Identity misconfigurations represent one of the most dangerous risks in cloud security. Risk detection and extensive visibility into users, roles, and policies has never been more essential for security teams.
Orca now integrates with Google Workspace, providing security teams with extensive, rich context about Google Cloud user policies, including vital security settings and usage history. Orca users now benefit from enhanced security coverage and visibility into Google Cloud environments, covering risks like disabled multi-factor authentication, inactive accounts, weak passwords, and more.
Cloud Identity Risks Have Never Been More Prevalent
In the ever-evolving landscape of cybersecurity, the traditional concept of a fortified perimeter that once safeguarded organizations’ sensitive data and digital assets has become increasingly porous and inadequate. As organizations transition to cloud-based infrastructures and remote work has become more common, a profound paradigm shift has occurred. Now, more than ever, “identity is the new perimeter,” and this transformation is particularly pronounced in the realm of cloud security.
Merely recognizing the importance of best practices in Identity and Access Management (IAM) is not enough. Human errors and forgetfulness are common, misconfigurations are widespread, and when it comes to maintaining healthy identity security hygiene, significant gaps remain. In the 2022 State of Public Cloud Security Report, published by Orca Security, research showed 76% of organizations had AWS credentials that had not been used for 90+ days. When it came to enforcing a foundational security measure like multi-factor authentication (MFA), 58% of organizations had MFA disabled for at least one privileged user in Azure. This means that it is essential to not only follow best practices, but also to have an automated system that checks and notifies when any of the best practices are not being followed.
Continuous monitoring of cloud identity and entitlement risks is an important pillar of the Orca Cloud Security platform. With the new Google Workspace integration, we’re now expanding our Cloud Identity and Entitlement (CIEM) capabilities even further.
Why Integrate with Google Workspace?
Google Workspace encompasses a suite of cloud-based tools, including popular applications like Gmail, Google Calendar, Google Drive, Google Docs, and Google Slides, among others, tailored to boost productivity and collaboration. Moreover, it offers centralized user management, authentication, and authorization capabilities. Given that many of these users also engage with Google Cloud, and that security insights like user attributes are stored in Google Workspace, integrating that data into Orca’s cloud security platform greatly benefits our joint customers.
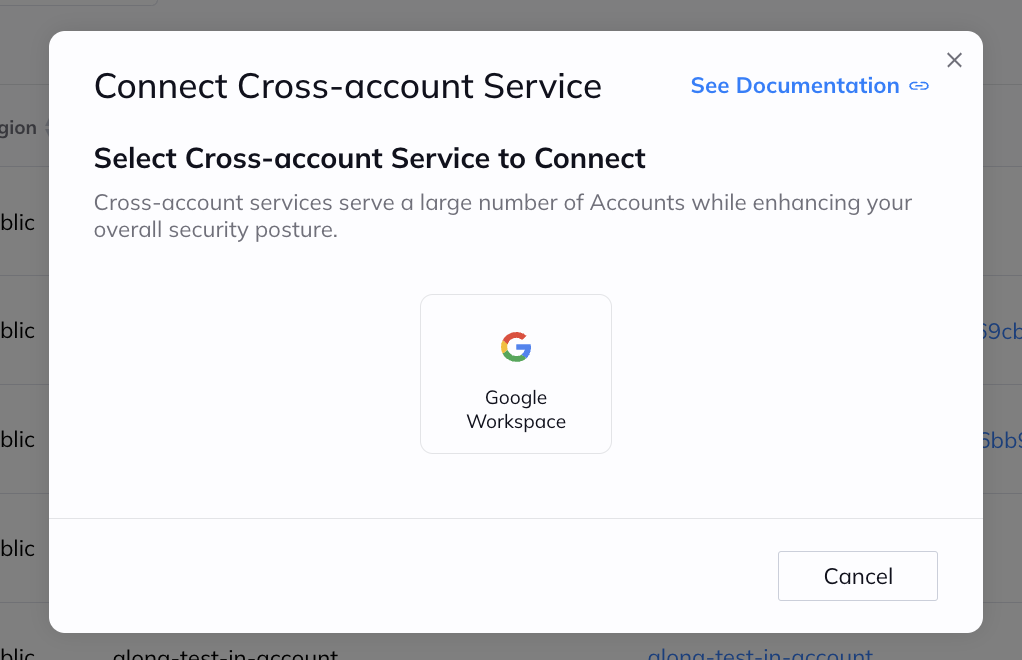
Orca Security allows for easy connection to Google Workspace accounts
The data from the Google Workspace integration enhances security teams’ ability to detect identity misconfigurations, follow least-privilege best practices, and identify suspicious user activity. Orca’s insights into the broader cloud risk context, combined with comprehensive Google Workspace data, surfaces how risks can be combined to create dangerous attack paths, thereby improving risk prioritization, and enabling security teams to remediate strategically.
Detect Worrisome Identity Misconfigurations
Orca excels at detecting identity misconfigurations and associated risks. Equipped with security insights that include MFA status, inactive accounts, password history, and more, security teams will have the deep visibility that is the foundation for security.
For example, Orca alerts on the following identity misconfigurations:
- Multi-factor authentication not enabled
- Unused credentials and roles
- Users with administrative privileges
- Users with unchanged passwords for 90+ days
- And more…
Orca alerts to a Google Cloud user with multi-factor authentication not enabled
Beyond misconfigurations, Orca also alerts security teams to suspicious activity related to identities. The integration will enable Orca to expand Cloud Detection and Response (CDR) capabilities to anomalies related to Google Workspace users. This enables SOC and IR teams to accelerate triage and investigation into potential security events.
How Orca Uses Context to Prioritize Risks
However, just generating a list of alerts is not the goal. Effective cloud security hinges on the ability to prioritize risks efficiently, a fundamental requirement in the face of the deluge of alerts generated by many security tools. To be efficient and stay one step ahead of the attackers, security teams must focus on addressing the most critical risks first.
To do that effectively, insight into the broader cloud risk context is essential. Instead of providing identity and access privilege management in a siloed solution, Orca combines all detected risks in a single platform, including vulnerabilities, misconfigurations, malware, lateral movement, the location of sensitive data, and more.
Orca uses this context in two powerful ways:
- To determine the severity of an individual risk
- To highlight dangerous attack paths to business critical assets.
All Orca alerts include an Orca Risk Score that considers factors such as severity, exploitability, and potential business impact. This prioritization mechanism empowers organizations to apply their resources where they matter most, ensuring a more robust defense against identity-related threats.
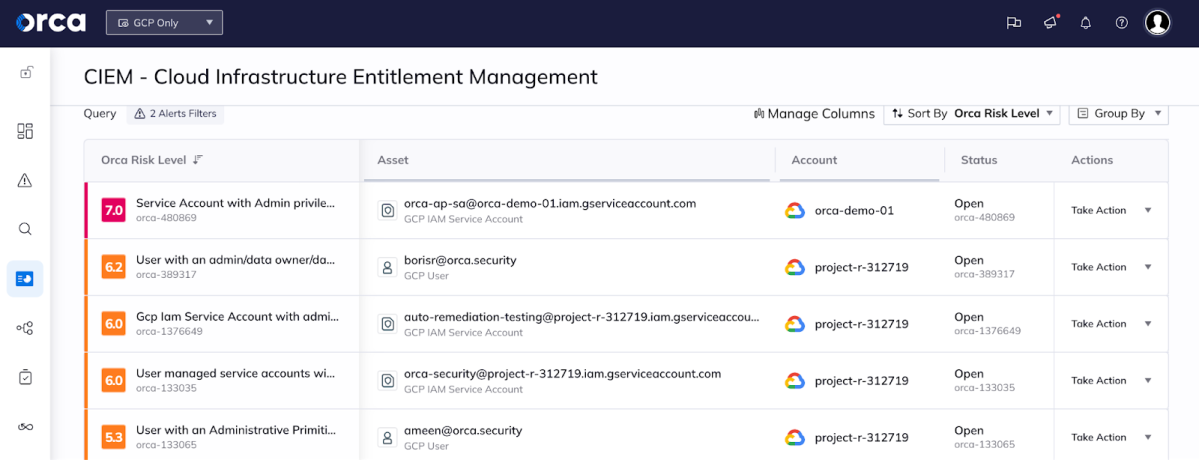
Orca show identity-related risks listed by severity and potential impact
Going beyond individual risks, through the implementation of Attack Path Analysis, Orca proactively notifies organizations of potential threats where attackers might exploit individual identity-related vulnerabilities within the cloud environment to create hazardous pathways leading to critical assets. This approach enables security teams to prioritize remediation efforts, concentrating on mitigating the most perilous risks to safeguard sensitive data, relieving alert fatigue and mitigating the risk of detrimental data breaches.
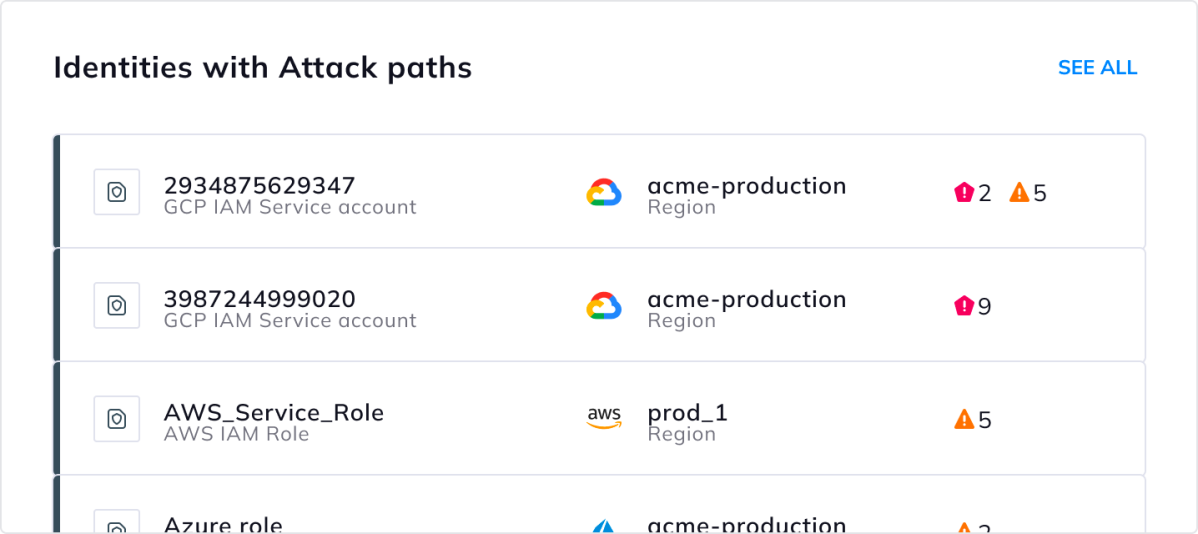
Orca Identities cloud assets with high-impact attack paths
Accelerate Risk Remediation
Orca alerts not only inform you of potential security risks but also enable swift resolution by providing guided remediation steps as well as automated remediation capabilities. All Orca alerts come with remediation instructions, allowing you to take specific steps to address the underlying issues. This includes AI-generated step-by-step instructions and code directly available within the alert in the Orca platform, which can be easily copied and pasted into relevant platforms like a CLI, Terraform, and Google Cloud Deployment Manager, simplifying configuration adjustments.
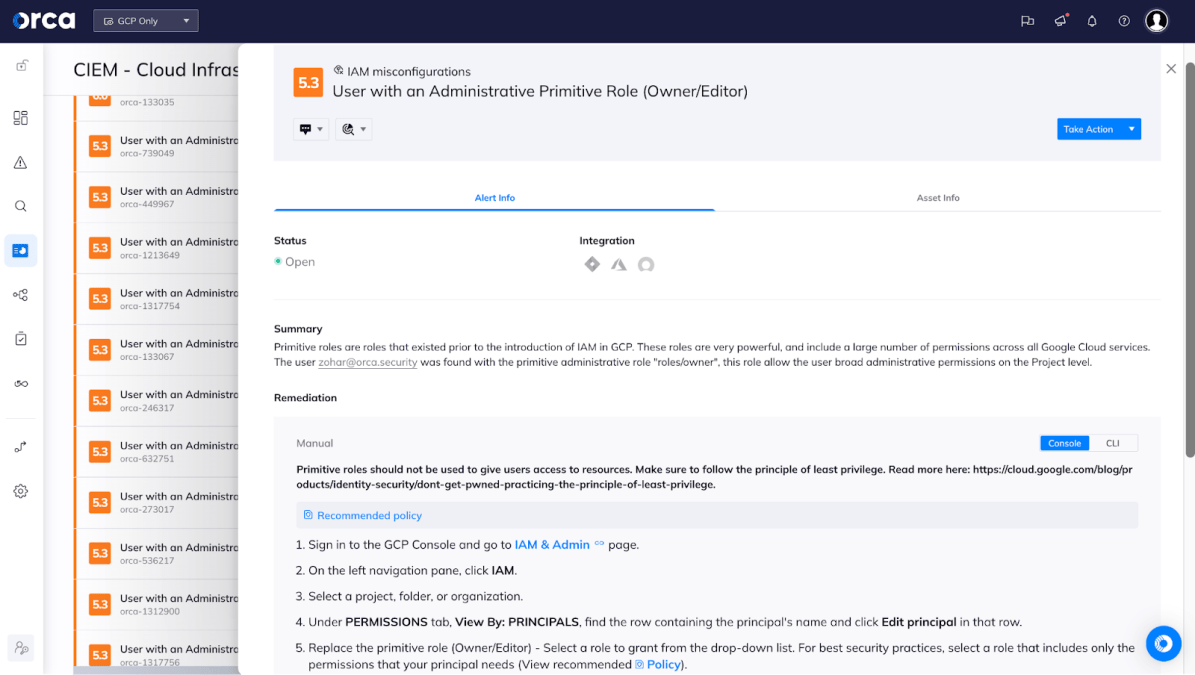
An Orca alert with guided remediation
In addition, Orca Security offers full automatic remediation, designed to swiftly resolve both common and complex security alerts without any manual effort. By enabling auto remediation at the account level and configuring your own automated actions for specific alerts, you can significantly reduce Mean Time to Remediation (MTTR), strengthen your overall security posture, and meet compliance requirements efficiently.
Advanced Querying of Identity and Entitlement Risks
In addition to generating alerts Orca allows users to perform advanced queries on entitlement and identity data, using 2000+ built-in alert templates or custom queries.
Examples of easy queries include:
- Which roles have not been used in 30 days?
- Do we have users without MFA enabled?
- Which are my unused custom roles in Google Cloud (see screenshot below)
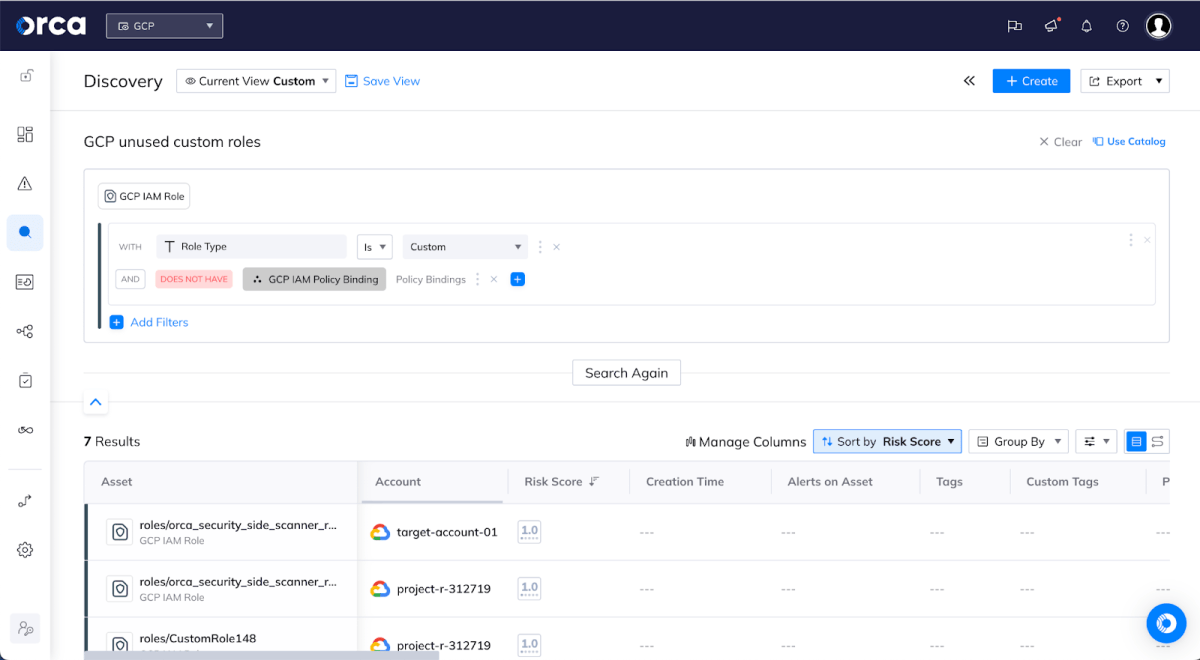
Query results showing unused custom roles in Google Cloud.
Furthermore, with Orca’s new AI-powered search, users can now search by asking plain language questions, empowering security teams to quickly and efficiently query their cloud environments up to the deepest granular level, and make data-driven decisions.
Here we ask Orca to “Find GCP Roles Not Used in the last 30 days.”
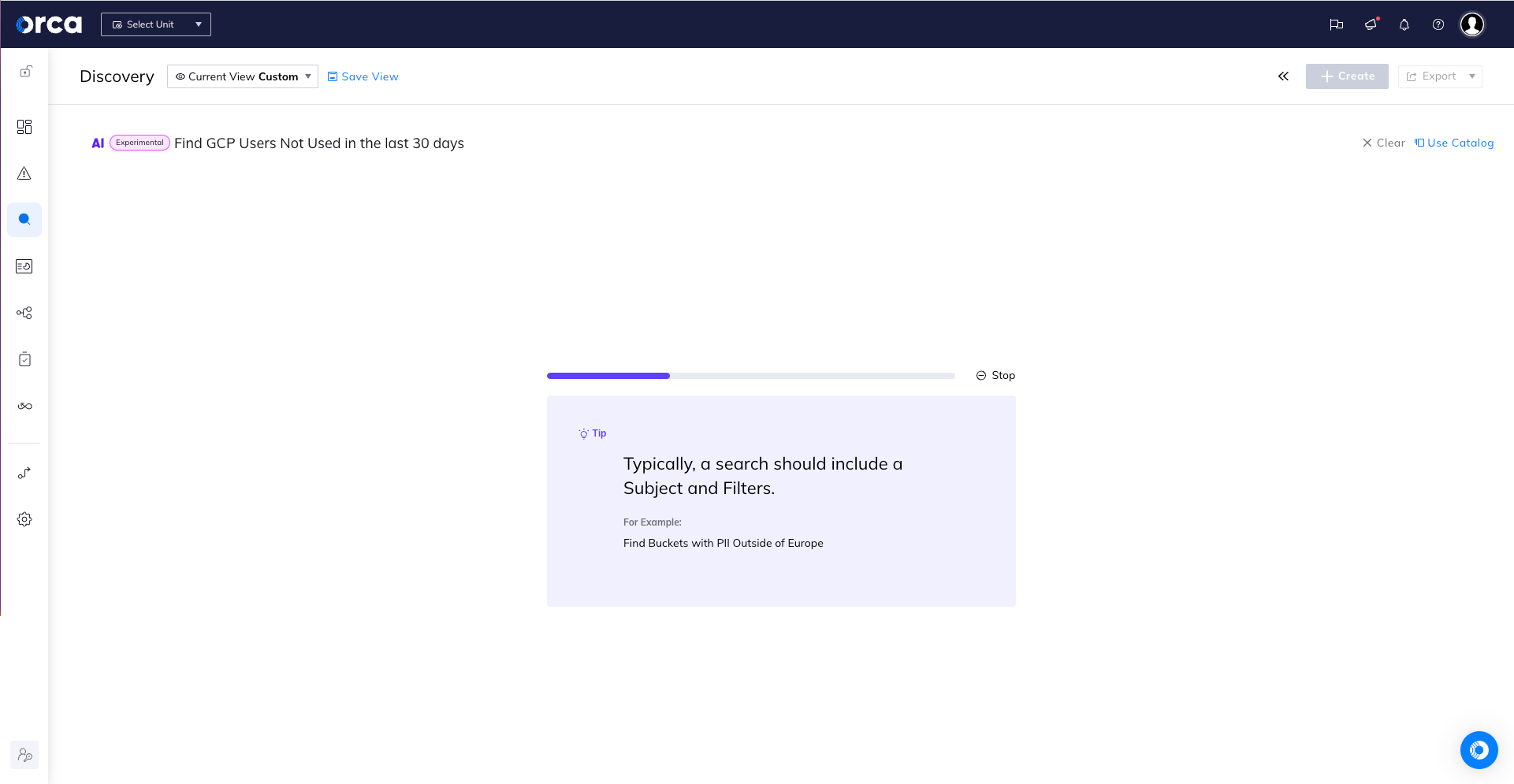
Within a few seconds, we see the results:
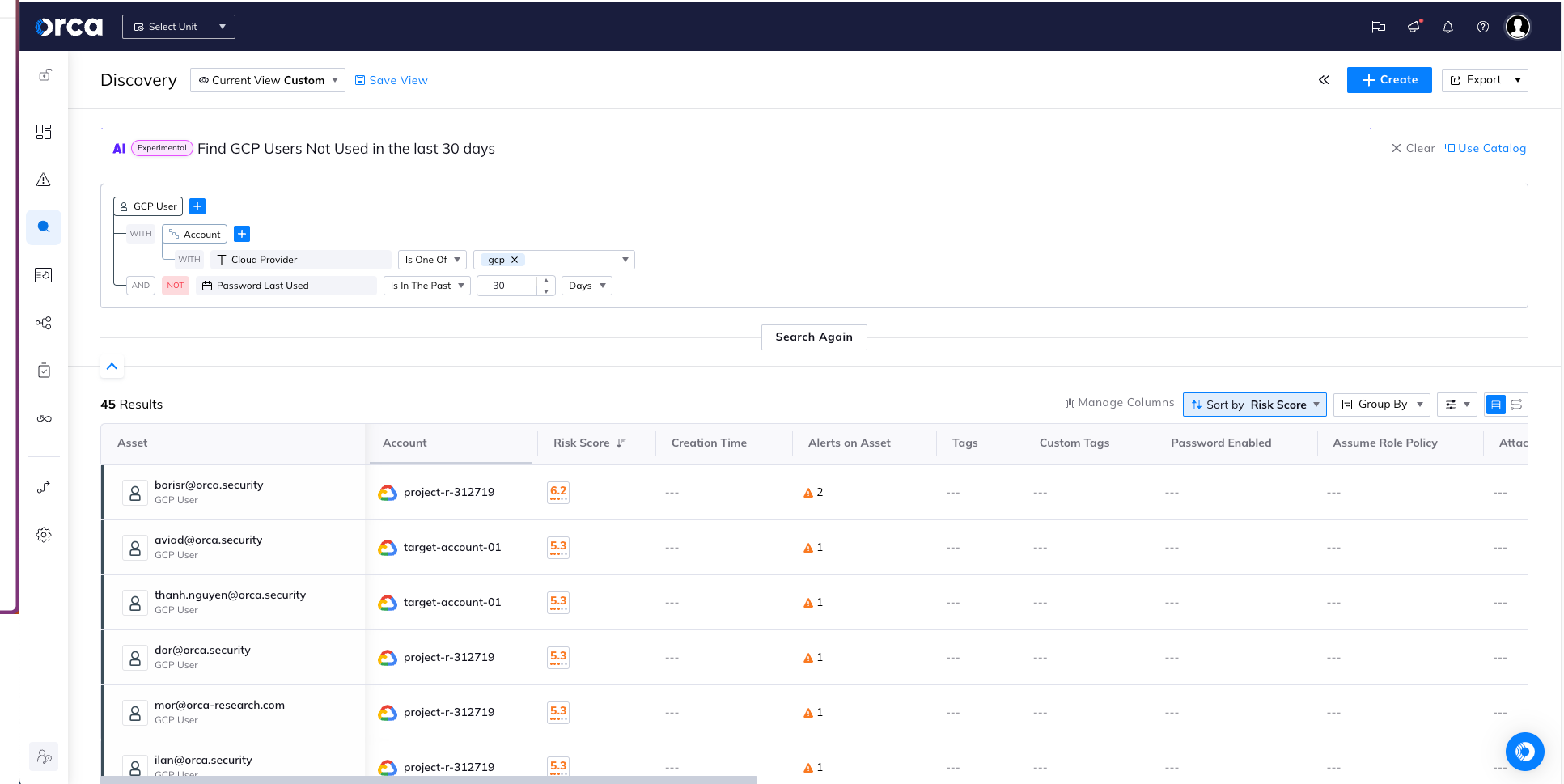
As you can see, the AI-powered search makes querying the Orca platform as easy as a simple question or request.
Learn More
To learn more about Orca’s Google Cloud security capabilities, visit our Google Cloud website. You can also view our latest recorded demo of the Orca Platform, or request a personalized demo for your team.






