The Challenge
Development, DevOps, and Security Teams Are Operating in Silos
Securing applications calls for bridging the gap between Cloud and Application Security. Yet existing tools and approaches only present barriers. Orca provides unified visibility and capabilities that span the full application pipeline, enabling complete lifecycle protection and seamless collaboration designed with security, development, and DevOps teams in mind.
Developers need to identify vulnerabilities and security issues while shipping code quickly.
DevOps teams must manage policies and create integrations for multiple tools, duplicating efforts and hindering consistency.
Security teams struggle with complex integrations, lack of shared context, and contradictory alerts.
Our Approach
A Unified Platform to Bring Teams Together Across the Application Lifecycle
The Orca Cloud Security Platform provides comprehensive security and compliance checks across the SDLC and helps secure applications across their lifecycle. The Orca Platform offers SCM Posture Management (SCM-PM) and advanced code security, including Software Composition Analysis (SCA), Static Application Security Testing (SAST), Secrets Detection, IaC security, and container image scanning. Orca also traces cloud risks to their code origins with its Cloud-to-Dev capabilities, enabling users to transform alerts into instant pull requests (PRs), accelerate remediations, and address issues at their source.
Code
Developer code is continually scanned during every code review and undergoes SCA, SAST, IaC scanning, and Secret Detection.
Build
Container images and IaC templates are scanned as part of regular, continuous integration (CI) / continuous delivery (CD) workflows.
Deploy
Registries are continually monitored to ensure application images are secure before deployment, with guardrail policies in place to prevent insecure deployments.
Run (and Back Again)
Production environments are monitored with contextual and prioritized alerts that link cloud risks to source code and enable AI-driven remediations and one-click PRs.
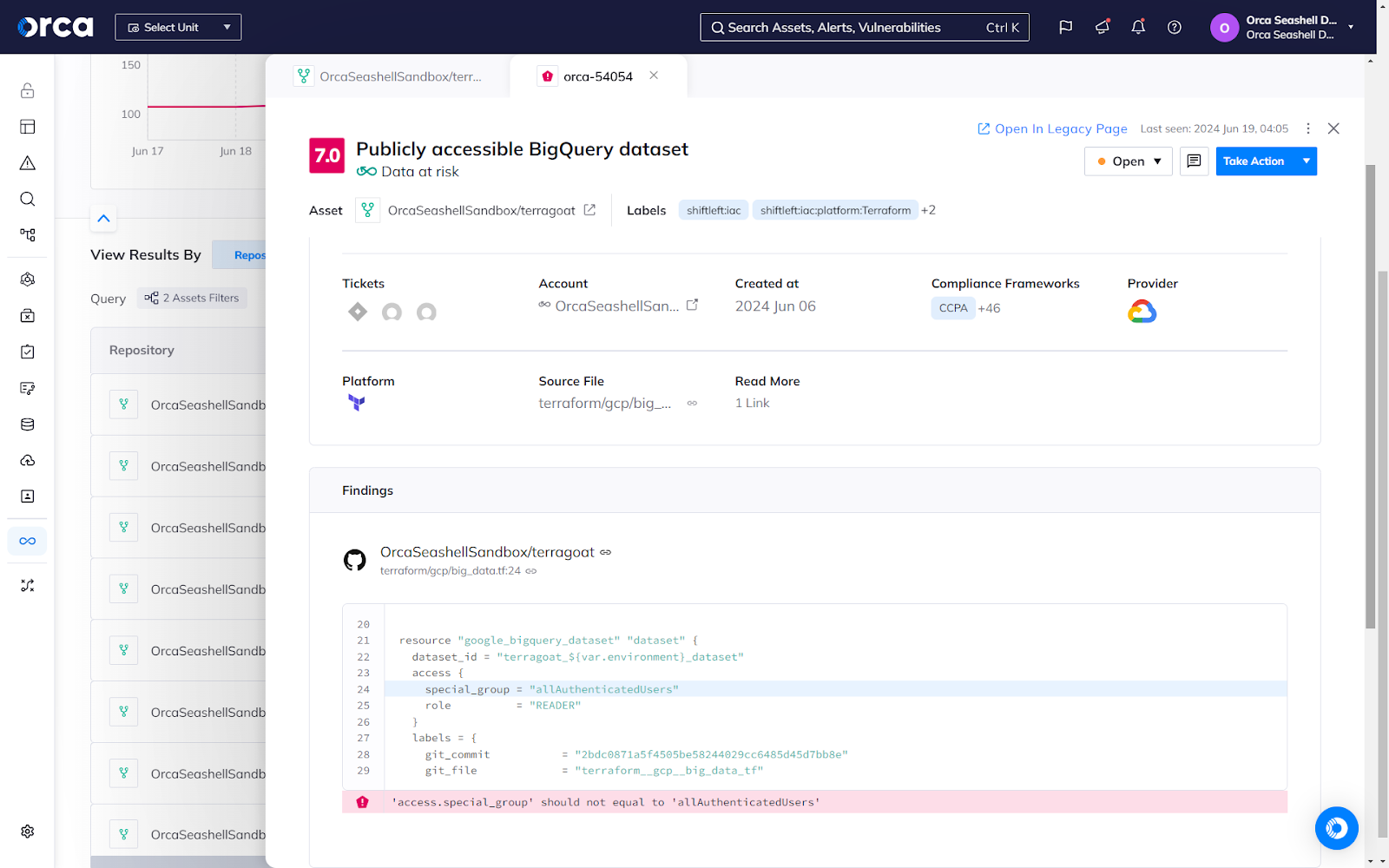
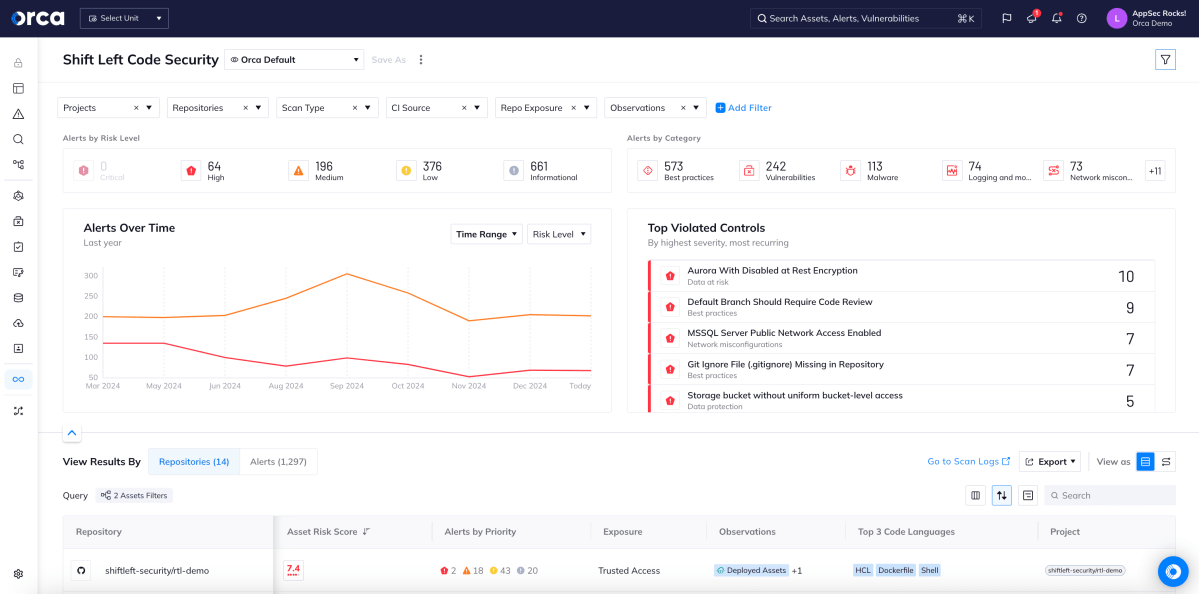
Secure your IaC at any stage in the application pipeline
Misconfigurations in Infrastructure-as-Code (IaC) can quickly propagate into hundreds or thousands of vulnerable cloud assets when reused for other projects. Orca offers detailed IaC scanning to catch issues early in the SDLC, as well as Cloud-to-Dev tracing, AI-Driven Remediation, and one-click PRs to fix IaC issues creating cloud risks.
- Easily set and customize policies for IaC scanning—including guardrails—to reflect your unique security requirements, and automatically scan IaC code on every PR to detect new issues or policy violations.
- Validate IaC code across popular IaC platforms, including Terraform, AWS CloudFormation, Azure Resource Manager, Google Deployment Manager, Ansible, Kubernetes, and more.
- Transform cloud alerts into AI-driven code fixes and one-click PRs that fix issues at their IaC origins and prevent risks from resurfacing.
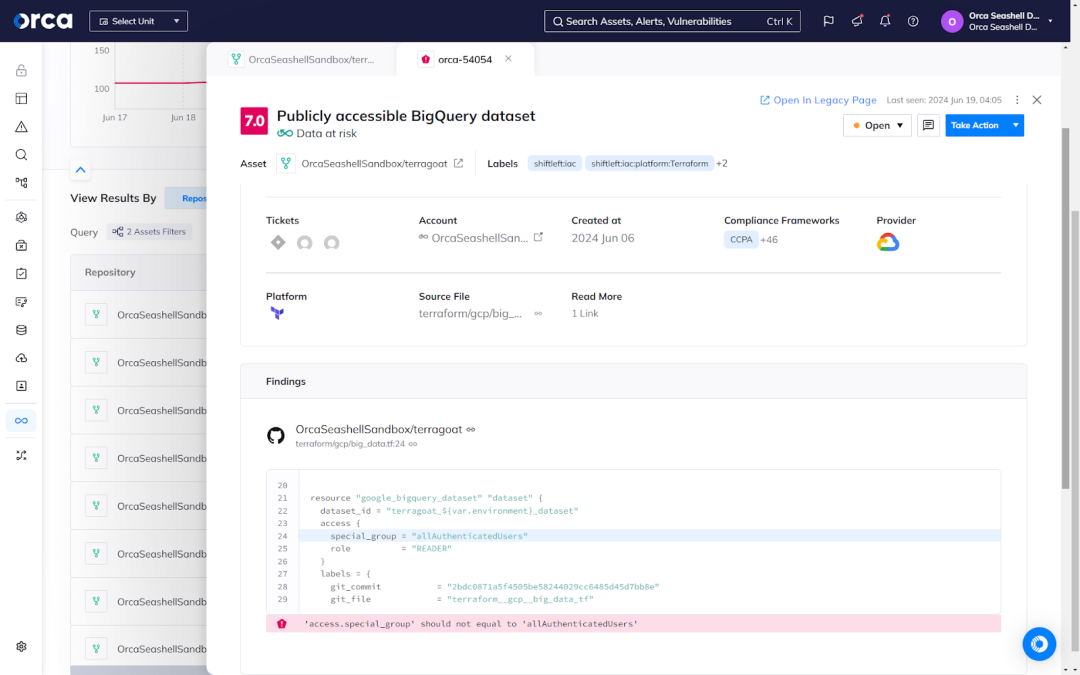
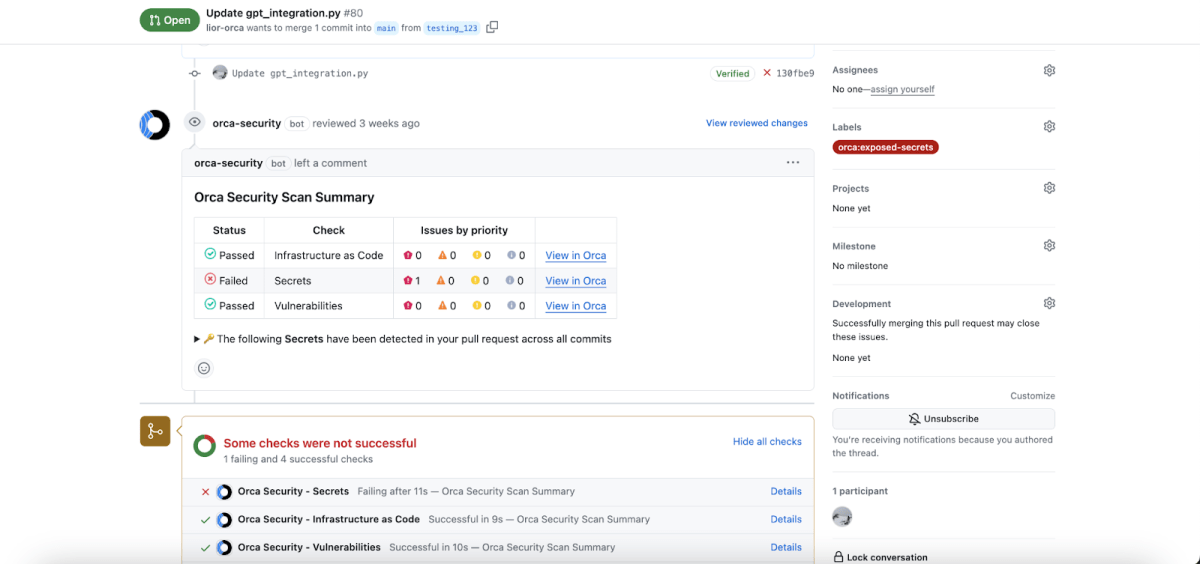
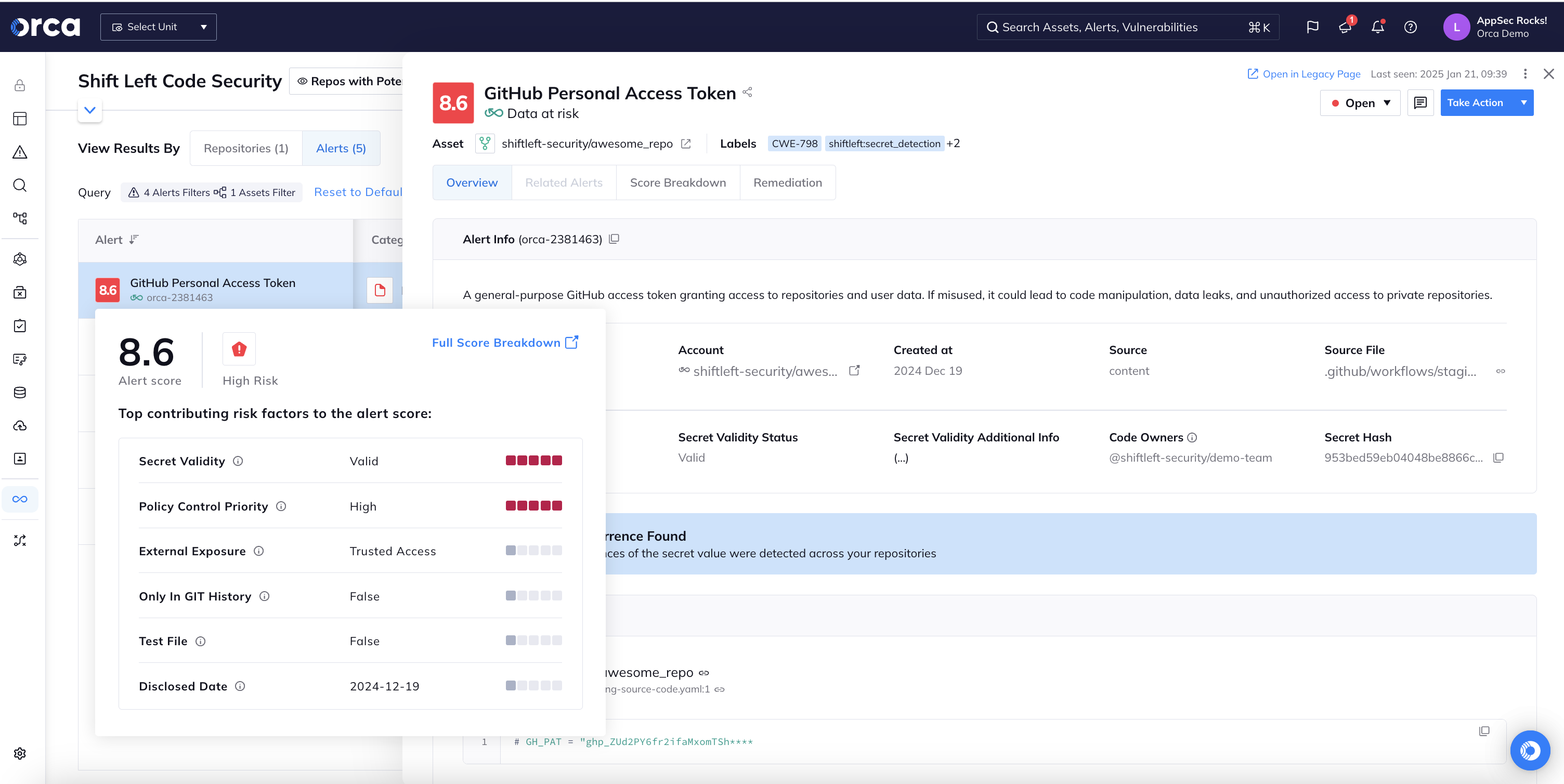
Detect Secrets before committing code
Attackers can discover exposed secrets in minutes. Orca prevents secrets exposure by detecting them early in the SDLC, long before code is built or shipped so you can keep secrets, secret.
- Integrate secrets detection into development platforms for automatic scanning, dynamic alert scoring, and risk prioritization using Orca’s GitHub App, GitLab App, Azure DevOps integration, or Orca CLI.
- Easily customize policies for secret detection to filter for specific security issues and set guardrails for blocking builds or notifying developers.
- Leverage Orca’s pre-commit hook to detect issues before they reach repositories, eliminating the need for secret rotations, risk analysis, and other post-commit measures.
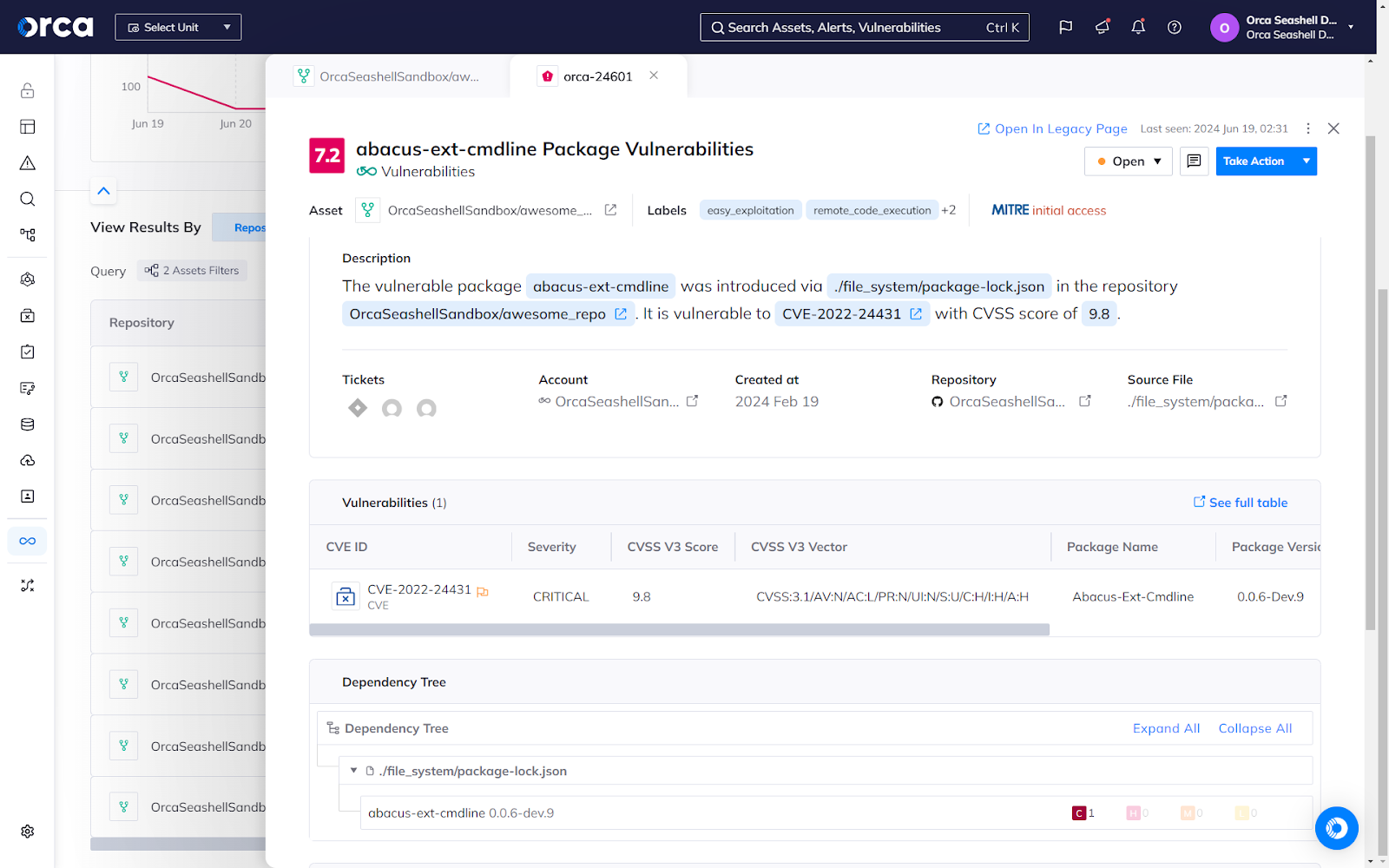
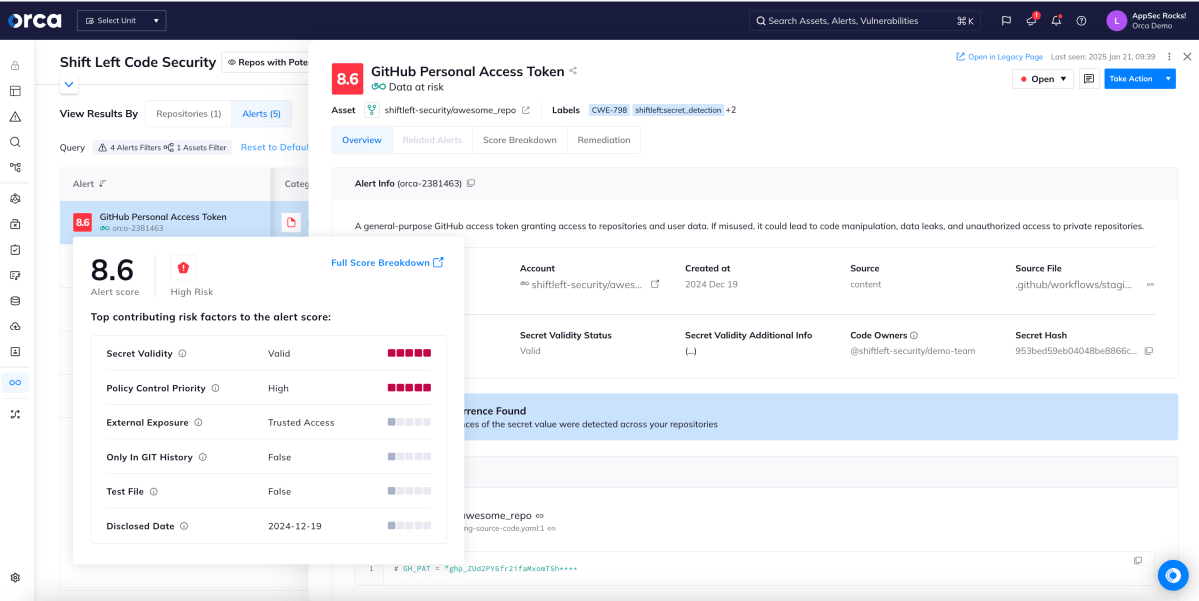
Software Composition Analysis (SCA) to detect open-source risks
Open-source vulnerabilities, misconfigurations, and licensing requirements are a question of “when,” not “if.” With Orca, you can automatically detect and secure open-source software in your codebase for enhanced security and confidence.
- Continuously scan your codebase, container images, and repositories during every code push or pull request.
- Obtain a full SBOM of your Code repositories, including transitive dependencies.
- Identify vulnerabilities introduced by dependencies across a wide range of packages, including Ruby, Python, PHP, Node.js, .NET, Java, Golang, and more.
- Detect OSS licenses of third-party packages and view associated requirements from code to cloud to enable effective compliance.
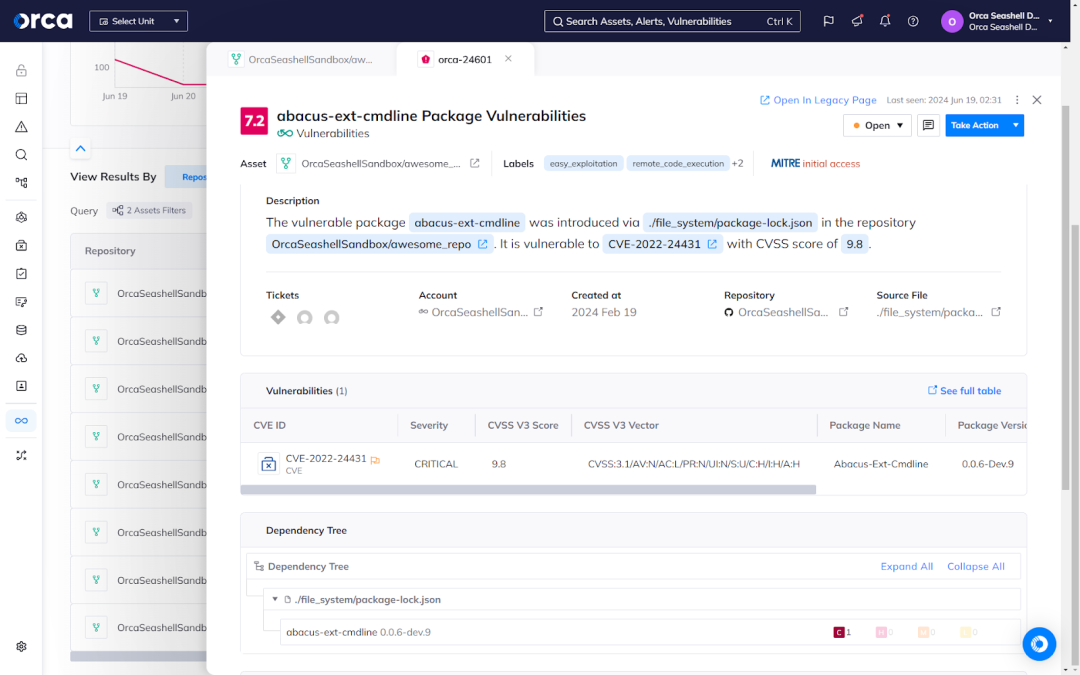
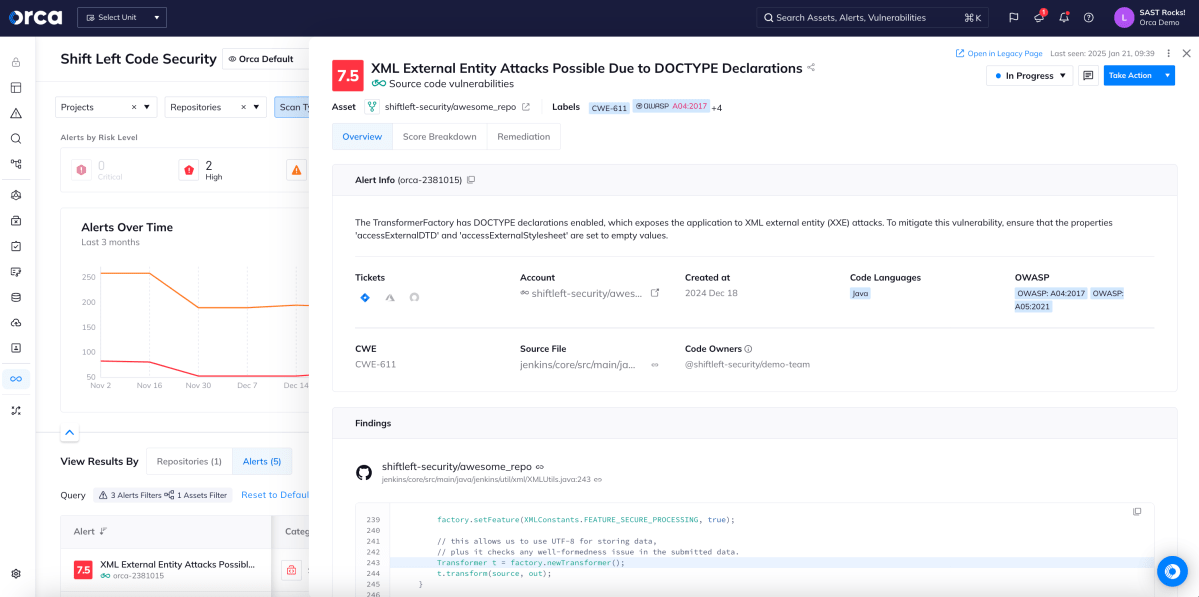
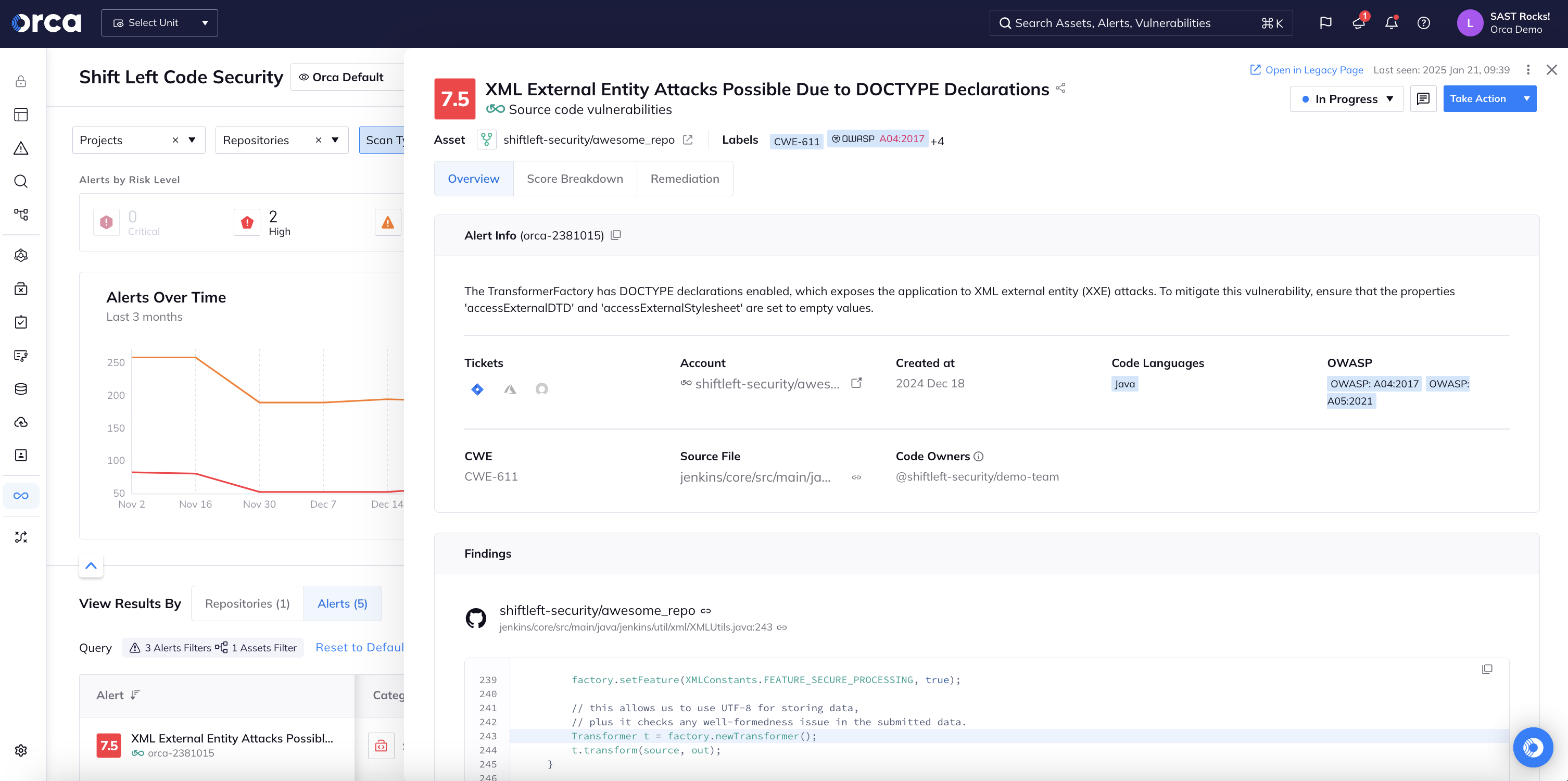
Secure first-party code with Static Application Security Testing (SAST)
Security teams often lack the visibility to catch risks when developers introduce vulnerabilities into first-party code. With Orca, security teams can leverage SAST scanning to detect issues early in the development pipeline.
- Scan source code to detect vulnerabilities and deliver actionable insights that developers can use during the coding process.
- Easily view, enable, or customize centralized SAST policies for scanning to tailor automated detections that scale across code repositories.
- Harness deep integrations with GitHub, GitLab, and Azure DevOps to ensure quick SAST deployment and a seamless, developer-centric experience.
- Leverage AI-driven code fixes and one-click PRs to fix vulnerabilities in first-party code from cloud to code.
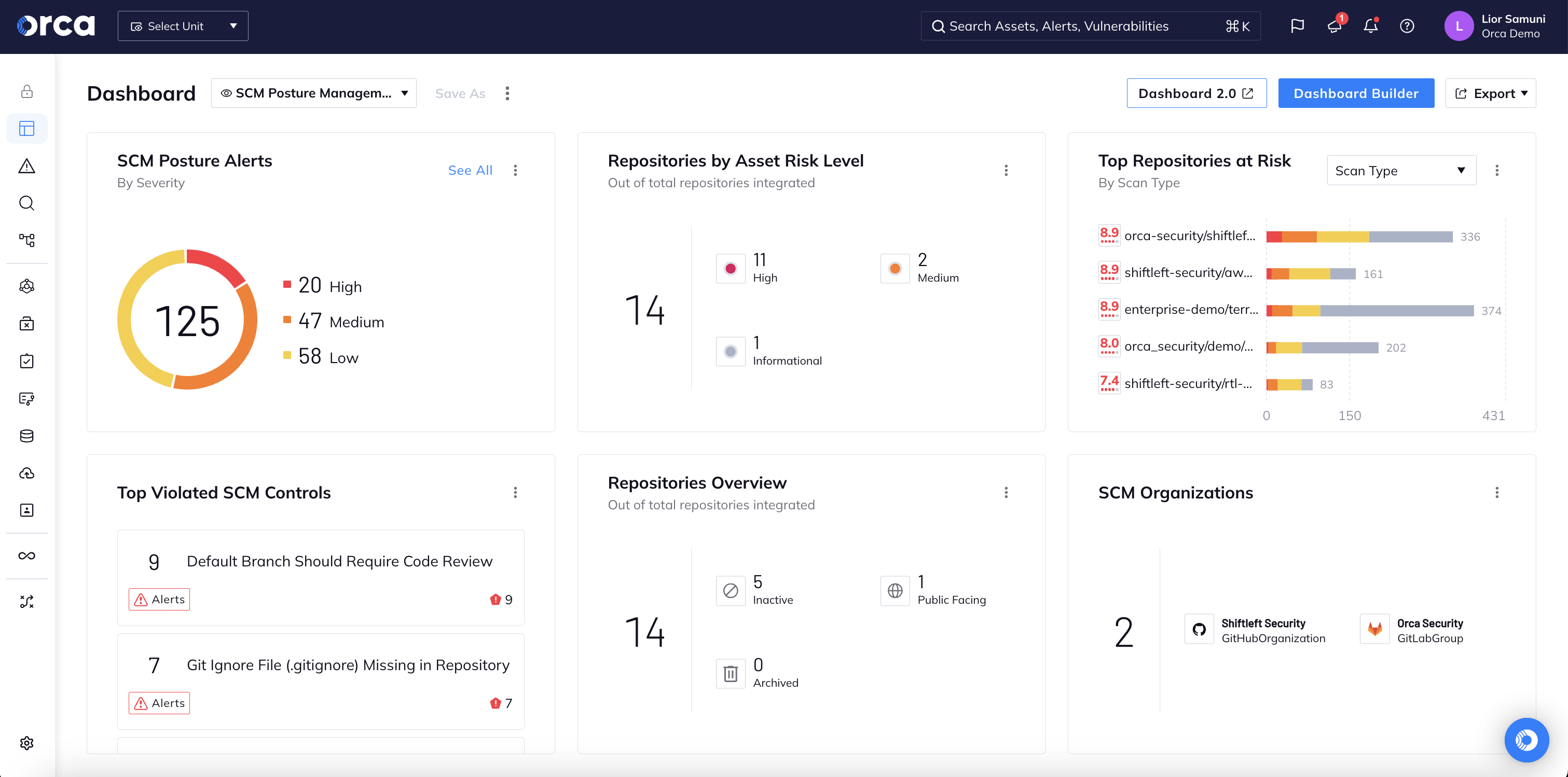
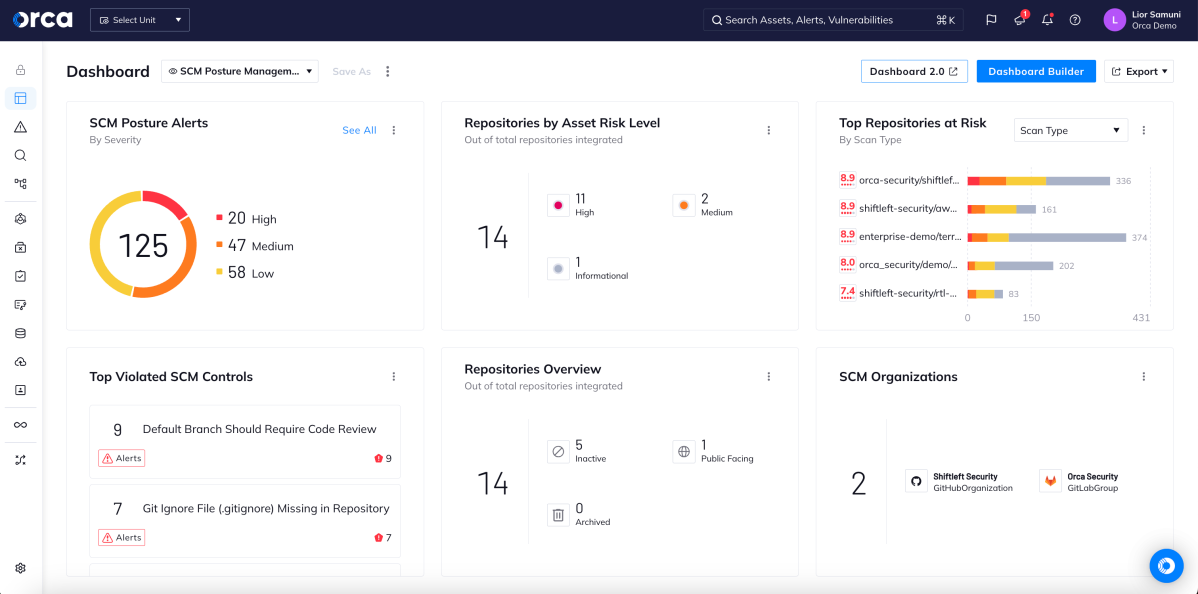
Keep Source Code Management configurations secure
Source Code Management (SCM) platforms can present significant security risks if not properly configured. With Orca, security teams can go beyond code security to detect and remediate misconfigurations and risks across SCM accounts and repositories.
- Get a comprehensive and detailed inventory of your repository instances, including any new repositories when they are created.
- Scan SCM platforms and assets using industry best practices from the Open Source Security Foundation (OPSSF), Legitify, and other industry standards.
- Leverage Orca’s dynamic risk assessments and prioritized alerts to enhance remediation efforts, reduce alert fatigue, and maximize productivity.

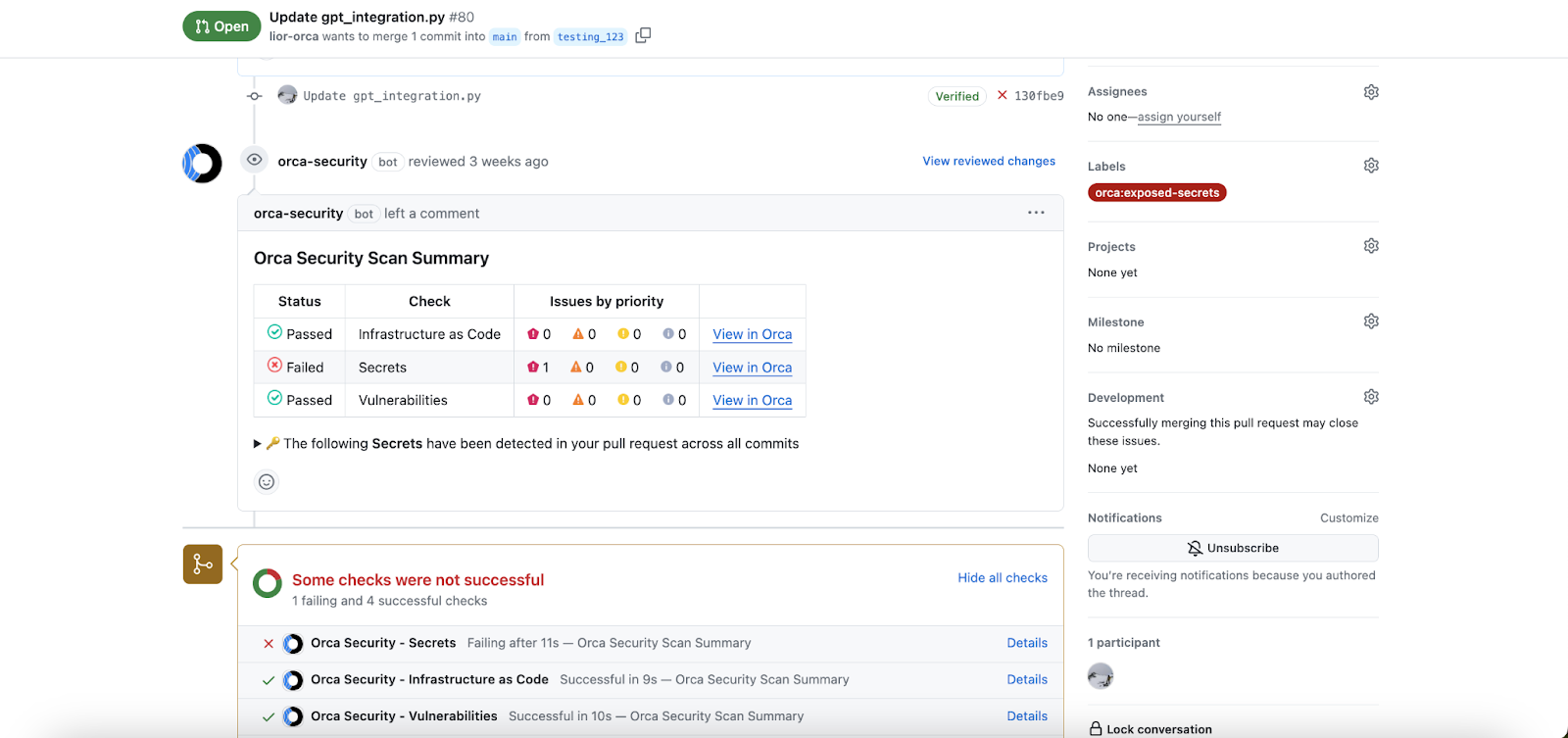
Build security into every CI/CD process
Embed comprehensive cloud security checks into your CI/CD process by leveraging Orca’s native integrations or easy-to-use command-line interface to:
- Automatically run all the critical security and compliance checks using CIS benchmarks and custom policies.
- Surface findings in native development tooling as well as the Orca Platform UI.
- Orca supports common CI and development tools, including Jenkins, BitBucket, CircleCI, GitHub, GitLab, and more.
Frictionless workflow integration and automation
Orca offers several off-the-shelf integrations so you can fit Orca into your existing workflows, ensuring fast remediation and avoiding confusion about team responsibilities.
- Forward findings to notification systems such as email, PagerDuty, OpsGenie, and Slack.
- Auto-assign alerts to remediation teams with ticketing systems such as Jira or ServiceNow.
- Apply security policy directly in GitHub, GitLab, and Azure DevOps using our deep integrations.
- Automate remediation by integrating Orca with SOAR systems, including Torq and Brinqa