Table of contents
As the largest cloud provider in the world, AWS stands at the forefront of the surging cloud computing market predicted to surpass $1 trillion by 2028. That’s when Gartner expects cloud computing to become a necessary investment for organizations. Yet as demand for cloud services rises sharply, so do the associated security risks. AWS security helps organizations maximize the benefits of cloud computing while controlling and minimizing the security risks and threats inherent to their AWS environments.
In this comprehensive guide, we explore AWS security in detail, revealing what it entails, why it matters, and how your organization can implement it successfully for optimal results.
What is AWS security?
AWS security refers to a collection of tools and practices designed to protect AWS cloud environments from security risks and threats. AWS security includes both solutions and services provided by AWS, as well as those offered by third-party vendors.
Today, companies are investing more in cloud-native applications and environments to develop new products and services, improve operational efficiencies, and expand into new markets. They’re also discovering a host of cloud security risks, such as misconfigurations, vulnerabilities, malware, permissive identities, and many others. AWS security introduces preventative and corrective measures to protect AWS environments and their workloads, data, identities, and entitlements.
Why is AWS security important?
For organizations migrating to the cloud or looking to make the move, AWS security is not only important, but imperative for the following reasons.
Shared Responsibility Model
Cloud computing operates according to the Shared Responsibility Model, which holds cloud service providers and their customers responsible for protecting different aspects of public cloud environments. These responsibilities vary according to the established business relationship between the two parties and fall into one of three categories:
- Infrastructure-as-a-Service (IaaS)
- Platform-as-a-Service (PaaS)
- Software-as-a-Service (SaaS)
Regardless of the arrangement, cloud providers own the responsibility to protect cloud infrastructure, while customers must protect their applications and data. With IaaS, customers also maintain the responsibility of managing and protecting their operating systems and databases, where this responsibility moves to cloud providers under a PaaS or SaaS arrangement.
The Shared Responsibility Model makes AWS security essential both for AWS and their customers.
Cloud security risks and consequences
AWS security helps protect against key security risks and their associated consequences. While this includes numerous types of risks, below are several main categories:
Misconfigurations
Misconfigurations represent a top security threat, which explains why Gartner predicts that more than 60% of organizations will make preventing cloud misconfigurations a top security priority by 2026. This reinforces findings from Orca’s Cloud Security Strategies Report, which found that more than half of organizations rank misconfigurations as their number one cloud security risk.
Misconfigurations include any error, coverage gap, or issue that exposes a cloud resource to risk. Common examples of misconfigurations include exposed access keys, overpermissioned identities, sensitive data exposure, and more. Misconfigurations often increase the likelihood an attacker can gain unauthorized access, laterally move, and endanger high-value assets.
Vulnerabilities
Security teams can only address 10% of vulnerabilities detected each month. Meanwhile, new research by Verizon finds that vulnerability exploitation tripled in the past year, accounting for more than 1 in 10 data breaches as an initial attack vector. Like misconfigurations, vulnerabilities represent a top security risk in the cloud.
Vulnerabilities often create weaknesses in an organization’s attack surface that threat actors can exploit. Vulnerabilities originate from open-source and third-party software components, custom code, as well as other sources.
Sensitive data exposure
As mentioned previously, misconfigurations can result in the exposure of sensitive data, such as personally identifiable information (PII), personal health information (PHI), and more. This can lead to significant consequences, including financial, legal, regulatory, and reputational. To illustrate, the global average cost of a data breach now stands at $4.88 million (USD) according to IBM’s Cost of a Data Breach Report, the highest total to date. For essential industries such as healthcare and financial services, this figure increases significantly.
Components of AWS security
AWS offers a variety of security features to help fortify cloud environments. Organizations must properly configure and maintain these features as part of their obligations under the Shared Responsibility Model. They include:
- Infrastructure security: includes features that support distributed denial of service (DDoS) mitigation, traffic encryption, and network firewalls.
- Data security: includes features that support data encryption and sensitive data discovery. For encryption, AWS offers AES-256 encryption across several services, as well as the option to use its Key Management Service (KMS). KMS enables you to create and control a unique encryption infrastructure or use an AWS Customer Master Key (CMK).
- Configuration management: includes features to manage AWS resources and configurations, including inventorying, analyzing, and auditing configurations.
- Identity and access control: includes features that enable you to set different levels of access to cloud resources and APIs, establish and manage password policies, enable multi-factor authentication (MFA) and single sign-on (SSO), and more.
- Monitoring and logging: includes features that monitor and log cloud activity, detect anomalous or malicious behaviors, and more.
Challenges of AWS security
AWS security presents unique challenges that organizations must navigate. Some of the main challenges include the following:
Multi-cloud compatibility (AWS, GCP, etc.)
Many organizations maintain a multi-cloud environment involving more than one cloud provider. This leads to several security challenges, including properly configuring, managing, and monitoring cloud providers’ native security features. These tools and services work exclusively for each provider’s platform, requiring organizations to juggle disparate features, interfaces, terminology, and more. This not only duplicates the work and complexity security teams must manage, but it also creates gaps in visibility and coverage due to information silos. The lack of multi-cloud compatibility creates the need for a third-party cloud security solution that integrates with and supports all major cloud provider environments.
Lack of visibility
As mentioned previously, cloud environments are highly dynamic, consisting of a vast network of ephemeral resources. The evolving and distributed nature of the cloud makes gaining and maintaining visibility a key challenge. This helps explain why nearly half of organizations believe increasing visibility will improve their cloud security posture, more than any other factor.
Visibility requires several components working together, including:
- Full coverage across every layer of a multi-cloud estate, including infrastructure, workloads, identities and entitlements, and data.
- Deep integrations with essential applications used by security, development, DevOps, and other functional teams—spanning across the application lifecycle.
- Unified intelligence and capabilities accessible from a centralized dashboard.
Risk prioritization
Most security teams receive more than 500 security alerts per day, while more than half admit that critical risks go unnoticed on a daily or weekly basis. Both represent alarming statistics, revealing the lack of accurately prioritizing risks to address the most critical ones.
Risk prioritization calls for several important capabilities:
- Full coverage of multi-cloud environments.
- Comprehensive risk detection that accounts for all types of cloud risks, including vulnerabilities, misconfigurations, malware, AI risks, API risks, data risks, identity and access management (IAM) risks, and more.
- Holistic risk analysis that accounts for cloud and business context and recognizes the interrelationships between cloud risks and resources.
Compliance
Compliance with regulatory frameworks and industry standards is mandatory for organizations, determining their authority to operate. Yet it also presents a number of challenges in cloud environments due to their ephemeral, dynamic, and distributed nature. These challenges include mapping cloud environments to compliance controls, monitoring and tracking adherence per control, addressing areas of non-compliance, preventing compliance drift, and reporting on compliance across different stakeholders.
Best practices for AWS security
Organizations can take a variety of different approaches to AWS security. That said, the following best practices can help you achieve the most optimal security outcomes.
Adopt a Cloud-Native Application Protection Platform (CNAPP)
By 2029, Gartner predicts that 60% of organizations that don’t adopt Cloud-Native Application Protection Platforms (CNAPP) technology will lack the visibility needed to achieve their zero-trust objectives.
CNAPPs consolidate essential cloud security solutions into one unified platform, enabling organizations to gain the full visibility and comprehensive detection that their multi-cloud environments demand. While CNAPPs vary in terms of capabilities and effectiveness, advanced solutions cover all cloud security use cases, including cloud configurations, workloads, identities and entitlements, sensitive data, vulnerabilities, APIs, and much more. They also provide the following benefits for AWS security:
- Unified visibility and full coverage across every layer of cloud estate.
- Holistic, contextual, and dynamic risk analysis.
- Effective prioritization of risks and attack paths.
- Fast and easy remediation.
- Streamlined and automated compliance management.
Follow AWS Foundational Security Best Practices (FSBP) and CIS AWS Foundations Benchmark
AWS provides two frameworks for helping you achieve and sustain best practices for AWS security. This includes AWS Foundational Security Best Practices (FSBP), a set of controls that detect when your AWS accounts and workloads don’t adhere to best practices related to multiple AWS services. It also includes Center for Internet Security (CIS) AWS Foundations Benchmark, a set of best practices for AWS security configurations. Both frameworks can help you fortify your AWS security.
Some advanced CNAPPs provide built-in templates for monitoring and addressing both AWS frameworks. These solutions map security risks to the relevant controls of each framework, allowing your team to easily identify, monitor, and remediate issues.
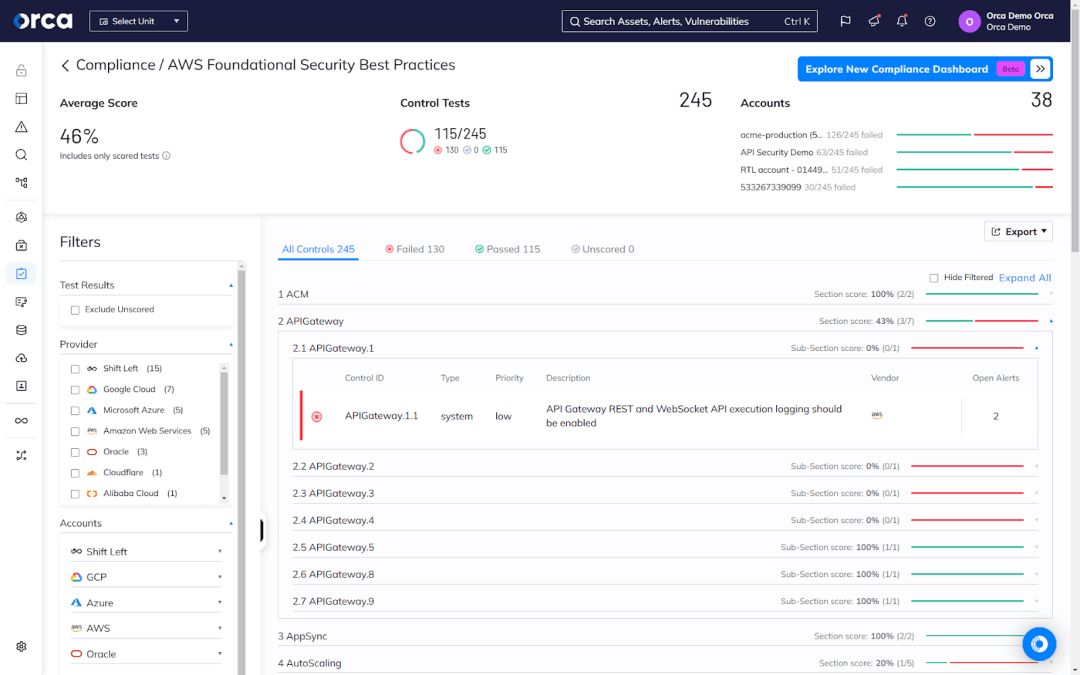
Tailor your technology
After adopting a CNAPP solution, best practice is to customize the technology to your unique needs. Most CNAPPs offer features that make it easy to tailor cloud security solutions to improve efficiency and effectiveness. Below are common ways to customize your CNAPP for better outcomes:
- Customize alerts: Create new alerts or modify existing ones to cover issues of particular concern. This may include changing the severity of an alert, changing your notification preferences, and more.
- Tailor dashboards: Dashboards generally serve as a vital tool for surfacing the most important insights that teams want to see at-a-glance. Most modern tools allow you to customize existing dashboards or build your own to display the most important intelligence.
- Create automations: Automations perform tasks without human intervention based on predefined criteria, saving your teams manual work and freeing up much-needed capacity. Most cloud security solutions offer pre-built or customizable automations. These offer significant value, especially for teams short on capacity, time, or personnel.
- Enable compliance: Select your desired compliance framework(s) to begin tracking and monitoring your current status. As covered in the previous section, most CNAPPs offer built-in templates covering major regulatory and industry frameworks. Typically, they map the resources and risks in your environment to your selected frameworks, alerting you to any failed controls and providing you the ability to remediate them.
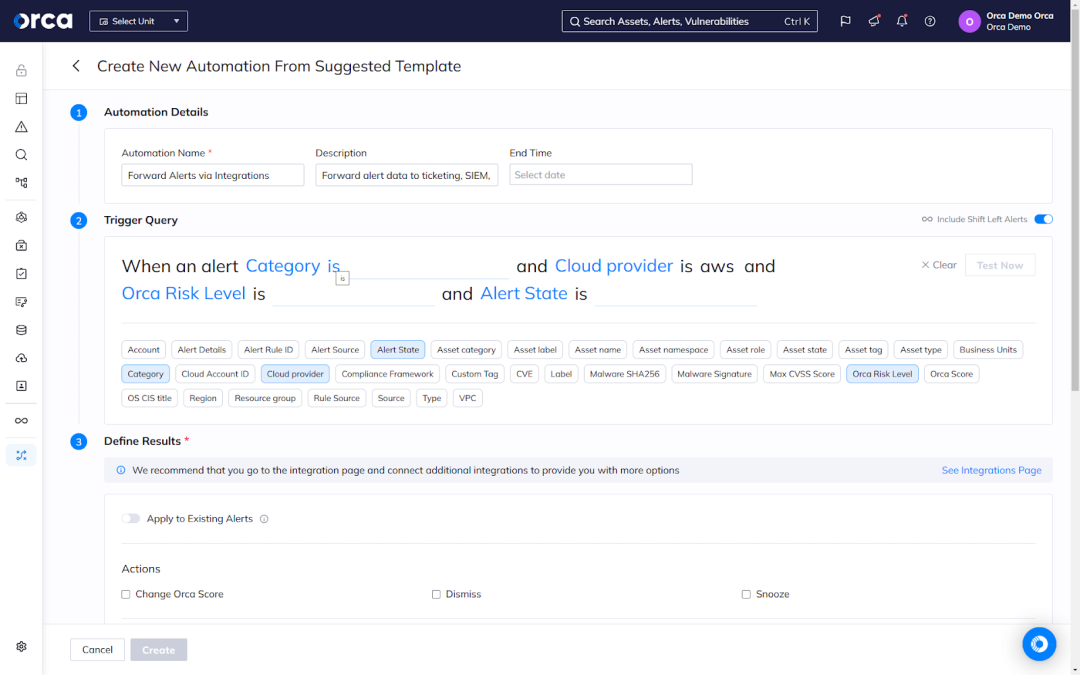
Leverage AI-driven security features
AWS has invested significantly in generative AI (GenAI) and Machine Learning technologies to enhance AI development in cloud-native environments. Some cloud security vendors have integrated AI services like Amazon Bedrock and Amazon SageMaker to accelerate critical AWS security tasks, helping to alleviate the scarcity of human resources.
Best practice is to learn about all the AI-powered security features available in your CNAPP, choose those that make sense for your organization, and train your employees on how to use them.
Using these features from the outset can help you maximize your time savings and productivity gains, as well as make your teams more receptive to incorporating security practices across the application lifecycle.
Support DevSecOps
DevSecOps refers to incorporating security throughout every phase of the application lifecycle, including the early stages of development. It represents an important discipline that helps organizations prevent security risks from reaching production environments, as well as remediate runtime risks most effectively and efficiently. Importantly, DevSecOps automates security checks and testing through advanced technology, while encouraging secure practices across different functional teams and stages of software development.
Many natively built CNAPPs provide Application Security, also known as Shift Left Security, capabilities that support DevSecOps. These capabilities include important solutions such as Software Composition Analysis (SCA), Secrets Detection, Infrastructure as Code (IaC) Security, container image scanning, Static Application Security Testing (SAST), and Source Code Management Posture Management (SCM-PM).
Most advanced CNAPPs also offer integrations with developer applications and environments, ensuring they can address security issues easily and efficiently. According to Gartner, this feature plays an important role in DevSecOps and the improvement of security outcomes.
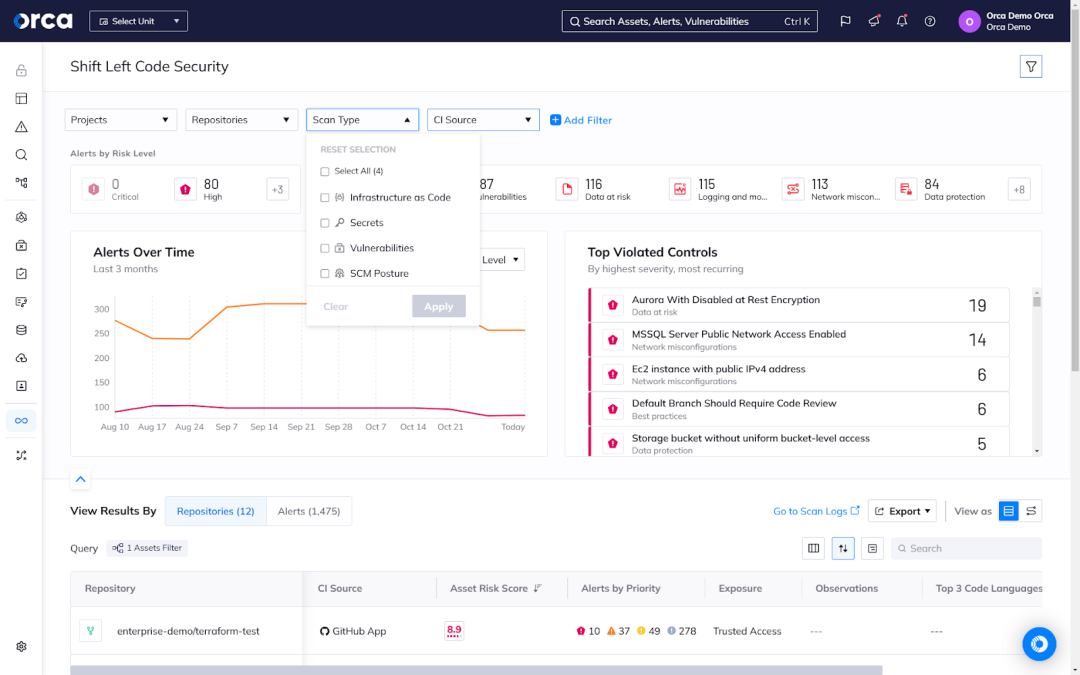
The future of AWS security
Several emerging trends continue to shape the future of AWS security, including the following developments.
AI-driven security
Seven in every 10 organizations report challenges with hiring and retaining security personnel, including competition in acquiring top candidates, finding the appropriate skills, budget limitations, and more. As organizations ramp up investments in cloud computing, security teams often lack the time, capacity, and know-how to effectively resolve the cloud risks they encounter. This illustrates the need for AI-driven security solutions, which augment labor and skill shortages with features that automate and accelerate critical tasks.
For example, the Orca Cloud Security Platform offers AI-Driven Remediation, a feature that generates remediation code and instructions on-demand, with the output tailored to an organization’s unique remediation process. The high-quality instructions help accelerate the resolution of runtime risks, and compensate for a lack of expertise for specific programming languages, cloud environments, and more.
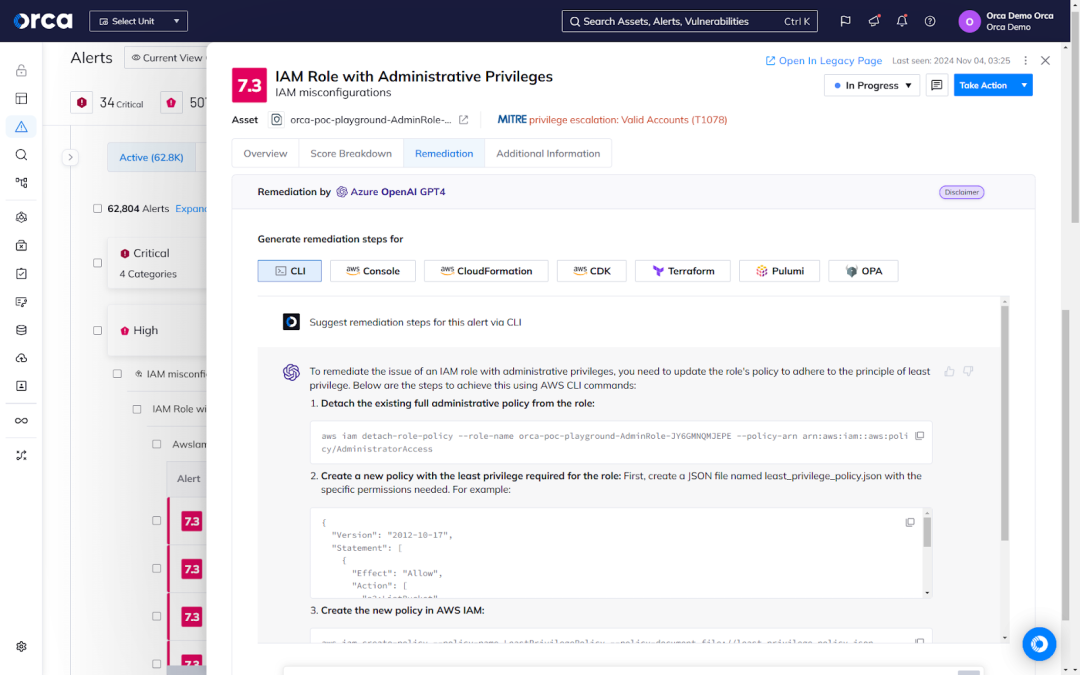
Orca also offers its AI-Driven Search feature, which saves security practitioners the need to learn the query language of AWS or any other cloud provider. Using the feature, they can discover any answer about their cloud estate by asking a question in plain language, with more than 50 languages supported.
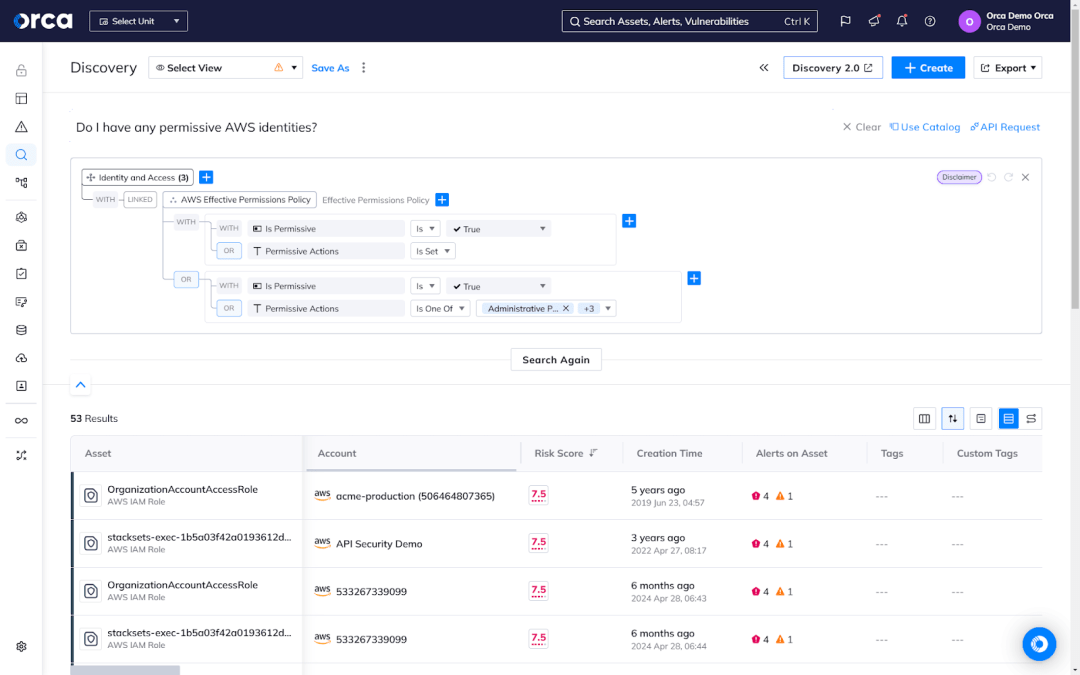
AI innovation and risks
According to the Orca 2024 State of AI Security Report, most organizations have adopted the AI services of their cloud provider to develop at least one custom application. This represents a significant percentage, meaning that many companies are not only using and testing AI models, but also creating their own custom solutions and integrations specific to their cloud-native environment.
As AI innovation in the cloud ramps up, so do the associated security risks. The State of AI Security Report found that 62% of organizations have deployed an AI package with at least one CVE. Regardless of its severity, any CVE can constitute a critical risk if it supports a high-severity attack path—a collection of interconnected risks that attackers can exploit to endanger high-value assets. This represents one type of risk associated with AI in cloud services, with others including misconfigurations, exposed AI models, insecure access, and more.
To address AI security risks, some CNAPP solutions have introduced AI Security Posture Management (AI-SPM) capabilities to provide full visibility and risk detection for AI services, models, and packages used in the cloud. The Orca Cloud Security Platform’s AI-SPM solution covers more than 50 AI models and packages, and integrates with Amazon Bedrock and Amazon SageMaker.
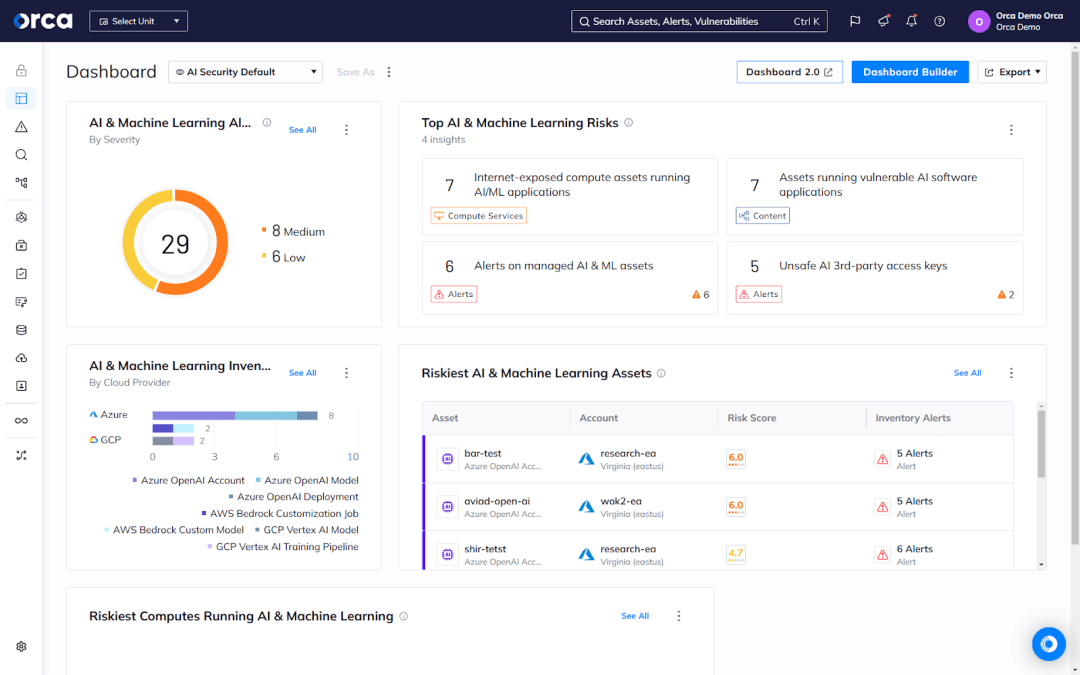
About the Orca Cloud Security Platform
The Orca Cloud Security Platform is an agentless-first CNAPP that detects, prioritizes, and remediates security risks and compliance issues across the multi-cloud environments of AWS, Azure, GCP, Oracle Cloud, Alibaba Cloud, and Kubernetes. A true CNAPP, the Orca Platform provides full visibility, comprehensive risk detection, and quick time to value across every stage of the application lifecycle.
Orca Security is a AWS Security Partner and global winner of the 2022 AWS Security Partner of the Year Award. Orca has achieved the AWS Security Competency and integrates with more than 100 AWS services and products, including EC2, ECS, EKS, Fargate, Lambda, GuardDuty, CloudTrail, Bedrock, Security Lake, and more.
To see how the Orca Cloud Security Platform can help you fortify your AWS security, schedule a personalized demo with one of our experts.
Conclusion
The value of public cloud services remains clear. Gartner and others predict cloud computing to become a necessary vehicle not only for future innovation, but business continuity. The future goes through AWS—the most popular cloud provider currently—and other major players such as Azure and GCP.
Yet capitalizing on this opportunity requires organizations to prioritize their AWS security and reimagine how they approach it. This involves equipping shorthanded security teams with tools that can compensate for gaps in knowledge, skills, and capacity; embracing methodologies such as DevSecOps; and adopting advanced technology, such as CNAPPs, which can enhance and automate cloud security functions.
FAQs
What are the main security risks of AWS?
The main security risks of AWS include: vulnerabilities, misconfigurations, identity and access management (IAM) risks, sensitive data exposure, API risks, malware, lateral movement risk, and AI risks. Organizations commonly encounter these risks in cloud provider environments, including AWS and their competitors.
What are the key benefits of AWS security?
AWS security helps organizations protect the availability, integrity, and confidentiality of their cloud-native applications, data, and environments. Gartner predicts cloud computing to become a necessary business investment by 2028 for organizations looking to remain competitive in their marketplace. AWS security enables organizations to leverage the benefits of cloud computing safely and securely.
What are the different types of AWS security?
AWS security involves multiple disciplines and solutions, including those provided by AWS as well as third-party cloud security vendors.
Security offered by AWS includes the following:
- Infrastructure security including DDoS mitigation, traffic encryption, and network firewalls.
- Data security including data encryption and creating custom encryption frameworks.
- Configuration management including inventorying, analyzing, and auditing AWS resources.
- Identity and access controls including customizable access levels, password policies, multi-factor authentication (MFA), and single sign-on (SSO).
- Monitoring and logging for tracking cloud activity and detecting anomalous or malicious behavior.
Numerous types of third-party security solutions exist. However, Cloud-Native Application Protection Platforms (CNAPPs) have become the most prominent choice for augmenting the native AWS security features. CNAPPs protect cloud-native applications and environments across the entire application lifecycle, offering a comprehensive solution and a superior alternative to multiple point solutions.






