You may be thinking: ‘Wait, this new CVE starts with 2018.., this must be a mistake?’. In fact, it is not a mistake. This is about a CVE that everyone thought was patched years ago but now appears to be alive and well.
In April 2018, a bug report was submitted to Zlib’s Github repository about a vulnerability, later identified as CVE-2018-25032, that could potentially allow a Denial-of-Service (DoS) attack. The vulnerability was promptly fixed. However, the patch never made it into release. Now, almost 4 years later, it looks like the vulnerability is finally getting its day in the spotlight. On March 25, 2022, Tavis Ormandy of Google’s Project Zero notified the OSS-Security mailing list of the vulnerability. While at first it seemed the issue was only reproducible in Zlib libraries with non-default flags, a couple of days later Tavis confirmed on Twitter that he and his team have a working Proof-of-Concept which reproduces the issue on the default configuration of Zlib, making it far more ubiquitous than previously thought.
The Orca Security Research Pod is highlighting this CVE due to the extreme popularity of the Zlib library. As of publishing this blog, the CVE is not yet known to be exploitable. Our team will continue to provide updates as details emerge.
What is Zlib?
Originally released in 1995, Zlib is an open source software library which implements the DEFLATE lossless compression algorithm – the same algorithm supported by the ZIP file format. The library has since been widely adopted for file decompression and it is not an overstatement to say that it is used by millions of applications. To further demonstrate how widely Zlib is used: it is more than likely you are reading this on a browser which uses Zlib.
Data compression is an important part of any application, including almost all those using internet communication. Websites constantly send pictures, videos, and other large files which, if uncompressed, simply take up too much space. The reduction in file size means less bandwidth being used – allowing for faster loading times, higher-quality content streaming, and snappier communication between servers and clients. The HTTP protocol, which websites and many applications are based on, also supports DEFLATE compression, and the Zlib library is a popular choice for browsers and web servers alike to implement that capability.
CVE-2018-25032
As mentioned, the Zlib vulnerability was first discovered in 2018 by Danilo Ramos of Eideticom. In certain cases, such as maliciously-crafted payloads, the vulnerability could allow the data being compressed (deflated) to overwrite critical areas of an application’s memory, leading to corrupted output and potentially crashing the application, causing Denial-of-Service (DoS).
At this point, it does not appear that the vulnerability leads to Remote Code Execution, but as the story progresses and more analysts begin to look into the issue, RCE is not out of the question.
Remediating CVE-2018-25032
In the original patch commit, it is mentioned the bug was introduced in Zlib version 1.2.2.2; while not verified, it is safe to assume the issue affects all versions up to 1.2.12 – the first new release of Zlib in over 5 years. As the Zlib library is used by many applications, organizations must approach their software vendors and ensure they implement the fix, and then update to the vendor’s latest software version. Alternatively, Linux distributions such as Ubuntu and Alpine have already implemented the fix in their latest releases, so you may want to update Zlib to your platform’s release of version 1.2.12, and re-compile any programs with the updated library. Of course, the patch is also available on Zlib’s GitHub page.
Identifying CVE-2018-25032 with Orca Security
The Orca Security Platform can detect cloud workloads impacted by CVE-2018-25032 on AWS, Azure and Google Cloud. In the main Risk Dashboard, Orca users can navigate to the From the News widget and click on the CVE announcement to learn more about the risk and see all the workloads in their cloud environment that are vulnerable to the CVE.
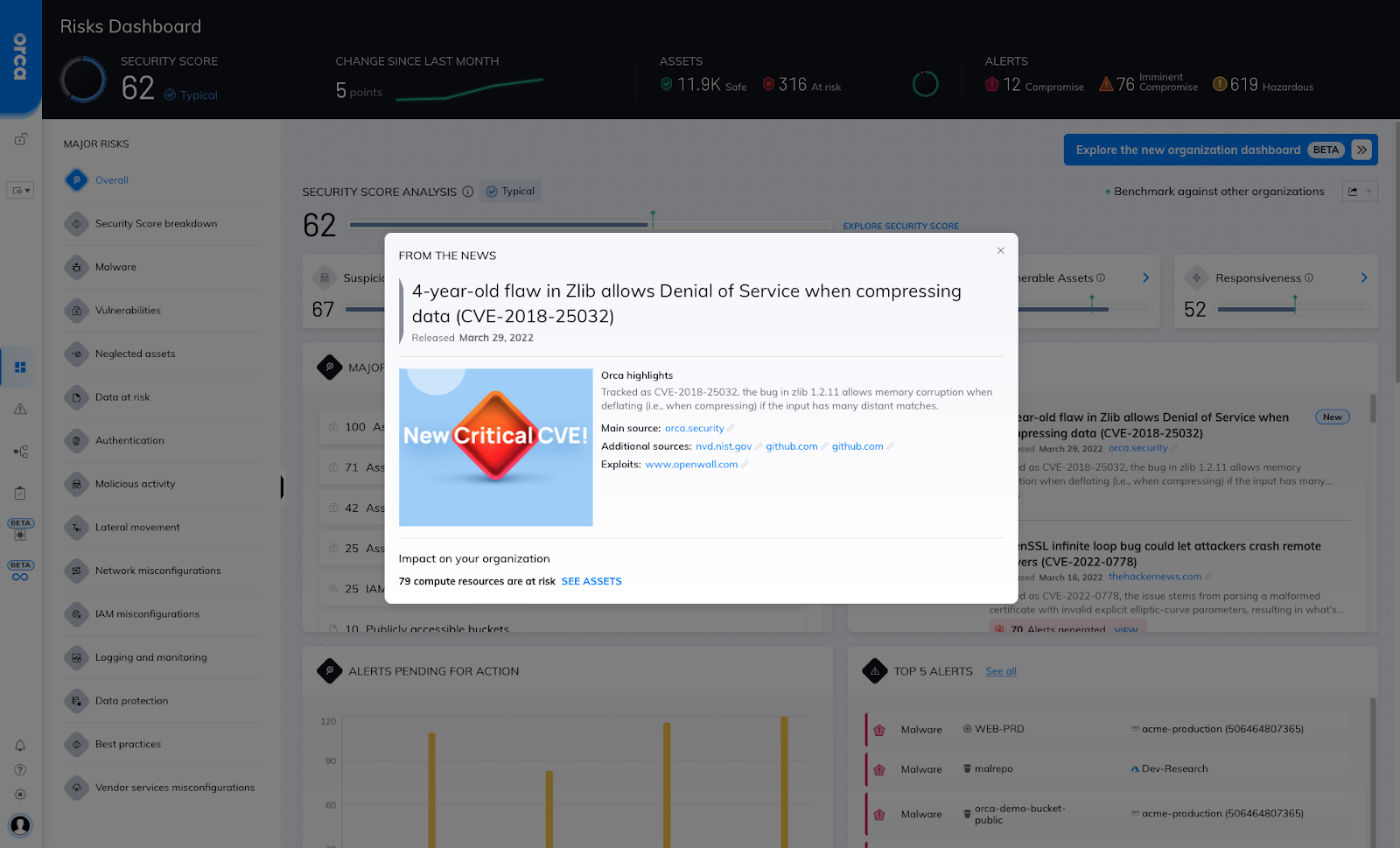
CVE-2018-25032 as shown in the From the News Widget
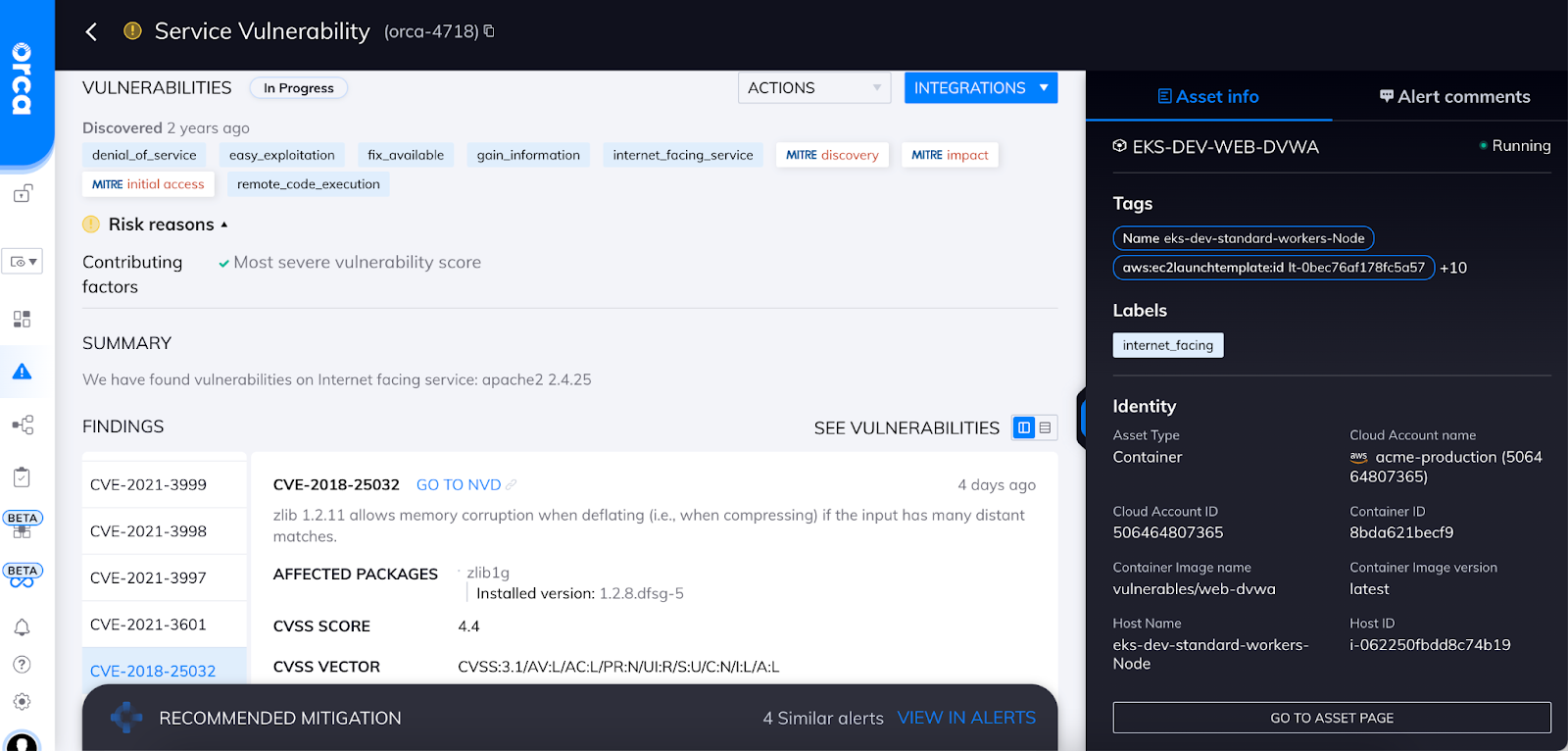
CVE details in the Orca UI
Users can then view specific findings, prioritized by assets with the greatest risk. Similar to Log4Shell, this CVE has the potential to dramatically impact customer environments since it is ubiquitous and has a known PoC. When a notable CVE like this one is announced, it is essential to have 100% comprehensive coverage across your entire cloud environment , so you can ensure that you catch each and every CVE. This is simply not possible with agent-based cloud security solutions. Orca’s agentless platform however, provides 100% visibility into every layer of your cloud estate and deploys in minutes.
In addition to full coverage, it is also important that your vulnerability management program is able to automatically prioritize the vulnerabilities that pose the greatest risk to your organization, so security teams can focus on the risks that need to be triaged or remediated first.
Sign Up for a Free Risk Assessment
To see if your environment is impacted by this CVE or other known vulnerabilities, sign up for a free, no obligation risk assessment today.






