Note: We are actively tracking the situation and will be updating this page and the Orca platform as more details become known.
If you are getting confused right now, you are not alone. Now that spring has officially started, so have, it seems, the ‘spring’ vulnerabilities. In the last few days, two vulnerabilities have been found in Spring Core and Spring Cloud Function, causing a lot of confusion in the cybersecurity community. Although both vulnerabilities are associated with the Spring framework, they are notably different.
Below, we have tried to shed some light on the differences between the two vulnerabilities and which one you need to be more concerned about (spoiler alert: it’s Spring4Shell).
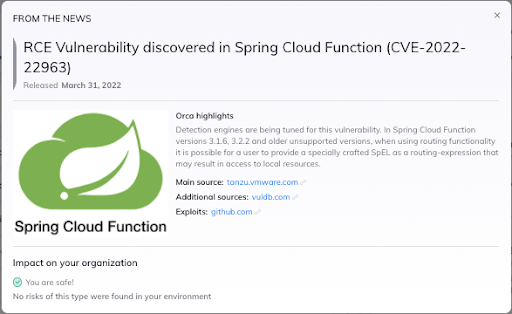
CVE-2022-22963 in Spring Cloud Function
| Name | CVE-2022-22963 |
| Published | March 29th, 2022 |
| Severity | Critical (CVSS score 9.8) |
| Exploitability | Medium |
| Affects | Spring Cloud Function versions 3.1.6, 3.2.2 and older unsupported versions. |
| PoC Exploit | Yes |
| Patch available | Yes, upgrade to Spring Cloud Function versions 3.1.7 and 3.2.3. |
| Usage | Not widely used |
| Description | This vulnerability allows a user to provide a specially crafted Spring Expression Language (SpEL) as a routing-expression that may result in access to local resources and remote code execution (RCE). |
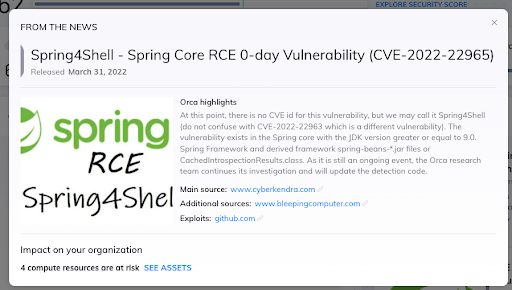
‘Spring4Shell’ (CVE-2022-22965) in Spring Core
| Name | Spring4Shell, SpringShell or CVE-2022-22965 |
| Published | March 30th, 2022 |
| Severity | Critical, Remote Code Execution (RCE), (CVSS score 9.8) |
| Exploitability | High |
| Affects | Spring Core on JDK (Java Development Kit) 9 and above. |
| PoC Exploit | Yes |
| Patch available | Yes, upgrade to Spring Framework version 5.3.18 and 5.2.20 |
| Usage | Millions of Java applications |
| Description | This vulnerability is dubbed ‘Spring4Shell,’ since it is Java-based and easily exploitable, just like Log4Shell. In certain configurations, an unauthenticated attacker can execute arbitrary code on the target system by sending a crafted HTTP request. However, the vulnerability is more difficult to exploit on other configurations. Although the severity of this vulnerability is high, the current opinion is that it is more difficult to exploit than Log4Shell. This vulnerability was leaked before it received a CVE but has now been assigned CVE 2022-22965. |
What is Spring Cloud Function?
Spring Cloud Function is now owned by VMWare and promotes the implementation of business logic via functions and decouples the development lifecycle of business logic from any specific runtime target. This enables the same code to run as a web endpoint, a stream processor, or a task.
What is Spring Core?
Spring Core is an open source application development framework for Java that provides comprehensive infrastructure support for developing robust Java applications and is widely used in millions of applications.
How to remediate CVE-2022-22963
Upgrade to Spring Cloud Function versions 3.1.7 and 3.2.3.
How to remediate Spring4Shell – CVE-2022-22965
An official fix has now been released and customers are encouraged to update to Spring Framework versions 5.3.18 and 5.2.20. If you are not able to upgrade your application, additional mitigation workarounds are also available.
How can Orca Security help you find these vulnerabilities in your cloud?
Orca automatically alerts on all vulnerable Spring Core and Spring Cloud Function installations that are found on your AWS, Azure and Google Cloud assets. To detect the Spring4Shell vulnerability, Orca checks the spring-beans jar file and the running JDK version (if installed via the OS package manager). Orca issues an alert if the spring-beans version is vulnerable and the installed JDK version is 9 or higher.
Both vulnerabilities are included in our From the News Widget in the Orca dashboard (see screen below), so users can simply click on the relevant news update to see if any of these vulnerabilities are found.
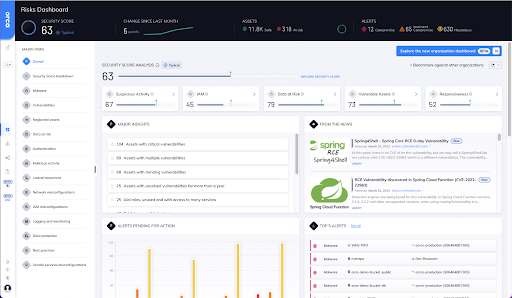
‘From the News Widget’ in Orca’s dashboard with coverage for Spring4Shell
How do I know which vulnerabilities need to be fixed first?
Orca automatically identifies and prioritizes the vulnerable assets that could potentially expose your business critical assets, so your security team can focus on remediating these first to stem the most immediate danger. These alerts will show up as ‘Imminent Compromise’ in the Orca dashboard.
In addition, Orca’s attack path analysis feature discovers the new attack paths that are created by these Spring vulnerabilities and scores and prioritizes the attack paths that endanger your crown jewels, so that your security team can make sure that these are remediated first.
Free Vulnerability Risk Assessment
To see if your cloud environment is impacted by these and other known vulnerabilities and zero-day threats, sign up for our free, no obligation risk assessment today. Since Orca’s platform is totally agentless, setup only takes a few minutes and full results from your entire environment will be available in a few hours.






