Security incidents across the EU more than doubled last year, according to the latest ENISA Threat Landscape Report. This follows a significant increase in the frequency and scale of cyber attacks in Europe and across the globe. Meanwhile, regulators continue to introduce new rules that lead to more oversight and cybersecurity requirements for organizations. Among the most notable regulations to be introduced in recent years is the UK’s Cyber Assessment Framework (CAF), developed and implemented by the National Cyber Security Centre (NCSC).
In this post, we break down the Cyber Assessment Framework to examine what it entails, why it matters, and how to achieve it sustainably for your organization.
What is the Cyber Assessment Framework?
The National Cyber Security Centre (NCSC) is the UK’s technical authority on cyber security. A technical advisor for organizations and regulators, NCSC developed CAF to assist with improving cybersecurity. The organization doesn’t maintain regulatory responsibilities and therefore doesn’t monitor or enforce CAF adherence.
CAF assesses the cyber security resilience of organizations in several essential areas. A sector-agnostic framework, it defines a series of principles or outcomes needed to support cyber security resilience. Unlike other regulatory frameworks, CAF provides general guidance for achieving outcomes that support cyber security resilience and doesn’t prescribe rules or activities.
CAF was introduced following the 2016 implementation of the Networks and Information Systems (NIS) Directive. Among other stipulations, the NIS Directive—which was repealed and replaced with the NIS2 Directive in December 2022—required sector-specific regulators (referred to as “Competent Authorities (CA)”) to have the ability to assess the cybersecurity of Operators of Essential Services (OES) and Relevant Digital Service Providers (RDSP). CAF is designed to help UK organizations meet the requirements of the NIS Directive and support critical national infrastructure (CNI) needs.
Because NCSC isn’t a regulatory institution, mandatory compliance with CAF depends on an organization’s type, sector, and the discretion of its respective CA. This means organizations may self-assess compliance with CAF, rely on a third-party auditor or regulator to do so, or both—depending on the organization’s unique circumstances.
Most CAs have adopted or adapted CAF and require the following organizations to comply with it:
- Operators of Essential Services (OES): Organizations responsible for services deemed critical to the economy and society.
- Relevant Digital Service Providers (RDSP): Organizations that provide an online marketplace, search engine, or cloud computing service. RDSPs must offer services in the EU, maintain their headquarters in the UK, and meet or exceed the definition of a medium-sized business.
What does the Cyber Assessment Framework cover?
The Cyber Assessment Framework consists of a collection of objectives, principles, contributing outcomes, and indicators of good practice (IGP). Below is a brief description of each:
- Objectives: A cybersecurity goal or priority.
- Principles: A high-level security focus that contributes to compliance.
- Contributing outcome: Specific requirements for supporting the achievement of each principle. Contributing outcomes can be measured as Achieved, Not Achieved, or Partially Achieved.
- Indicators of good practice (IGP): A non-exhaustive list of practices designed to support the achievement of contributing outcomes.
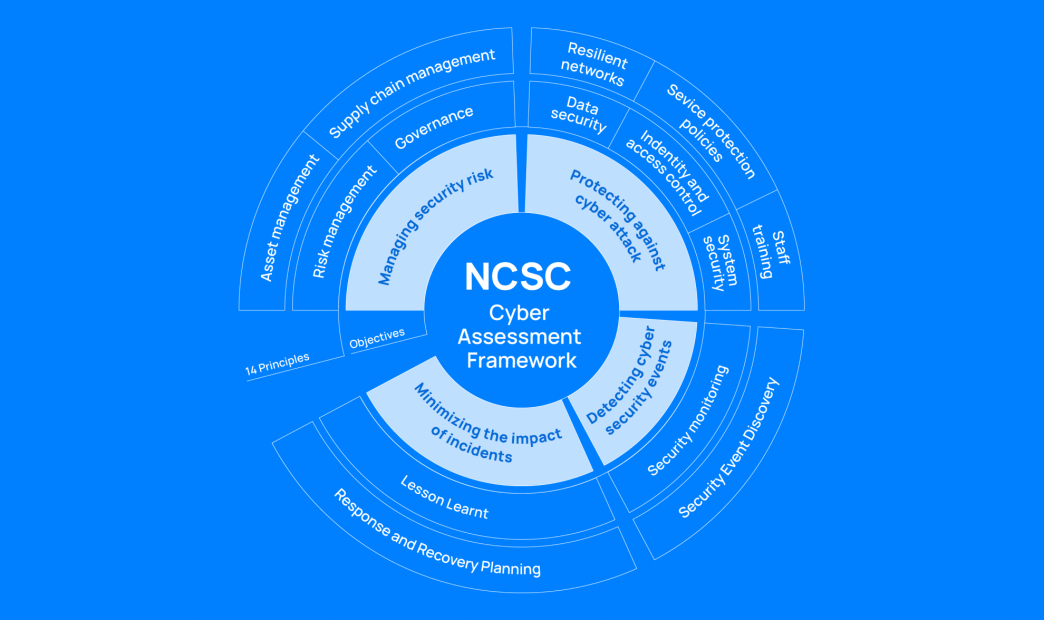
CAF includes four security objectives, 14 principles, and 39 contributing outcomes. For each contributing outcome, the framework includes a set of IGPs. CAF requires organizations to demonstrate how they meet each of the 39 contributing outcomes and their associated IGPs by providing statements and evidence.
Below are the objectives and principles included in CAF:
Objective A: Managing security risk
- Principle A1: Governance
- Principle A2: Risk management
- Principle A3: Asset management
- Principle A4: Supply chain
Objective B: Protecting against cyber attack
- Principle B1: Services protection policies and processes
- Principle B2: Identity and access control
- Principle B3: Data security
- Principle B4: System security
- Principle B5: Resilient networks and systems
- Principle B6: Staff awareness
Objective C: Detecting cyber security events
- Principle C1: Security monitoring
- Principle C2: Proactive security event discovery
Objective D: Managing security risk
- Principle D1: Response and recovery planning
- Principle D2: Lessons learned
4 best practices for complying with CAF
Like other regulations, CAF requires organizations to make a significant investment of time, resources, and capacity. Your organization can increase its return on investment by adopting the following four best practices.
1. Make compliance a priority
When approached reactively, compliance can significantly disrupt your business. Racing to prepare for an audit or deal with the aftermath of a compliance violation not only diverts your time and attention from high-value activities, it also adds unnecessary pressure and stress that can undermine performance.
That illustrates the importance of taking a proactive approach to compliance. To facilitate buy-in, your organization should stress the importance of compliance as a priority, and this message should come from the top down to set the tone. Your leadership and management should also reinforce it continually in their scheduled and ad hoc interactions with teams.
2. Adopt a cloud security solution
According to the Orca 2024 Cloud Security Strategies Report, most organizations operate up to half of their information systems in the public cloud. These environments experience rapid, continual changes due to the ephemeral nature of systems, services, and other assets. That explains why organizations need technology that can account for the dynamism of cloud environments—an area where legacy compliance solutions and methods fall short.
Organizations need a cloud security solution that provides continual compliance monitoring and reporting capabilities. Generally, look for a solution that provides full coverage of your entire cloud estate, comprehensive risk detection, flexible and extensive compliance monitoring and reporting, and also integrations that support cross-functional collaboration.
3. Leverage automations and integrations for continuous compliance
With your cloud security solution in place, you should take advantage of features that automate some of your compliance efforts. Sophisticated cloud security solutions offer the ability to automate low-level tasks, boosting productivity and efficiency across compliance monitoring, remediation, and reporting activities.
For example, some cloud security solutions enable you to build custom automated workflows that execute when specific conditions are met. You can configure the automatic remediation of specific issues when detected or set up special notifications for certain compliance issues.
Sophisticated cloud security solutions also integrate with popular and important business and security applications, including ticketing systems, notification applications, SIEM/SOAR solutions, and more. To enhance visibility, coordination, and buy-in across your various teams, best practice is to configure all integrations when onboarding your new cloud security solution.
4. Prevent compliance issues from reaching your software supply chain
For organizations that develop cloud-native applications, Shift Left Security is an essential measure that can maximize security, efficiency, and organizational stability. Shift Left Security focuses on detecting and remediating misconfigurations and vulnerabilities as early as possible in the software development lifecycle (SDLC) and before they reach production.
How Orca helps with your CAF compliance
The Orca Cloud Security Platform provides advanced and sophisticated features that enable you to achieve multi-cloud compliance across AWS, Azure, Google Cloud, Kubernetes, Oracle Cloud, and Alibaba Cloud environments. Orca supports your compliance efforts regardless of sector, regulatory framework, or industry regime.
Below are a few of the important features Orca offers for compliance.
Full coverage of your cloud environments
Orca provides full visibility and monitoring of your entire cloud estate, eliminating all blindspots and gaps in coverage. Importantly, this complete coverage creates the conditions for achieving 100% compliance.
Onboarding the Orca Cloud Security Platform is a simple three-step process that takes minutes. Within an hour, the Orca Platform provides you with complete visibility and coverage of your entire cloud estate. Orca also continually updates to account for any changes in your cloud assets and risks, including additions and subtractions.

Automatic compliance monitoring and risk prioritization
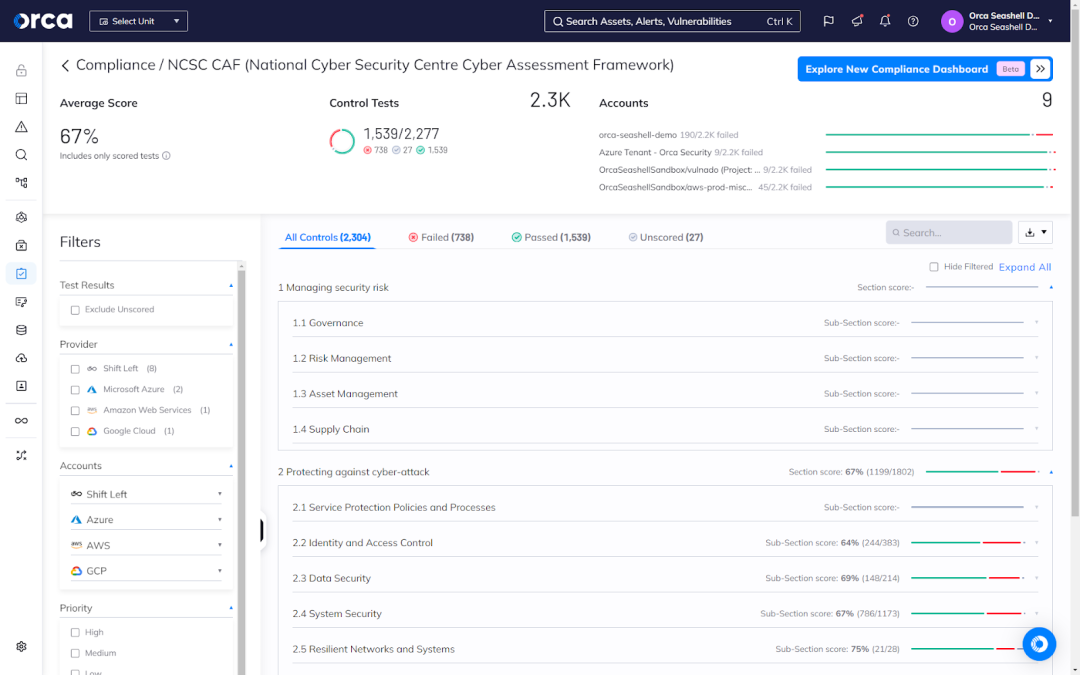
When you choose from more than 150 of Orca’s out-of-the-box frameworks, the Orca Platform automatically and immediately scores your current compliance, providing a comprehensive and detailed inventory of failed and passed controls. Orca also lists all controls included in a specific framework, including those that require intervention outside the Orca Platform. This ensures your teams remain fully aware and informed of all compliance requirements.

Orca detects the full scope of risks that affect compliance, including misconfigurations, vulnerabilities, sensitive data risk, API risk, AI risks, malware and anonymous activity, permission and identity risk, and more.
For every detected risk, Orca dynamically assesses it using a full contextual awareness of the risks and assets in your cloud estate. This assessment accounts for multiple factors, including severity, exploitability, business impact, and lateral movement. Orca accurately and precisely prioritizes risk and continually updates alerts as conditions change. Orca also presents this information in an intuitive dashboard for security teams to quickly digest and leverage for targeted and timely remediation.
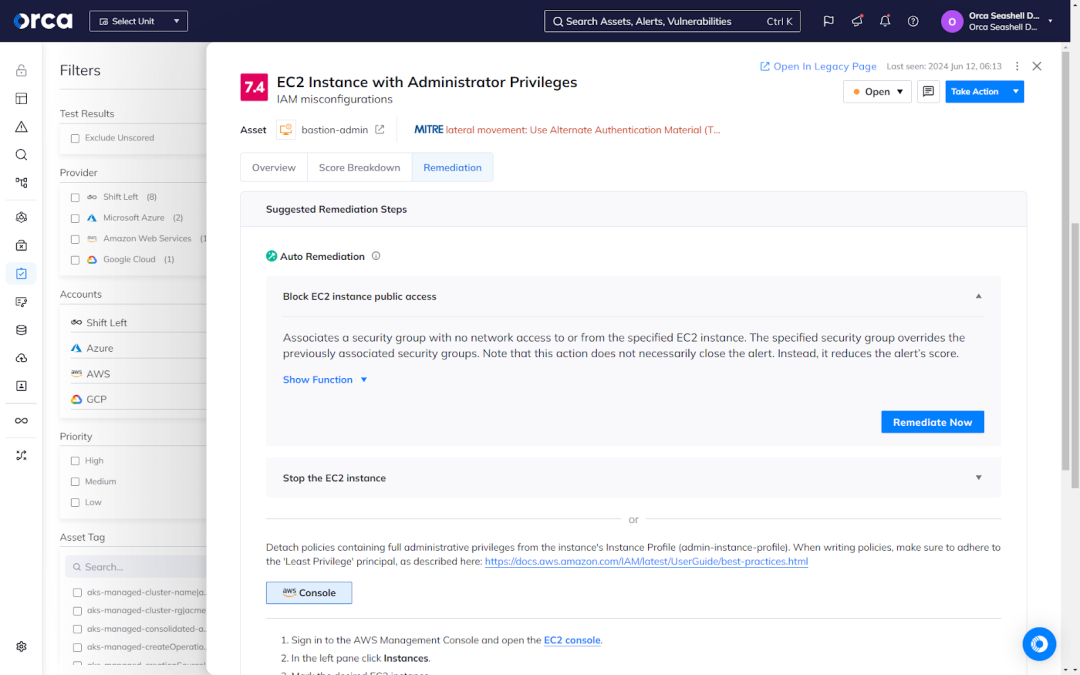
Effective and flexible remediation
Orca enables you to remediate risks when viewing alerts and provides multiple options for maximal efficiency and flexibility. This includes the ability to leverage suggested remediation instructions generated automatically from Orca, as well as tailored remediation guidance powered by Orca’s AI-driven remediation solution. The latter enables you to harness real-time, detailed remediation instructions using Azure OpenAI, Amazon Bedrock, or Vertex AI for your specific remediation tool (e.g., AWS CloudFormation, Azure Console, Google Cloud Console, Terraform, Pulumi,etc.).
Two-way integrations
Orca offers more than 50 technical integrations to infuse cloud security and compliance into your existing workflows and tools. This includes two-way integrations with Jira and ServiceNow, enhancing the convenience and efficiency of coordinating remediation efforts across cross-functional teams. Security teams can create tickets directly from Orca alerts, monitor their status, and verify if issues have been resolved once tickets are closed—all without leaving the Orca Platform. Meanwhile, developers never need to leave their ticketing system, login to Orca, and learn to use the platform.
Seamless, flexible, and automated compliance reporting
The Orca Platform simplifies and automates compliance reporting to ease your efforts. Using the platform, you can generate reports immediately on-demand to present your current compliance status. Orca offers the option to export reports in PDF format for management teams or external stakeholders, as well as CSV or JSON formats for stakeholders needing more granular information, such as remediation instructions for the alerts mapped to failed controls.
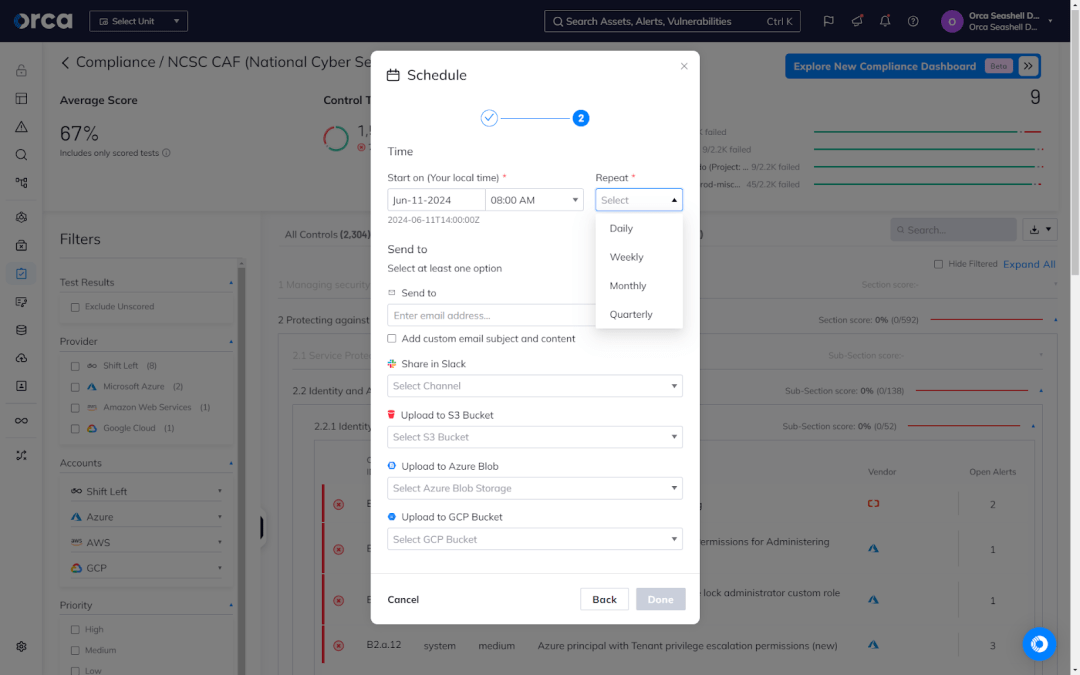
While the Orca Platform makes it convenient to produce ad hoc reports, it also allows you to easily schedule one-time or recurring reports and send them to an email or distribution list, Slack channel, or storage bucket within a specific cloud environment.
Orca’s reporting capabilities solve one of the most time-intensive and resource-consuming aspects of compliance, making continuous compliance efforts not only feasible, but efficient and effective.
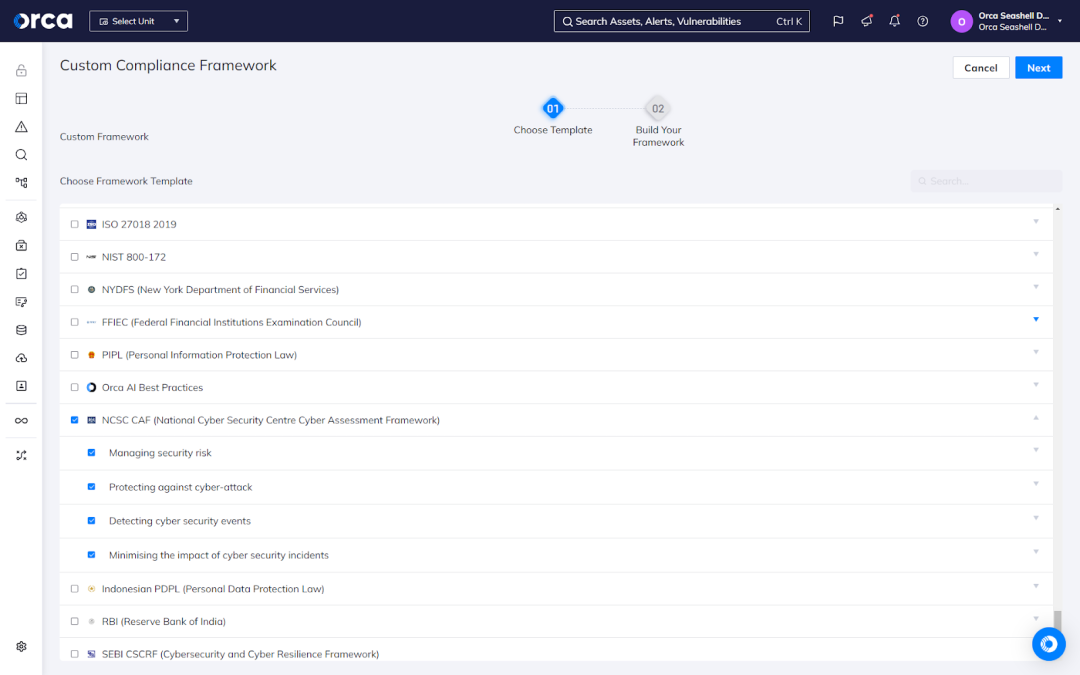
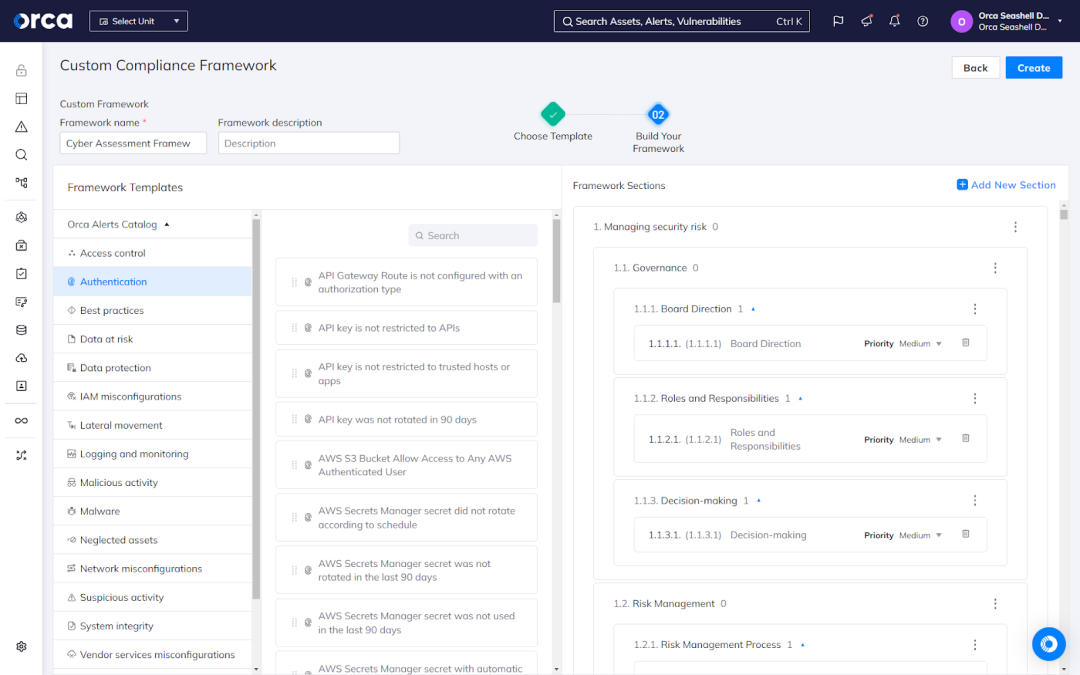
Custom framework creation
To provide maximal flexibility, Orca allows you to create custom compliance frameworks tailored to your needs. Orca allows you to combine controls from out-of-the-box compliance frameworks, whether entirely or selectively, as well as add Orca alerts individually from a catalog of more than 2,200 covering a variety of use cases. Orca also enables you to create your own bespoke framework from scratch.
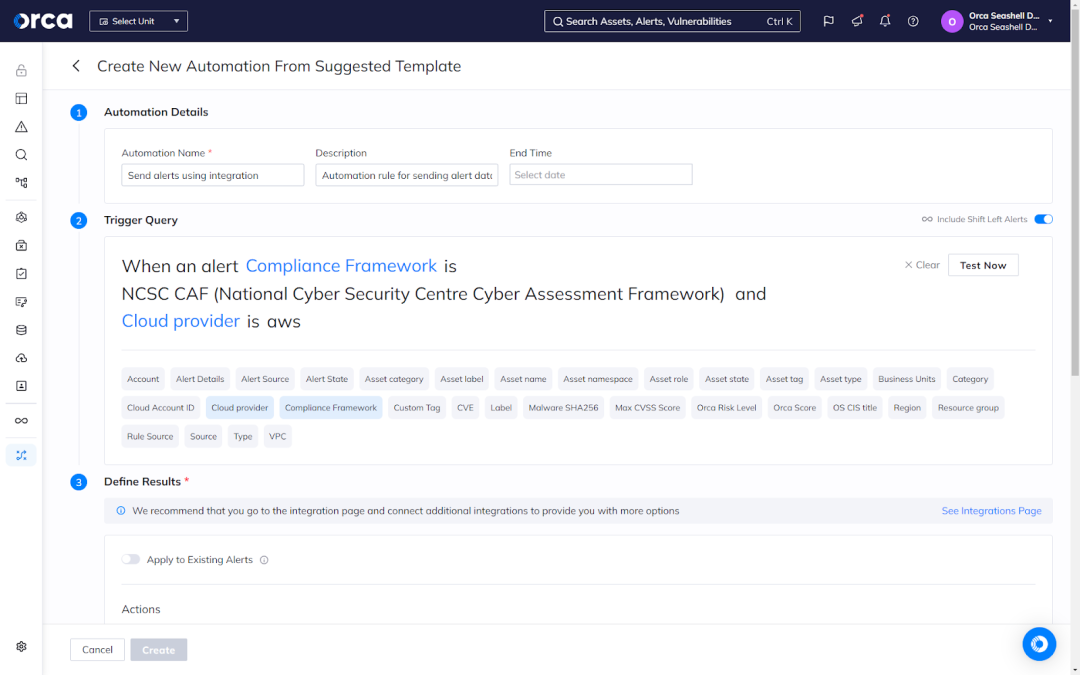
Automations that facilitate continuous compliance
Orca provides customizable automations that make continuous compliance beneficial and sustainable. Automations perform tasks on behalf of your teams without intervention when specific conditions are met—and for a variety of compliance use cases.
For example, you can create an automation for a specific risk that automatically creates a ticket in Jira or ServiceNow, or remediates a risk according to predefined criteria. Orca’s Automations supports more than 30 customizable categories of conditions to provide comprehensive and extensive flexibility.
Learn more about how Orca eases CAF compliance efforts
Offering more than 150 out-of-the-box compliance frameworks, including CIS® benchmarks, Orca empowers you to achieve multi-cloud compliance continuously and seamlessly.
The Center of Internet Security® (CIS®) Benchmarks has certified the Orca Cloud Security Platform across 24 cloud frameworks, validating that Orca accurately identifies any configurations that deviate from best practices in more than 60 CIS® Benchmarks.
Schedule a demo of the Orca Platform to see how it can ease and enhance your compliance efforts, in addition to securing your entire cloud estate.