Table of contents
- What does DevSecOps stand for?
- History of DevSecOps
- What does DevSecOps entail?
- Why do you need DevSecOps?
- How can you implement DevSecOps?
- DevSecOps best practices
- How do you foster a DevSecOps culture?
- Tools and technologies for DevSecOps
- What are the challenges in implementing DevSecOps?
- How does a CNAPP help DevSecOps?
- FAQs
In today’s fast-paced world of cloud-native development, organizations are under tremendous pressure to deliver applications quicker than ever. However, this speed often comes at a significant cost—security. Historically, security has been an afterthought, handled at the end of the software development lifecycle (SDLC). This not only increases time and cost, but it results in vulnerabilities that can slow down the entire development process when code is returned for corrections. Poor security in production can also have disastrous consequences for customers and company reputation.
Imagine working on a complex project where developers are coding at breakneck speed and operations teams are deploying seamlessly—until security steps are performed at the last minute, exposing critical flaws and bringing everything to a standstill. This scenario was all too common before the advent of DevSecOps.
DevSecOps is a game-changing methodology that integrates security into all phases of the SDLC workflow from the very start, also referred to as Shift Left Security. This prevents bottlenecks and guarantees that security concerns don’t stifle innovation.
So, what exactly is DevSecOps? How does it work? What challenges does it address? And what best practices can you use to foster a DevSecOps culture within your SDLC?
In this guide, we will answer these and other concerns to help you leverage DevSecOps and thrive while keeping up with modern development methods and speed.
What does DevSecOps stand for?
DevSecOps stands for Development, Security, and Operations. It represents a cultural shift integrating security into every software development lifecycle phase (SDLC). This approach allows organizations to release software quickly and securely, avoiding last-minute panic over vulnerabilities before, or even worse, in deployment.
To successfully implement DevSecOps, organizations must encourage collaboration, automate processes, and cultivate a shared sense of responsibility among all teams for security throughout the SDLC. This proactive approach eliminates late-stage security vulnerabilities, which can be hard and expensive to remedy.
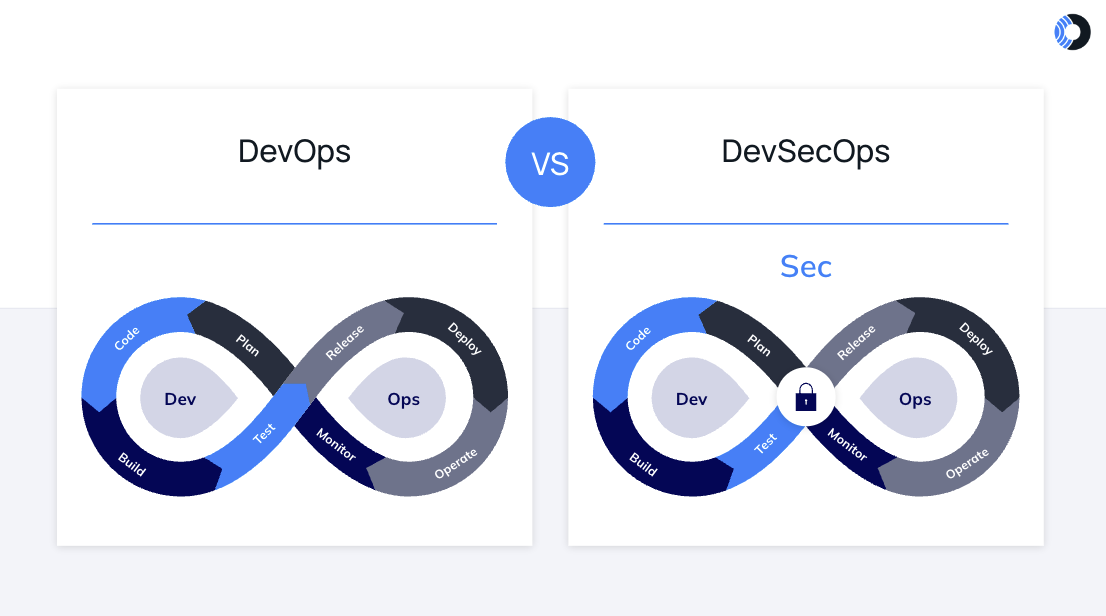
DevSecOps is an extension of the DevOps practice. It combines DevOps principles with security practices, focusing on application and infrastructure security from the start. While DevOps focuses on automation and continuous integration, the “Sec” in DevSecOps guarantees that security measures are applied promptly and consistently.
History of DevSecOps
Let’s take a trip down memory lane to explore how the evolution of DevSecOps has been shaped by changes in software development practices over the years:
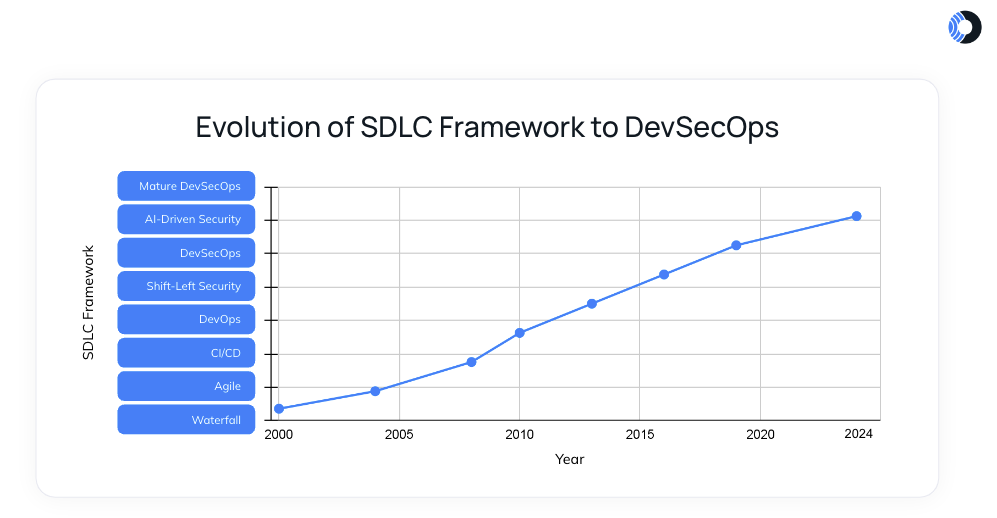
- Waterfall Era: Back in the late 90s and early 2000s, software development followed the waterfall methodology, which resembled constructing a skyscraper. This linear approach required detailed plans and strict sequences, where each stage had to be completed before moving on. Imagine the stress of realizing a major flaw in the foundation when the building is halfway complete! In this model, security was often an afterthought, addressed only at the end of development, causing significant project delays and costly fixes.
- Agile and DevOps: Around 2010, the DevOps methodology emerged, transforming software development with its focus on collaboration, automation, and speed. This approach shifted the process from a rigid structure to a more flexible, iterative model. While development and operations teams began collaborating more effectively, security teams often remained isolated and reactive.
- Shift-Left Movement: Around 2012, the “Shift Left” movement encouraged teams to address security earlier in the development process, making it a proactive priority instead of a reactive concern.
- DevSecOps Emergence: By 2014, the idea of integrating security fully into the DevOps process—creating DevSecOps—began to take hold. This was about embedding security at every step of the way, not just at the end.
Fast forward to today, DevSecOps practices are more advanced than ever. With tools like the Orca Cloud Security Platform, organizations can integrate security across their entire stack—from code to infrastructure—ensuring comprehensive protection throughout the development lifecycle.
What does DevSecOps entail?
Traditionally, developers prioritized speed, often pushing features to production quickly while security teams struggled to keep pace, leading to vulnerabilities that could compromise applications and data integrity. With DevSecOps, security becomes a shared responsibility, embedded in every phase of the development lifecycle, enabling teams to collaborate effectively toward a common goal.
Key Components of DevSecOps
Below, we list the most important components of DevSecOps:
- Continuous integration and delivery (CI/CD): This combined approach encourages developers to frequently commit code to a central repository, allowing for automatic integration and testing. By catching bugs and integration issues early, teams can ensure a smoother transition from development to production. Rigorous testing, including user interface and API assessments, helps deliver production-ready code that meets user expectations consistently.
- Continuous security: Integrating security practices throughout the development lifecycle is essential. This involves conducting threat modeling and implementing automated security testing at various stages. By continuously evaluating the software for vulnerabilities and other risks, organizations can deliver secure applications while minimizing the risk of security breaches.
- Collaboration and communication: Effective collaboration among development, security, and operations teams is crucial for the success of DevSecOps. By breaking down traditional silos and fostering open communication, organizations create a culture where security is everyone’s responsibility. This collaborative spirit enhances security awareness and encourages the sharing of knowledge and best practices.
- Automation of security processes: Automation is vital for streamlining security checks and testing. By integrating security tools into the CI/CD pipeline, organizations can conduct security evaluations without hindering development speed. Automated tools provide real-time feedback, enabling developers to address potential security risks as they write code.
Why do you need DevSecOps?
In an era of increasingly sophisticated cyber threats, DevSecOps has become essential for organizations aiming to efficiently deliver secure software. Here’s why:
- Early detection of vulnerabilities: DevSecOps ensures that software teams identify and address vulnerabilities at earlier stages of development. This proactive approach minimizes the cost and time required to fix issues, ensuring a smoother and more secure user experience.
- Faster time to market: DevSecOps allows software teams to automate security tests, lowering the chance of human error. This prevents security assessments from becoming bottlenecks in development processes, resulting in faster software delivery without compromising security.
- Regulatory compliance: DevSecOps facilitates regulatory compliance for organizations by integrating security best practices into the development process. For example, Orca Security’s multi-cloud compliance capabilities focuses on risk management and compliance for the cloud and containerized apps, allowing organizations to achieve continuous multi-cloud security compliance with 150+ standards and CIS benchmarks such as PCI DSS, HIPAA, and GDPR.
- Improved collaboration: DevSecOps encourages open channels of communication between the security, operations and development teams, leading to a shared responsibility for security. They can therefore work together to identify and remedy vulnerabilities, making the development process more secure.
- Stronger security culture: DevSecOps develops a security-conscious culture in which everyone is responsible for protecting the software they develop. This empowers teams whereby developers are more proactive in crafting secure code, identifying potential security concerns, and working with security and operations professionals to ensure the product being deployed is secure and compliant.
How can you implement DevSecOps?
Implementing DevSecOps is about weaving security into the fabric of your development processes. Here are some of the steps you can follow to effectively implement DevSecOps in your organization:
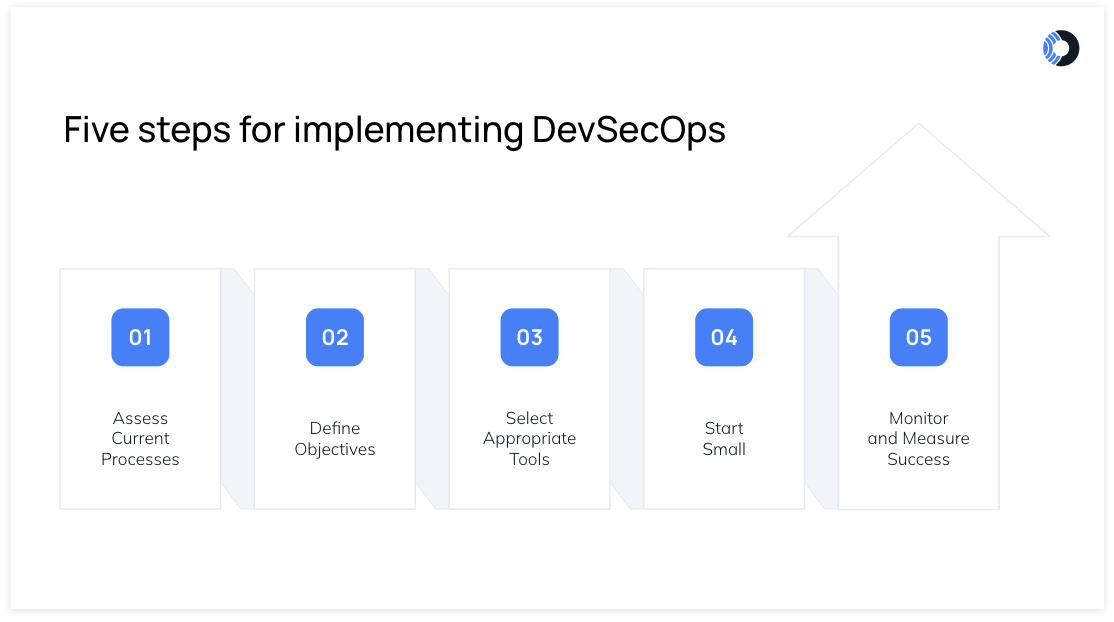
- Assess current processes: Start by assessing your current workflows to pinpoint where security can be better integrated. For instance, if your team is using CI/CD pipelines, consider how security checks can be embedded at each stage.
- Define objectives: Next, define clear objectives for your DevSecOps initiative. Are you aiming to enhance your security posture or reduce vulnerabilities? Having specific goals will guide your strategy and help measure success.
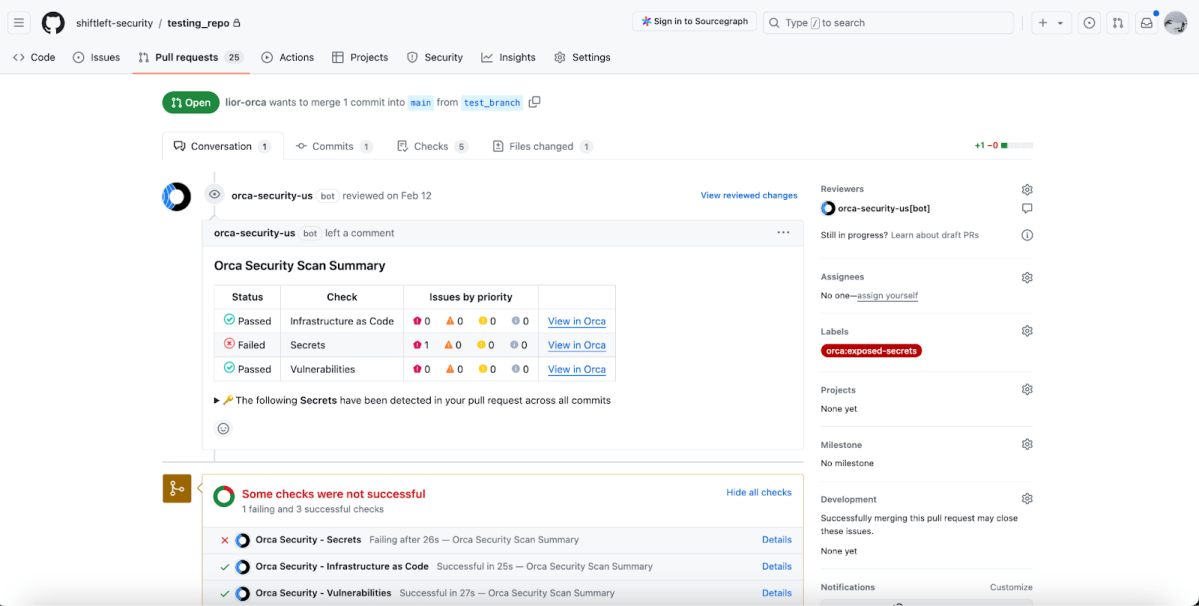
- Select appropriate tools: Choosing the right tools is crucial. Look for solutions that automate security tasks and integrate seamlessly into your existing processes and don’t require your developers to change the way they work. For example, Orca’s Shift Left Security offers native integrations with common CI and development tools, including Jenkins, BitBucket, CircleCI, GitHub, GitLab, as well as an Orca command-line interface (Orca CLI) to surface findings in native development tooling as well as the Orca Platform UI.
- Start small: Implement DevSecOps practices in a pilot project first. This allows you to test integration strategies and refine your approach before rolling it out across the organization. Encourage feedback from your teams throughout this process to identify challenges and celebrate successes.
- Monitor and measure success: Finally, establish metrics to monitor the effectiveness of your DevSecOps practices. Track vulnerabilities and project delivery timelines to see how well your initiatives are performing.
DevSecOps best practices
Here are some best practices for implementing DevSecOps:
1. Shift Left on Security
One of the most important practices is to “shift security left,” which means integrating security measures early in the SDLC process. This approach allows teams to identify and fix any vulnerabilities, secrets, and misconfigurations before they reach production, ensuring that security is a priority from the outset.
2. Automate Security Processes
Automation plays a crucial role in maintaining security without hindering development speed. By automating security checks, teams can ensure that security measures are consistently applied, allowing developers to focus on building features rather than manually checking for vulnerabilities.
3. Foster Collaboration Across Teams
Creating a collaborative environment is vital for DevSecOps’ success. Orca Security emphasizes the need for open communication and shared responsibility for security. Regular cross-functional meetings can help align development, security, and operations teams on common security goals.
4. Educate and Train Developers
Training developers on secure coding practices is essential. Orca Security notes that many developers may not be aware of “common vulnerabilities or secure coding standards.” Providing resources and training sessions empowers them to write secure code from the beginning.
5. Implement Continuous Monitoring
Continuous monitoring is key to maintaining security in a fast-paced environment. Orca Security highlights the importance of real-time visibility into application performance and security, enabling teams to quickly detect and respond to anomalies before they escalate.
How do you foster a DevSecOps culture?
Building a strong DevSecOps culture is essential for the success of any security program. It begins with changing the organizational mindset and ensuring that processes are in place to facilitate this transition. Traditional barriers, such as rigid policies and workflows, must be dismantled to promote a culture of shared responsibility and collaboration among development, security, and operations teams.
Here are some of the steps you can follow to foster a DevSecOps culture in your organization:
- Start with leadership buy-in: The journey to cultivating a thriving DevSecOps culture begins at the top. Leadership’s involvement is crucial, as it sets the tone for the entire organization. Leaders are not just decision-makers; they are influencers. When executives prioritize DevSecOps, it sets a positive tone for the entire organization. This commitment encourages open communication, allowing team members to discuss security challenges and solutions freely. Establishing channels for dialogue empowers everyone to contribute their insights, fostering a collaborative environment.
- Break the silos and encourage collaboration: Traditional silos create communication barriers and hinder security efforts. Effective collaboration between Dev, Sec, and Ops fosters faster time to market, enhanced security, and optimized resource allocation. By recognizing and rewarding teams that exemplify the DevSecOps principle of collaboration, teams are motivated to adopt the DevSecOps culture.
- Create room for experimentation: Encourage teams to explore new tools and processes without fear of failure, as this can lead to innovative solutions. Additionally, setting clear expectations regarding security responsibilities ensures that everyone understands their role in maintaining security throughout the development lifecycle.
By following these strategies, organizations can effectively implement DevSecOps, adopt best practices, and cultivate a culture that prioritizes security and collaboration.
Tools and technologies for DevSecOps
Organizations that would like to effectively implement DevSecOps must have the right tools and technologies. These tools automate security processes and seamlessly integrate them into existing workflows, thus boosting the organization’s security posture and delivering applications more effectively and securely. Here are some examples of DevSecOps tools and technologies:
Static Application Security Testing (SAST)
DevSecOps developers utilize SAST tools to analyze source code for vulnerabilities before the application is compiled and run. SAST tools offer automatic code checks and real-time feedback, which is a proactive approach that helps to identify potential security issues early in the development process.
Dynamic Application Security Testing (DAST)
DAST tools enable you to simulate real-world attacks using a series of predefined tests while the application is running. This allows you to identify vulnerabilities that static code analysis may not detect.
Container Scanning
Container scanning solutions are essential for organizations that utilize containerized applications. They provide security features that are specifically designed to protect the container and its underlying infrastructure from potential security threats.
Infrastructure as Code (IaC) Scanning
IaC security tools enable you to execute automated security checks on your infrastructure at the code level for noncompliance with security policies and standards. As a result, they enforce security policies within IaC templates, guaranteeing compliance and minimizing the risk of misconfigurations being shipped to production.
Software composition analysis (SCA)
When creating applications and features, developers often employ third-party frameworks and plugins, which may introduce security risks. DevSecOps therefore relies heavily on software composition analysis tools, which are crucial for identifying open-source components in applications and ensuring that known vulnerabilities are fixed.
What are the challenges in implementing DevSecOps?
While DevSecOps offers numerous benefits, organizations face several challenges during implementation:
- Cultural resistance: Changing to a DevSecOps model requires a cultural change, which can be met with resistance from teams used to traditional ways of working. To shift the mindsets of teams to prioritize security and overcome this challenge, you need to ensure strong leadership, continuous training and communication across teams.
- Tool overload: Another challenge faced during DevSecOps implementation is integrating new security tools into existing workflows. The sheer number of security tools can lead to confusion and inefficiency and that is why you need to adopt platforms like Orca Security which offers deep integrations with popular tools like GitHub and GitLab that seamlessly fit into your development pipelines without disrupting productivity.
- Skill gaps: To implement DevSecOps, all team members must have the necessary skills or knowledge of security practices, which may not always be available. To bridge this skills gap, firms may need to prioritize team upskilling or hiring specialist personnel.
How does a CNAPP help DevSecOps?
A Cloud-Native Application Protection Platform (CNAPP) is instrumental for organizations adopting DevSecOps, as it provides comprehensive security throughout the entire application lifecycle—from development to deployment and beyond. By consolidating various security capabilities such as vulnerability management, cloud security posture management (CSPM), and workload protection into a single platform, CNAPPs simplify security processes and enhance collaboration among development, security, and operations teams.
With a CNAPP, organizations can automate and unify security across their cloud environments, ensuring continuous monitoring and protection of all infrastructure and applications. This automation aligns perfectly with the DevSecOps philosophy, facilitating faster and more secure software delivery.
CNAPPs address the challenges associated with using multiple, siloed security tools. Instead, they offer full visibility into cloud environments, allowing teams to detect security and compliance risks across the entire technology stack, including cloud configurations, workloads, and identity management. This holistic view is crucial for identifying vulnerabilities early in the development lifecycle, a practice known as shift-left security.
By combining vulnerabilities with contextual information and relationships, CNAPPs help organizations understand how seemingly unrelated low-severity risks can converge to create significant attack vectors. This insight allows security teams to prioritize remediation efforts effectively, reducing the chances of misconfigurations and security mismanagement.
Furthermore, CNAPPs facilitate better collaboration by providing a unified platform that all stakeholders can use, thereby linking development and operations visibility with risk analysis. This integration improves the overall enterprise security posture, allowing organizations to maintain consistent security policies across their cloud assets while minimizing operational overhead.
About the Orca Cloud Security Platform
The Orca Cloud Security Platform serves as a full-featured Cloud-Native Application Protection Platform (CNAPP) to guard cloud-native apps. It offers deep visibility into vulnerabilities across the whole stack—from code to runtime (and back)—allowing organizations to proactively spot and fix security issues.
Orca uses an agentless-first approach to seamlessly integrate into your cloud environment. This ensures security measures do not disrupt workflow. With Orca, teams are empowered to maintain a strong security posture without sacrificing speed or agility. Orca helps organizations address vulnerabilities, misconfigurations, and compliance issues throughout development.
With Orca, organizations can leverage a unified platform that simplifies cloud security, enhances team collaborations, and speeds up remediation efforts. Ultimately, this builds a security-centered culture within the DevSecOps framework. Schedule a personalized 1:1 demo with an Orca expert to see how your company can benefit from the Orca CNAPP Platform.
FAQs
What is the difference between DevOps and DevSecOps?
DevOps and DevSecOps differ in their focus and approach. DevOps aims to optimize and automate development and operations processes for faster software delivery. DevSecOps goes a step further by incorporating security practices into this collaboration. It ensures that security is an integral part of the development process and a shared responsibility throughout the software development life cycle (SDLC), rather than being an afterthought.
Why is DevSecOps the future?
DevSecOps is paramount for the future due to the evolving cyber threat landscape, which renders traditional security measures ineffective and demands a more proactive approach toward security. By integrating security measures in the development process, DevSecOps protects sensitive data, mitigates vulnerabilities, and ensures continued compliance. Simply put, security can no longer be treated as an afterthought but should be woven into the fabric of software development in every way.
Can DevSecOps reduce the risk of data breaches?
DevSecOps does indeed lower the risk of data breaches. If you build security into each stage of the SDLC, you will be able to identify and resolve vulnerabilities much earlier, reducing the risk of these issues emerging in the production environment. As a result, sensitive data becomes more secure, and the risk of data breaches is significantly decreased.
Table of contents
- What does DevSecOps stand for?
- History of DevSecOps
- What does DevSecOps entail?
- Why do you need DevSecOps?
- How can you implement DevSecOps?
- DevSecOps best practices
- How do you foster a DevSecOps culture?
- Tools and technologies for DevSecOps
- What are the challenges in implementing DevSecOps?
- How does a CNAPP help DevSecOps?
- FAQs