Database with Potentially Personal Identifying Information found – Credit Card Numbers
Hazardous (3)
Non-platform specific
About Personally Identifiable Information
Personally identifiable information (PII) is any piece of data which, when used alone or with other related information, can uniquely identify a person. Some examples of PII include name, phone numbers, email addresses, and credit card information.
An organization may contain PII of different user groups, e.g., employees, customers, vendors, or partners. Protecting PII both at rest and in transit is very important.
The first step to protecting PII is identifying where it exists. PII may exist in dedicated database tables that contain sensitive information, as well as other places in the system. For example, an application may write usernames or email addresses of active users to log files; a developer may hardcode partner phone numbers in source code; plaintext credit card numbers may mistakenly get written to the table that contains transactional records.
Creating an inventory of the PII you handle is important, especially if you process financial information, like credit card numbers. Once you have identified all your PII, it’s important to create dedicated, secure data stores for it. Never store it as plaintext or directly on cloud assets like VMs or containers.
Cloud Risk Description
Credit card numbers are found on a cloud asset. If this information is exposed to cybercriminals, it can lead to financial loss for the exposed individuals as well as your organization via regulatory fines.
How Can Orca Help?
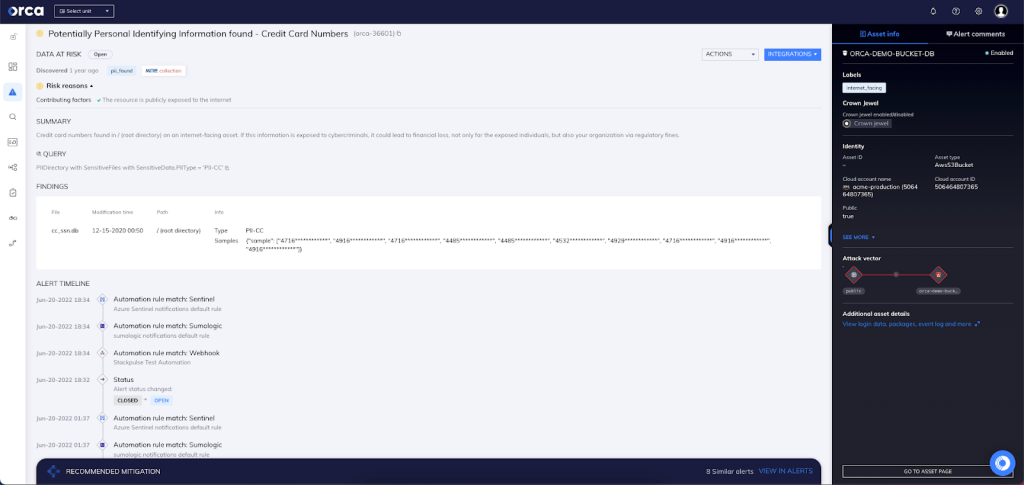
Orca detects sensitive data at risk across both the workload and control plane and, if found, dispatches an alert along with remediation steps and exact data location (see screenshot). Since leakage of such confidential data is also subject to security compliance regulations (and large fines), the alert is prioritized so that security teams will know to immediately remediate the issue.
Recommended Mitigation Strategies
-
Use cryptographically strong encryption algorithms to encrypt PII, both at rest and in transit.
-
Store PII in purpose-built, secure data stores.
-
Follow the principle of least privilege when granting access to data stores that contain credit card numbers or any other PII.
-
Use tools like AWS Comprehend to detect the presence of PII and remove or encrypt the data accordingly.
-
Never store sensitive information on the file system, especially not as plaintext.
-
Never hardcode any PII in your applications’ source code.
Useful Links
- PCI rules for storing credit card numbers: https://www.globalpaymentsintegrated.com/en-us/blog/2019/11/25/pci-rules-for-storing-credit-card-numbers-in-a-database
- Challenges of keeping PII secure in the cloud: https://community.idera.com/database-tools/blog/b/community_blog/posts/the-challenge-of-keeping-pii-secure-in-the-cloud
- AWS – Detecting PII: https://docs.aws.amazon.com/comprehend/latest/dg/how-pii.html
- Securing PII: https://digitalguardian.com/blog/how-secure-personally-identifiable-information-against-loss-or-compromise
- Protecting PII under GDPR: https://www.csoonline.com/article/3215864/how-to-protect-pii-under-gdpr.html
Orca Security, the cloud security innovation leader, provides cloud-wide, workload-deep security and compliance for AWS, Azure, and GCP - without the gaps in coverage, alert fatigue, and operational costs of agents.
