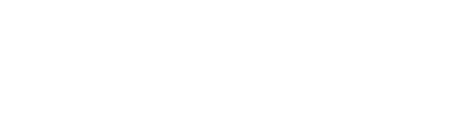The Challenge
Incomplete Insights Provide Incomplete Security
Existing threat detection solutions were not built for the cloud and rely on agents to obtain workload telemetry. They lack insight into the entire cloud attack surface that encompasses workloads, cloud configurations, events, and identities.
EDR, TDR, and XDR solutions only detect risks at the cloud workload level, not the control plane. For example, a stolen identity used by an outside attacker won’t be detected by workload-focused tools.
Many existing CDR tools are adapted from on-premises TDR, EDR or XDR solutions that don’t offer any cloud telemetry or present blindspots due to lack of contextual insight.
Detection & Response tools require security agents to be installed for each asset.
Our Approach
CDR Built for the Cloud
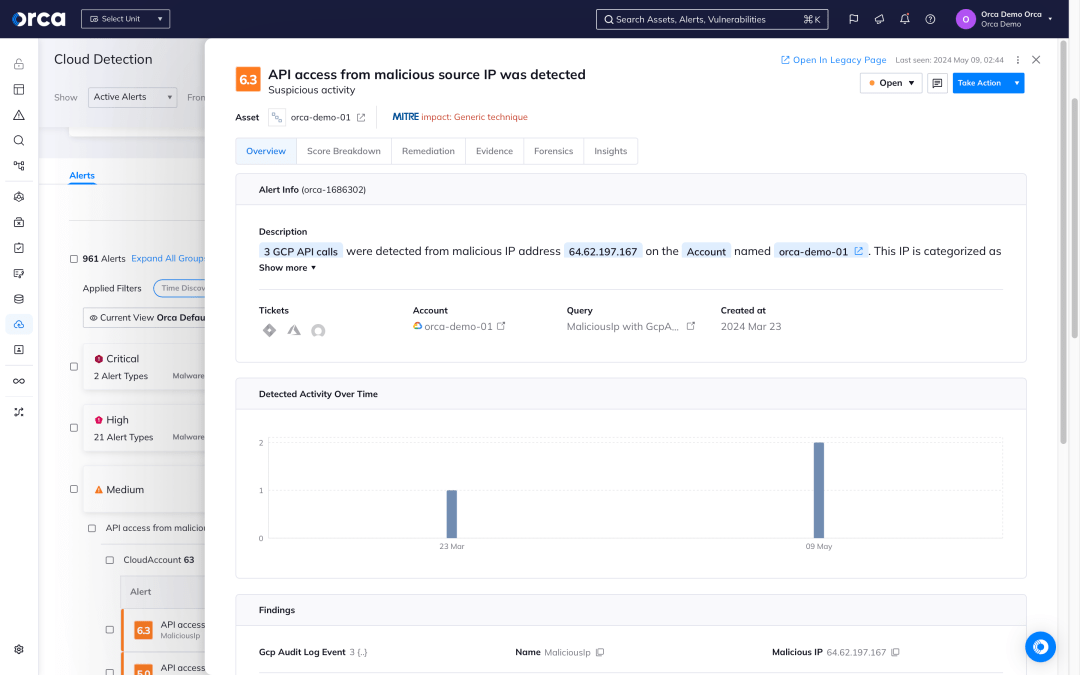
Orca provides 24×7 monitoring of cloud provider logs and threat intelligence feeds. By uniquely combining this information with Orca’s insights into existing risks found in cloud workloads and configurations, and the location of the company’s most critical assets, Orca quickly recognizes which events are potentially dangerous and require immediate attention.
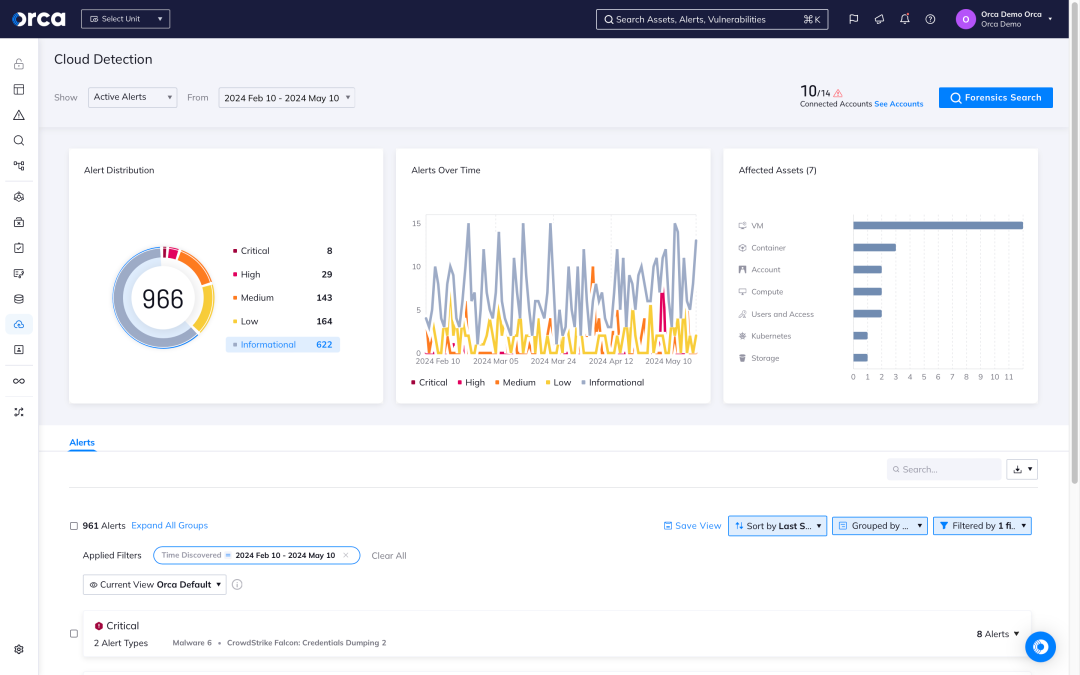
Detect
Receive alerts when changes and anomalies occur that indicate possible malicious intent versus normal behavior, automatically prioritizing events that endanger the company’s most critical assets.
Investigate
Research malicious activity to quickly gain insight into whether the events are malicious and if any of the organization’s critical assets are in danger.
Respond
Intercept cloud attacks by leveraging remediation steps and automatically assigning issues using Orca’s 50+ third-party technical integrations (including SOAR, notifications, and ticketing systems).
With Orca’s CDR capabilities, organizations can detect, investigate, and respond to cloud attacks in progress.
Continuous analysis without requiring agents
Orca’s SideScanning™ technology collects workload-deep intelligence and cloud configuration metadata without the blind spots, organizational friction, high TCO and performance hits of agent-based solutions.
- Automatically cover 100% of your assets, including newly added assets.
- Orca combines cloud events and threat intelligence with risks found in cloud workloads, configurations and identities to understand when anomalies could potentially be dangerous.
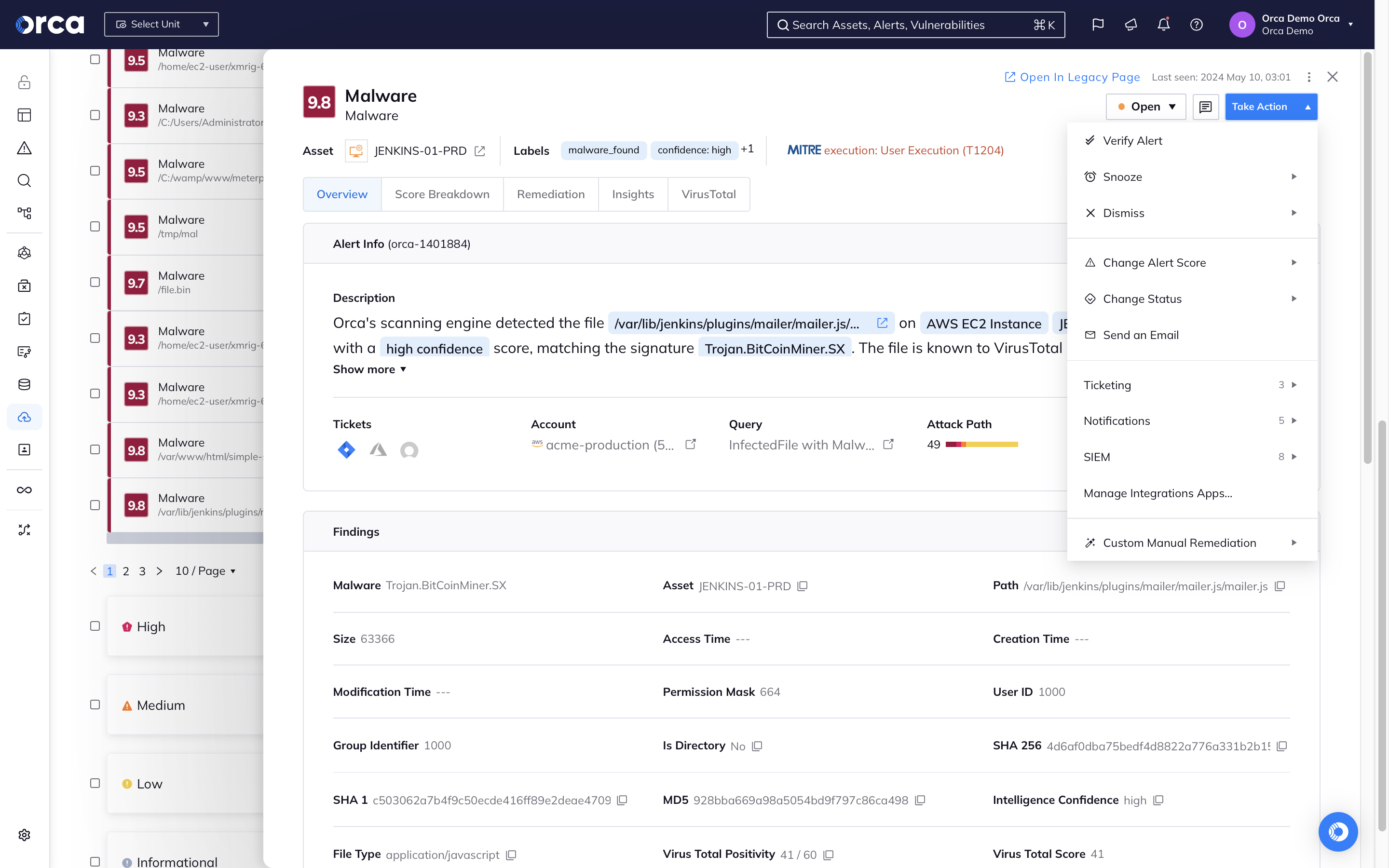
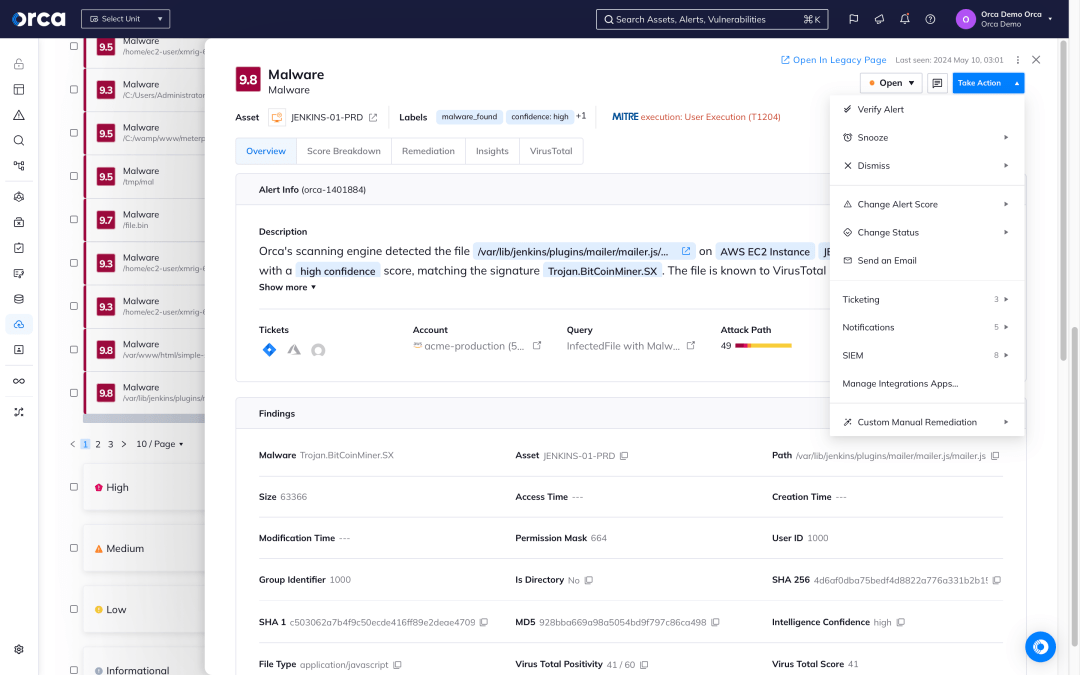
- For malware-based threats, the Orca Platform augments its CDR capabilities with signature and heuristic-based malware detection for all workloads.
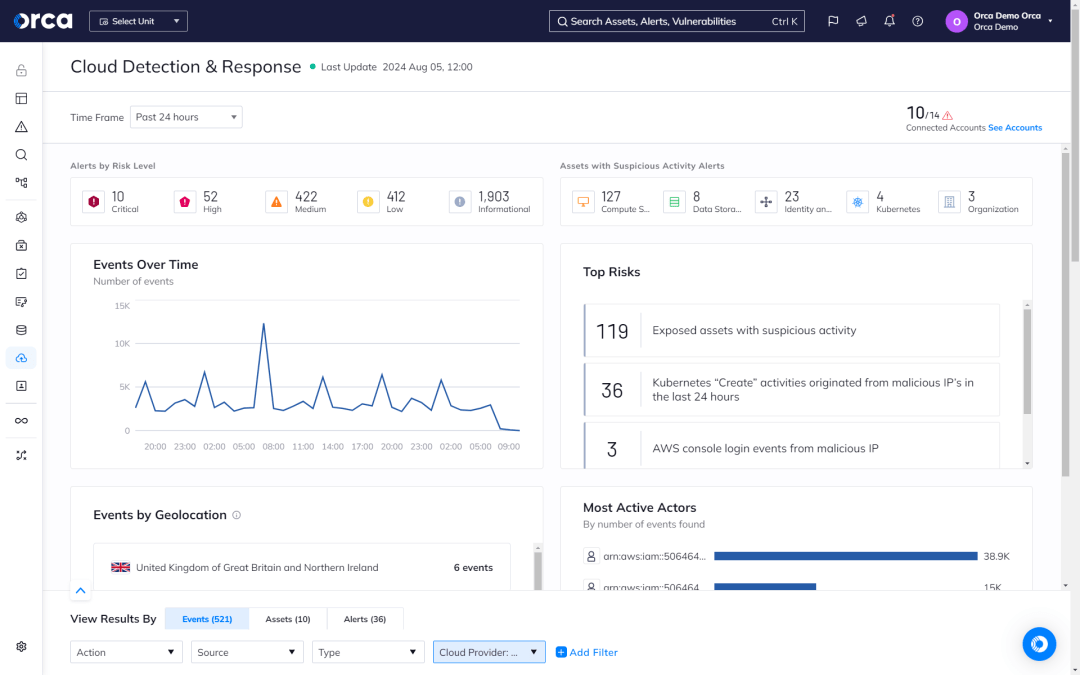
Empowering the SOC and IR team
With CDR in place, teams can leverage vital telemetry to closely monitor their cloud estate and quickly respond to suspicious activities, events, or changes demanding immediate action.
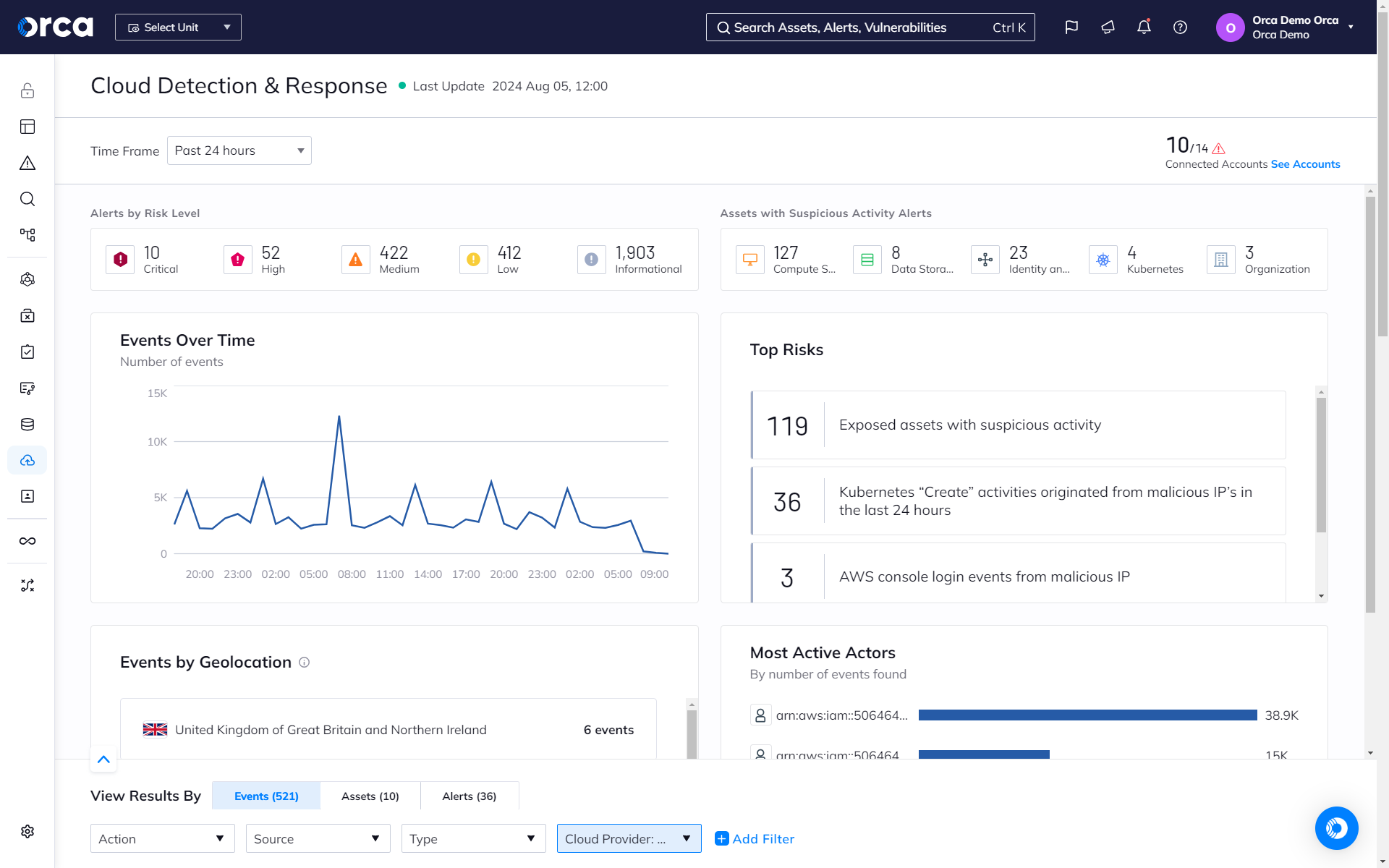
- View timely, actionable insights from Orca’s event-driven security dashboard to expedite investigation and response.
- Leverage cloud-agnostic event parameters that use universal terminology, enabling lean teams to streamline investigations without cloud-provider specialization or knowledge.
- Dynamically search and filter all cloud logs from a single, unified location using any event parameter, SQL query, or pre-built investigation from Orca’s catalog.
Fast remediation to stop attacks
Orca helps teams quickly discover and mitigate risks, limiting any potential damage of an ongoing attack.
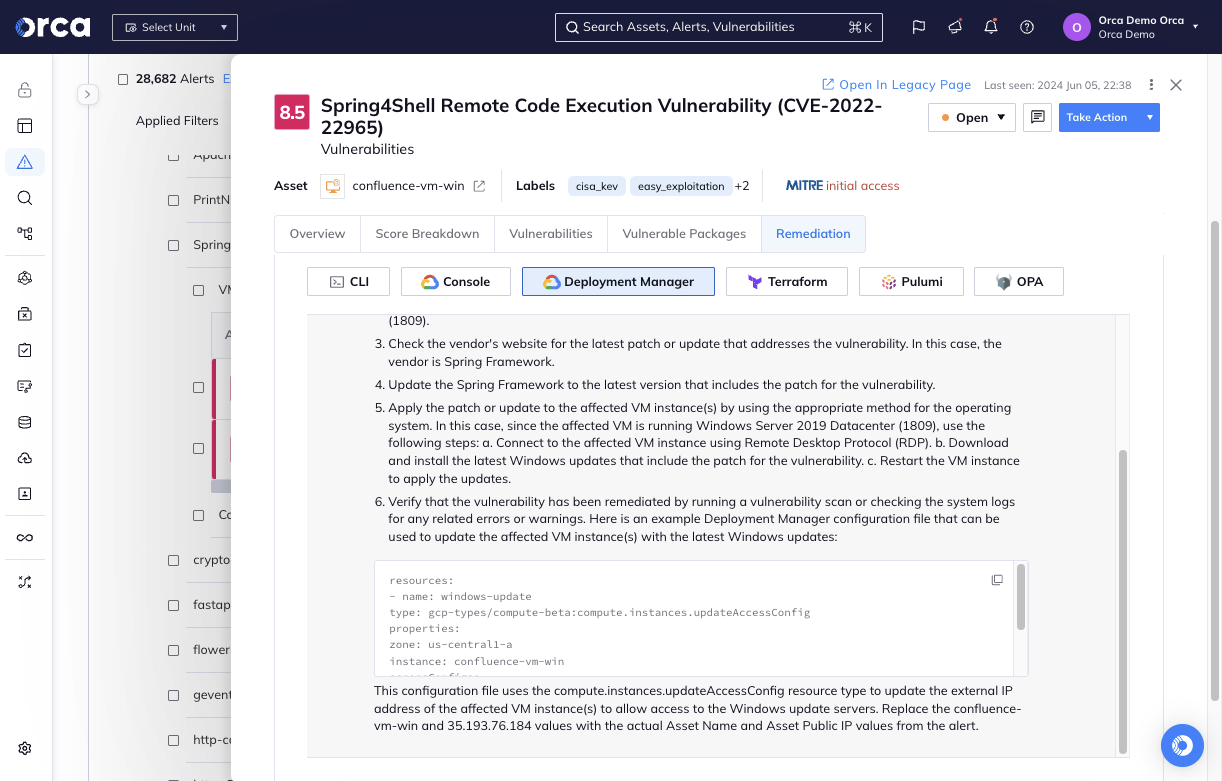
- Automate investigation and response with Orca’s prioritized alerts, which cover all CDR use cases, fully contextualize forensic findings, and provide flexible remediation options.
- Accelerate response with automated workflows that resolve specific risks as soon as they are detected without requiring any manual intervention.
- Leverage Orca’s AI-powered remediation feature to generate high-quality remediation instructions for each alert.
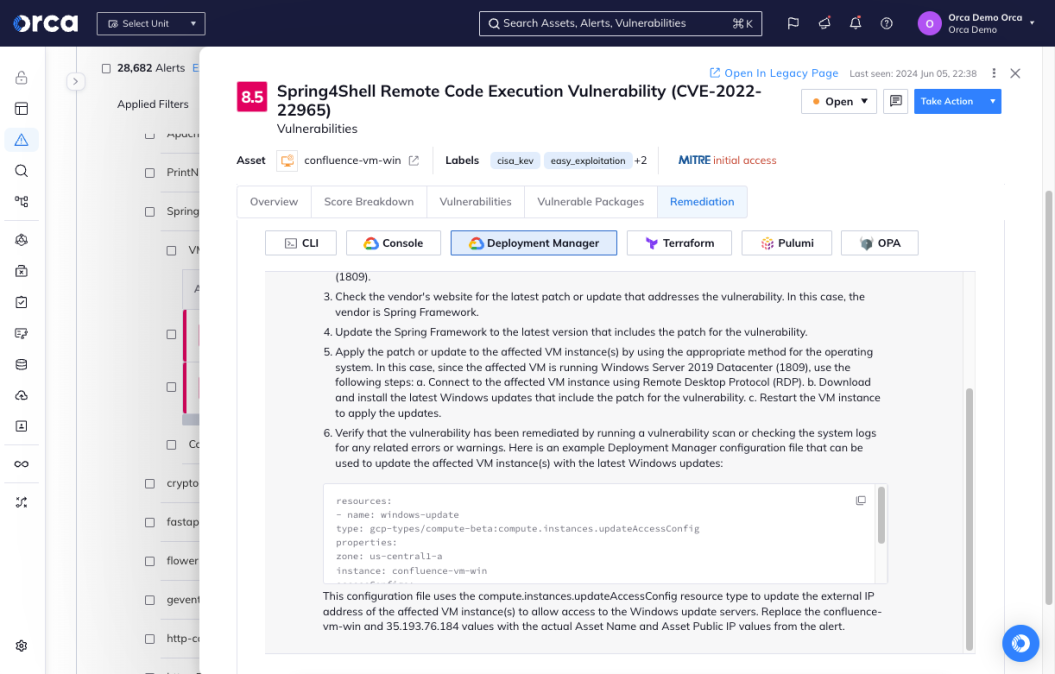
Frictionless workflow integration
Orca offers 50+ third-party integrations to fit seamlessly into your existing tools and workflows:
- Integrate CDR alerts from AWS GuardDuty, Azure Defender for Cloud, and GCP Security Command Center with Orca for comprehensive detection.
- Create and monitor Jira or ServiceNow tickets directly from Orca alerts, enhancing cross-functional collaboration.
- Integrate Orca alerts with SIEM solutions (e.g. Splunk, Sumo Logic, IBM QRadar) for fast investigation and remediation.
New
Gain integrated runtime visibility and security for critical workloads
Integrated with the Orca Platform, Orca Sensor enables you gain powerful runtime visibility, detection, investigation, and prevention for your critical workloads.
- Leverage rich telemetry that deepens the visibility of the Orca Platform with a real-time view of activity, active threats, malicious and suspicious behavior flows, and more.
- Use our extensive library of built-in detections to detect and prevent a wide range of threats, including memory persistence and execution even for fileless attacks.
- Take advantage of runtime protection optimized for cloud-native applications with a flexible, lightweight solution built for the future of preventive and proactive security.
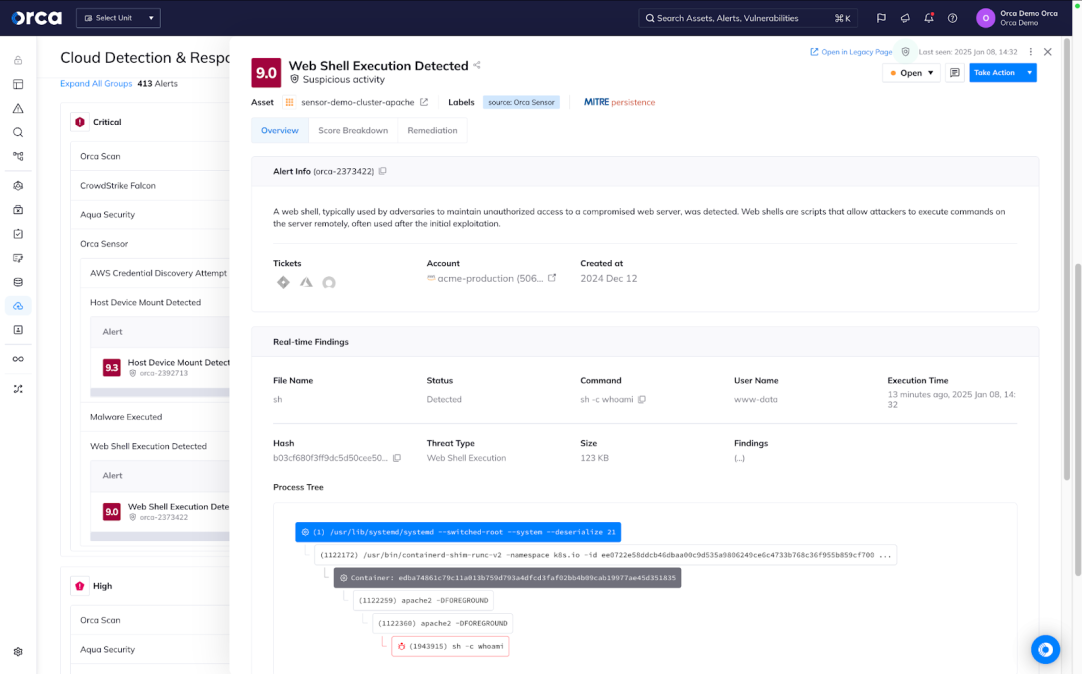
Detect and Respond Swiftly with Orca
Frequently Asked Questions
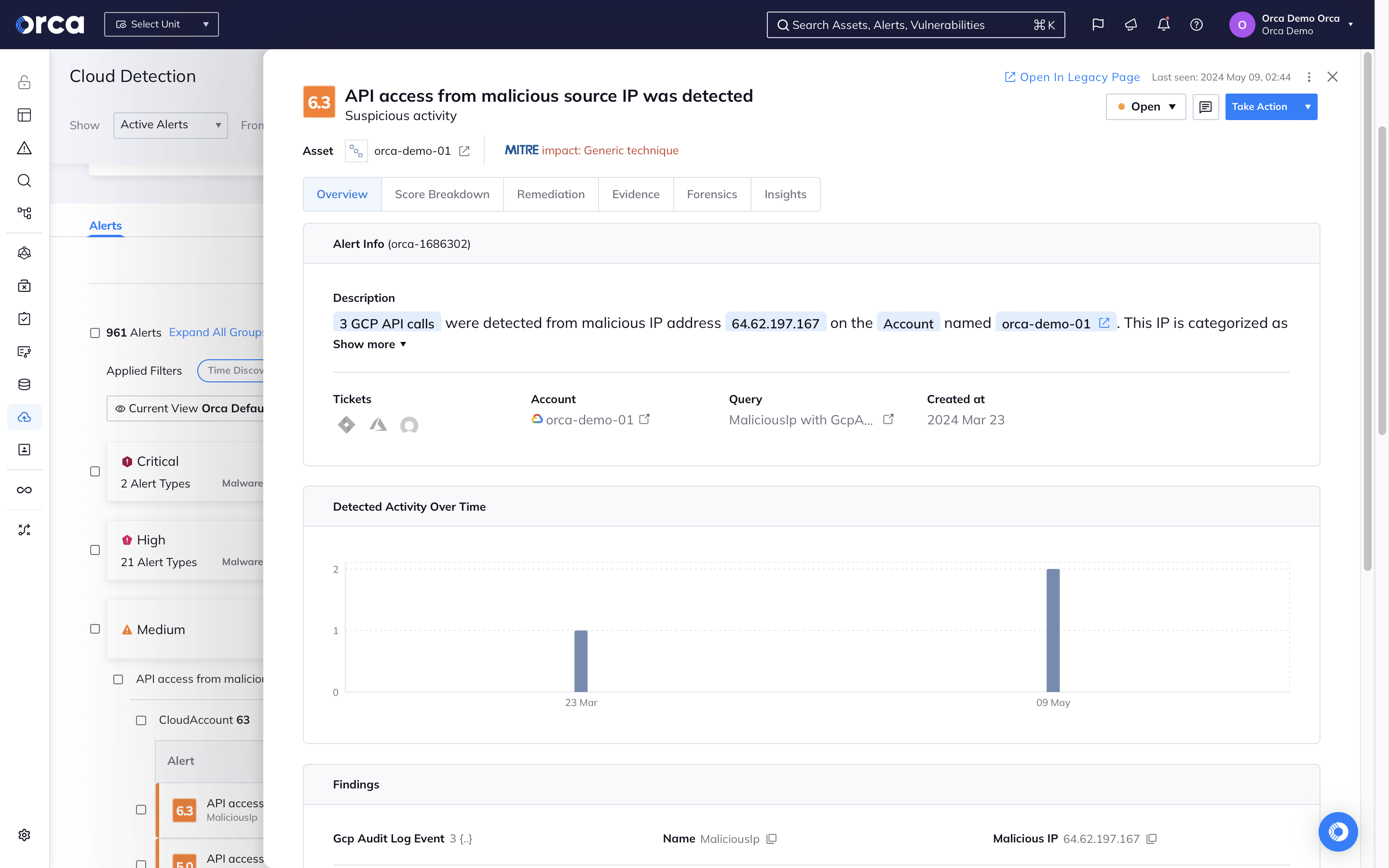
Cloud Detection and Response (CDR) is a branch of cloud security that focuses on detecting active attacks in cloud environments and provides organizations with the information and tools needed for security teams to investigate and respond to these attacks.
The main objective of CDR is to detect cloud attackers who have breached the perimeter controls of cloud resources and applications. By continuously providing security operation center (SOC) and incident response (IR) teams with contextualized data on potential malicious activity in the cloud environment, CDR accelerates investigation and response to cloud attacks.
As organizations increasingly depend on the cloud, many still rely on traditional, on-premises tools to detect and respond to cloud attacks, providing limited insight, missed attacks, and high rates of false positives. CDR helps organizations gain the visibility and awareness of in-progress cloud attacks, accelerate and enhance their response, and limit the scope and severity of incidents.
As with on-premises detection and response, CDR involves four stages:
- Detection: Continuous or frequent monitoring for attacks across cloud services feeds with alerting capabilities.
- Investigation: Review of attack steps, techniques, and timelines, and analysis of available data to determine a needed response to the threat.
- Response: Capabilities that focus on ensuring cloud threats are contained before they can do damage, such as auto-remediation or automatic forwarding to ticketing systems.
- Resilience: Organizations conduct a post-mortem investigation, draw conclusions, and focus on potential remediations based on available data. Following threat mitigation, they investigate the root cause, and take actions—patching, encryption, stricter IAM policies—that harden the cloud environment.
Alternative solutions to CDR include:
- Endpoint Detection and Response (EDR): EDR solutions treat endpoints as potential attack vectors. They use agents to record endpoint activity and identify potential threats, and rely on anomaly detection, machine learning, and other approaches.
- Network Detection and Response (NDR): NDR detects threats by analyzing organizational network traffic. NDRs look for potential threats based on anomalous or unauthorized protocols, port utilization, odd timing and transfer sizes, and more.
- Threat Detection & Response (TDR): TDR typically gathers information most relevant to a current threat. Endpoint TDR tools record data about an identified threat or analyze if an event or process constitutes a threat. Analytical TDRs leverage existing data and apply analytics to identify threats.
- Extended Detection & Response (XDR): XDR platforms detect threats by ingesting endpoint agent data, network level information, and device logs.
However these solutions don’t offer any actual cloud telemetry like CDR does and are siloed tools without any contextual insight into the existing cloud environment risks. Therefore these tools tend to have a higher rate of false positives since they cannot accurately assess the danger of certain actions.
Orca Security Platform provides around-the-clock monitoring of cloud provider logs and threat intelligence feeds. Orca ingests this information and integrates it with our insights into existing risks across the cloud estate and the location of an organization’s most critical assets. This enables Orca to quickly detect potentially dangerous events that require immediate attention.
With Orca’s CDR solution, you can detect, investigate, and respond to in-progress cloud attacks:
- Detect: Get prioritized alerts about events that endanger your most critical assets.
- Investigate: Gain quick insights into security events, including whether they’re malicious and if they threaten your critical assets.
- Respond: Remediate in-progress cloud attacks quickly with automated remediation steps and integrations.