Compliance is too often seen as a burden or necessary evil as compared to other components of cloud security risk management. While compliance is often difficult, the idea of it being somehow less important is, of course, inaccurate.
That said, cloud compliance can be challenging. Compliance can be fragmented and separate from cloud security teams responsible for risk management, resulting in a lack of cohesion, efficiency, and friction. Organizations that rely on cloud platform native security tools often need to maintain and align policies across disparate solutions. Although dedicated compliance solutions exist, they often require manual processes, lack remediation techniques, and do not provide the ability to create custom frameworks. All of these factors add to the complexity of ensuring cloud security compliance, explaining why it is often seen as a burden.
This is why we designed the Orca Platform to take the pain out of cloud compliance. Orca allows organizations to efficiently automate the compliance process across multiple cloud providers from a single platform, deploy automated and guided remediation, and if needed, customize compliance frameworks to their specific needs.
As the Orca Cloud Security Platform is agentless, Orca’s fast and one-time deployment results in continuous reporting and analysis on compliance status for relevant controls. It also means that the compliance analysis automatically scales with your cloud efforts, not against them. Each time a new asset is added, it is automatically covered by the Orca Platform.
With support for over 100 compliance frameworks and Center for Internet Security (CIS) benchmarks, as well as the capability to create custom frameworks, Orca shows which compliance controls are being met or whether improvement is needed. This is not a separate tool, but rather a critical capability within the unified Orca Cloud Security Platform.
“We’re in our second year with the SOC 2 audit and Orca Security makes it so much easier,” says Tomer Kazaz, Co-founder and CTO of Hunters. “We export an Orca report, take a few screenshots, and paste it as evidence. But the audit isn’t just about production. They want to know about policies pertaining to enterprise security and other company processes. Orca helps us with technical aspects of the audit by informing us how we can run as cleanly as possible.”
Comprehensive Cloud Compliance with Fewer Tools
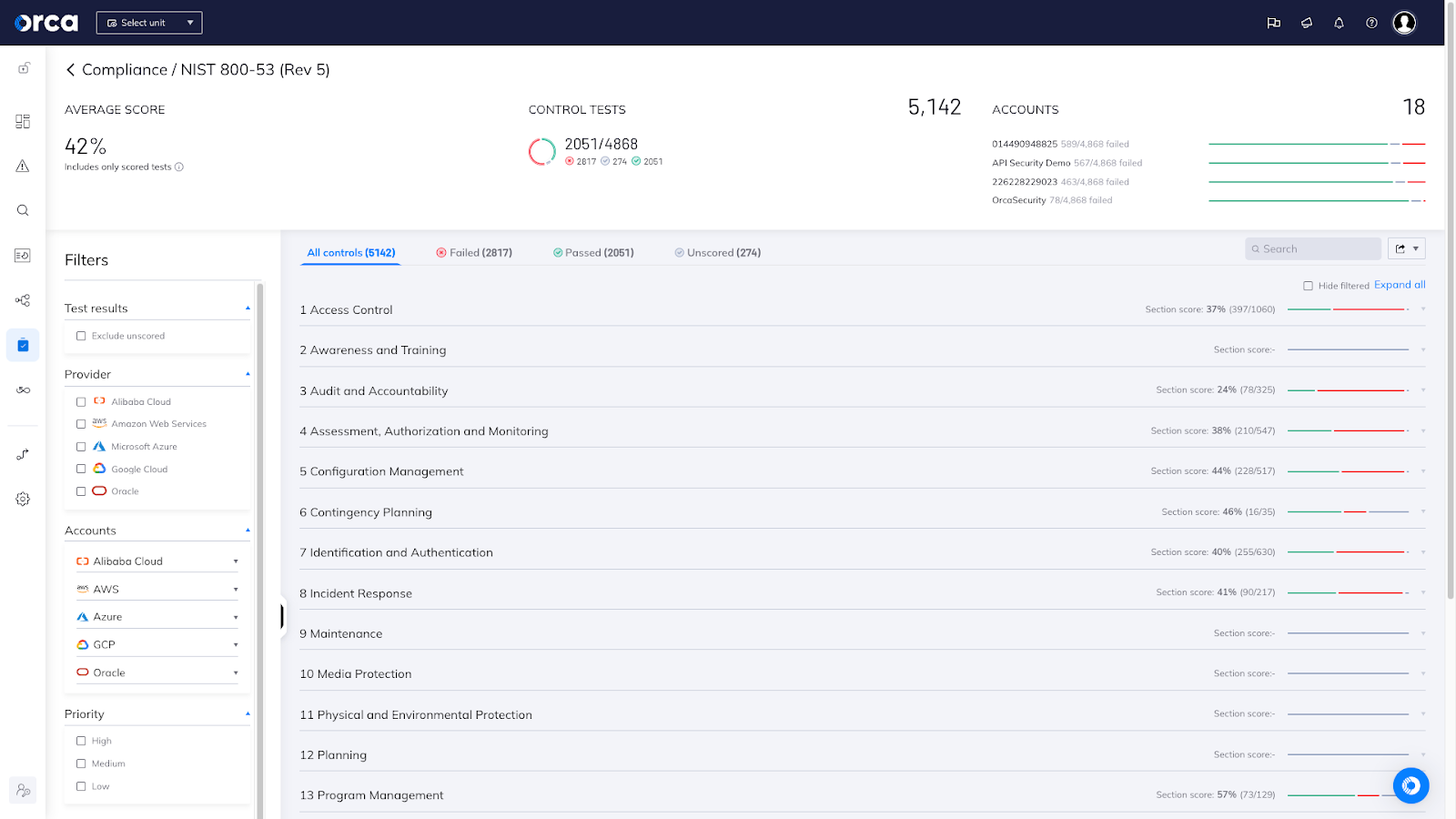
Percentage of controls that have passed are shown and other high level compliance information
Whether an organization is formally regulated, or simply looking for best practice guidance, Orca provides extensive cloud compliance value and solutions.
As opposed to using multiple security tools to handle compliance, from vulnerability management to data security tools, or tools that provide support for only a single cloud service provider, Orca is able to consolidate comprehensive compliance capabilities into a single platform. The capabilities include:
- Multi-cloud compliance support – Instead of relying on separate CSP tools to measure compliance with different cloud provider CIS benchmarks, Orca’s multi-cloud security platform provides a compliance ‘HQ’ for all major compliance frameworks and CIS benchmarks (see more later in this article). As Orca’s visibility into cloud resources and prioritization of security risks is unified across cloud providers, so too are our compliance capabilities.
- Complete visibility into cloud assets – As Orca is not limited by the need to have an agent installed on every cloud workload, coverage is wider across the entirety of the cloud estate to include workloads – virtual machines, containers, storage buckets, databases, or serverless functions. Orca also looks into cloud infrastructure, identities, web and API endpoints, and sensitive data. This translates into wider compliance visibility, eliminating the need for multiple tools to scan different asset categories.
- Greater automation of compliance verification and remediation – While there are cloud compliance tools that aggregate the controls of various frameworks and essentially place reminders of requirements at different levels of your IT and application infrastructure, they do not perform the technical verification checks for you, and require you to do it manually. This demands a lot of time and effort from operations, DevOps, and cloud engineering teams. It also can lead to purchasing additional tools to fully do the job.
In contrast, the Orca platform automates the process. With an easy to use compliance dashboard that provides actionable metrics, compliance teams can know where they stand in meeting framework requirements, and stay ahead of compliance audits. In addition, compliance teams can use Orca’s auto-remediation capabilities to reduce Mean Time to Remediation (MTTR) to the bare minimum, thereby improving your security posture and compliance requirements.
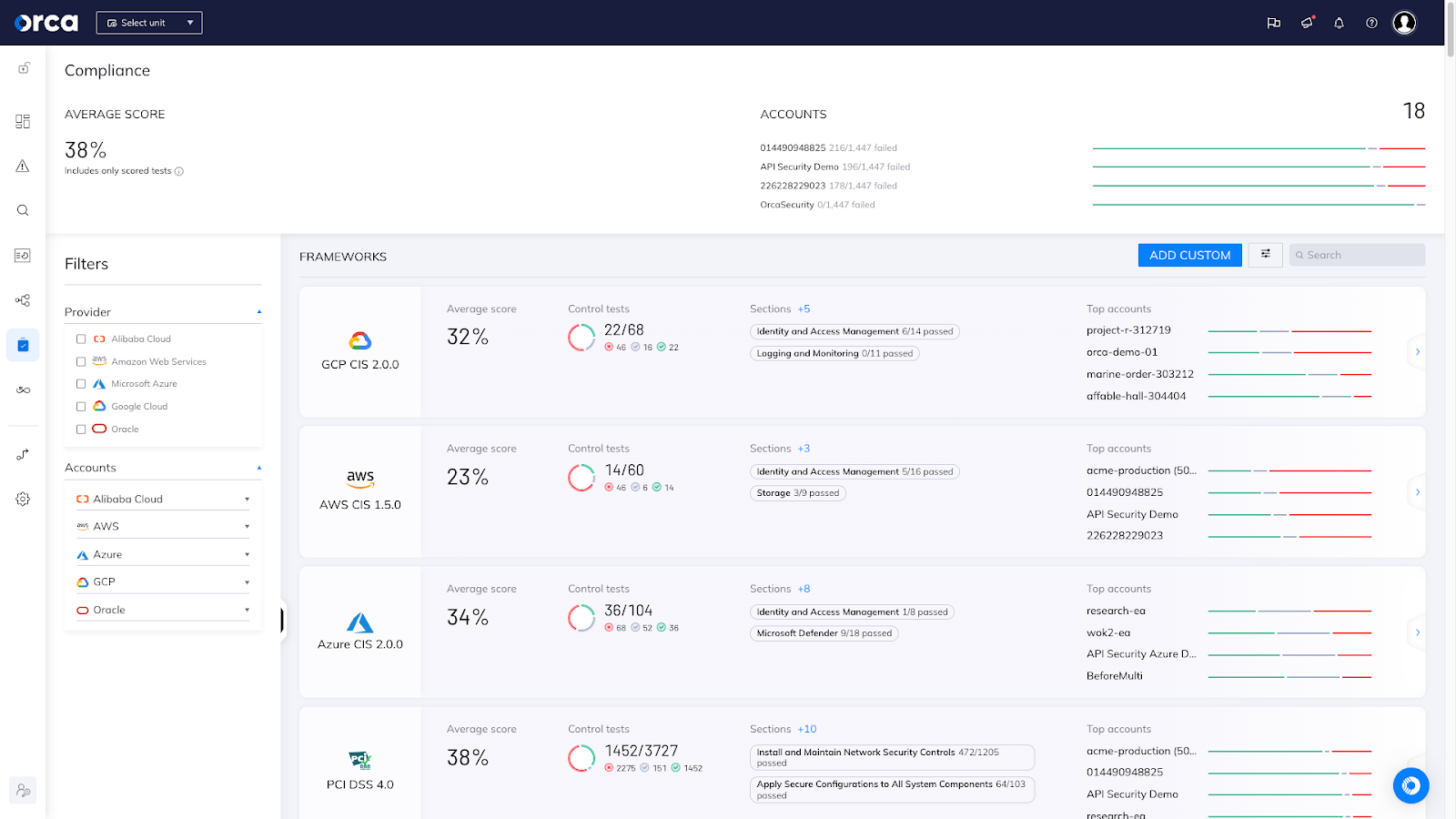
Orca’s centralized compliance dashboard covers cross-cloud CIS benchmarks and compliance frameworks
Linking Cloud Risks with Compliance Controls
The Orca platform leverages comprehensive visibility of cloud assets across Amazon Web Services (AWS), Microsoft Azure, Google Cloud (GCP), and Kubernetes accounts, and the security risks attached to them, to offer out-of-the-box compliance capabilities (that are also customizable). This results in a unified view covering cloud assets, cloud risks, and compliance.
The platform also alerts to a comprehensive list of cloud risks, including misconfigurations, vulnerabilities, identity and access management, lateral movement, sensitive data at risk exposed APIs, suspicious activity, and more. Each alert has a list of compliance frameworks that are relevant to it. Within each alert are clear remediation instructions to reduce the attack surface and tighten compliance.
Using the Orca Cloud Security Platform, security and compliance teams get clear and detailed answers to questions such as:
- What assets do I have and where?
- What is exposed?
- Are our cloud environments meeting compliance regulations?
- Are they adhering to internal corporate IT governance policies?
Orca provides a centralized compliance dashboard containing information that is purpose built both for the practitioner, with executive dashboard reports for other stakeholders. The dashboard supports granular search and filtering so you can easily filter using a combination of cloud providers and accounts.
Regulatory Compliance Support to Stay Ahead of Audits
Orca’s compliance capabilities enable compliance teams to understand the status of their cloud resources relative to compliance regulations ahead of external or internal audits. Orca includes out-of-the-box compliance templates for 100+ regulatory frameworks including PCI-DSS, GDPR, HIPAA, ISO 27001, NIST 800-53, MITRE ATT&CK, and SOC 2.
The same goes for CIS benchmarks like AWS Foundational Security Best Practices, GCP CIS, Azure CIS, OCI CIS, Alibaba Cloud CIS, as well as Kubernetes CIS benchmarks—both general (K8S CIS) and platform-specific (EKS, AKS, and GKE – from AWS, Azure, and Google Cloud). It’s important to note that Orca consistently monitors and adds support for newer versions of CIS benchmarks, keeping up-to-date on changes as they evolve, reflecting the latest cloud security best practices.
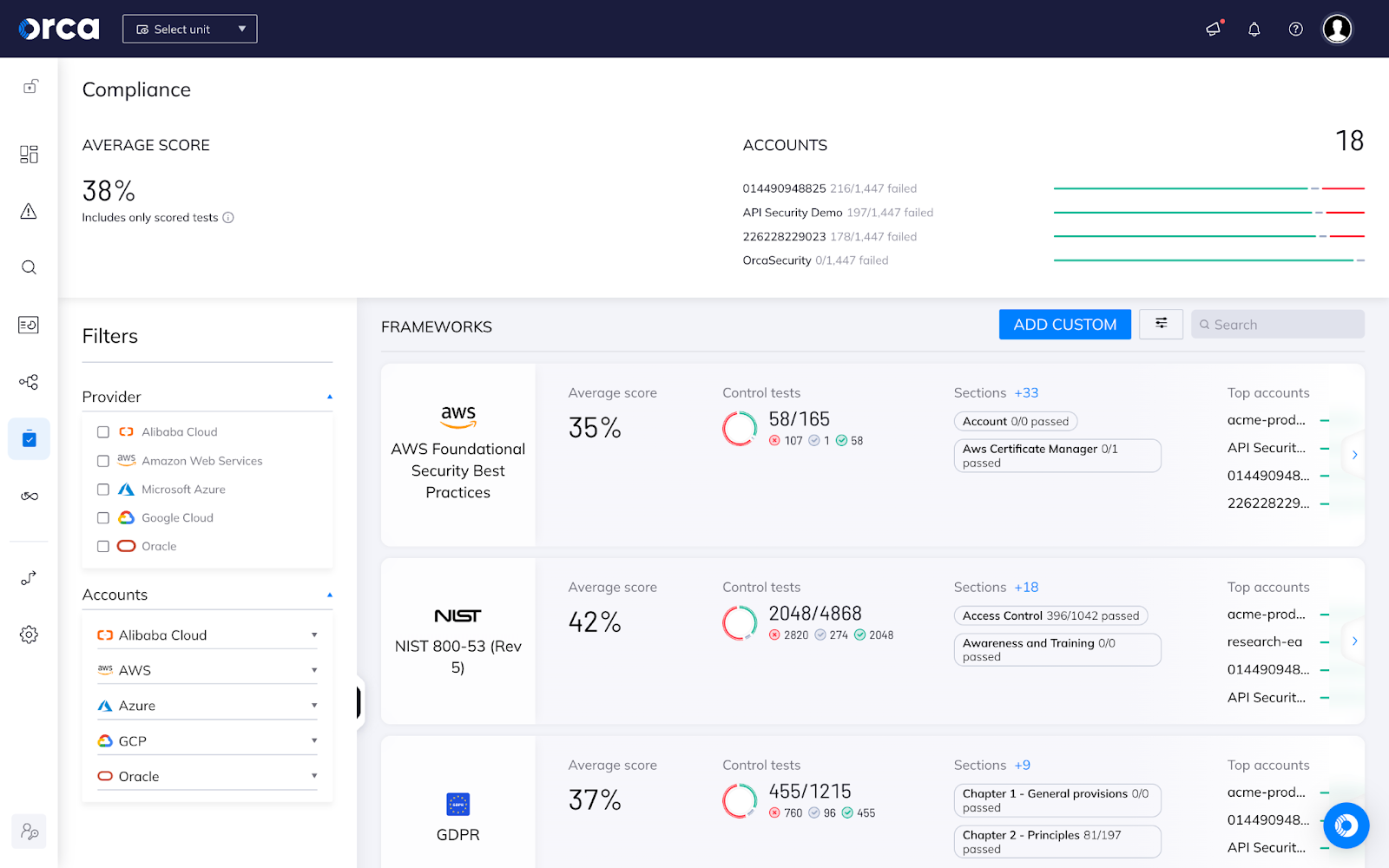
Orca’s centralized compliance dashboard
Orca is committed to continually update, improve, and expand supported frameworks and CIS benchmarks. Below we have listed some of the latest additions to our compliance frameworks:
- Motion Picture Association Best Practice Guidelines – The Motion Picture Association (MPA) has established a set of best practices for securely storing, processing and delivering protected media and content. Media companies use these best practices as a way to assess risk and security of their content and infrastructure.
- Australian Cyber Security Centre (ACSC) Essential Eight Standard – Published by the Australian government’s lead agency for cyber security, the ACSC recommends that organizations implement eight essential mitigation strategies, with the goal of making it harder for adversaries to compromise systems.
- Personal Data Protection Act (PDPA) – Singapore’s PDPA governs the collection, use, disclosure, and care of personal data. At the center of the PDPA are the data protection obligations including consent, purpose limitation, notification, access and correction, accuracy, protection, retention, transfer, and openness.
- GCP CIS 2.0.0 – This security configuration benchmark covers the foundational elements of Google Cloud. The recommendations detailed are important security considerations when designing your infrastructure and building applications in Google Cloud. Note that this is the latest version, but Orca also provides support for earlier versions, if needed.
Some compliance frameworks are focused on particular industries, such as HIPAA (healthcare and pharma), CJIS (law enforcement), and FedRAMP governmental organizations.
Other frameworks might be national or regional, such as UK Cyber Essentials, Brazilian General Data Protection (LGPD), Australian Government Information Security Manual, or the Personal Data Protection Act in Singapore.
A few other noteworthy frameworks support by the Orca Cloud Security Platform include:
- ISO 27001:2022 – One of the most adopted cybersecurity standards, it details requirements for establishing, implementing, maintaining and continually improving an information security management system (ISMS) – the aim of which is to help organizations make the information assets they hold more secure. Organizations that meet the standard’s requirements can choose to be certified by an accredited certification body following successful completion of an audit.
- K8s OWASP Top 10 – This framework provides coverage of the priority risks around the Kubernetes ecosystem, the most popular container orchestration platform, and helps security professionals, system administrators, and developers understand, prioritize, and address these risks.
- MITRE ATT&CK – Provided by the MITRE Corporation, ATT&CK stands for Adversarial Tactics, Techniques & Common Knowledge and has been compiled based on real-world observations. It is used as a foundation for the development of specific threat models and methodologies, and is intended to be used by organizations as a tool to decrease their attack surface.
- Orca DSPM Compliance framework – A new framework unique to Orca, dedicated to securing sensitive data in the cloud, which includes six sections: Data at Risk, Data Encryption, Network Security, Access Control, Logging and Monitoring, and Backup and Restore.
- Orca Cloud Cost Optimization framework – Utilizing the diverse cloud scanning capabilities of the Orca platform, the framework automatically identifies resources, such as VMs, databases, or other critical cloud assets, that are not being used so organizations can reduce unnecessary cloud consumption and optimize their cloud costs.
Customize Compliance Frameworks to Fit Specific Needs
In addition to out-of-the box frameworks, Orca provides the ability to customize particular controls of a given framework, or to create a different, custom framework entirely.
There are many reasons why organizations may want to customize their compliance controls. Perhaps they have other tools already within their organization that handle certain sections (IAM access and policies, for example). Alternatively, a framework like PCI-DSS or NIST gives general guidelines, but not specific rules for cloud environments, and so the organization will choose to supplement the framework with additional controls.
To provide complete flexibility, users have the option of defining custom frameworks, using framework templates or building them from scratch. Templates enable users who wish to make small changes to an existing framework or combine rules from two or more frameworks.
This means that your compliance tests can be customized to your environment for improved accuracy, fewer false positives, and ultimately greater trust in the results.
These templates can be used out-of-the-box or easily customized by adding, deleting, and modifying controls to meet your individual requirements. Users can then run comprehensive reports based on these templates to easily demonstrate compliance to auditors.
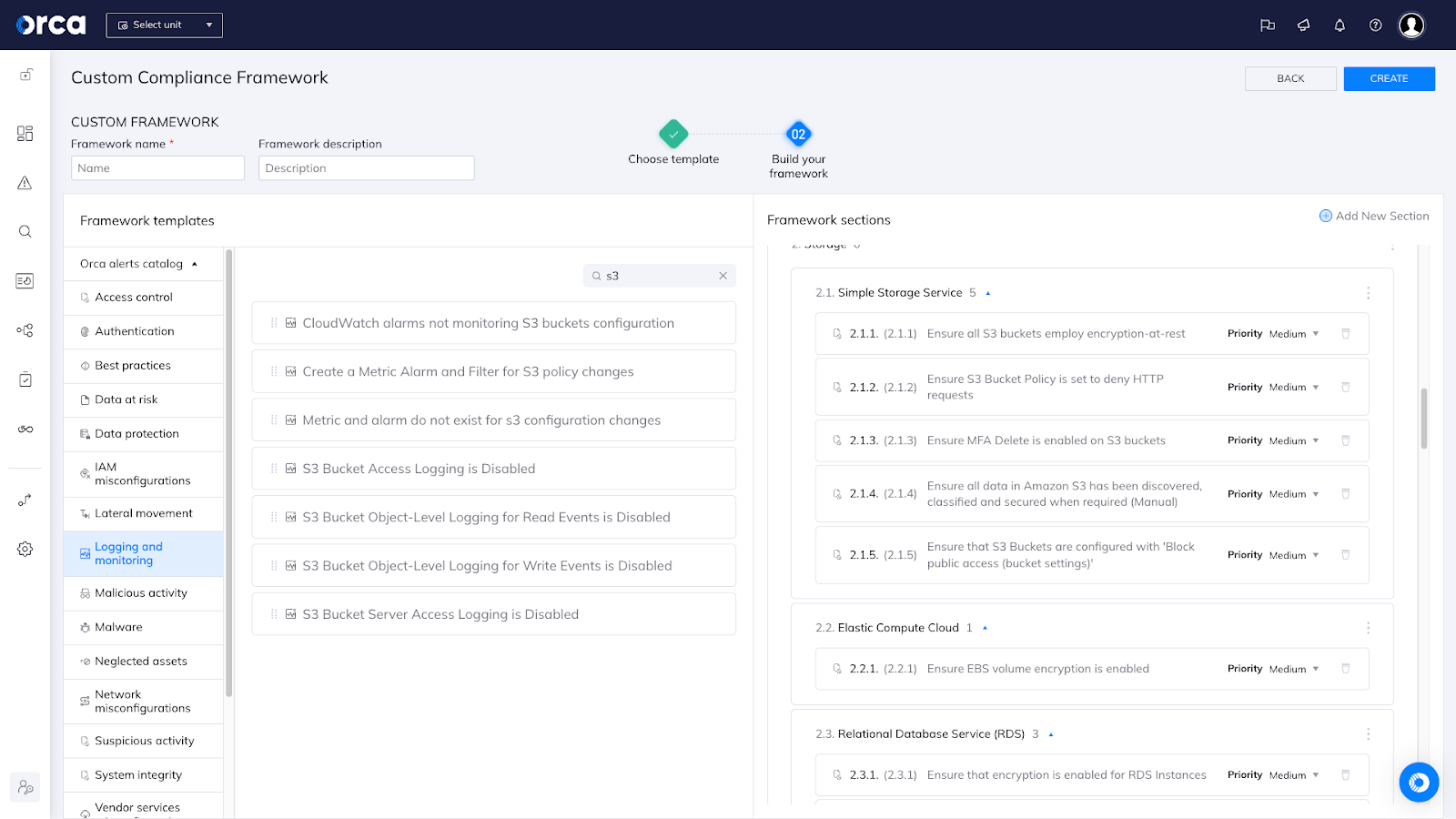
Orca allows for compliance framework customization
Do Not Focus Only on Compliance
A word of caution – it would be a mistake to have compliance regulations be the sole motivator or focus when determining cloud security strategies. Meeting just the minimum requirements will not protect organizations from a breach. Attackers will not wait for governmental and regulatory bodies to catch up with the latest attack techniques.
Beyond just checking a box, cloud compliance should be integrated with cloud data security (and cloud security more broadly) strategies. A dedicated focus on risk management, continuous asset discovery and inventory, and leveraging the wider cloud risk content to gain a comprehensive understanding of which cloud risks are truly the most dangerous is critical.
Achieve Cloud Compliance Objectives with Orca Security
Ready to get started with maintaining compliance or updating your cloud compliance strategy? Learn how Orca helped Hunters to ease the SOC 2 Audit Process in this recent case study. You can also schedule a demo or sign up for a Free Risk Assessment to experience the comprehensiveness and simplicity of securing your entire cloud estate with Orca’s agentless Cloud Security Platform.




