On September 21st 2022, the Strengthening Agency Management and Oversight of Software Assets Act was introduced in the US Senate and approved by the Senate Homeland Security and Governmental Affairs Committee on September 28th. The act states that each US agency “shall complete a comprehensive assessment of the software entitlements and software inventories of the agency”. As a consequence, all US federal agencies are required to provide a list of all software used or under license within one year after the date of enactment, i.e. by September 28th, 2023.
They will need to report this complete Software Bill of Materials (SBOM) to the following institutions:
- Comptroller General
- Committee on Homeland Security and Governmental Affairs of the Senate
- Committee on Oversight and Reform of the House of Representatives
Another critical element is that this initial assessment will include a before and after report in order to demonstrate ‘completeness’. This is certainly not trivial and will require significant effort from agency CIOs, CFOs, CIOs, procurement officers, and agency General Counsel.
How to comply with the Strengthening Agency Management and Oversight of Software Assets Act
According to the text of the legislation, the bill requires federal agencies to:
- Deliver “comprehensive” software assessments: List their largest software suppliers, costs and volumes of software purchased, and software that is being paid for but not deployed. This includes “a comprehensive, detailed accounting of any software deployed for the agency as of the date of the comprehensive assessment”.
- Develop plans to consolidate software licenses: Decide how to move towards consolidating software licenses and adopt agency-wide enterprise license agreements. Those plans would include strategies for measuring actual software usage, priorities for converting to enterprise licenses, and cost estimates to moving toward enterprise, open-source, or other licenses that “do not restrict the use of software by the agency, and any projected cost savings or efficiency measures.”
- Await OMB proposals on reducing costs and improving software performance: Give the Office of Management and Budget two years to submit a strategy to the Senate Homeland Security and House Oversight and Reform committees that includes proposals to show opportunities to leverage government procurement policies and practices to increase interoperability of software contracts to reduce cost and improve performance.
Meeting asset inventory requirements
The initial step agencies should take in their efforts to meet the bill’s requirements is to aggregate and review contracts and licensed subscriptions. However, conducting an asset inventory can be a complex task and requires collecting system level data on what software packages are installed as well as associated usage levels.
Creating an inventory of on-premise software
Organizations can use the Lightweight Directory Access Protocol (LDAP) or Microsoft’s Active Directory (AD) to collect basic IT Asset Management (ITAM) information and although not necessarily comprehensive of the software version level, it does provide insight. Also, directory services like AD and LDAP are typically the first place an auditor looks for determining inventory.
To meet the requirements of this Act, agencies are likely going to require use of an asset inventory tool with a software inventory module or plugin. The challenge here is that the devices need to be on and connected for the (yes, seriously) asset inventory software to collect the required data. When combined with information from the directory services, it should provide adequate insight on what software is installed and on what device. This approach covers hardware assets that are powered on and connected to a network.
Creating an inventory of software in your cloud
The next challenge is to address the cloud services in use at the agency (and department level). Although moderately straightforward in simple environments, collecting this information can quickly become complicated when there are multiple accounts across several cloud service providers. Adding to this complexity are cloud features such as containers and auto-scale groups that may have different features and packages installed and are only viewable or accessible when turned on and in a connected state. any of which are ephemeral in nature. This creates an operational and compliance burden when complying with the act.
Combining this cloud software inventory with the contract, licensing, subscription, billing and non-cloud inventories, provides a holistic view of all the agency’s software and associated assets. Now the agency can categorize based on costs and volume, which is a further requirement of the Act. This review also addresses the requirement of accuracy and completeness of the inventory as well as compliance with the software in use and under license by the agency.
Using Orca Security to complete your cloud SBOM
The FedRAMP ReadyOrca Cloud Security Platform can be a valuable partner in completing your cloud SBOM (Software Bill of Materials), since it is able to scan multi-account, multi-cloud ecosystems without requiring a single agent. Orca creates a full inventory of workloads across your cloud estate spanning AWS, Azure, Google Cloud, Alibaba Cloud, and Kubernetes. This inventory includes information on OS packages, applications, libraries, as well as versions, author, description, and other identifying characteristics.
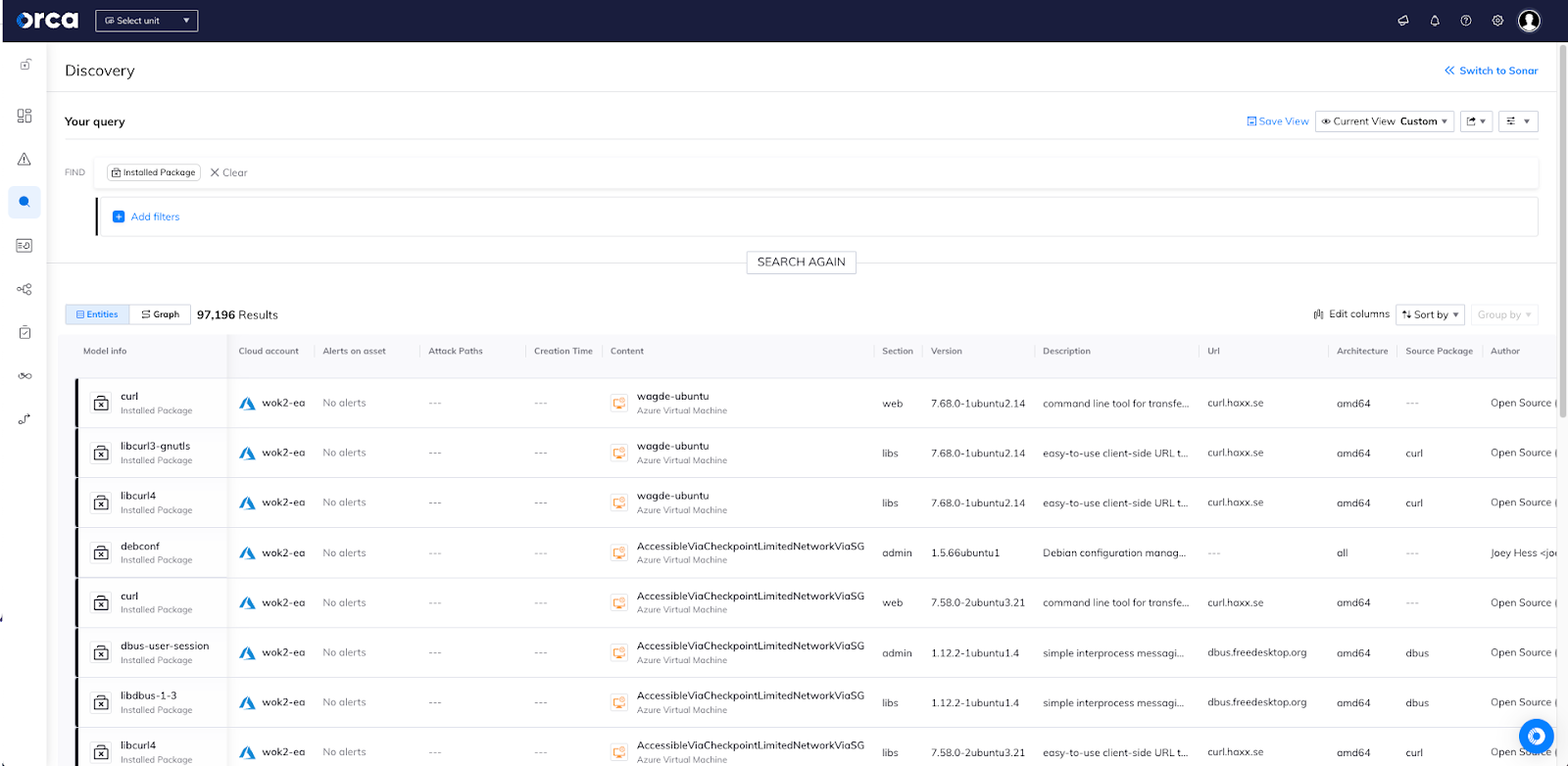
Orca’s query system enables easy identification and location of installed software packages, both across the entirety of the multi-cloud environment, as well as within a particular cloud account or asset. Orca also allows you to see a full list of packages installed on a particular asset, as seen in the screenshot below.
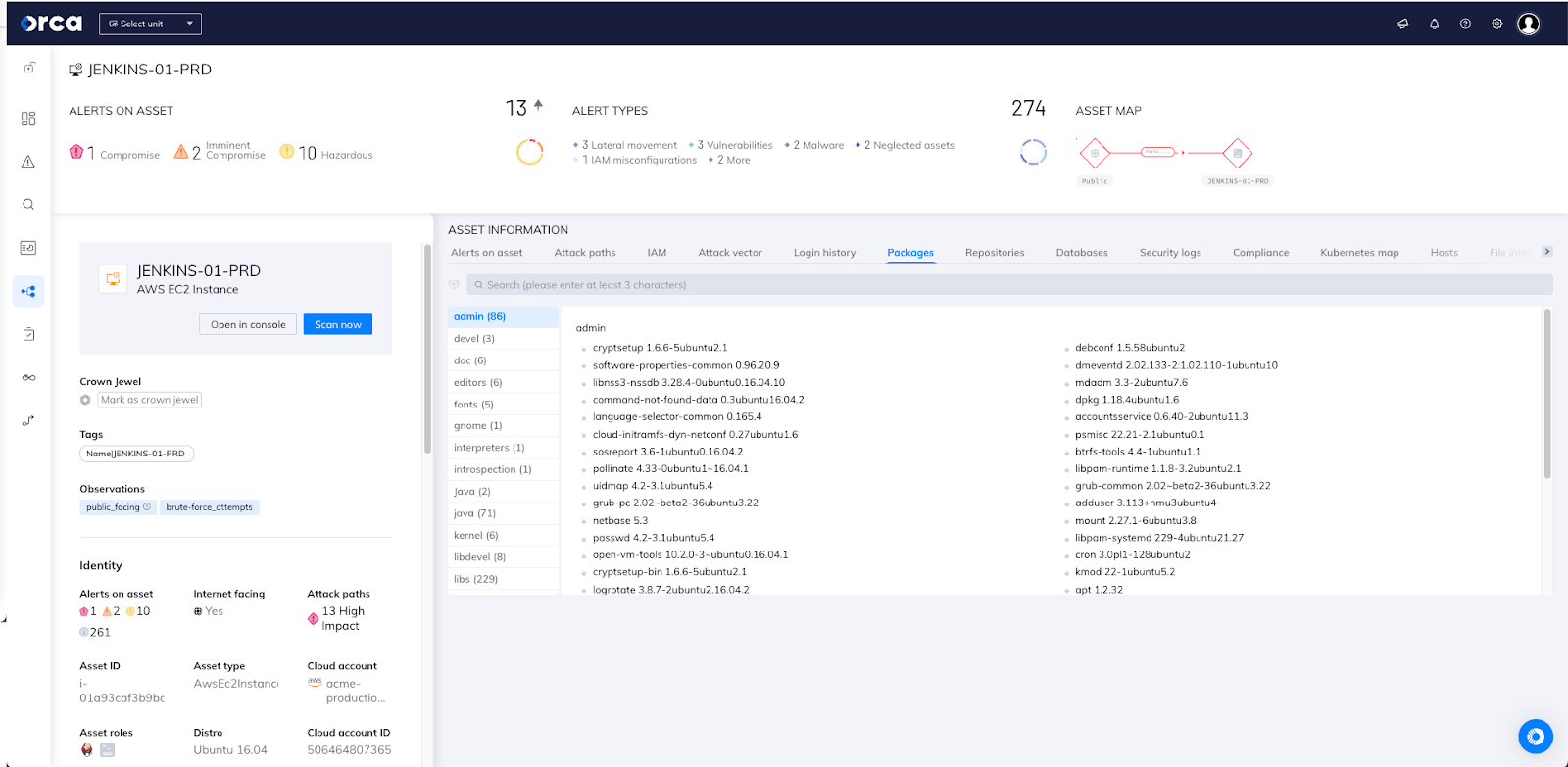
The continuous asset inventory that the Orca platform delivers serves as a foundation for comprehensive, centralized visibility of an entire cloud estate, without blind spots and without the need for a single agent to be deployed. Within minutes, Orca finds and prioritizes your most critical cloud risks, including vulnerabilities, malware, misconfigurations, lateral movement risks, API risks, IAM risks, and sensitive data at risk.
The Orca Cloud Security Platform is designated as FedRAMP Ready, and is listed on the FedRAMP Marketplace, the official online repository for FedRAMP Cloud Service Offerings (CSOs).
Get 100% visibility with Orca Security – Free Cloud Risk Assessment
As opposed to agent-based solutions that cover less than 50% of cloud assets due to cumbersome and partial deployments, the Orca platform is agentless and instantly scans each cloud asset, providing 100% visibility and ensuring that every asset is included in the inventory list.
Read more about how Orca offers cloud security and compliance for government cloud estates and provides 100% visibility and coverage while eliminating the blind spots, high TCO, organizational friction, and performance hits associated with traditional solutions.If you would like to try out Orca and get a complete list of assets and software in your cloud environment, sign up for our free risk assessment.







