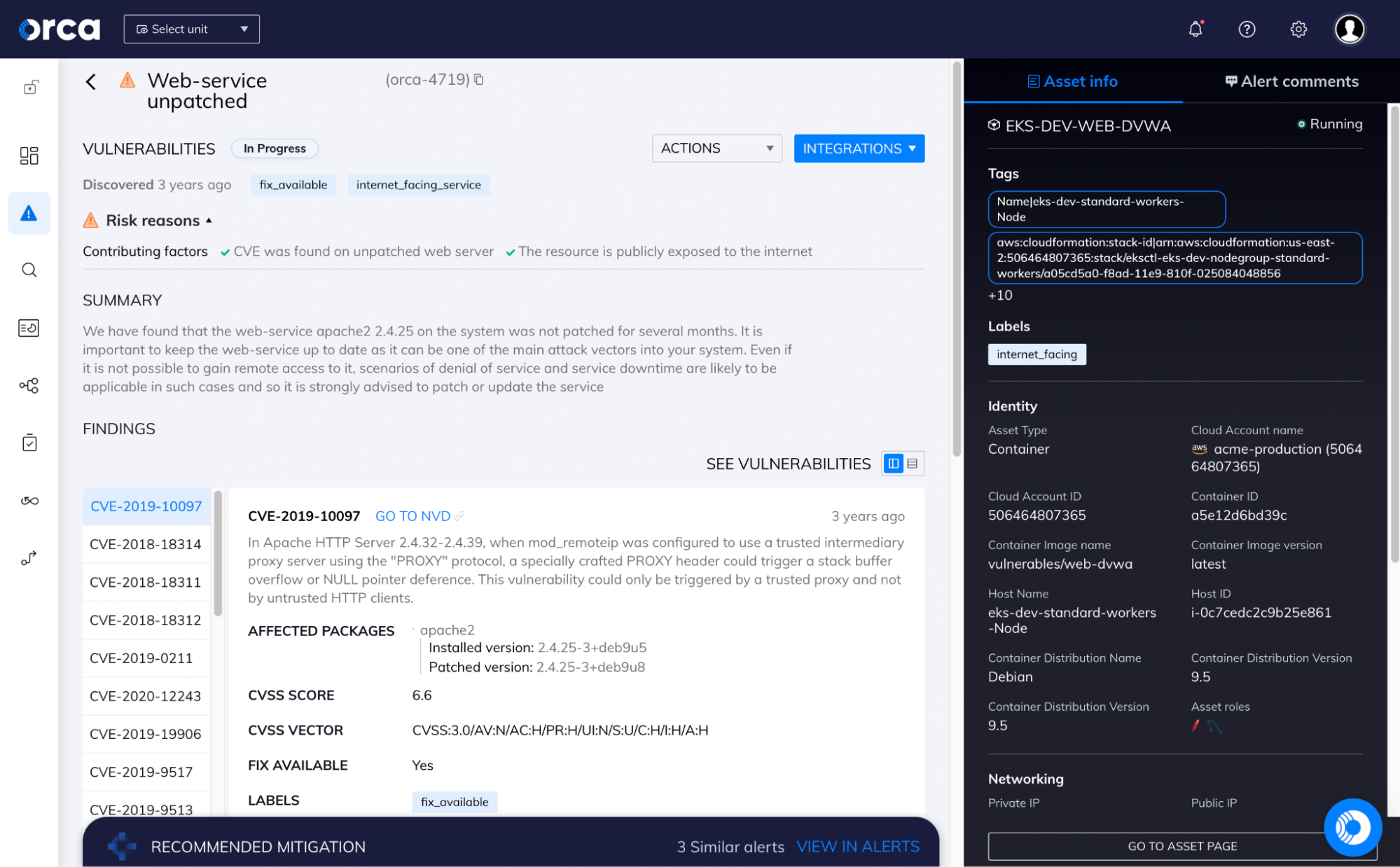
Cloud Vulnerability Management
Detect and fix vulnerabilities in your cloud without requiring a single agent
The Challenge
Agents and Scanners Create Blindspots
Agent-based solutions and vulnerability assessment scanners require tedious deployments and management for each workload, leading to high TCO. Vendors offering a choice between agents and agentless approaches only add to the complexity and often have hidden limits on their ‘agentless’ capabilities. In addition, traditional vulnerability assessment solutions only cover cloud workloads and miss risks in the cloud control plane, such as misconfigurations and overly permissive identities.
Traditional solutions lack context, without insights into cloud configurations and identities, leaving important security gaps.
IT teams need to spend countless hours installing, configuring, and maintaining software and partial deployment of agents and scanners causes serious blind spots.
Security teams often need to burden development and DevOps teams to install agents, creating organizational friction.
Our Approach
Agentless Security Reinvents Cloud Vulnerability Management with Context
Unlike traditional vulnerability assessment solutions, Orca covers every layer of your cloud estate, including cloud workloads and configurations. Orca combines all this information in a Unified Data Model to effectively prioritize risks and recognize when seemingly unrelated issues can be combined to create dangerous attack paths.
Orca collects data directly from your cloud configuration and the workload’s runtime block storage out-of-band.
Within minutes, Orca finds and prioritizes your most critical cloud risks, including vulnerabilities, malware, misconfigurations, lateral movement risks, IAM risks, and sensitive data at risk.
Unlike other solutions, Orca combines workload-deep intelligence with cloud configuration metadata all in one platform.
Orca’s patented SideScanning™ technology is a radical new approach that addresses the shortcomings of traditional vulnerability assessment and agent-first cloud security solutions.
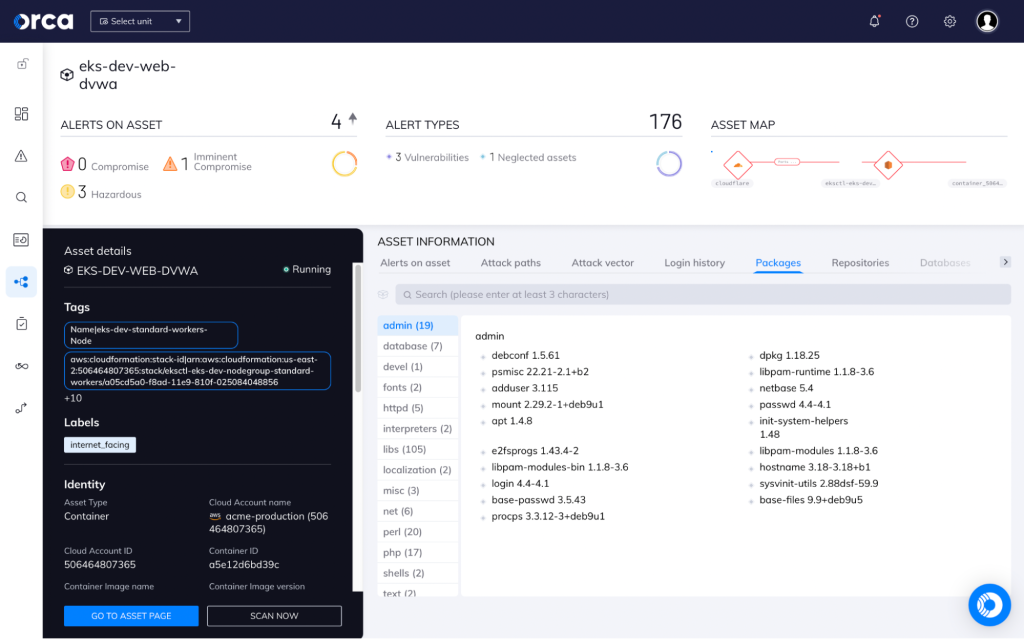
Cloud native vulnerability management
Orca creates a full inventory of your cloud environment and leverages 20+ vulnerability data sources to discover and prioritize vulnerabilities across your entire cloud estate.
- Orca’s workload inventory includes information on OS packages, applications, libraries, as well as versions and other identifying characteristics.
- Unlike other solutions that simply report on the CVSS score, Orca considers the context of cloud assets, their connections and risks, to understand which vulnerabilities need to be addressed first.
- In rapid response situations such as Log4Shell, Orca allows you to quickly identify vulnerable cloud assets and prioritize patching the ones that pose the greatest risk to the business.
- With Orca, you can easily query your entire environment using our modern query builder to understand vulnerabilities, risk level, and context
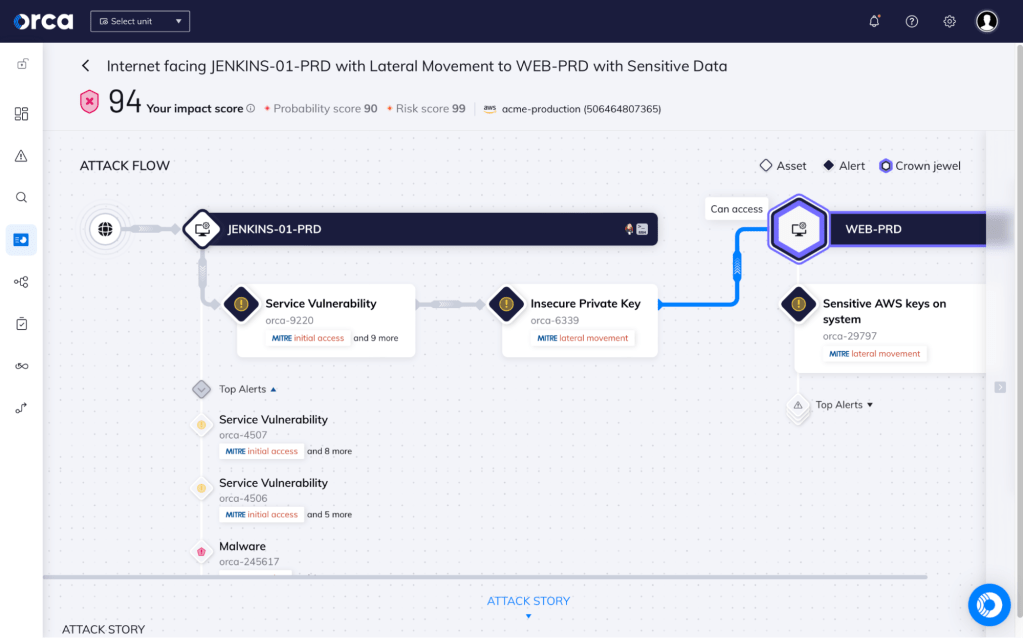
Think about vulnerabilities in terms of interconnected risks
Orca uses Attack Path Analysis to identify dangerous risk combinations that potentially expose the company’s most valuable assets and utilizes an advanced algorithm to assign business impact scores to each path.
- By scoring and prioritizing attack paths, security teams can focus on a much smaller number of dangerous attack paths versus sifting through hundreds of siloed alerts.
- Each attack path is presented in a visual graph with contextual data on the relevant cloud entities (IAM, compute, storage, etc.) and the relations between them.
- For each attack path, Orca shows which risks need to be remediated to break the attack path, further prioritizing issues for remediation if they break multiple paths.
Easily understand how a new CVE impacts your entire environment
Because Orca has a complete view of all your assets, workloads, identities, data and more, you can easily locate a new CVE and its impact on your environment.
- With the From the News widget, Orca automatically surfaces breaking and trending CVEs with instant analysis of their presence and impact on your environment
- Easily query your environment to surface CVE details, as well as interconnected context that adds to risk like Internet exposure or configuration status
- See how vulnerabilities coordinate with other toxic risks using our Attack Path Analysis dashboard

Orca Has You Covered

Demo the Orca Platform
In just 10 minutes, you’ll see how Orca Security can revolutionize your cloud security strategy. Watch a recorded demo from a cloud security expert now.