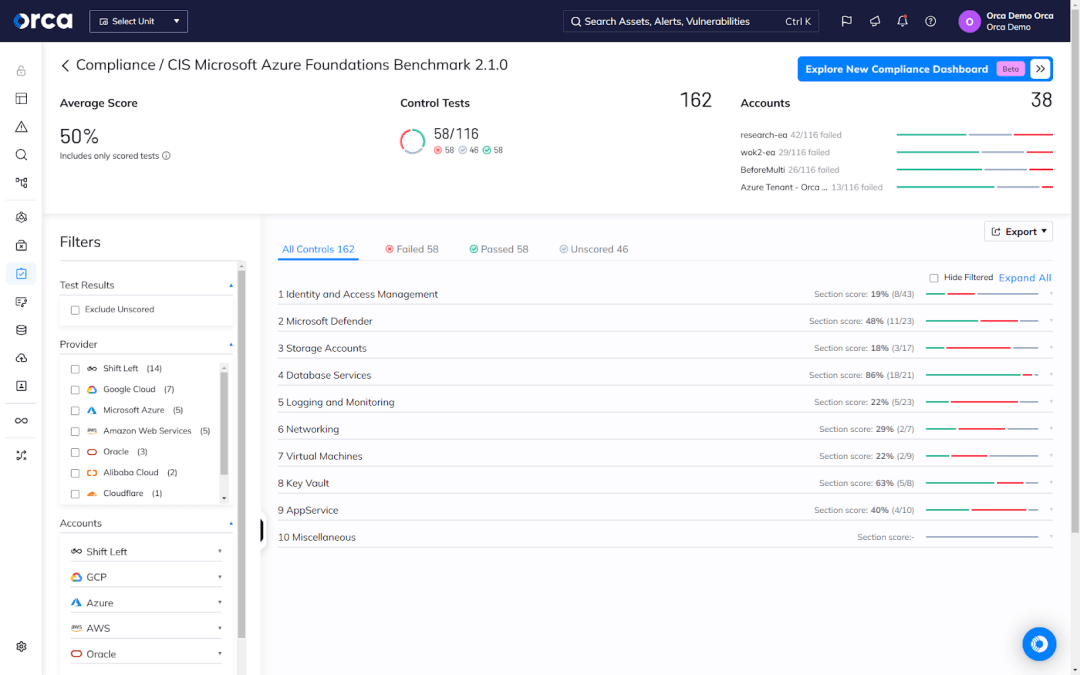
Automate compliance
While a business priority, compliance in the cloud can demand significant time and resources needed elsewhere. That explains the importance of using technology to automate as much of the compliance process as possible. It also calls for acquiring capabilities that integrate across your security stack, offer full visibility, and facilitate seamless collaboration across different functional teams.
Best practice is to choose cloud security solutions that offer automated features for compliance, built-in compliance frameworks, extensive integrations, flexible capabilities for reporting, and more.
Adopt a Cloud-Native Application Protection Platform (CNAPP)
As mentioned previously, Azure security demands the ability to effectively prioritize risks. This calls for both full and continuous coverage and comprehensive risk detection—capabilities that Cloud-Native Application Protection Platforms (CNAPPs) provide. CNAPPs unify multiple cloud security capabilities in one platform and offer protection across the full application lifecycle (i.e., code to cloud, cloud to code). That may explain why Gartner predicts that most organizations will need to adopt a unified CNAPP by 2029 to meet their zero-trust goals.
Best practice is to deploy a unified CNAPP for your Azure security needs, rather than relying exclusively on native security features, using multiple point solutions, or leveraging a poorly integrated platform.
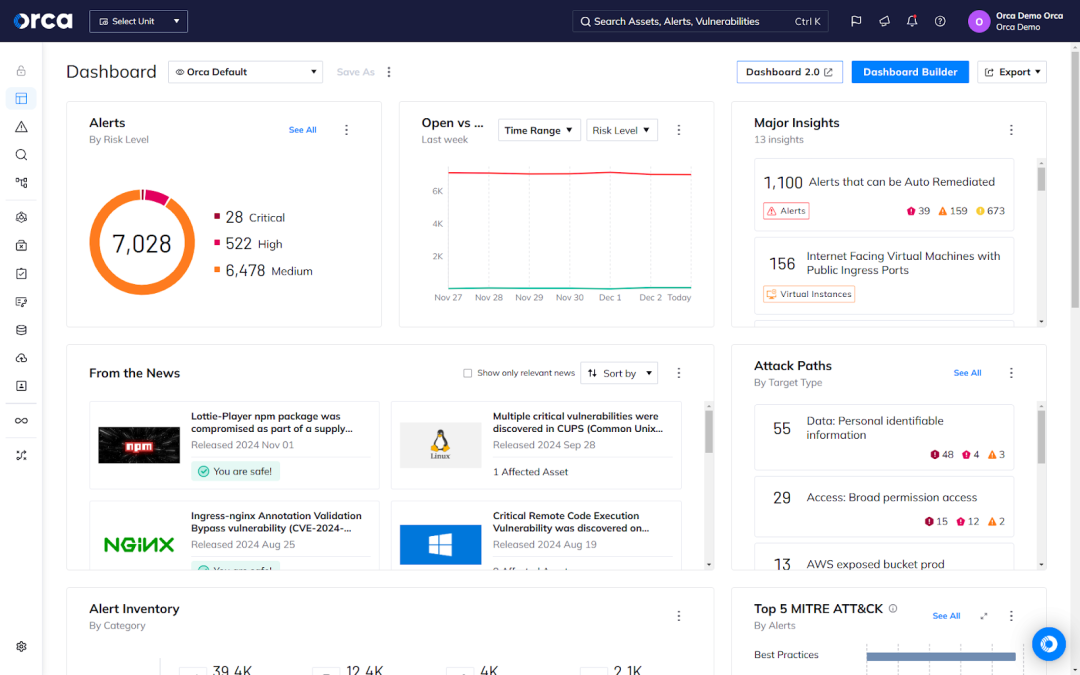
The future of Azure security
As we look to the future, several exciting developments are shaping the landscape of Azure security.
AI-driven security
As referenced earlier, cloud risks often present overwhelming demands on security teams. To help compensate for capacity constraints, knowledge gaps, and talent shortages, many cloud security solutions are introducing AI-driven capabilities. These features leverage generative AI (GenAI) and machine learning (ML) to automate or accelerate security workflows.
Examples include AI-powered search capabilities that enable users to more easily understand what exists in their cloud environments, whether specific risks or resources. Other examples include capabilities that streamline remediation by generating tailored remediation instructions and code that security teams can use when coordinating with development teams.
The future promises more advanced AI-driven capabilities across more cloud security use cases.
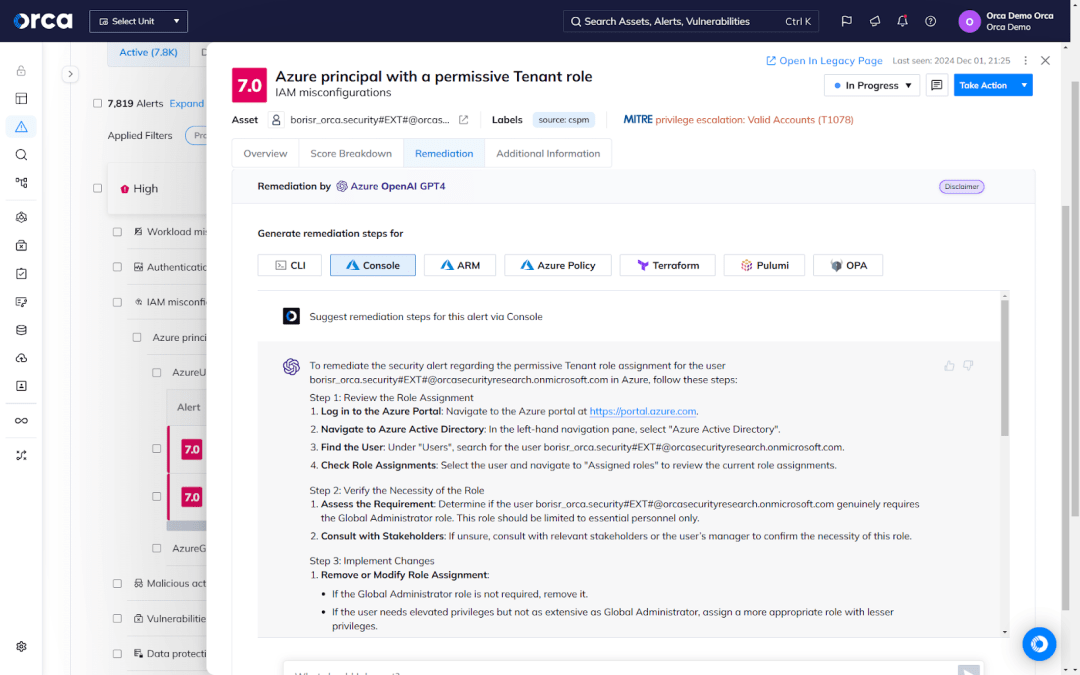
The risk of AI innovation
While GenAI provides benefits to cloud security teams, it also introduces a new category of risks they must protect against. Today, 56% of organizations are using GenAI to build custom applications in the cloud, according to the 2024 State of AI Security Report. This expands their attack surface, requiring security teams to properly configure the AI services offered by CSPs, gain a full inventory of their AI models and packages, as well as prioritize their AI risks.
As a result, some advanced CNAPP solutions have introduced AI Security Posture Management (AI-SPM) capabilities to meet these needs.
For example, the Orca Cloud Security Platform offers an AI-SPM solution that detects and surfaces your AI risks end-to-end—from training and fine-tuning to deployment and inference. It became the first CNAPP solution to support GPT-4 through Microsoft’s Azure OpenAI service. Today, it supports more than 50 AI services, models, and packages.
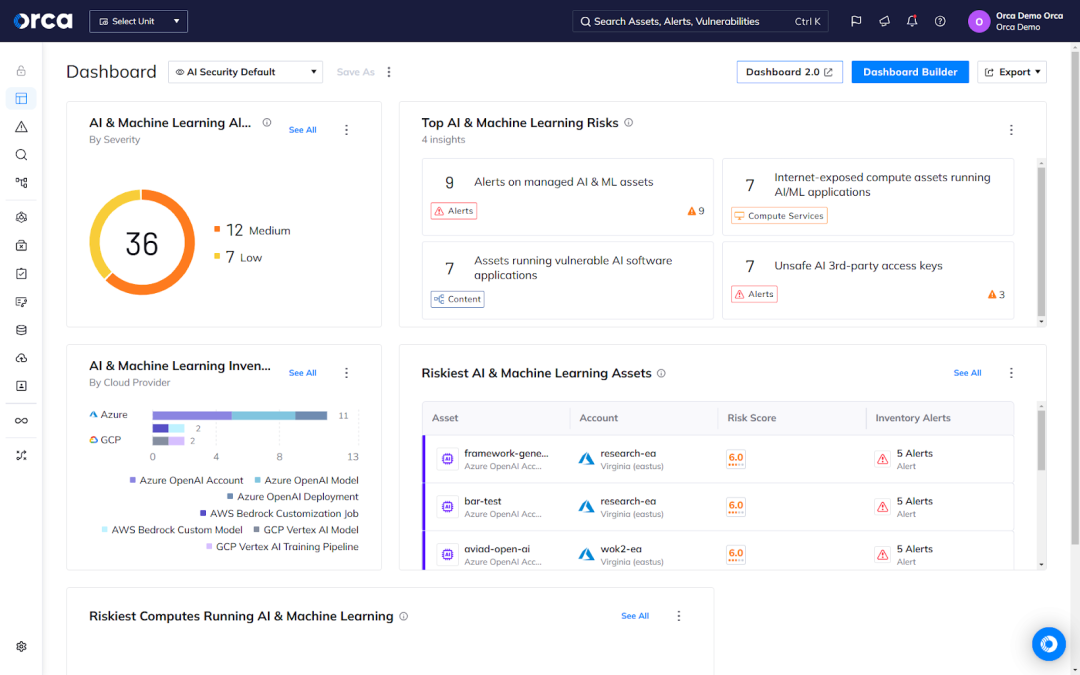
Conclusion
The importance of cloud computing continues to grow, with institutions such as Gartner predicting that it will become a necessary business investment by 2028. For Microsoft Azure, this represents welcome news as the company represents the second most popular cloud service provider. Yet for organizations, it highlights the growing need for strong cloud security measures and controls.
As this post illustrates, enhancing your Azure security calls for a variety of practices, solutions, and considerations. By understanding them and embracing the best practices covered in this post, you can begin to optimize your Azure security and leverage the full potential of the platform.
About the Orca Cloud Security Platform
As a true CNAPP, the Orca Cloud Security Platform provides comprehensive cloud security capabilities across the full application lifecycle. For Azure security, as well as other popular CSP environments, the Orca Platform offers advanced detection, effective risk prioritization, fast and easy remediation, as well as automated compliance. The Orca Platform does this by delivering full coverage, holistic risk analysis across all types, seamless integrations, built-in compliance frameworks and tools, and more.
For example, Orca offers more than 50 deep integrations with cross-functional applications and more than 160 out-of-the-box compliance frameworks.
Using Orca’s patented SideScanning™ Technology, the Orca Platform contextualizes risks and discovers any dangerous risk combination that can endanger your high-value assets. This enables Orca to prioritize risks effectively, reduce alert fatigue, and allow your teams to focus on their most important tasks.
To see the Orca Platform in action, schedule a personalized demo with one of our experts.
FAQs
What are Azure security fundamentals?
Azure security fundamentals are the core principles for securing the Azure cloud platform. They cover a variety of cloud security disciplines, such as identity and access management (IAM), data encryption, network security, threat protection, and security monitoring. Mastering these fundamentals is crucial for organizations to enhance their Azure security and protect their cloud environment.
What are Azure’s main security risks?
Key security risks in Azure include misconfigurations, vulnerabilities, malware, lateral movement risks, permissive identities, and more.
What are the key benefits of Azure security?
The primary benefits of Azure security include the following:
- Enhanced protection for cloud resources.
- Insurance against security incidents.
- Improved efficiency for security, DevOps, and development teams.
- Better coordination and collaboration between security and development teams.





