At Orca Security, we’re on a mission to make it fast, easy, and cost effective for organizations to address the most critical cloud security issues so they can operate in the cloud with confidence. As a purpose-built cloud native platform, we aim to address a wide-range of cloud security requirements, spanning cloud infrastructure, workloads and applications, data and storage, APIs, and more.
As we continue to drive adoption of our platform, we’re proud to share that Orca Security has been named a Strong Performer in The Forrester Wave™: Cloud Workload Security, Q1 2024. This is the first time we’ve participated in a Wave for this category.
In the report, the Orca Cloud Security Platform received the highest possible scores in the following criteria:
- Admin identity and access management (5/5) – At Orca we’ve made significant headway in expanding our CIEM capabilities as well as introducing our IAM Policy Optimizer that uses AI to automatically calculate right-sized permissions and provides teams with turnkey policies that can instantly be applied to cloud accounts.
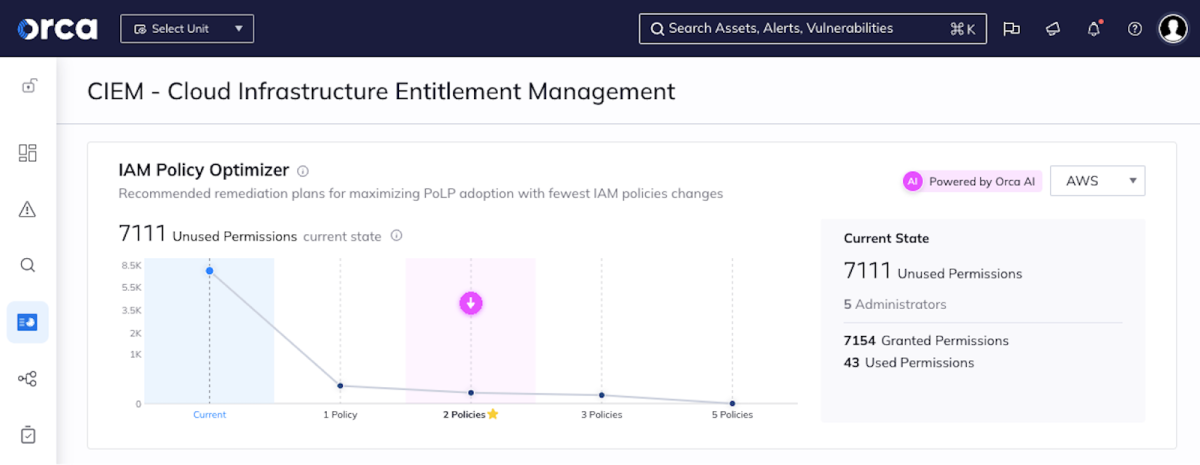
Orca calculates how to make the largest security improvements with the least policy changes
- Infrastructure as Code (IaC) scanning (5/5) – We’ve been particularly focused on expanding our IaC scanning capabilities by closing the loop between risks found in production and their code origins – what we call our ‘Cloud-to-Dev’ capabilities. By showing security teams which application development artifacts deployed the risks into production, they can partner with development and DevOps teams to fix risks quickly, rather than having to spend days or even weeks to understand where the risk originated from.
- Scale (5/5) – From Orca’s perspective, this has always been one of the major benefits of our SideScanning technology that is at the heart of our agentless-first platform. The ability to deploy in minutes, cover 100% of assets, and automatically include new assets when they are added without needing manual intervention.
- Roadmap (5/5) – We believe our vision to deliver innovative cloud security that helps modern and cloud-forward businesses excel in the cloud, shows on our roadmap.
- Partner ecosystem (5/5) – At Orca it has always been our priority to work with partners and integrate with third-party applications so that teams do not need to change the way they work.
“Orca’s administrator IAM and IaC scanning are powerful and are ahead of the competition. The vendor’s largest number of workloads protected by the vendor’s agentless CWP is also ahead.”
The Forrester WaveTM: Cloud Workload Security, Q1 2024, by Andras Cser
Why Cloud Workload Security (CWS) is Critical for Organizations
Cloud Workload Security addresses the multi-faceted requirements for securing the entirety of the cloud tech stack, as well as integrating capabilities for securing cloud native artifacts pre-deployment, such as IaC templates or container images. CWS solutions should also support multi-cloud environments for both unified visibility and security.
Critical capabilities include:
- Cloud Security Posture Management to provide centralized visibility, misconfiguration management, and security across clouds
- Multi-Cloud Infrastructure Entitlement Management capabilities to monitor access and user activity within cloud environments
- IaC scanning to secure cloud environments pre-deployment
- Compliance with support for out-of-the-box frameworks and templates and customized reporting
Expanding Orca’s Agentless-First Approach with Agent-Based Protection
From inception, Orca Security has been the agentless-first Cloud Security Platform that identifies, prioritizes, and remediates security risks and compliance issues across your cloud estate spanning AWS, Azure, Google Cloud and Kubernetes.
The Orca Platform is:
- Agentless-first, to ensure easy onboarding and quick time-to-value
- Unified, to centralize cloud data, ease compliance efforts, and prioritize views into risk
- AI-Driven, to empower security, DevOps, and development teams to automate and accelerate critical tasks
For the 2024 Wave, Forrester required organizations to have capabilities Generally Available (GA) by June 30, 2023. As a result, our agent-based runtime protection capabilities, powered by ThreatOptix, were not included in the evaluation of the report. We firmly believe that our continued capabilities in this area would only improve our standing in future.
“The vendor’s CWS roadmap includes: 1) improving threat detection and response automation, especially in the DevOps area; 2) agent-based runtime protection for Linux and Windows virtual machines; and 3) expanding shift-left scanning security.”
The Forrester WaveTM: Cloud Workload Security, Q1 2024, by Andras Cser
Get a demo of the Orca Platform today
If you are interested in learning more about the Orca Cloud Security Platform, sign up for a demo or visit our Platform webpage.






