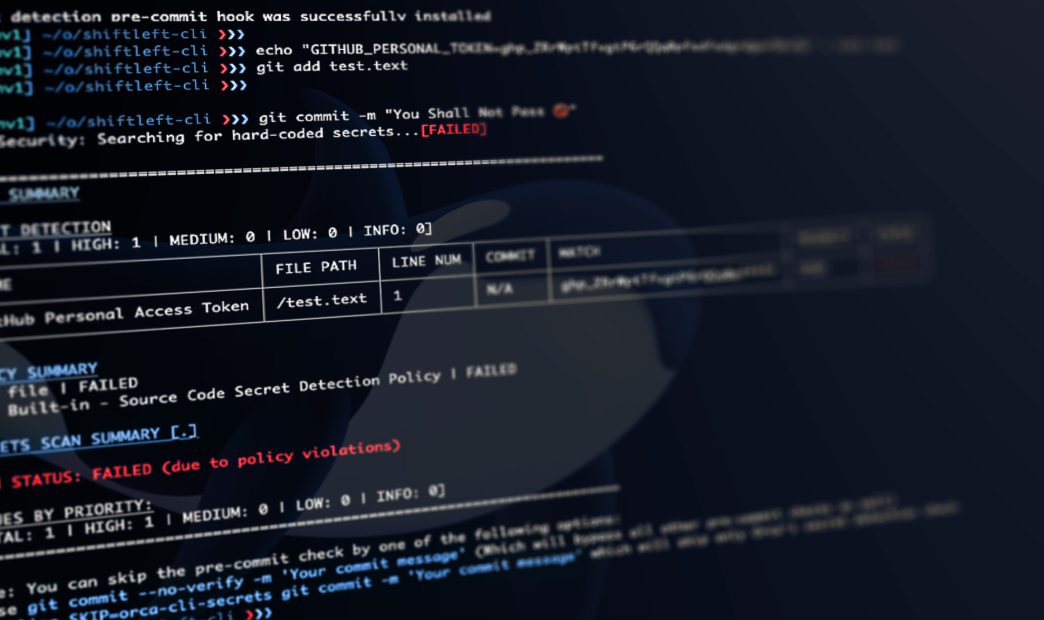
Our 2023 honeypot research showed that it takes attackers just two minutes to discover an exposed secret on GitHub before exploiting it. Since code repositories like GitHub are monitored so heavily by attackers and secrets are discovered so quickly, it’s vital that organizations ensure that any secret leakage is prevented before committing code. This is why it’s so important to scan code repositories for exposed secrets across the entire software development lifecycle (SDLC), and not only in production.
In this post, we detail how the Orca Cloud Security Platform embraces Shift Left Security and integrates seamlessly into the CI/CD process, detecting risks such as vulnerabilities, malware, and misconfigurations, as well as exposed secrets in source code packages long before code is built or shipped.

Seamless integrations with development apps
Secrets detection starts by integrating with development platforms, and Orca offers ample flexibility in this area. Orca’s GitLab App and GitHub App allow organizations to quickly integrate Orca’s secrets scanning into the respective tools without any manual work.
Organizations using other development platforms can take advantage of Orca CLI, Orca’s lightweight command-line interface that makes it easy to embed secrets detection into your development platform of choice.
Orca’s seamless integrations with development platforms maximize ease and efficiency, reducing team friction and avoiding developers having to deviate from their existing tools or workflows.
Flexible policies and centralized management
After integrating with your repositories, Orca enables security teams to easily create and enforce flexible policies for security issues. Teams can set guardrails to block builds or notify developers without disrupting workflow, applying policies to specific or all repositories as needed.
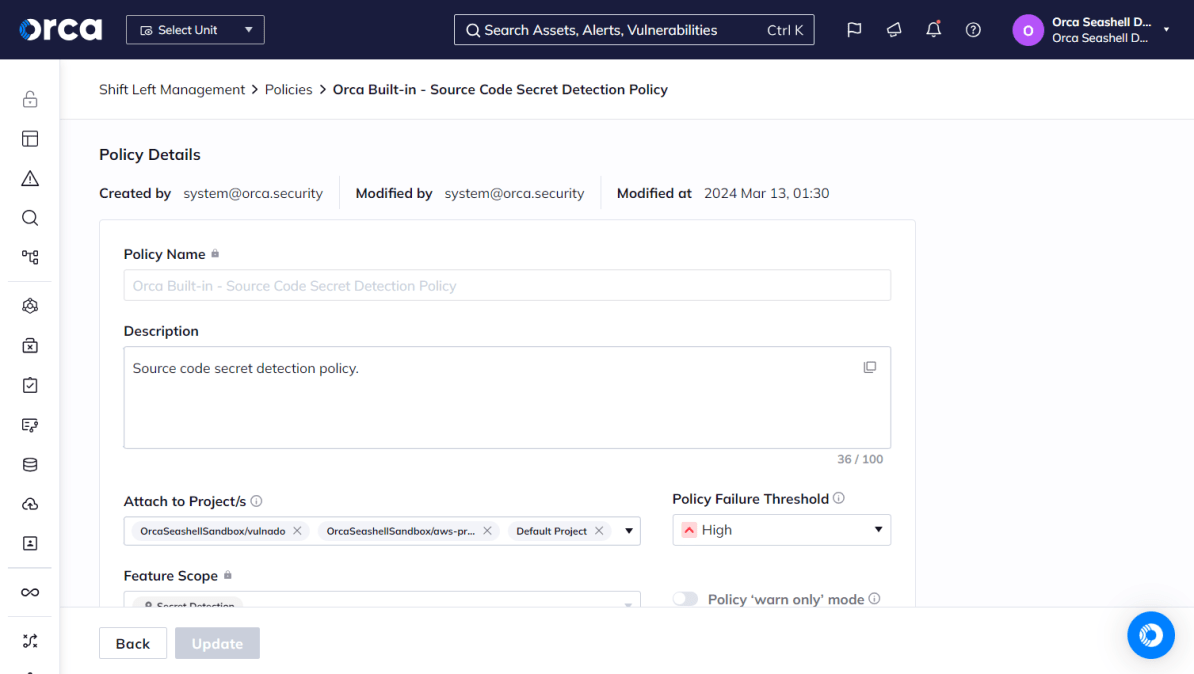
Orca also offers comprehensive visibility and control over secret detection with centralized logging and full alert management. Security teams can monitor all scans in one place, receiving alerts and gaining a detailed, global view of potential security risks in the codebase.
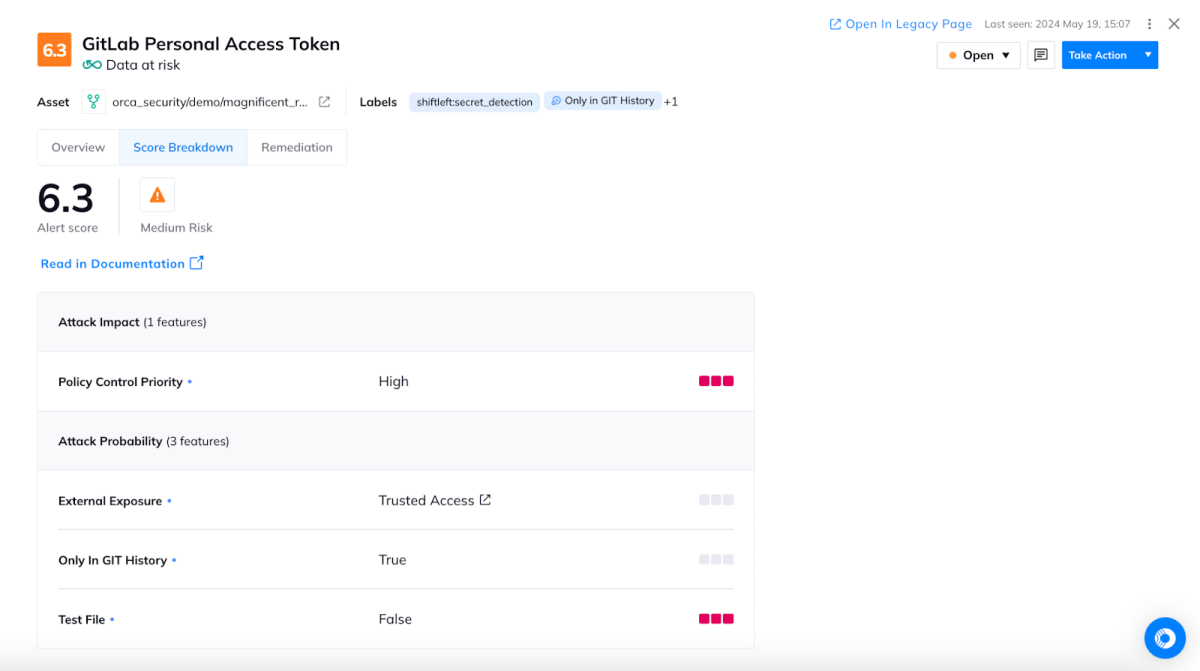
Enhanced secrets detection
Orca’s secrets detection combines in-depth scanning with dynamic alert scoring to effectively prioritize risks and accelerate resolution efforts. Secrets scanning occurs whenever developers push something new or create a pull request. Orca’s GitLab App and GitHub App will scan any code change, including side branches, and create dynamic alerts for disclosed secrets.
Orca also scans your entire Git history for the existence of any secrets. When removing exposed keys, this will only remove them from the newest commit, but they’ll still be in the history. This is why attackers are also scanning for exposed keys in the Git history, and it’s important to ensure that no secrets are lurking there.
After each scan, Orca prioritizes the risk of detected secrets using our complete, continual awareness of your repositories and entire cloud estate. This includes the visibility of your repositories, if the secret exists in your history, if the secret resides in a test file, and when the secret was first disclosed, to name a few factors. For example, a secret disclosed in a public repository carries greater urgency and risk than one disclosed a year ago in a private repository. This gives your security and development teams the most reliable guidance for remediation efforts.
Orca also offers built-in automation rules for integrations with popular tools like Jira, PagerDuty, ServiceNow, Slack, and many others, allowing you to automate and accelerate critical tasks. For example, you can easily create an automation rule that generates a service ticket in Jira for any new Orca alert and routes it to the appropriate developer to address.
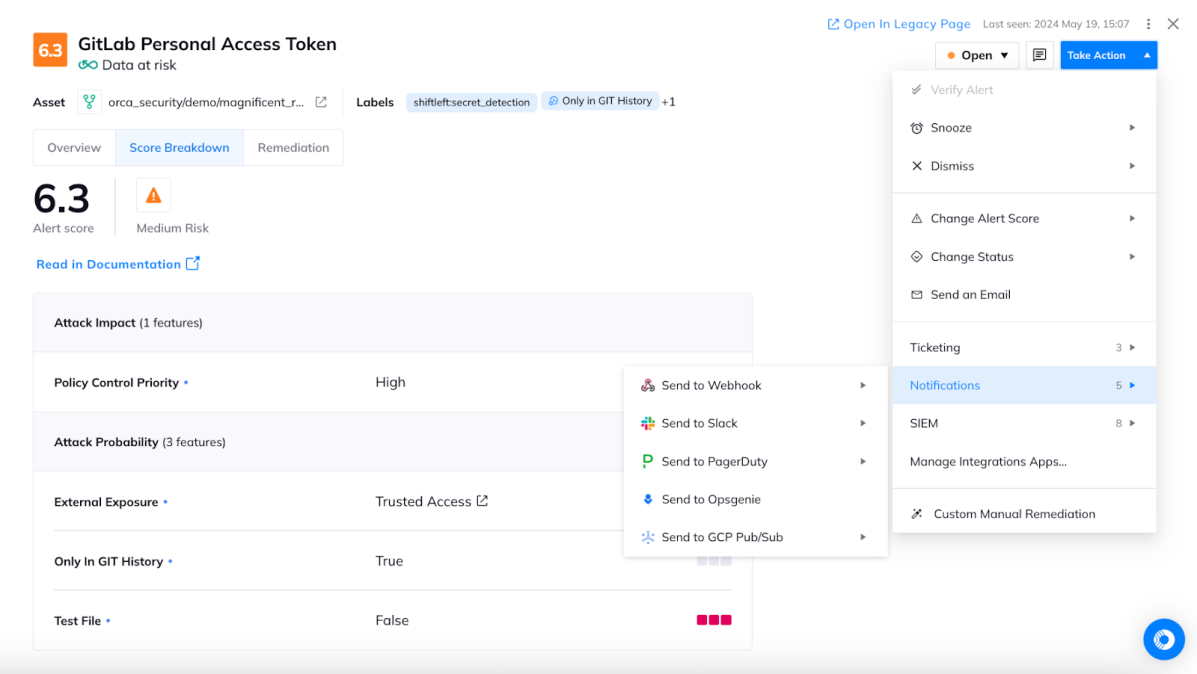
Enhanced visibility and capabilities for developers
Effective secret management relies heavily on developers’ active participation. Orca’s approach enhances this collaboration by performing code reviews to detect secrets, with in-line code comments to highlight the risk. This instant review ensures that developers are immediately alerted and can pinpoint the exact location where a secret was introduced, allowing them to quickly address security concerns and policy violations without disrupting their existing workflows or tools.
Additionally, Orca offers a pre-commit hook that prevents secret disclosure by detecting potential issues before developers commit code to a repository. This early-stage prevention not only streamlines development workflows but also eliminates the need for extensive post-commit security measures, such as risk analysis and secret rotations that would be necessary in the event of a secret disclosure.
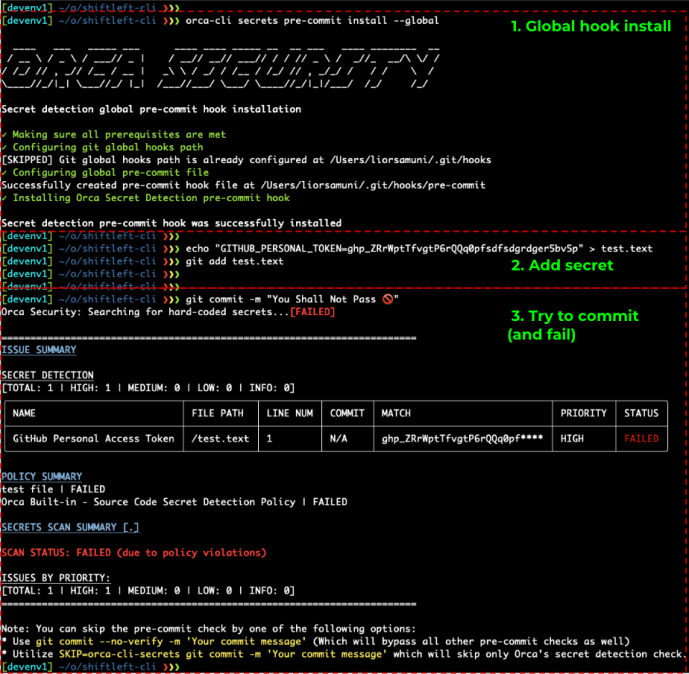
By bringing security issues into focus for developers, Orca helps facilitate their buy-in and compliance, while also fostering a more security-conscious mindset.
Secrets detection: Just the beginning of Shift Left Security
When it comes to cloud security, preventing risks is the best approach for cloud-native organizations. That’s why Orca remains committed to introducing new features and enhancements for its Shift Left Security solution, including detecting secrets in source code. Stay tuned for upcoming announcements that highlight our complementary capabilities for shifting security left.