The security industry spends a lot of ink (or electrons) telling CISOs how to secure their cloud estates, but there is generally an underlying assumption that there is an entire estate to be secured. We often assume that the CISO’s company is either cloud-native, or has aggressively moved into the cloud already. I’m just as guilty of this as anyone; while I never outright say it, the underlying premise of my How to CISO in the Cloud ebooks is certainly aimed at those who already live in the cloud.
But what if you and your company are just getting started in the cloud? You should approach security when you’re just dipping your toes in the water a little bit differently than when you’re already swimming in the deep end. If you’re overly cautious and don’t let anything happen, you risk missing out on the benefits of cloud transformation. If you’re too lax and let everything happen, then you risk setting a standard (or lack thereof) of nonexistent security, and you’ll be pushing uphill for years trying to get security back into conversations about cloud. Let’s look at some concepts you need to be aware of, and conversations you should have, as you start your cloud journey.
Multi-cloud Realities
You’re probably going to hear a lot about “multi-cloud strategies” – the idea that you can build your applications in the cloud in an agnostic way – so you can move from AWS to Azure on a moment’s notice if there is a problem in one or the other. Often, security teams end up leading the doomed charge on multi-cloud advocacy, and I’d recommend staying away from it.
One of the biggest mistaken beliefs that organizations often have as they move to the cloud is that Infrastructure-as-a-Service businesses are really just about shifting costs from up-front capital expenditures to ongoing operational expenses, thus saving money. That can exist, of course, but the best benefits of the cloud are really around agility, and you get the greatest agility when you leverage the tools that cloud providers have. The more you leverage those tools, though, the less that you’re going to be able to simply move a workload (that’s the new word for what used to be called servers, and it’s a little broader) from one cloud provider to another.
That said, you are going to end up multi-cloud. Not in the sense of distributing some workload onto two different platforms. Instead, you’ll end up with different parts of your business solving their problems with different clouds. You might get there by acquisition, when you buy a company that uses different tools. Maybe you’ll end up there when some developers start experimenting with a platform they used at a different company. Or maybe you’ll get a financial incentive to move some work into yet another cloud. However it happens, you’re likely going to end up with a business that spans multiple cloud environments, which will still need to interact with each other, and you’ll need to plan for that.
Visibility and Attack Paths to Better Understand Risks
Unlike in a traditional data center, where you can just walk up and down the frigid rows of server racks, counting your machines and comparing it to the printed spreadsheet on your clipboard, the cloud is a little bit more nebulous. Not only can workloads be “spun up” and “spun down” on a moment’s notice based on demand, the ways in which they interact with one another aren’t as simple as tracing cables inside a rack. Instead, you need to not only be able to identify workloads, but also see how they interact with each other… and the vulnerabilities each present to the other.
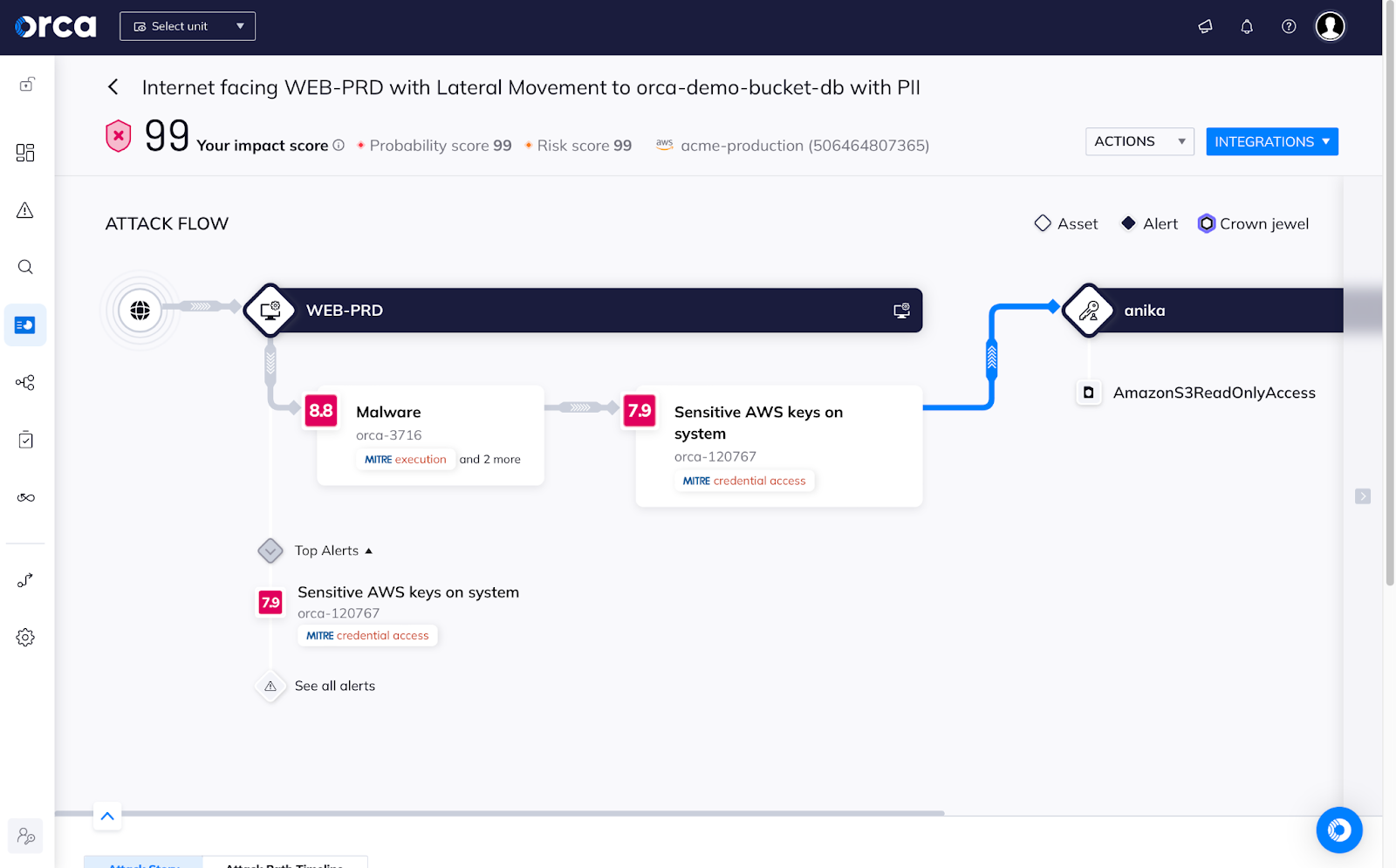
Complete visibility not only gives you a queryable inventory, it lets you understand something deeper: the attack paths that an adversary could take through your cloud environment, as they move from exploiting a vulnerability to using an overly-broad permission to access your core cloud control plane, getting to the sensitive data you thought was locked down. You need to know what those attack paths are, so you can apply thoughtful security controls… or, dare I say, “guardrails”?
Enforcing Cloud Security Controls: Guardrails or Baby Gates?
“Guardrails” is one of the favorite phrases among CISOs these days: enacting policies that keep your business from doing things they shouldn’t. Sometimes, though, we don’t even know enough to set up sustainable guardrails to keep people on a road, and if we get it wrong, then our business partners stop trusting us to be their partners. As we start our digital transformations, sometimes it’s better to aim for “baby gates”: lightweight controls that we expect our business to outgrow, but we’d really like to start with these smaller challenges as we all learn the cloud. Implementing either requires strong coverage – we have to know what we are doing in the cloud so that we can ask if we should be doing that.
For example, maybe we don’t allow PII into the cloud at first. It’s easy to just say that in a policy, but unless we monitor for PII, we shouldn’t expect that rule to last long. Perhaps we have supportability needs, so we should be monitoring for machines that aren’t getting updated. We’d like to monitor which developers have access to make sure that we know what projects are in the cloud. We should certainly expect some cloud projects to be abandoned – so we should be monitoring for wasted resources.
Moving Forward with Your Secure Digital Transformation
If your company is headed into its digital transformation, congratulations! Stay close to what’s going on, so you know what technologies you need to learn more about securing before you’re behind the curve.
Remember this as well: we’re still living in a time where organizations are just beginning their digital transformations, so diving in head first with all-things cloud and all-things cloud security isn’t (and shouldn’t be thought of as) feasible. All you need to do is get a handle on what cloud services you plan to take advantage of, and what solutions are available for keeping those specific aspects of your new cloud estate secure.
If you’re just getting started with your cloud journey and you’d like to be proactive about security from the very start, I recommend checking out a free risk assessment from Orca here.






