Blog
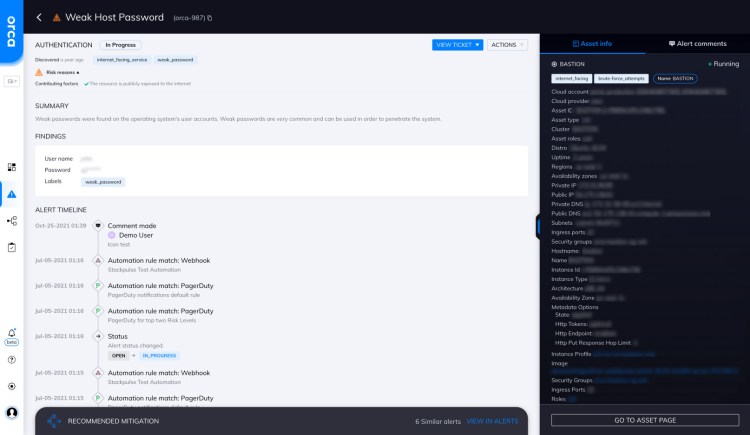
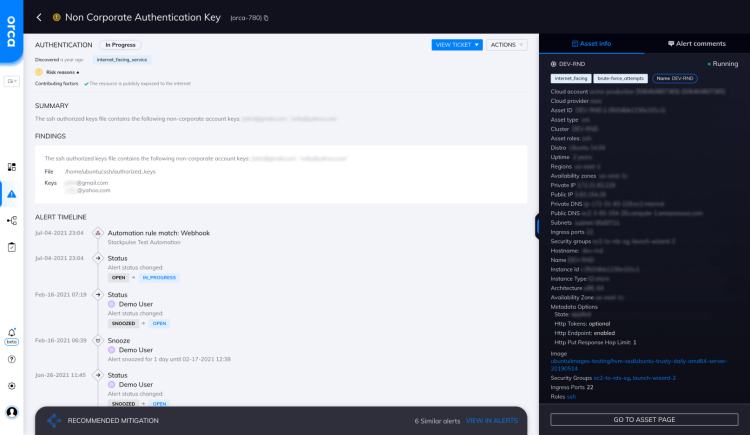
Non-Corporate Authentication Key
The SSH authorized_keys file contains the following non-corporate account keys: 'xxx@gmail.com', 'xxx@yahoo.com'. Illegitimately added keys usually have non-corporate usernames and...
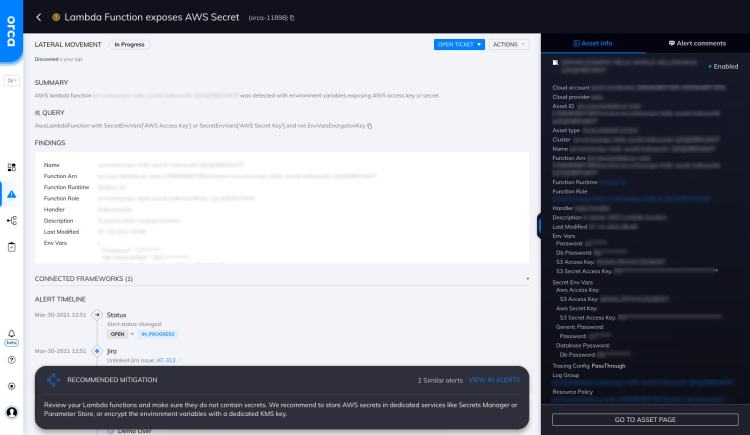
Lambda Function Exposes AWS Secret
AWS lambda function {AwsLambdaFunction} was detected with environment variables exposing AWS access key or secret.
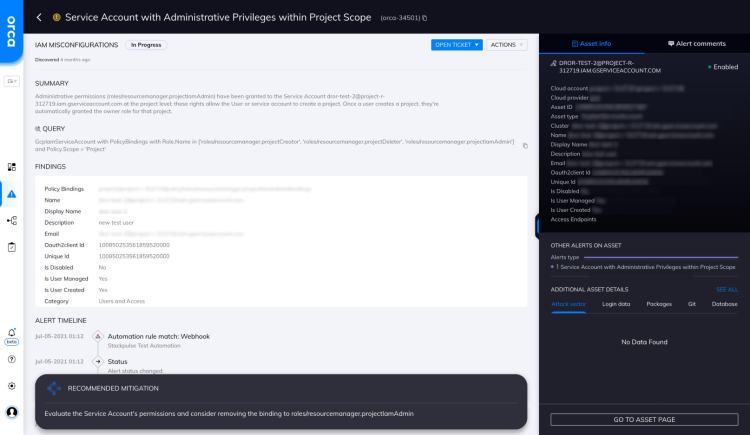
Service Account with Administrative Privileges within Project Scope
Administrative permissions ({PolicyBindings.Role}) have been granted to the Service Account {GcpIamServiceAccount} at the project level; these rights allow the User...
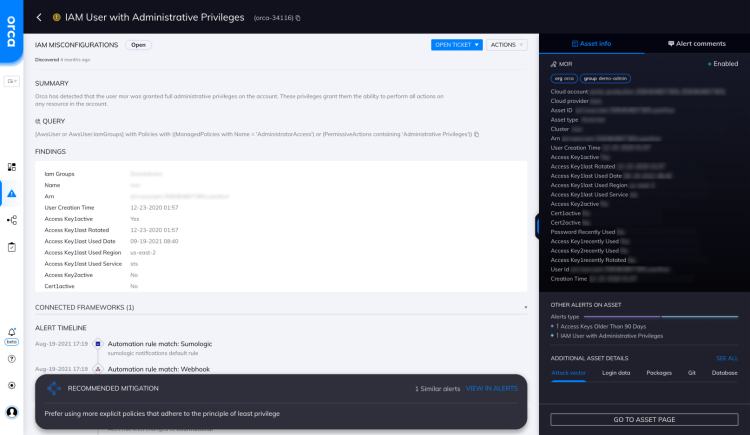
IAM User with Administrative Privileges
Orca has detected that the user {AwsUser} was granted full administrative privileges on the account. These privileges grant them the...
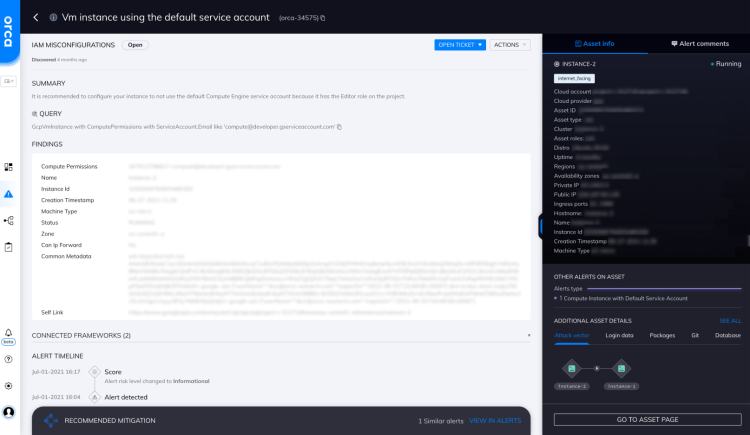
VM Instance Using the Default Service Account
It is recommended to configure your instance to not use the default Compute Engine service account because it has the...
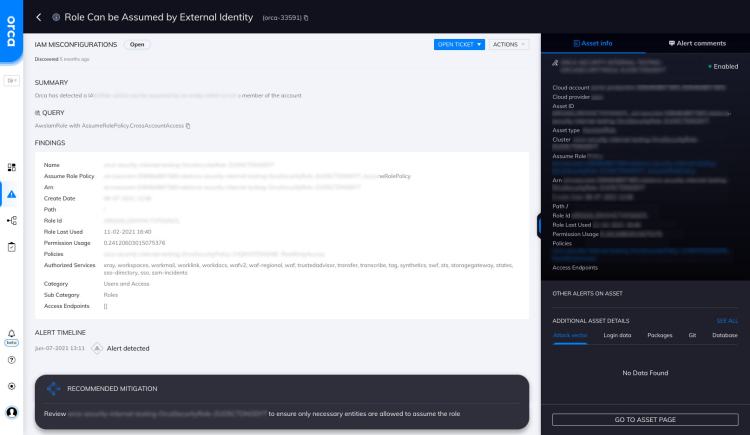
Role Can be Assumed by External Identity
Orca has detected a IAM Role which can be assumed by an entity which is not a member of the...
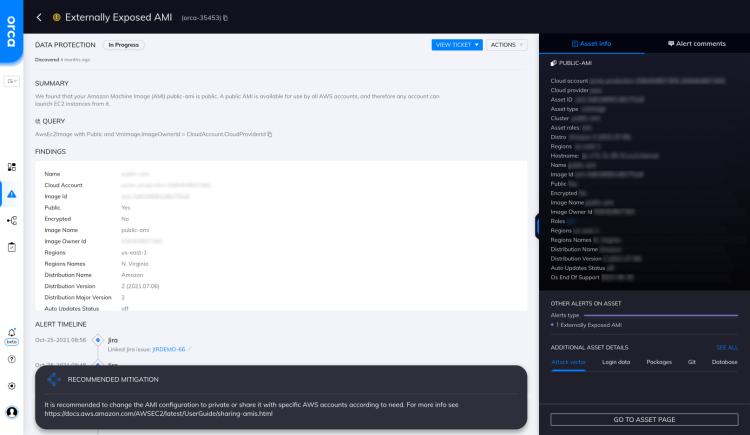
Externally Exposed AMI
We found that your Amazon Machine Image (AMI) {AwsEc2Image} is public. A public AMI is available for use by all...
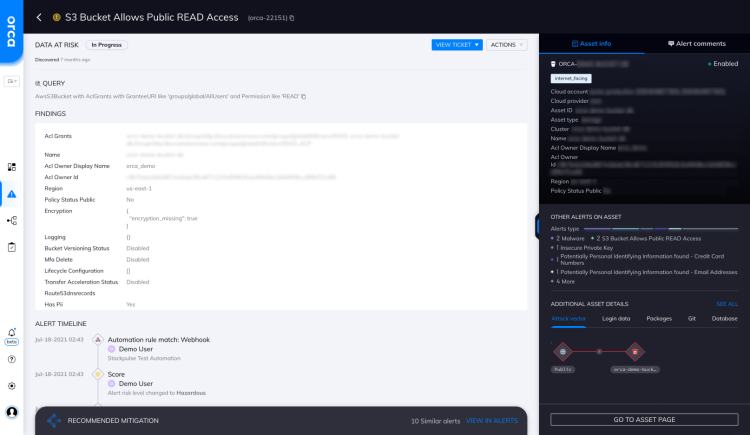
S3 Bucket Allows Public READ Access
Ensure that your S3 buckets content cannot be publicly listed in order to protect against unauthorized access. An S3 bucket...