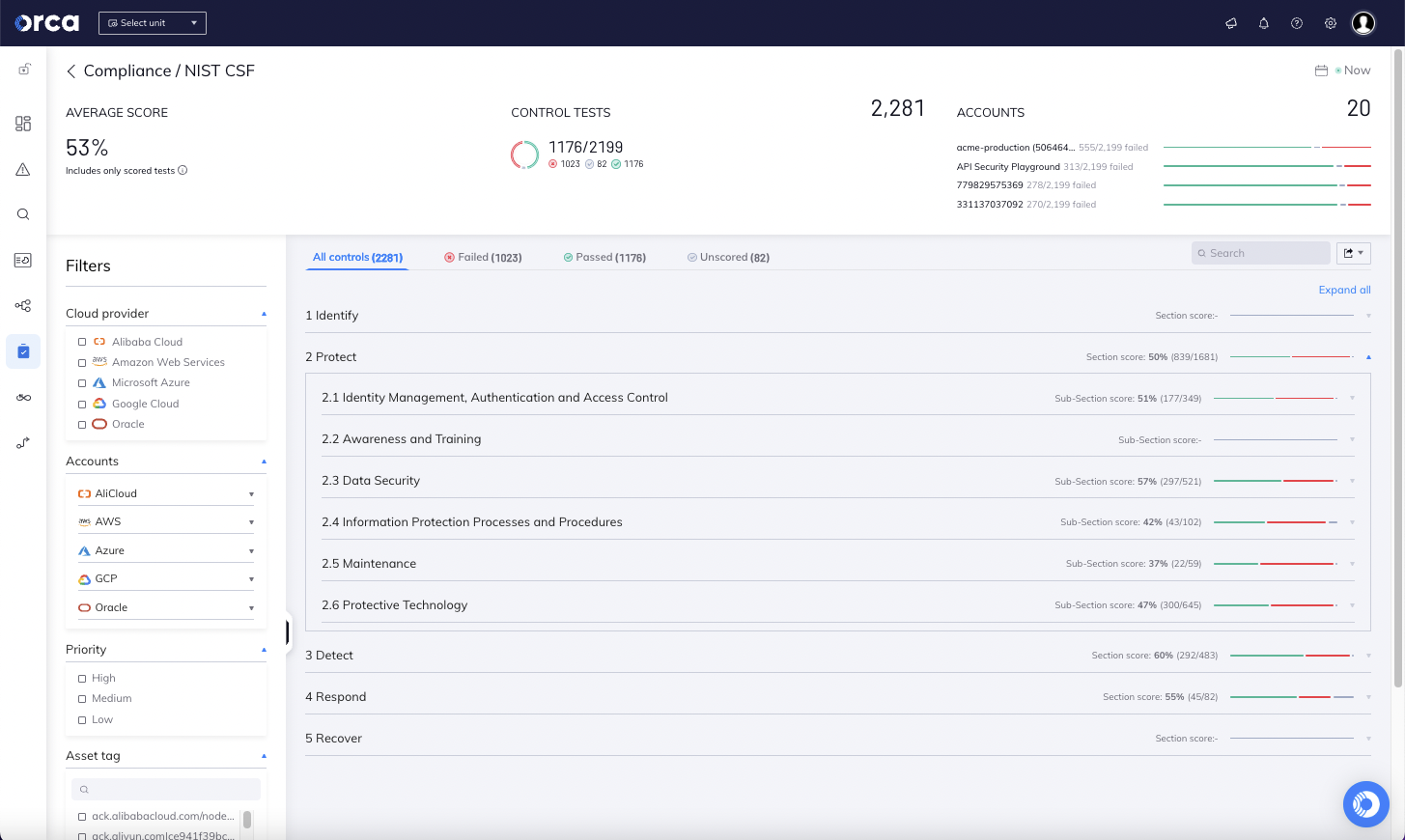
Orca Security is excited to announce that our Cloud Security Platform has achieved the FedRAMP Ready designation, which indicates the offering has the capability to serve the US Federal Government, its agencies and contractors with a fully agentless cloud security platform for Federal Risk and Authorization Management Program (FedRAMP) environments. The FedRAMP Ready designation attests to the robust security capabilities of the Orca platform since the federal program is generally considered one of the strictest security certifications. The Orca Platform is now listed on the FedRAMP Marketplace as FedRAMP Ready, the official online repository for FedRAMP Cloud Service Offerings (CSOs).
To achieve a FedRAMP Ready designation, a SaaS provider must undergo a rigorous independent security capabilities assessment conducted by a third-party assessment organization (3PAO) to ensure that it complies with NIST Special Publication (SP) 800-63B, and implements strong security controls for storing government data.
“We are thrilled to have achieved FedRAMP Ready status and look forward to making a valuable contribution towards securing federal cloud environments,” said Avi Shua, CEO of Orca Security. “Our comprehensive Cloud Security Platform offers wide and deep visibility into the entire cloud estate, is fast and frictionless to deploy, and surfaces and prioritizes risks across cloud workloads, configurations, and identities – without requiring a single agent. We are excited to be able to offer our platform while adhering to the stringent security and privacy requirements set by the US government.”
What is FedRAMP?
FedRAMP, which stands for Federal Risk and Authorization Management Program, was created in 2011 by the US government and outlines requirements for cloud products and services around authorization, security assessment, and continuous monitoring. The goal of this program is to enable the Federal Government to leverage the benefits of the cloud, while maintaining the highest level of security and data protection. Since the initial launch of FedRAMP, there have been several Executive Orders specifying and requiring federal agencies to transition from legacy technologies to cloud services, including improving security.
Orca Security: Agentless FedRAMP Ready Cloud Security Solution
With the FedRAMP Ready designation, Orca Security has the capability to provide a fully agentless cloud security platform for FedRAMP environments. An agentless solution has significant advantages over agent-based solutions since it avoids the additional overhead needed to install and maintain agents, the organizational friction this can cause, and the performance overhead of installing plugins on workloads.
Another important reason why agent-based solutions are not sufficient in FedRAMP environments is because they only provide partial coverage. As organizations scale, they need to ensure that these security solutions are deployed on all new instances, VMs, containers, etc. In a dynamic environment such as the cloud, it is simply impossible to install agents on every workload. In fact, our experience shows that coverage of agent-based solutions is typically not more than 50%. This means that half of the assets in the cloud are completely unmanaged.
As opposed to other platforms that “add-on” siloed tools to expand their capabilities and often require the use of separate consoles, Orca was built as one unified solution from the start. With this Unified Data Model, Orca has deep contextual data of the entire cloud estate, and is uniquely positioned to quickly understand which risk combinations create dangerous attack paths to mission data. This allows security teams to immediately focus on their top threats instead of wasting time having to sift through hundreds of low priority and possibly duplicate alerts before even getting to think about remediation.
“As we survey the federal cloud landscape we see an IT community wrestling with the practices and paradigms of agent-based security that was not built for the cloud. Our identification of these challenges drove our investment in Orca Security as a technology partner with an eye towards FedRAMP certification. Orca’s comprehensive cloud security platform offers an “outside the box” approach to provide complete visibility across cloud provider platforms that deploys in minutes and achieves scalable, context-aware risk identification and prioritization across cloud-native assets – all without requiring a single agent. With that in mind, it is with great anticipation that we look forward to the finalization of Orca’s FedRAMP certification, which we see as a catalyst to the realization of successful IT modernization within the federal government.”
Shawn Kingsberry, VP of Cyber Innovation at SAIC
Benefits of a Fully Agentless Cloud Security Platform
In contrast, the Orca Cloud Security Platform is fully agentless, providing the following major benefits:
- Low TCO: Fast time-to-value with a deployment process of under 30 minutes.
- Full coverage: 100% visibility into the entire FedRAMP environment, including VMs, containers, Kubernetes, serverless, storage, functions, databases, identities, and APIs.
- Comprehensive: Discover not just security concerns like traditional CVE vulnerabilities, but also identity and access issues, malware, misconfigurations, sensitive data at risk, attack paths, API risks, code security, compliance status and risk posture, all presented in a single view.
- Context-aware: All data from workloads, configurations, and identities is stored in a Unified Data Model and operated from a single console, giving Orca deep contextual insights into your entire cloud estate. This allows Orca to quickly uncover the risk combinations that create dangerous attack paths to your crown jewels, saving your security team valuable time sifting through endless alerts.
How Does Orca Help Secure Federal Cloud Environments?
The Orca Cloud Security Platform enables government organizations and its contractors to identify and address cloud risks that could endanger mission critical data stored in the cloud. Orca scans deep and wide, including all layers of every cloud asset, and across the entire software development life cycle, from development to production.
The Orca Platform helps government agencies in the following key areas:
#1. Full, Multi-Cloud Inventory
To adequately evaluate cloud risk, an agency needs to first have full visibility into their cloud inventory. Simply stated, if you don’t know what you have, how can you protect it? While this may seem pretty straightforward, current FedRAMP cloud security solutions are mainly agent-based which means that they cannot provide a full inventory of all cloud assets in the environment.
Orca’s SideScanning™ technology covers 100% of assets and delivers a full inventory across multiple cloud platforms, detailing all installed OSes, software packages, and versions, without requiring anything to be installed in the federal cloud environment. Not only does this help security teams to secure their cloud assets, it also helps federal government agencies comply with the recently approved ‘Strengthening Agency Management and Oversight of Software Assets Act’ that requires each agency to undertake an inventory of all software used by the government.
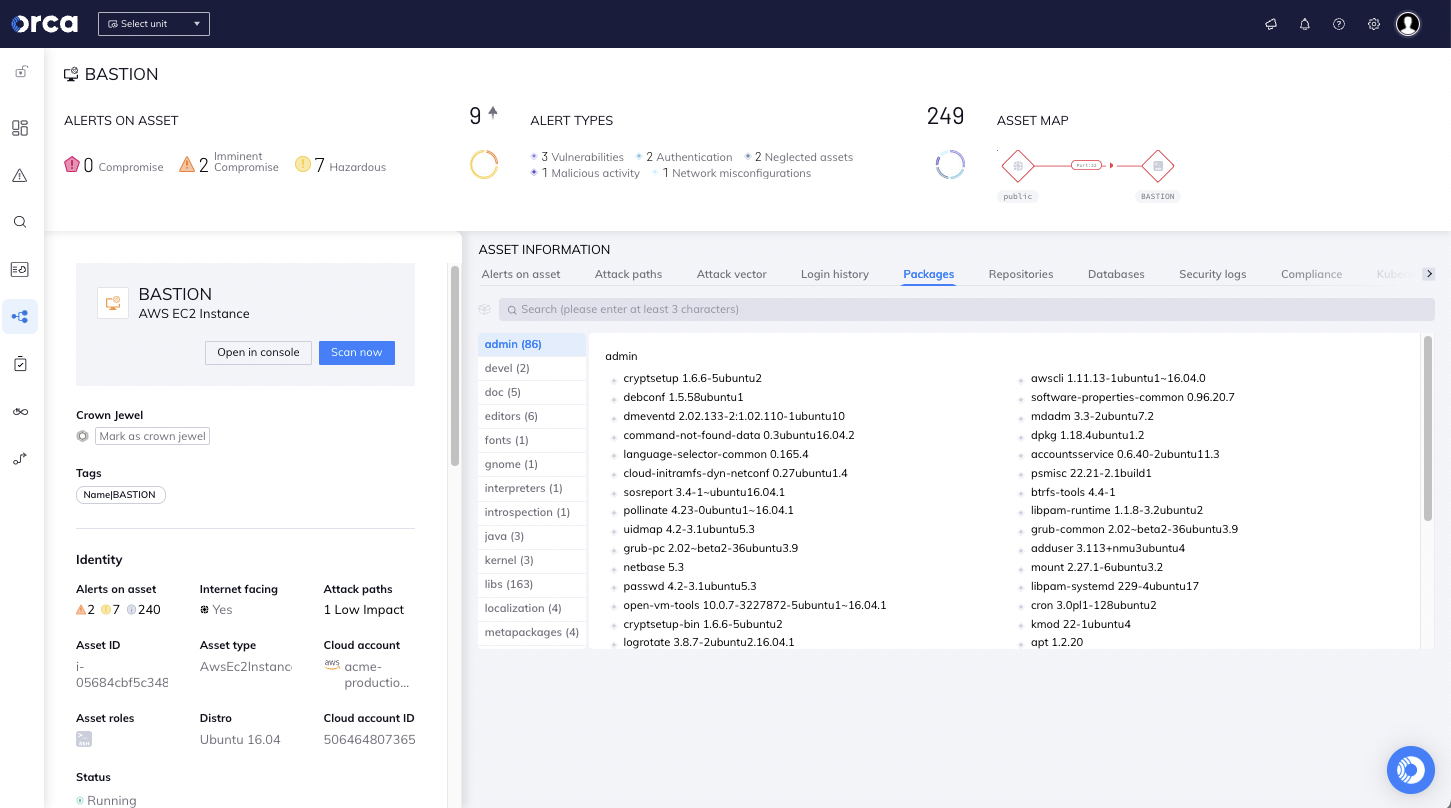
#2. Vulnerability Management
Another key, and perhaps critical, component is vulnerability identification. This not only includes CVEs, but also misconfigurations, identity and access issues, sensitive data protective controls, and compliance concerns. When taken in combination with inventory and access, federal agencies can better determine the totality of risk across the cloud estate, which vulnerabilities create the most risk and must be addressed first. Having this view empowers stakeholders to make data driven risk management decisions based on the potential likelihood and impact of a vulnerability being exploited, essentially reducing cloud risk.
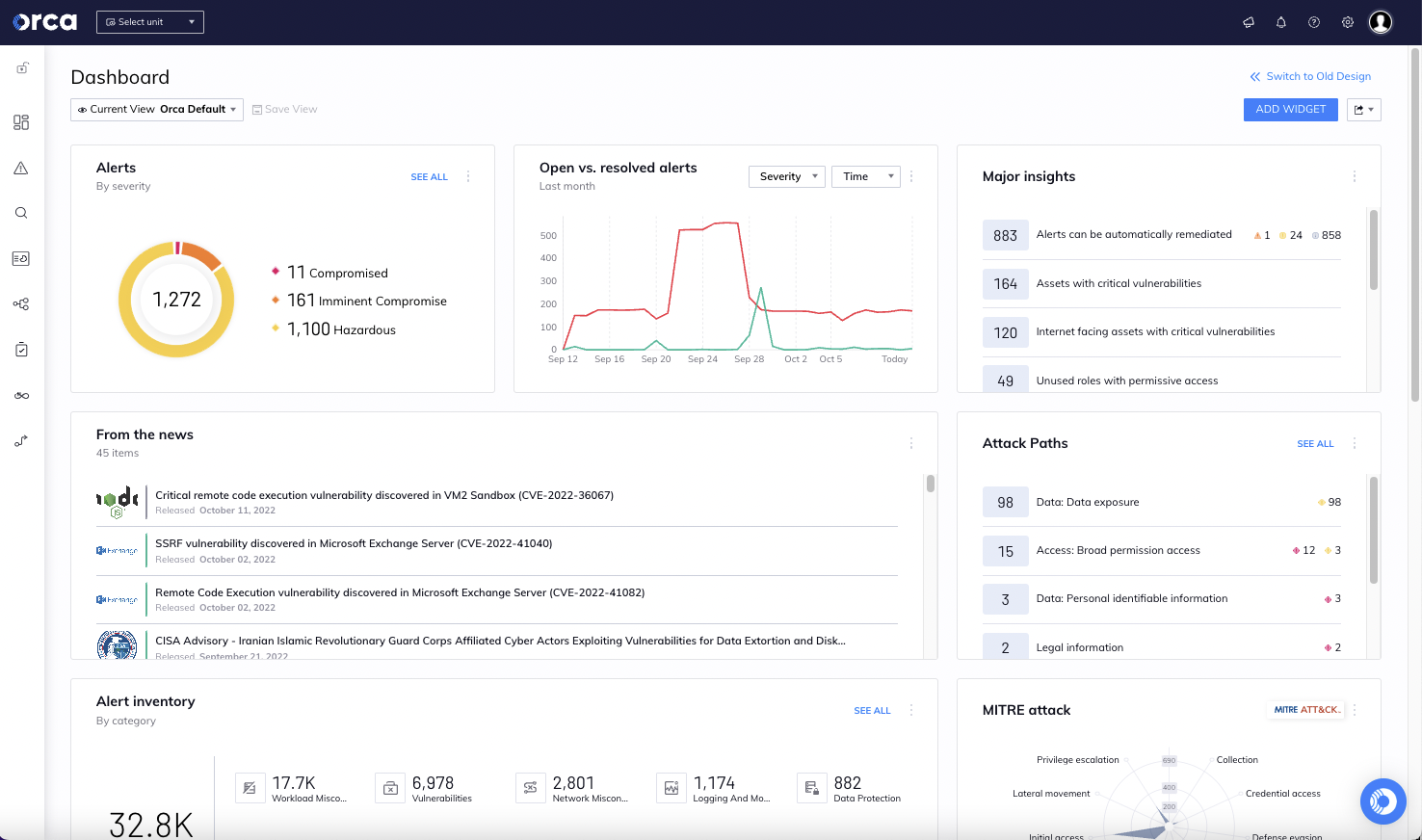
#3. Attack Path Analysis
With Orca’s attack path analysis and prioritization capabilities, security teams no longer need to sift through hundreds of siloed alerts to find out which issues need to be fixed and in what order, but instead can focus on a much smaller amount of prioritized attack paths, or combinations of alerts, that endanger the organization’s most critical assets.
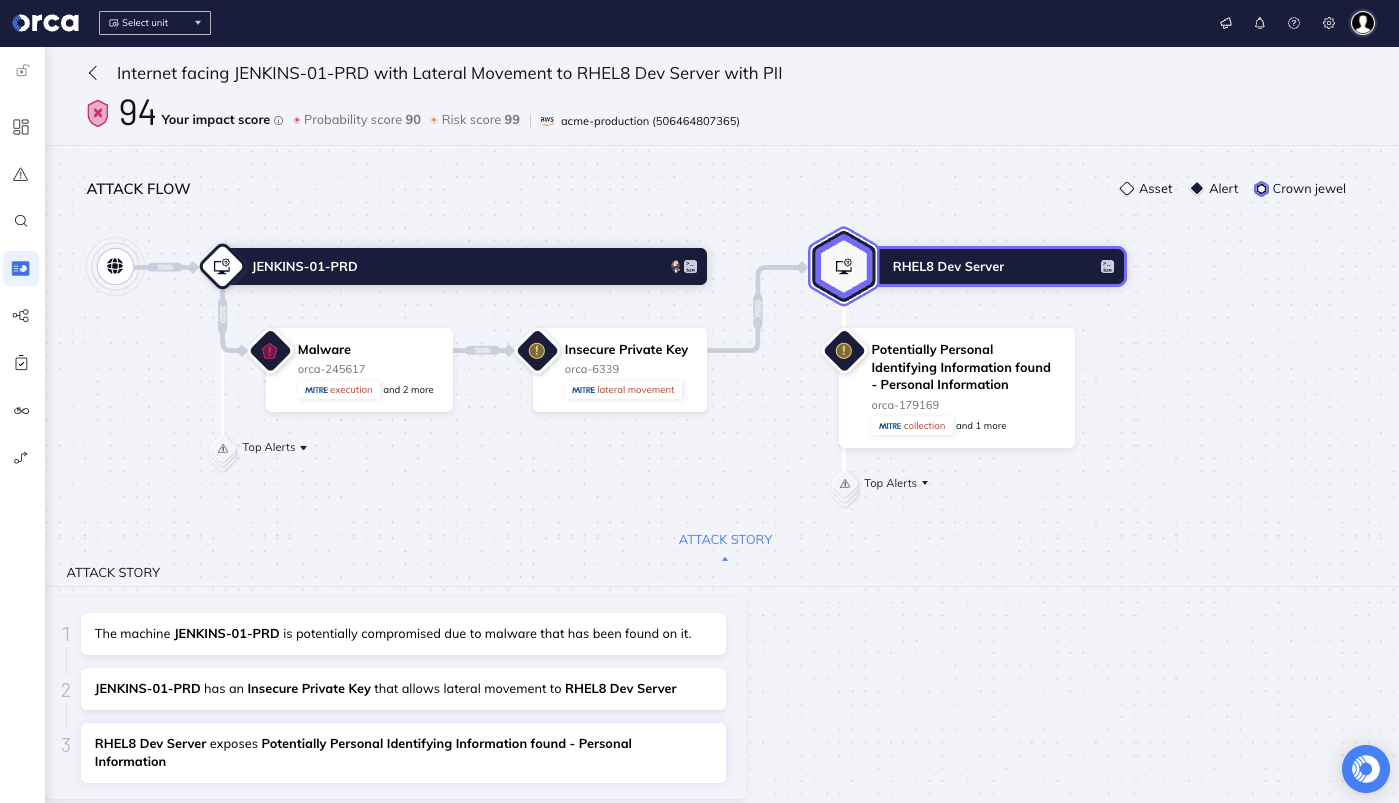
Orca provides a visual representation of each attack path, along with detailed information on each attack vector. Each attack vector in the path includes tags for easy identification and filtering, including applicable MITRE ATT&CK categories.
#4. Continuous Monitoring and Security Analytics
A key tenant in FedRAMP estates and essential to securing the mission is continuous monitoring. Supported by NIST SP800-137 Information Security Continuous Monitoring (ISCM) for Federal Information Systems and Organizations, this provides the framework and guidance for ongoing assurance that organizational risk tolerance is aligned with implemented and planned controls.
Further, in the event that gaps in security coverage are identified, continuous monitoring provides the basis for what is necessary to address risk concerns and how quickly they need to be addressed. Additionally, this presents a large challenge for agencies and government contractors given the extensibility and dynamic nature of cloud ecosystems.
Typically, organizations approach continuous monitoring through an aggregation of legacy agent-based tools that are fed into a SIEM or similar type of dashboard. Although this approach meets compliance requirements for NIST SP800-137 and FedRAMP, it requires meaningful time and effort for security and compliance teams to manage. Moreover, the time and effort needed to manage and maintain continuous monitoring distracts security and compliance teams from issues that may lead to a loss of data confidentiality, network exposure or compliance issues.
The Orca Cloud Security Platform offers continuous monitoring through its Cloud Detection & Response capabilities, which provide 24×7 monitoring of cloud provider logs and threat intelligence feeds. By uniquely combining this information with Orca’s insights into existing risks found in cloud workloads and configurations, and the location of the company’s most critical assets, Orca quickly recognizes which events are potentially dangerous and require immediate attention.
#5. Zero Trust Policy
On January 26, 2022 the Executive Office of the President – Office of Management and Budget (OMB) issued the ‘Memorandum for the Heads of Executive Department and Agencies’ (M-22-09) establishing a zero trust architecture (ZTA) and requiring that agencies meet specific cybersecurity standards and objectives by 2024. This is being done as part of the broader US government initiatives to improve the security of the federal government and its supply chain. Additionally, Zero Trust Architecture was included in CISA’s Cloud Security Technical Reference Architecture publication.
Orca helps government agencies and contractors on their Zero Trust journey by alerting when cloud configurations and entitlements do not adhere to the principle of least privilege as well as providing guided IAM remediation to advise the optimal policy changes that need to be made to achieve the greatest improvement in IAM posture. In addition, Orca identifies when user accounts have not been used for a certain time period and advises to remove the accounts.
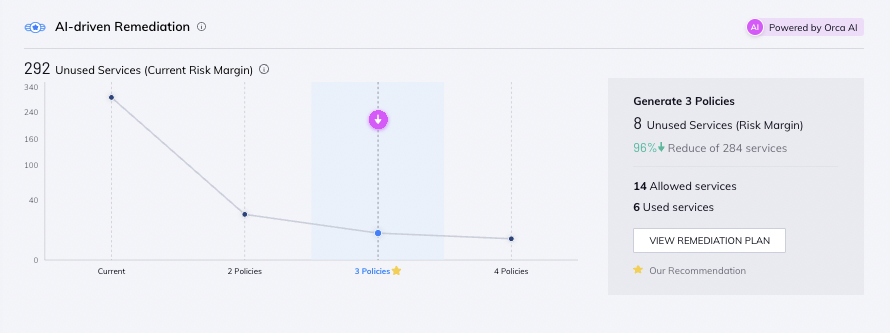
#6. Cloud Compliance
Whether addressing the Executive Order on Improving the Nation’s Cyber Security (Executive Order 14028), or ensuring adherence to relevant CIS benchmarks, the Orca Cloud Security Platform delivers continuous compliance that is key for securing federal missions.
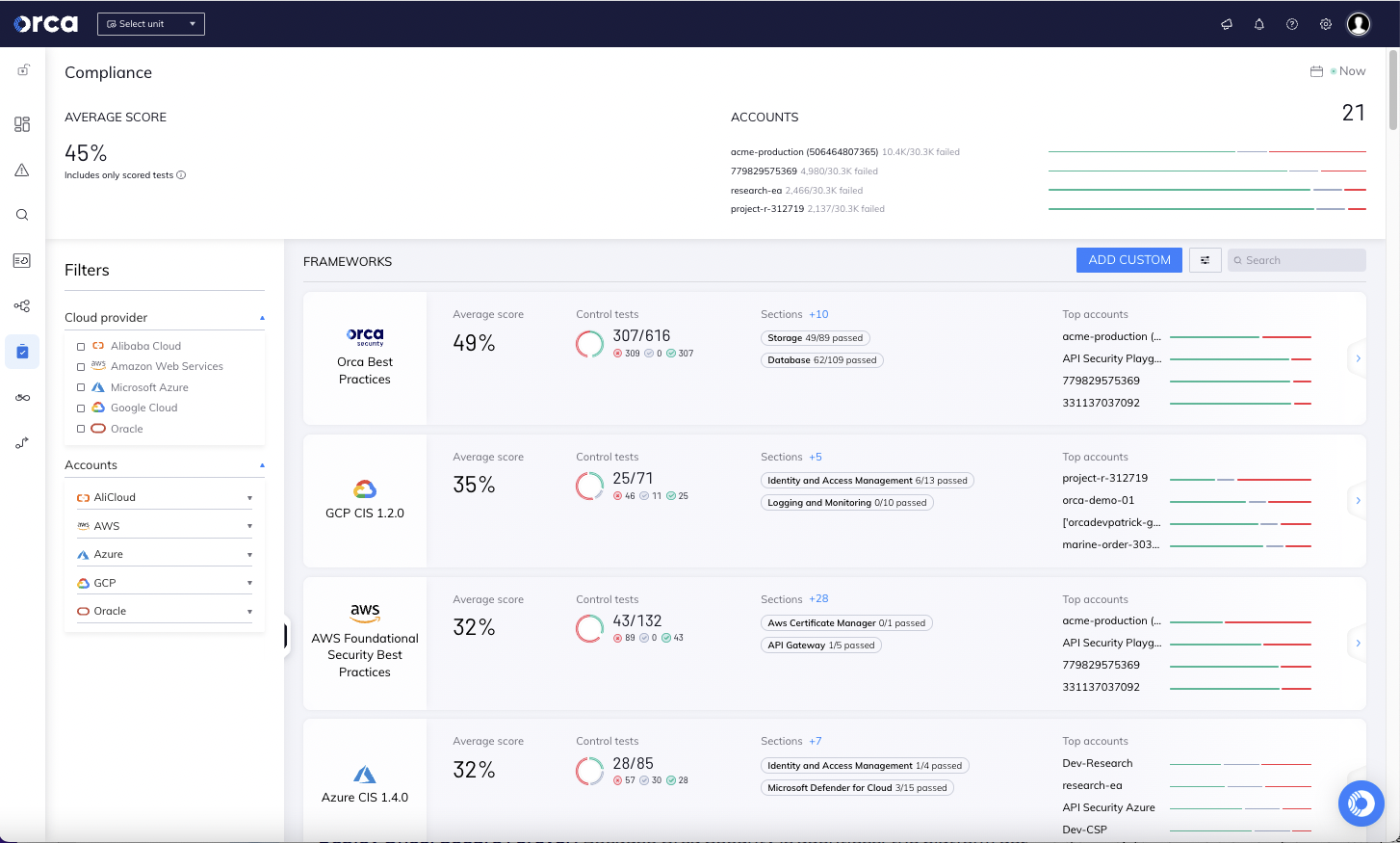
The Orca Platform helps federal agencies achieve regulatory compliance with over 65 out-of-the-box frameworks, CIS Benchmarks, and custom compliance checks across multiple cloud platforms. The Orca research team also maintains a large collection of Orca Security Best Practices and continually adds controls when they become aware of new risks and issues.
#7. Container and Kubernetes Security with CI/CD Controls
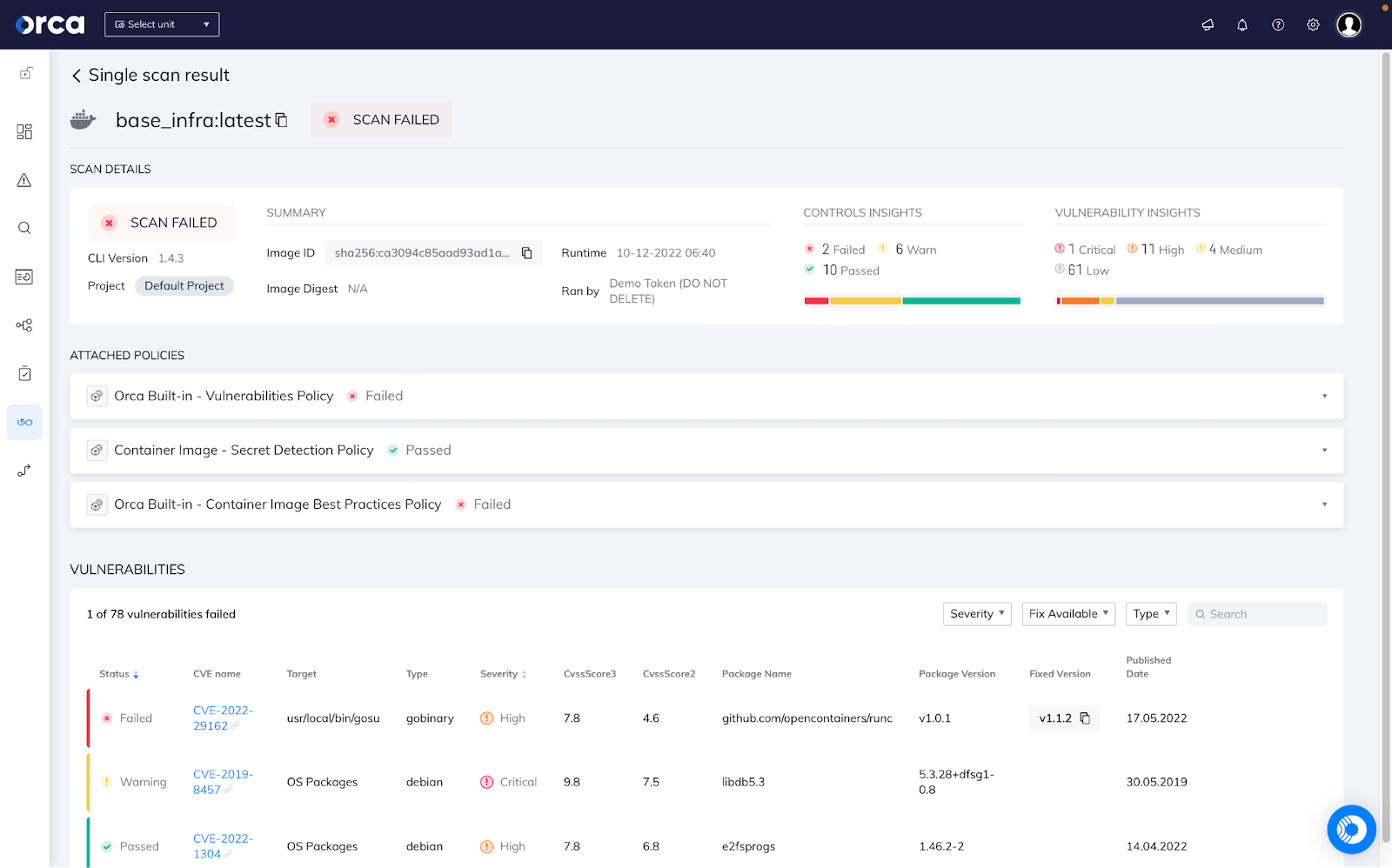
For securing cloud native applications, Federal agencies and government organizations want to secure their applications across the full application lifecycle. The Orca Platform allows security and DevOps teams to integrate security from pipeline to production, including:
- Scanning container images and IaC templates pre-deployment as part of the CI/CD process
- Continuously scanning container registries
- Monitoring vulnerabilities, compliance issues, and advanced threats at runtime
- Enabling developers to securely store build artifacts
Learn more about Orca Security for Government
Would you like to learn more about how Orca is deployed in a FedRAMP environment? View our government solutions page, or watch our recorded demo. If you would like to discuss your FedRAMP cloud security requirements with us, please fill out our contact form.






